Blog
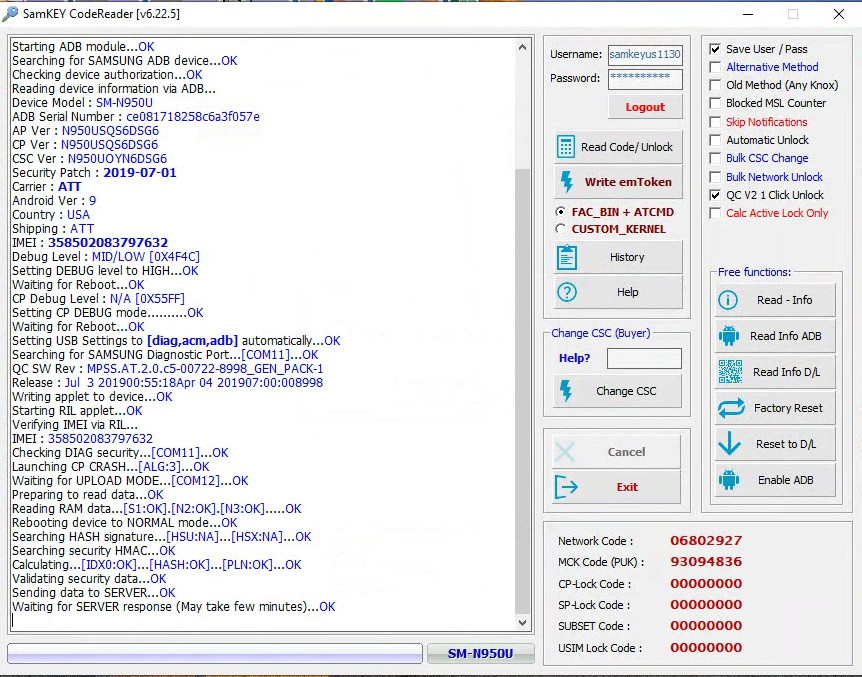
Direct Unlock SM-N950U by Samkey
Searching for SAMSUNG Mobile USB Modem...OK
SAMSUNG USB Modem detected on [COM7]
Looking for DEVICE.....OK
Reading USB MODEM information...OK
MODEL : SM-N950U
VER : N950USQS6DSG6/N950UOYN6DSG6/N950USQS6DSG6/N950USQS6DSG6
IMEI : 358502083797632
S/N : R38JA0M9QF
U/N : CE081718258C6A3
Algorithm : MSM Crypto Engine
Loading ADB module............OK
Starting ADB module...OK
Searching for SAMSUNG ADB device...OK
Checking device authorization...OK
Reading device information via ADB...
Device Model : SM-N950U
ADB Serial Number : ce081718258c6a3f057e
AP Ver : N950USQS6DSG6
CP Ver : N950USQS6DSG6
CSC Ver : N950UOYN6DSG6
Security Patch : 2019-07-01
Carrier : ATT
Android Ver : 9
Country : USA
Shipping : ATT
IMEI : 358502083797632
Debug Level : MID/LOW [0X4F4C]
Setting DEBUG level to HIGH...OK
Waiting for Reboot...OK
CP Debug Level : N/A [0X55FF]
Setting CP DEBUG mode..........OK
Waiting for Reboot...OK
Setting USB Settings to [diag,acm,adb] automatically...OK
Searching for SAMSUNG Diagnostic Port...[COM11]...OK
QC SW Rev : MPSS.AT.2.0.c5-00722-8998_GEN_PACK-1
Release : Jul 3 201900:55:18Apr 04 201907:00:008998
Writing applet to device...OK
Starting RIL applet...OK
Verifying IMEI via RIL...
IMEI : 358502083797632
Checking DIAG security...[COM11]...OK
Launching CP CRASH...[ALG:3]...OK
Waiting for UPLOAD MODE...[COM12]...OK
Preparing to read data...OK
Reading RAM data...[S1:OK].[N2:OK].[N3:OK].....OK
Rebooting device to NORMAL mode...OK
Searching HASH signature...[HSU:NA]...[HSX:NA]...OK
Searching security HMAC...OK
Calculating...[IDX0:OK]...[HASH:OK]...[PLN:OK]...OK
Validating security data...OK
Sending data to SERVER...OK
Waiting for SERVER response (May take few minutes)...OK
SamKEY Team (2016-2024)
FRP One Plus N200 5G by Chimera Tool
Primero Desconectar pantalla para poder hacer el Test Point
Chimera Mobile Phone Utility version: 44.46.0957 @ 2025-10-07
Delete FRP partition
Clearing FRP lock
Rebooting the phone...
Finished at local time: [10.07.25 10:07:10]
WorkID: 402293195

onn 8 Tablet Azul FRP Factory Reset by Chimera Tool file= preloader_t302aa.bin
Tablet ONN Azul
Presionar Apagar y presionar Volumen Abajo para que la detecte en BROM
..Port - Device detected :)
Preloader - CPU: MT6768/MT6769(Helio P65/G85 k68v1)
Preloader - HW version: 0x0
Preloader - WDT: 0x10007000
Preloader - Uart: 0x11002000
Preloader - Brom payload addr: 0x100a00
Preloader - DA payload addr: 0x201000
Preloader - CQ_DMA addr: 0x10212000
Preloader - Var1: 0x25
Preloader - Disabling Watchdog...
Preloader - HW code: 0x707
Preloader - Target config: 0xe1
Preloader - SBC enabled: True
Preloader - SLA enabled: False
Preloader - DAA enabled: False
Preloader - SWJTAG enabled: False
Preloader - EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: False
Preloader - Root cert required: False
Preloader - Mem read auth: True
Preloader - Mem write auth: True
Preloader - Cmd 0xC8 blocked: True
Preloader - Get Target info
Preloader - BROM mode detected.
Preloader - HW subcode: 0x8a00
Preloader - HW Ver: 0xca00
Preloader - SW Ver: 0x0
Preloader - ME_ID: 5D0460E07ACDF00530423239DB7186E9
Preloader - SOC_ID: B9282535F434E79783F7EA2C7249FB5179C5D19282784E7B38A85085FF666236
DaHandler - Device is protected.
DaHandler - Device is in BROM-Mode. Bypassing security.
PLTools - Loading payload from mt6768_payload.bin, 0x264 bytes
Exploitation - Kamakiri Run
Exploitation - Done sending payload...
PLTools - Successfully sent payload: \payloads\mt6768_payload.bin
Port - Device detected :)
DaHandler
DaHandler - [LIB]: Device is in BROM mode. No preloader given, trying to dump preloader from ram.
Successfully extracted preloader for this device to: preloader_t302aa.bin
DAXFlash - Uploading xflash stage 1 from MTK_DA_V5.bin
XFlashExt - Patching da1 ...
Mtk - Patched "Patched loader msg" in preloader
Mtk - Patched "hash_check" in preloader
Mtk - Patched "Patched loader msg" in preloader
Mtk - Patched "get_vfy_policy" in preloader
XFlashExt - Patching da2 ...
XFlashExt - Security check patched
XFlashExt - DA version anti-rollback patched
XFlashExt - SBC patched to be disabled
XFlashExt - Register read/write not allowed patched
DAXFlash - Successfully uploaded stage 1, jumping ..
Preloader - Jumping to 0x200000
Preloader - Jumping to 0x200000: ok.
DAXFlash - Successfully received DA sync
DAXFlash - Sending emi data ...
DAXFlash - DRAM setup passed.
DAXFlash - Sending emi data succeeded.
DAXFlash - Uploading stage 2...
DAXFlash - Upload data was accepted. Jumping to stage 2...
DAXFlash - Boot to succeeded.
DAXFlash - Successfully uploaded stage 2
DAXFlash - DA SLA is disabled
DAXFlash - EMMC FWVer: 0x0
DAXFlash - EMMC ID: AT3SFB
DAXFlash - EMMC CID: ec2900415433534642300d2fd384baf9
DAXFlash - EMMC Boot1 Size: 0x400000
DAXFlash - EMMC Boot2 Size: 0x400000
DAXFlash - EMMC GP1 Size: 0x0
DAXFlash - EMMC GP2 Size: 0x0
DAXFlash - EMMC GP3 Size: 0x0
DAXFlash - EMMC GP4 Size: 0x0
DAXFlash - EMMC RPMB Size: 0x400000
DAXFlash - EMMC USER Size: 0x748000000
DAXFlash - HW-CODE : 0x707
DAXFlash - HWSUB-CODE : 0x8A00
DAXFlash - HW-VERSION : 0xCA00
DAXFlash - SW-VERSION : 0x0
DAXFlash - CHIP-EVOLUTION : 0x1
DAXFlash - DA-VERSION : 1.0
DAXFlash - Extensions were accepted. Jumping to extensions...
DAXFlash - Boot to succeeded.
DAXFlash - DA Extensions successfully added
DeviceClass - [Errno 19] No such device (it may have been disconnected)
Reset command was sent. Disconnect usb cable to power off.
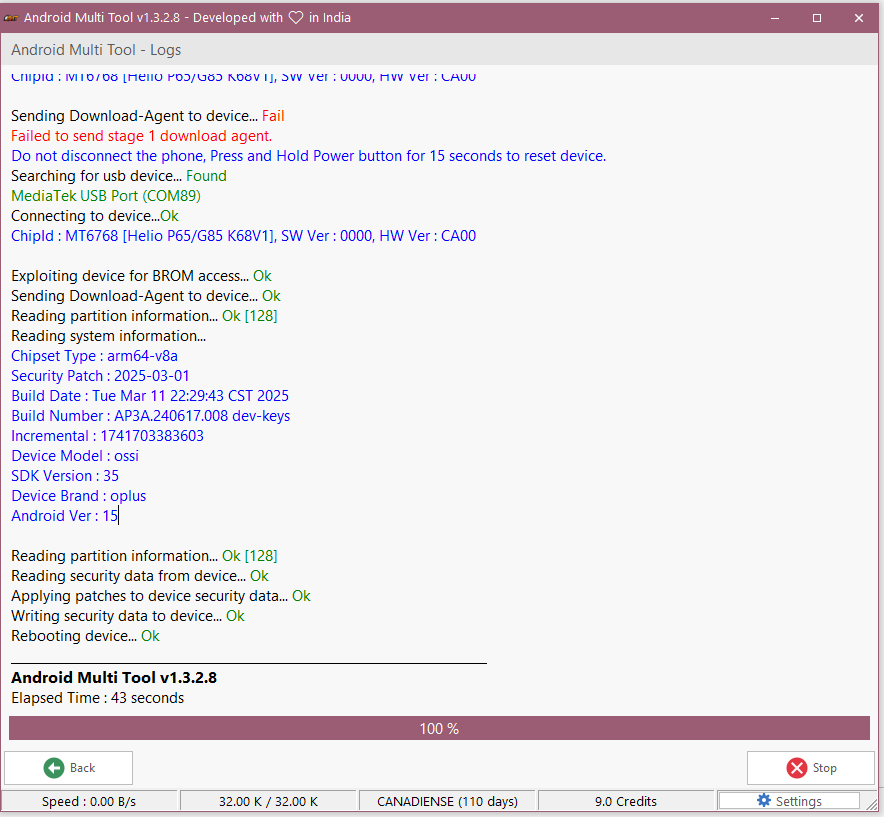
FRP Oppo A58 CPH2577 by AMT
Presionar Volumen + - Insertar cable USB para entrar en modo Preloader
Instalar Drivers QcomMtk_Driver_Setup_4.0.1.6_.exe
Brand : OPPO
Model : A58
Operation : Reset FRP
Searching for usb device... Found
MediaTek PreLoader USB VCOM (Android) (COM87)
Connecting to device...Ok
ChipId : MT6768 [Helio P65/G85 K68V1], SW Ver : 0000, HW Ver : CA00
Sending Download-Agent to device... Fail
Failed to send stage 1 download agent.
Do not disconnect the phone, Press and Hold Power button for 15 seconds to reset device.
Searching for usb device... Found
MediaTek USB Port (COM89)
Connecting to device...Ok
ChipId : MT6768 [Helio P65/G85 K68V1], SW Ver : 0000, HW Ver : CA00
Exploiting device for BROM access... Ok
Sending Download-Agent to device... Ok
Reading partition information... Ok [128]
Reading system information...
Chipset Type : arm64-v8a
Security Patch : 2025-03-01
Build Date : Tue Mar 11 22:29:43 CST 2025
Build Number : AP3A.240617.008 dev-keys
Incremental : 1741703383603
Device Model : ossi
SDK Version : 35
Device Brand : oplus
Android Ver : 15
Reading partition information... Ok [128]
Formatting desired partition... Ok
Reading partition information... Ok [128]
Reading security data from device... Ok
Applying patches to device security data... Ok
Writing security data to device... Ok
Rebooting device... Ok
Android Multi Tool v1.3.2.8
Elapsed Time : 43 seconds
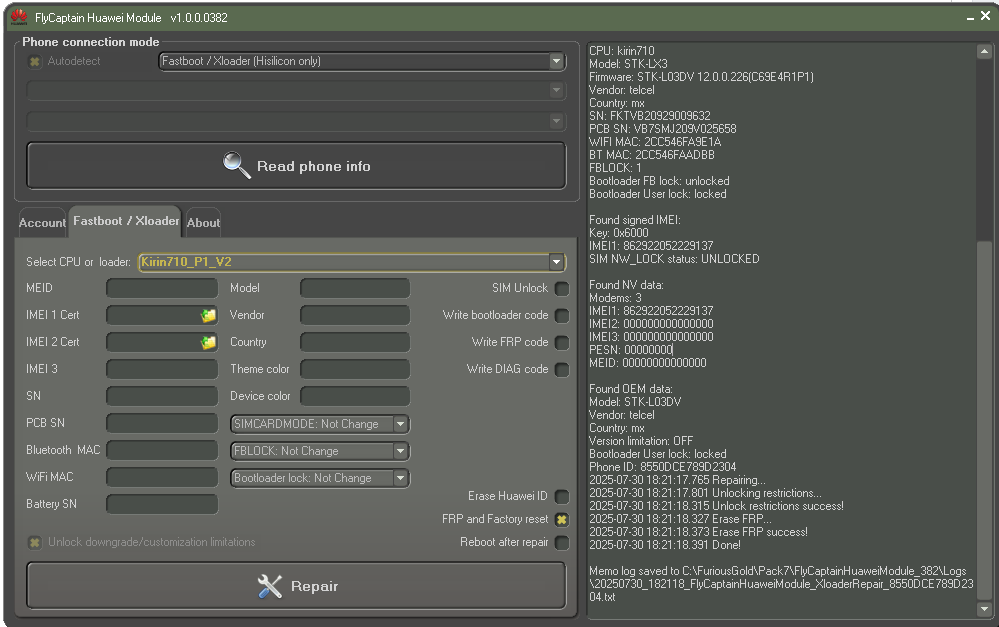
FRP Huawei Y9s Telcel by Furious Gold Pack 7
Hacer Test Point

30/07/2025 06:21:01 p. m.
FlyCaptain Huawei Module v1.0.0.0382
Account: 0064B621
Before operation turn phone to TestPoint mode:
Turn off phone, then short TestPoint on phone pcb
and plug USB cable
Wait for device "HUAWEI USB COM 1.0" in Ports
Repair
Unlock downgrade/customization limitations
FRP and Factory reset
Selected Cpu/Bootloader - Kirin710_P1_V2
2025-07-30 18:21:03.387 Connecting to server...
2025-07-30 18:21:03.879 Connected!
2025-07-30 18:21:07.024 HUAWEI device in Test Point mode Not found!
2025-07-30 18:21:07.380 Reading info...
2025-07-30 18:21:11.900 IMEI certifiacate backup success!
2025-07-30 18:21:12.951 Done!
Fastboot provided info:
CPU: kirin710
Model: STK-LX3
Firmware: STK-L03DV 12.0.0.226(C69E4R1P1)
Vendor: telcel
Country: mx
SN: FKTVB20929009632
PCB SN: VB7SMJ209V025658
WIFI MAC: 2CC546FA9E1A
BT MAC: 2CC546FAADBB
FBLOCK: 1
Bootloader FB lock: unlocked
Bootloader User lock: locked
Found signed IMEI:
Key: 0x6000
IMEI1: 862922052229137
SIM NW_LOCK status: UNLOCKED
Found NV data:
Modems: 3
IMEI1: 862922052229137
IMEI2: 000000000000000
IMEI3: 000000000000000
PESN: 00000000
MEID: 00000000000000
Found OEM data:
Model: STK-L03DV
Vendor: telcel
Country: mx
Version limitation: OFF
Bootloader User lock: locked
Phone ID: 8550DCE789D2304
2025-07-30 18:21:17.765 Repairing...
2025-07-30 18:21:17.801 Unlocking restrictions...
2025-07-30 18:21:18.315 Unlock restrictions success!
2025-07-30 18:21:18.327 Erase FRP...
2025-07-30 18:21:18.373 Erase FRP success!
2025-07-30 18:21:18.391 Done!
Memo log saved to C:\FuriousGold\Pack7\FlyCaptainHuaweiModule_382\Logs\20250730_182118_FlyCaptainHuaweiModule_XloaderRepair_8550DCE789D2304.txt
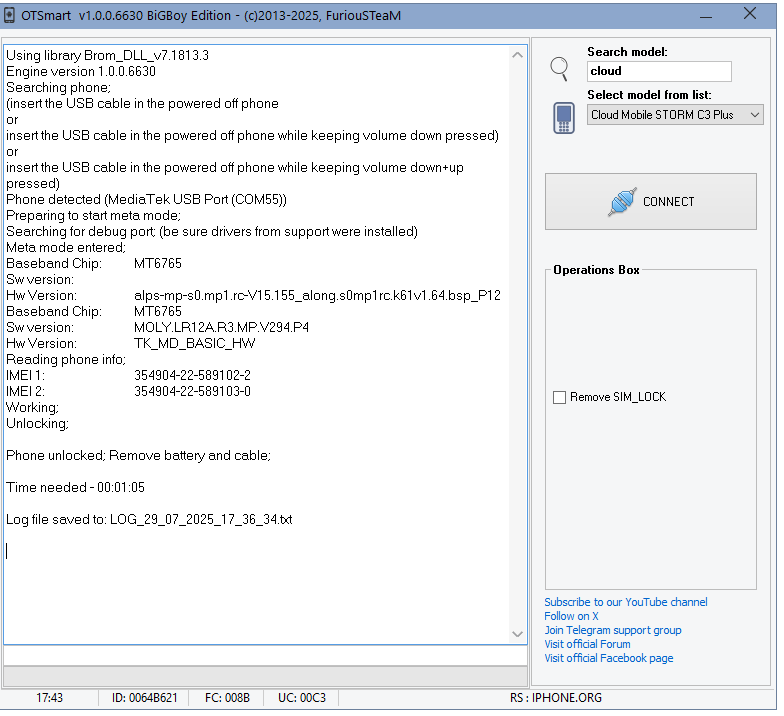
Direct Unlock Cloud Mobile C8 By Furious Gold
Volumen + - conectar el cable
Using library Brom_DLL_v7.1813.3
Engine version 1.0.0.6630
Searching phone;
(insert the USB cable in the powered off phone
or
insert the USB cable in the powered off phone while keeping volume down pressed)
or
insert the USB cable in the powered off phone while keeping volume down+up pressed)
Phone detected (MediaTek USB Port (COM55))
Preparing to start meta mode;
Searching for debug port; (be sure drivers from support were installed)
Meta mode entered;
Baseband Chip: MT6765
Sw version:
Hw Version: alps-mp-s0.mp1.rc-V15.155_along.s0mp1rc.k61v1.64.bsp_P12
Baseband Chip: MT6765
Sw version: MOLY.LR12A.R3.MP.V294.P4
Hw Version: TK_MD_BASIC_HW
Reading phone info;
IMEI 1: 354904-22-589102-2
IMEI 2: 354904-22-589103-0
Working;
Unlocking;
Phone unlocked; Remove battery and cable;
Time needed - 00:01:05
Log file saved to: LOG_29_07_2025_17_36_34.txt
FRP Samsung A155M A15 by Unlocktool
[PRELOADER] ERASE FRP
Selected auth :
CUSTOM DA
Retrieving server data...
OK
[364.76 KiB]
Phone must have battery inside!
Waiting for device...
COM55
[BOOTROM:0E8D:0003]
Initializing usb...
OK
Waiting for device...
COM55
[BOOTROM:0E8D:0003]
Reading hardware info...
OK
Hardware :
MT6789 [Helio G99]
1208
8A00
CA00
0000
Security Config :
SCB DAA
MEID :
7241F58401C665C5C20CF2E70A71969A
Custom DA(e) :
Samsung_A155M_MT6789_BIT5
Sending Download-Agent...
OK
Syncing with target...
OK
Booting device (brom auth)...
OK
Authenticating
SLA
...
OK
Syncing with
DA
...
OK
Storage :
UFS
- CID :
4B4D354C3930303144412D423432340000000000
UFS: LU0 Size :
4 MiB
- LU1 Size :
4 MiB
- LU2 Size :
119.17 GiB
Reading partition info...
OK
[58]
Reading device info...
OK
[super]
Model Name :
SM-A155M_LA_TPA_MKEY1
Manufacturer :
SAMSUNG
Build ID :
A155MUBS1AXD2
Connecting to device...
OK
Erasing
FRP
...
OK
UNLOCKTOOL
2025.07.15.0
Elapsed time :
1 minute 10 seconds
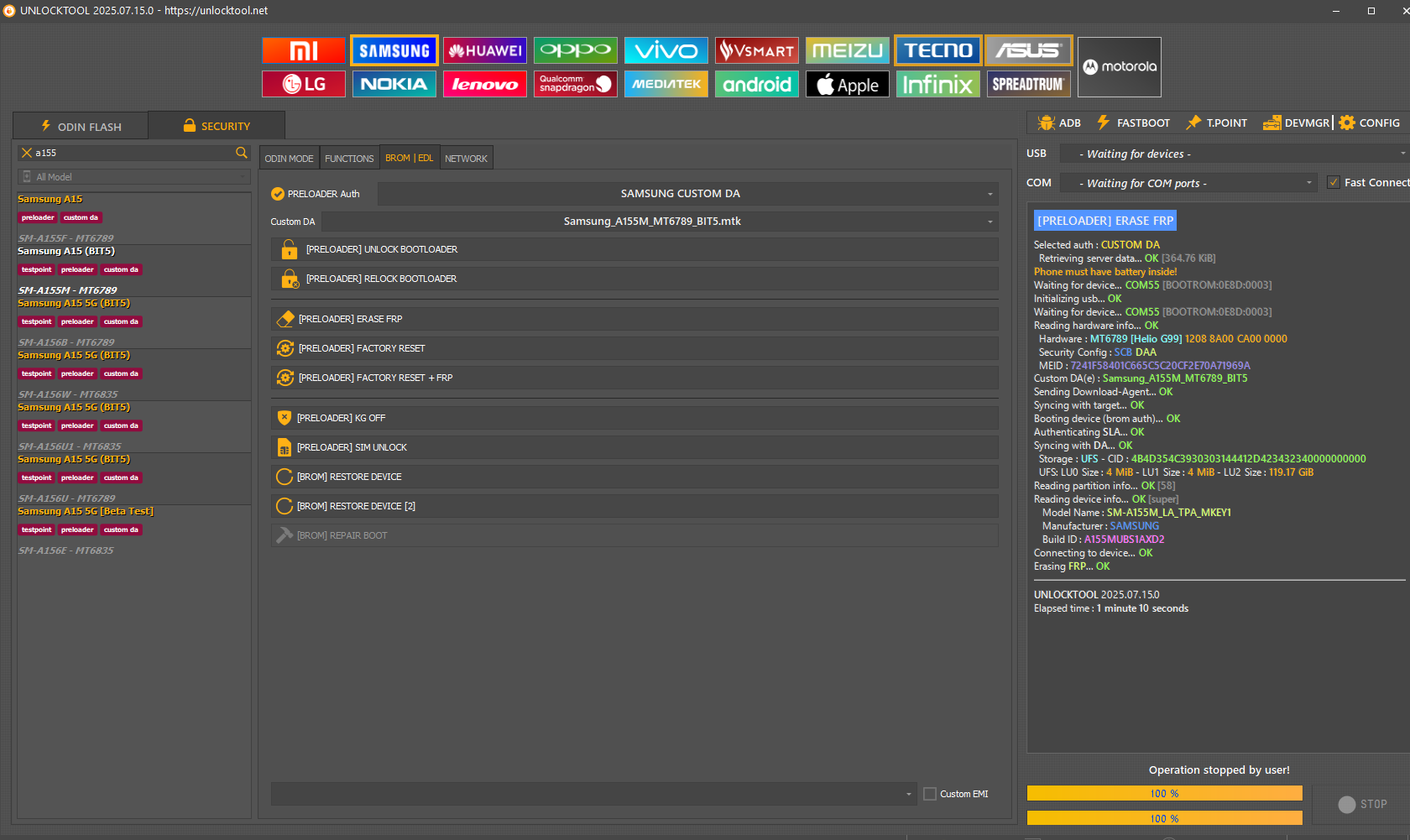
FRP LG X180g MTK MT6592 by Octopus Box LG
Welcome to Octoplus/Octopus Box LG Software version 3.2.4
Plesionar volumen abajo + cable usb
Selected USB connection type
Work ID: 00000000021E2DC7
Checking data...OK
Platform: LG MTK
Selected port:
Selected baudrate: 0
Selected model: X180G
Press and hold "Vol-" and connect cable.OK
Phone found.
CPU name: MT6592
CPU revision: 8A00.CA00.0000.0000
Prepairing loader...OK
Sending loader...OK
Synchronizing with loader...
Detecting flash chip...OK
Detecting EMMC flash chip...OK
Reading info...OK
Reconnecting phone...OK
Found model at port COM88
Reading partitions...OK
Checking security...
Checking security passed!
--------------------------------------------------------------------------------
IMEI A: 354597-07-032132-5
IMEI B: Bad
Bluetooth address: 88:07:4B:60:83:E6
Wi-Fi MAC address: 88:07:4B:E9:2E:3F
EMMC rpmb size: 4 Mb
EMMC boot1 size: 4 Mb
EMMC boot2 size: 4 Mb
EMMC gp1 size: 0 Mb
EMMC gp2 size: 0 Mb
EMMC gp3 size: 0 Mb
EMMC gp4 size: 0 Mb
EMMC user area size: 15032 Mb
--------------------------------------------------------------------------------
Reading partitions...OK
Resetting FRP Lock...OK
Resetting FRP lock successfully completed!
Performed by 3.2.4 Software version.
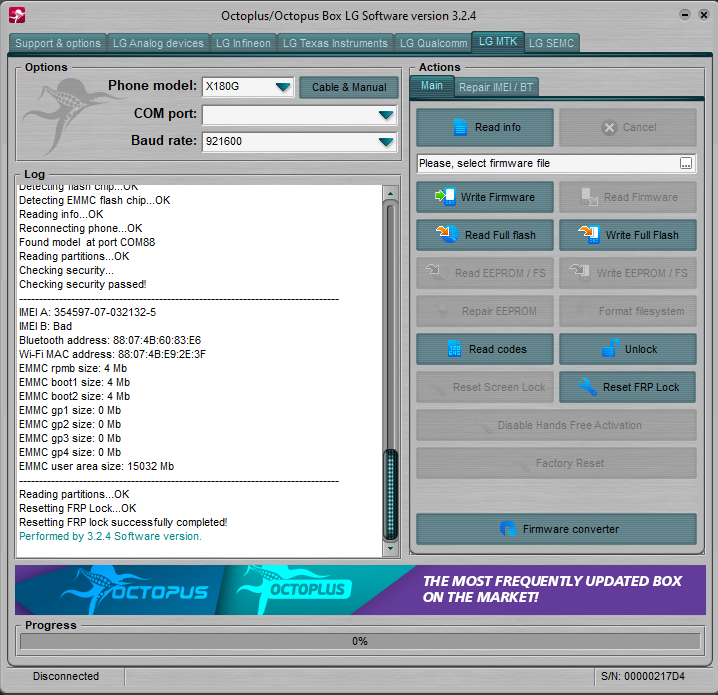
Direct Unlock TCL 4058R by Furious Gold
Using library Brom_DLL_v7.2116.0
Engine version 1.0.0.6630
Searching phone;
(insert the USB cable in the powered off phone
or
insert the USB cable in the powered off phone while keeping volume down pressed)
or
insert the USB cable in the powered off phone while keeping volume down+up pressed)
Phone detected (MediaTek USB Port (COM204))
Preparing to start meta mode;
Requesting authorization;
Searching for debug port; (be sure drivers from support were installed)
Meta mode entered;
Baseband Chip: MT6739
Sw version:
Hw Version: alps-mp-r0.mp1-V8.172.2_tct.spf.r0mp1.k61v1.64.bsp_P3
Baseband Chip: MT6739
Sw version: MOLY.LR12A.R3.MP.V179.5.P40
Hw Version: TK_MD_L4_HW
Reading phone info;
IMEI 1: 016143-00-199383-1
IMEI 2: 000000-00-000000-0
BB ID: RjcxREZBQkZEMEMwODFBM0EzRDk3NjQ1MDZFQUFFNDY=
Working;
Connecting to server;
Authorisation process started;
Furious Multipurpose Credits: 16
Done;
Requesting data from server ! Wait please ...
Checking data integrity;
Data integrity: OK;
SIM_LOCK: ENABLED
Rebuilding security;
Unlocking;
Phone unlocked; Remove battery and cable;
Time needed - 00:00:47
Log file saved to: LOG_19_06_2025_13_10_34.txt
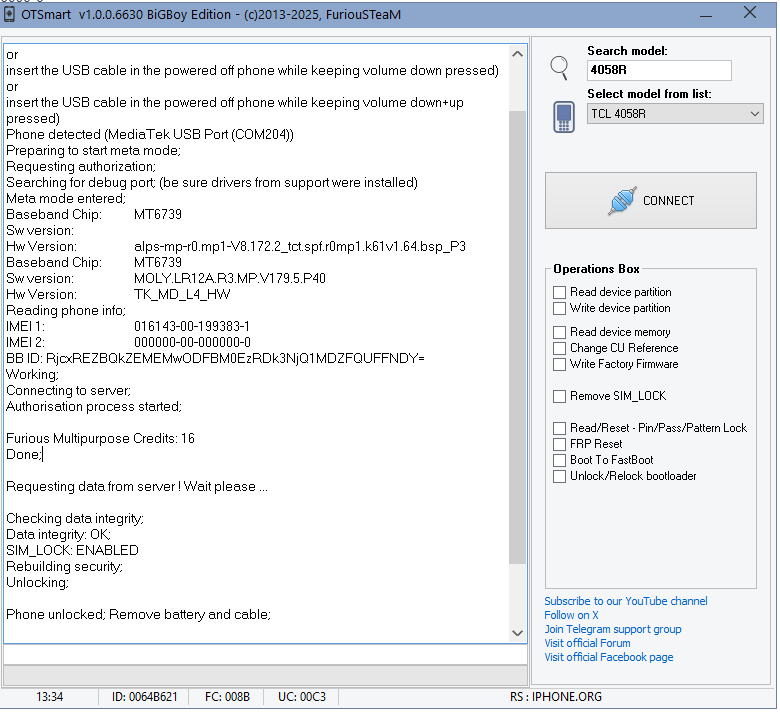
FRP REDMI 12 by AMT Android Multi Tool
Consume 1 credito
presionar volumen arriba + encendido (conectar cable usb)
Brand : XIAOMI
Model : REDMI 12
Operation : Mi Assistant FRP
Searching for Android ADB Device... Ok
Getting device information...
Device Model : fire
Device Product : fire_global
Device Version : V14.0.13.0.TMXMIXM
Device Serial No. : 0x07f2ccfeca003a41e3bc35d0b94e28dd7af626bc
Device Codebase : 13
Device Branch : F
Device Language : en
Device Region : US
Device Recovery Version : 2
Getting mi assistant frp token from server... Ok
Resetting FRP... Ok
Rebooting device... Ok
Android Multi Tool v1.3.2.5
Elapsed Time : 10 seconds
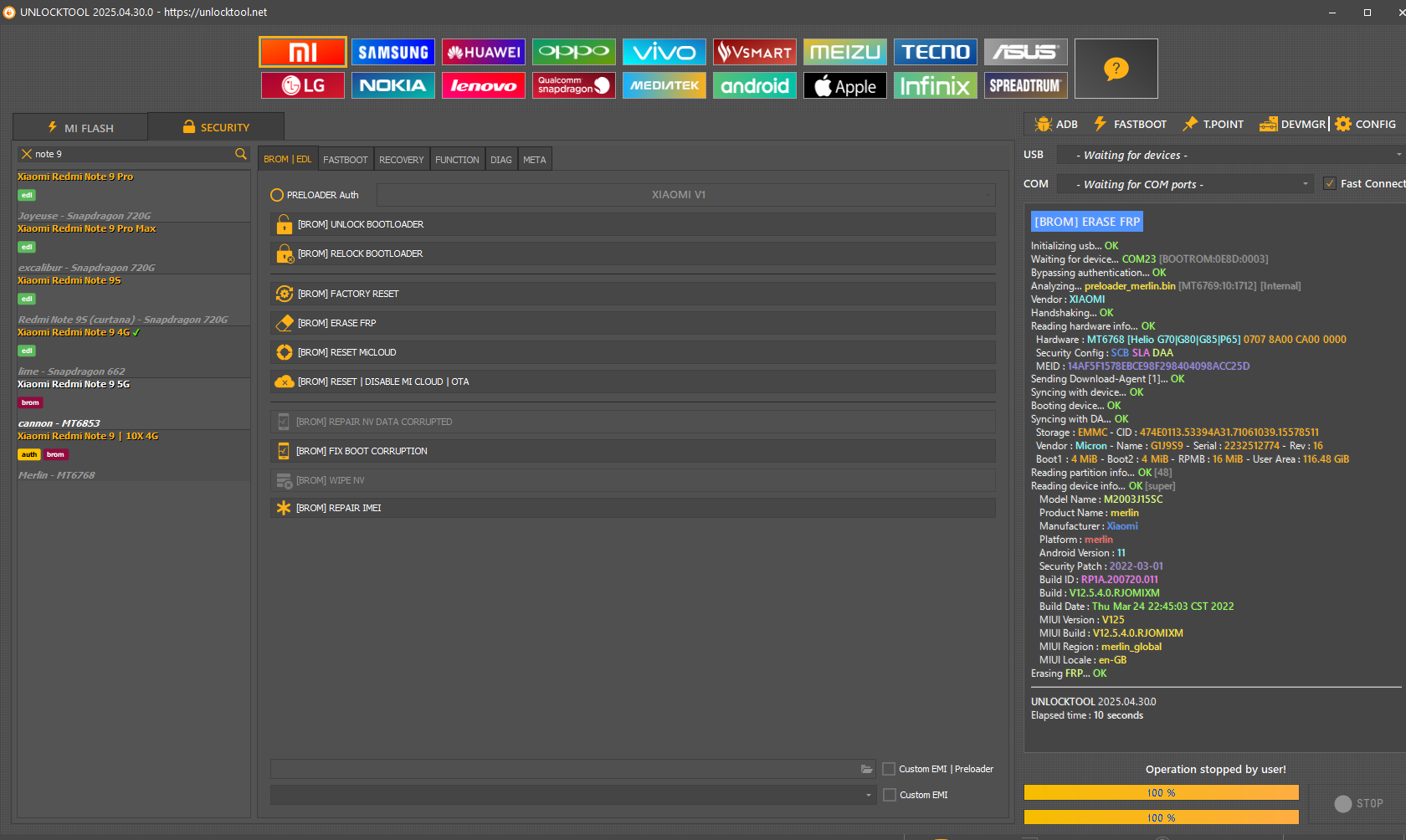
FRP Xiaomi Note 9 5G By Unlocktool
[BROM] ERASE FRP
Initializing usb...
OK
Waiting for device...
COM23
[BOOTROM:0E8D:0003]
Bypassing authentication...
OK
Analyzing...
preloader_merlin.bin [MT6769:10:1712] [Internal]
Vendor :
XIAOMI
Handshaking...
OK
Reading hardware info...
OK
Hardware :
MT6768 [Helio G70|G80|G85|P65]
0707
8A00
CA00
0000
Security Config :
SCB SLA DAA
MEID :
14AF5F1578EBCE98F298404098ACC25D
Sending Download-Agent [1]...
OK
Syncing with device...
OK
Booting device...
OK
Syncing with DA...
OK
Storage :
EMMC
- CID :
474E0113.53394A31.71061039.15578511
Vendor :
Micron
- Name :
G1J9S9
- Serial :
2232512774
- Rev :
16
Boot1 :
4 MiB
- Boot2 :
4 MiB
- RPMB :
16 MiB
- User Area :
116.48 GiB
Reading partition info...
OK
[48]
Reading device info...
OK
[super]
Model Name :
M2003J15SC
Product Name :
merlin
Manufacturer :
Xiaomi
Platform :
merlin
Android Version :
11
Security Patch :
2022-03-01
Build ID :
RP1A.200720.011
Build :
V12.5.4.0.RJOMIXM
Build Date :
Thu Mar 24 22:45:03 CST 2022
MIUI Version :
V125
MIUI Build :
V12.5.4.0.RJOMIXM
MIUI Region :
merlin_global
MIUI Locale :
en-GB
Erasing
FRP
...
OK
UNLOCKTOOL
2025.04.30.0
Elapsed time :
10 seconds
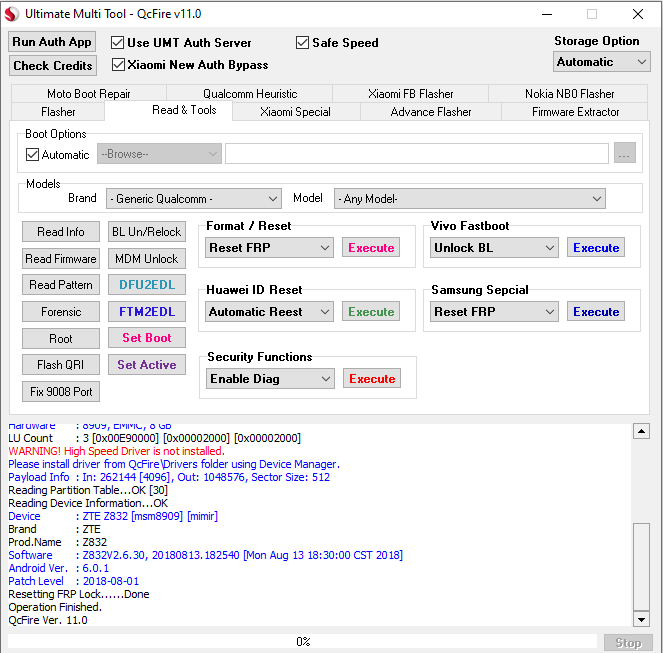
FRP ZTE Z832 By UMT Box
Enter FTM = Volumen Abajo + Encendido
$ adb reboot edl
# Qualcomm mode detected
Operation : Reset FRP
Checking for existing devices...Found
Port : Qualcomm HS-USB QDLoader 9008 (COM243)
Driver Info : Qualcomm Incorporated, qcusbser.sys, 2.1.4.1
Opening Port...OK
Init Handshake Sequence...OK
Hardware ID : E1009600 [8909] 00000400
OPK_DATA : 39B5FF24D131CBE6DFF161CD237FD1087FBC923F2174267E93C62FDF1ED5F076
Initializing Protocol...OK
Using Auto Loader Selection [1]
Preparing Loader...Done
Sending Loader [8909_040]...Done
Executing Loader...OK
Detecting Storage Type...OK
Hardware : 8909, EMMC, 8 GB
LU Count : 3 [0x00E90000] [0x00002000] [0x00002000]
WARNING! High Speed Driver is not installed.
Please install driver from QcFire\Drivers folder using Device Manager.
Payload Info : In: 262144 [4096], Out: 1048576, Sector Size: 512
Reading Partition Table...OK [30]
Reading Device Information...OK
Device : ZTE Z832 [msm8909] [mimir]
Brand : ZTE
Prod.Name : Z832
Software : Z832V2.6.30, 20180813.182540 [Mon Aug 13 18:30:00 CST 2018]
Android Ver. : 6.0.1
Patch Level : 2018-08-01
Resetting FRP Lock......Done
Operation Finished.
QcFire Ver. 11.0
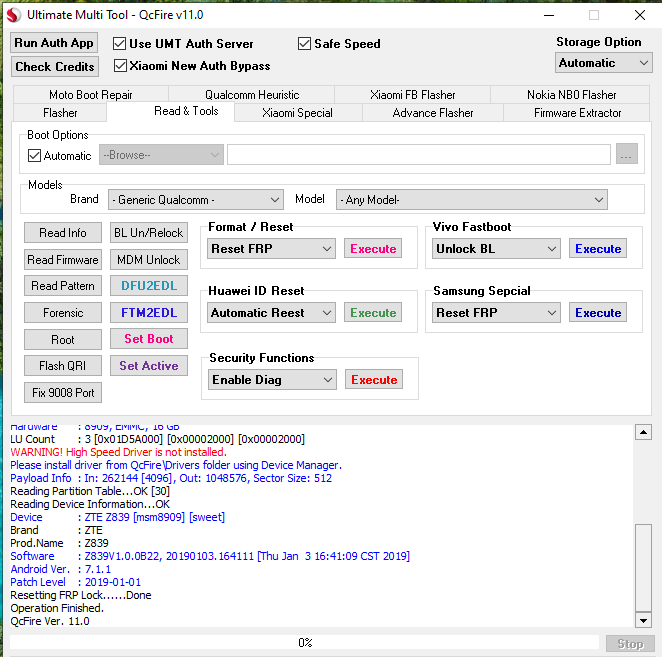
FRP ZTE Z839 by UMT Box
Enter FTM
$ adb reboot edl
# Qualcomm mode detected
Operation : Reset FRP
Checking for existing devices...Found
Port : Qualcomm HS-USB QDLoader 9008 (COM243)
Driver Info : Qualcomm Incorporated, qcusbser.sys, 2.1.4.1
Opening Port...OK
Init Handshake Sequence...OK
Hardware ID : E1009600 [8909] 00000400
OPK_DATA : A4F889863F66ABF67892BE4BFC68025AF5E25CB69AE2BAA25DFF4BCA141C5EBA
Initializing Protocol...OK
Using Auto Loader Selection [1]
Preparing Loader...Done
Sending Loader [8909_046]...Done
Executing Loader...OK
Detecting Storage Type...OK
Hardware : 8909, EMMC, 16 GB
LU Count : 3 [0x01D5A000] [0x00002000] [0x00002000]
WARNING! High Speed Driver is not installed.
Please install driver from QcFire\Drivers folder using Device Manager.
Payload Info : In: 262144 [4096], Out: 1048576, Sector Size: 512
Reading Partition Table...OK [30]
Reading Device Information...OK
Device : ZTE Z839 [msm8909] [sweet]
Brand : ZTE
Prod.Name : Z839
Software : Z839V1.0.0B22, 20190103.164111 [Thu Jan 3 16:41:09 CST 2019]
Android Ver. : 7.1.1
Patch Level : 2019-01-01
Resetting FRP Lock......Done
Operation Finished.
QcFire Ver. 11.0
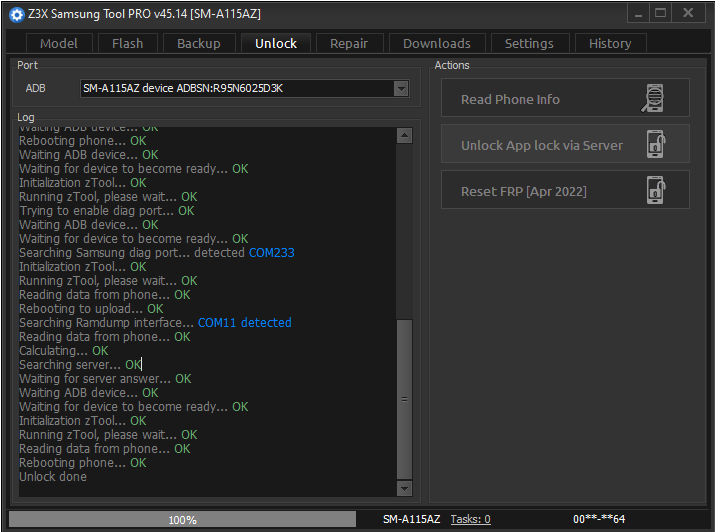
Direct Unlock Samsung SM-A115AZ Device Unlock Cricket by Z3X Samsung
Operation: Unlock
Selected model: SM-A115AZ
Software version: 45.14
Checking Login and Password... OK
Balance: 10 crd.
You have 10 credit(s) left. This operation takes 6 credits. Continue? Yes
Waiting ADB device... OK
Reading phone info...
Model: SM-A115AZ
Android version: 10
PDA version: A115AZTUU1ATF3
CSC version: A115AZAIO1ATF3
Phone version: A115AZTUU1ATF3
Product code: SM2A115AZKZAIO
CSC country code: USA
CSC sales code: AIO
Carrier ID: AIO
Phone SN: R95N6025D3K
IMEI: 355679111066587
HW version: REV1.0
RF cal date: 2020.06.10
Chip name: SDM450
Modem board: SDM450
Security patch: 2020-05-01
SIM State: NETWORK_LOCKED
Rebooting phone... OK
Waiting ADB device... OK
Rebooting phone... OK
Waiting ADB device... OK
Waiting for device to become ready... OK
Initialization zTool... OK
Running zTool, please wait... OK
Trying to enable diag port... OK
Waiting ADB device... OK
Waiting for device to become ready... OK
Searching Samsung diag port... detected COM233
Initialization zTool... OK
Running zTool, please wait... OK
Reading data from phone... OK
Rebooting to upload... OK
Searching Ramdump interface... COM11 detected
Reading data from phone... OK
Calculating... OK
Searching server... OK
Waiting for server answer... OK
Waiting ADB device... OK
Waiting for device to become ready... OK
Initialization zTool... OK
Running zTool, please wait... OK
Reading data from phone... OK
Rebooting phone... OK
Unlock done
Done with Samsung Tool PRO v.45.14 [SM-A115AZ,Unlock]
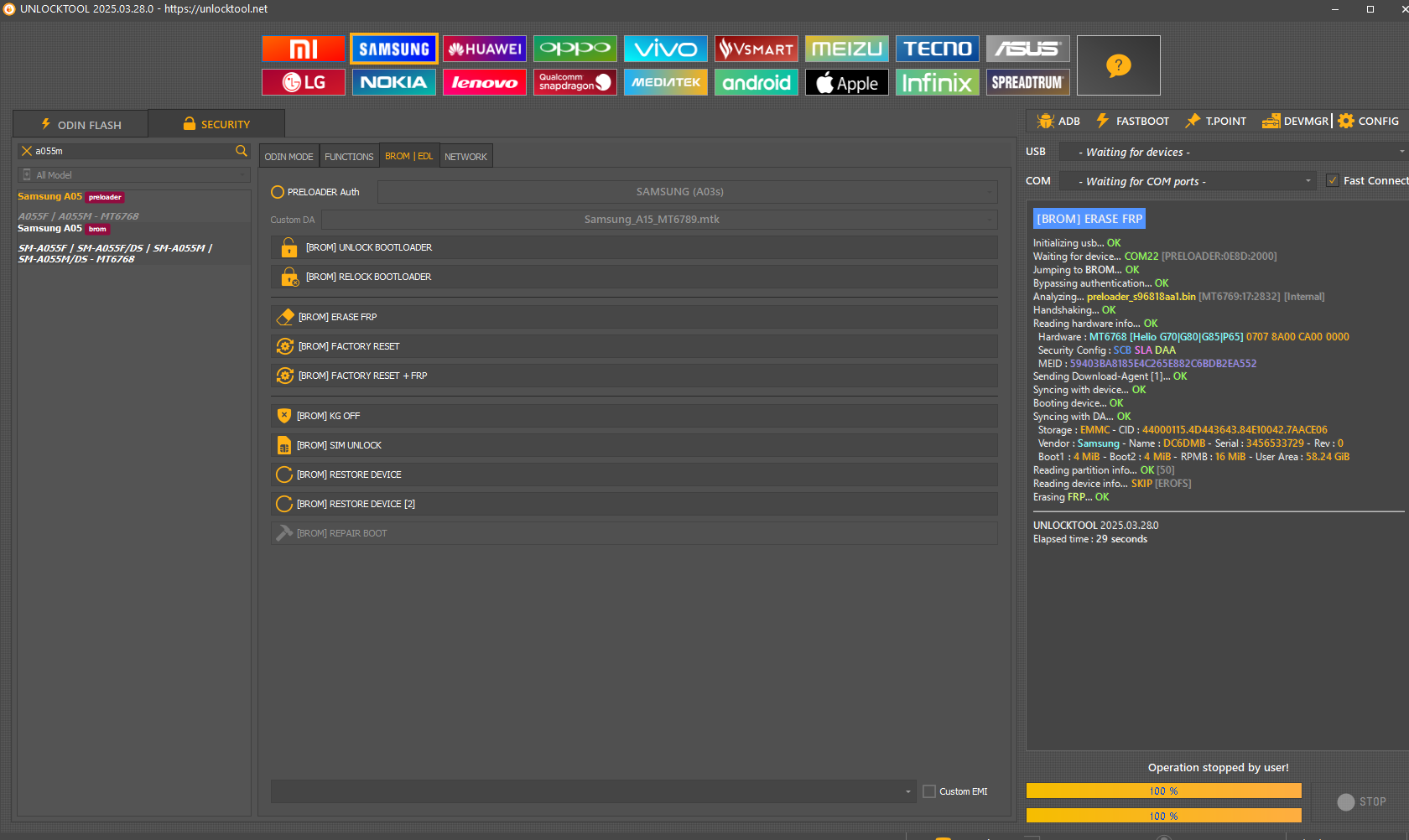
FRP Samsung SM-A055M by Unlocktool

[BROM] ERASE FRP
Initializing usb...
OK
Waiting for device...
COM22
[PRELOADER:0E8D:2000]
Jumping to
BROM
...
OK
Bypassing authentication...
OK
Analyzing...
preloader_s96818aa1.bin [MT6769:17:2832] [Internal]
Handshaking...
OK
Reading hardware info...
OK
Hardware :
MT6768 [Helio G70|G80|G85|P65]
0707
8A00
CA00
0000
Security Config :
SCB SLA DAA
MEID :
59403BA8185E4C265E882C6BDB2EA552
Sending Download-Agent [1]...
OK
Syncing with device...
OK
Booting device...
OK
Syncing with DA...
OK
Storage :
EMMC
- CID :
44000115.4D443643.84E10042.7AACE06
Vendor :
Samsung
- Name :
DC6DMB
- Serial :
3456533729
- Rev :
0
Boot1 :
4 MiB
- Boot2 :
4 MiB
- RPMB :
16 MiB
- User Area :
58.24 GiB
Reading partition info...
OK
[50]
Reading device info...
SKIP
[EROFS]
Erasing
FRP
...
OK
UNLOCKTOOL
2025.03.28.0
Elapsed time :
29 seconds
FRP Samsung SM-A032F
Realisar Test Point
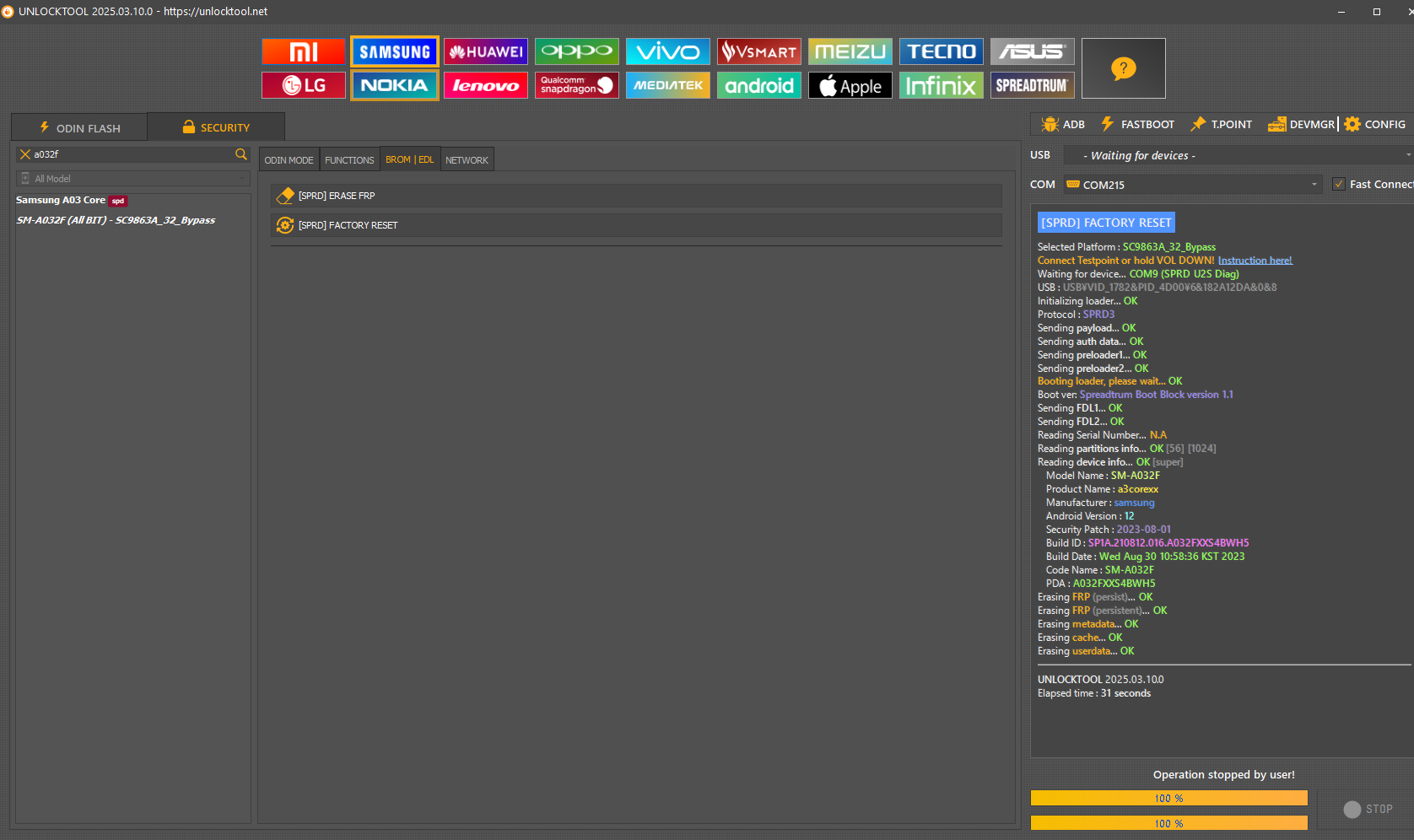
[SPRD] FACTORY RESET
Selected Platform :
SC9863A_32_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM9 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\6&182A12DA&0&8
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading Serial Number...
N.A
Reading
partitions info
...
OK
[56] [1024]
Reading
device info
...
OK
[super]
Model Name :
SM-A032F
Product Name :
a3corexx
Manufacturer :
samsung
Android Version :
12
Security Patch :
2023-08-01
Build ID :
SP1A.210812.016.A032FXXS4BWH5
Build Date :
Wed Aug 30 10:58:36 KST 2023
Code Name :
SM-A032F
PDA :
A032FXXS4BWH5
Erasing
FRP (persist)
...
OK
Erasing
FRP (persistent)
...
OK
Erasing
metadata
...
OK
Erasing
cache
...
OK
Erasing
userdata
...
OK
UNLOCKTOOL
2025.03.10.0
Elapsed time :
31 seconds
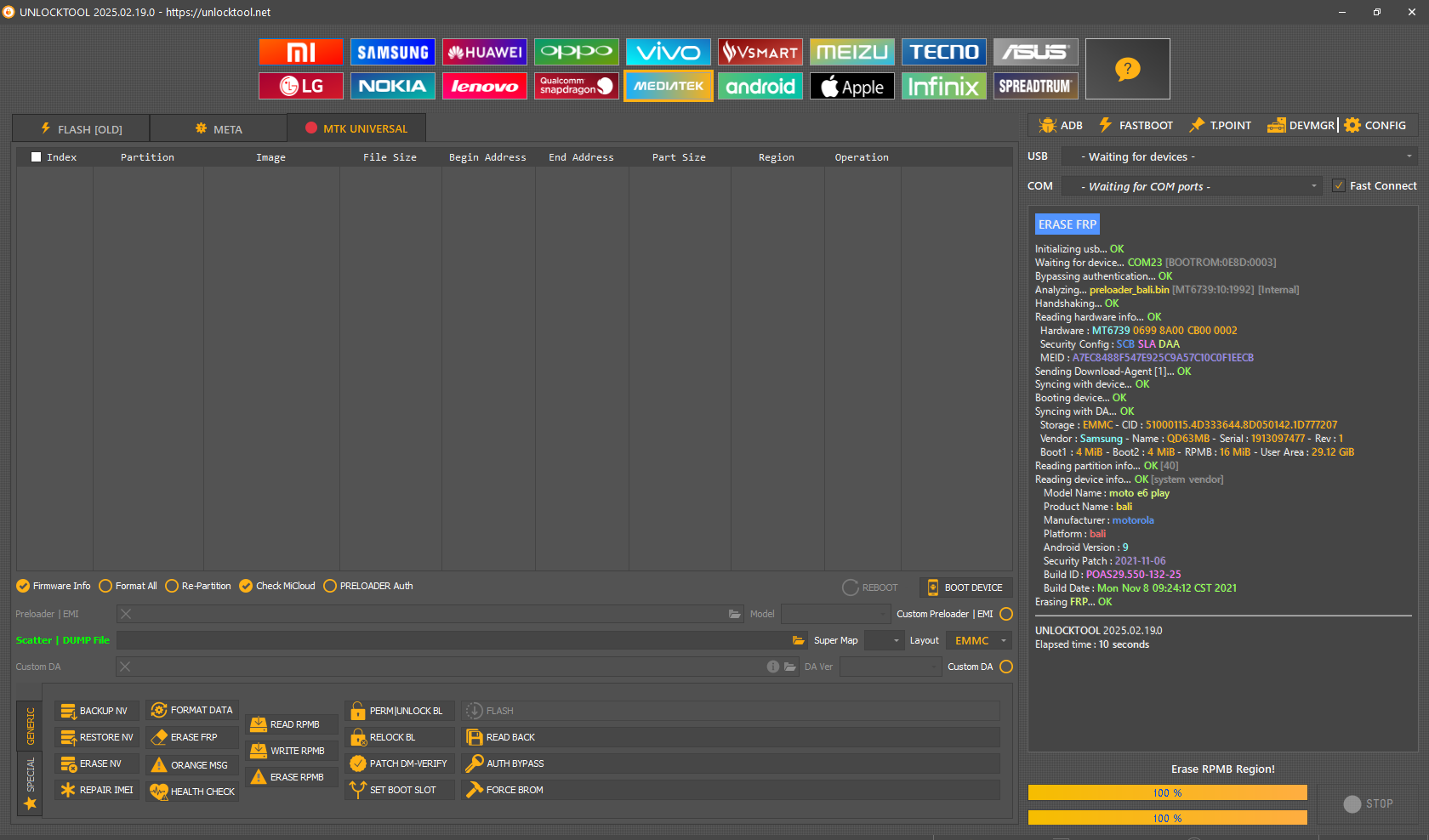
FRP Motorola E6 Play
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:003214 SourceURL:file%3a%2f%2f
ERASE FRP
Initializing usb...
OK
Waiting for device...
COM23
[BOOTROM:0E8D:0003]
Bypassing authentication...
OK
Analyzing...
preloader_bali.bin [MT6739:10:1992] [Internal]
Handshaking...
OK
Reading hardware info...
OK
Hardware :
MT6739
0699
8A00
CB00
0002
Security Config :
SCB SLA DAA
MEID :
A7EC8488F547E925C9A57C10C0F1EECB
Sending Download-Agent [1]...
OK
Syncing with device...
OK
Booting device...
OK
Syncing with DA...
OK
Storage :
EMMC
- CID :
51000115.4D333644.8D050142.1D777207
Vendor :
Samsung
- Name :
QD63MB
- Serial :
1913097477
- Rev :
1
Boot1 :
4 MiB
- Boot2 :
4 MiB
- RPMB :
16 MiB
- User Area :
29.12 GiB
Reading partition info...
OK
[40]
Reading device info...
OK
[system vendor]
Model Name :
moto e6 play
Product Name :
bali
Manufacturer :
motorola
Platform :
bali
Android Version :
9
Security Patch :
2021-11-06
Build ID :
POAS29.550-132-25
Build Date :
Mon Nov 8 09:24:12 CST 2021
Erasing
FRP
...
OK
UNLOCKTOOL
2025.02.19.0
Elapsed time :
10 seconds
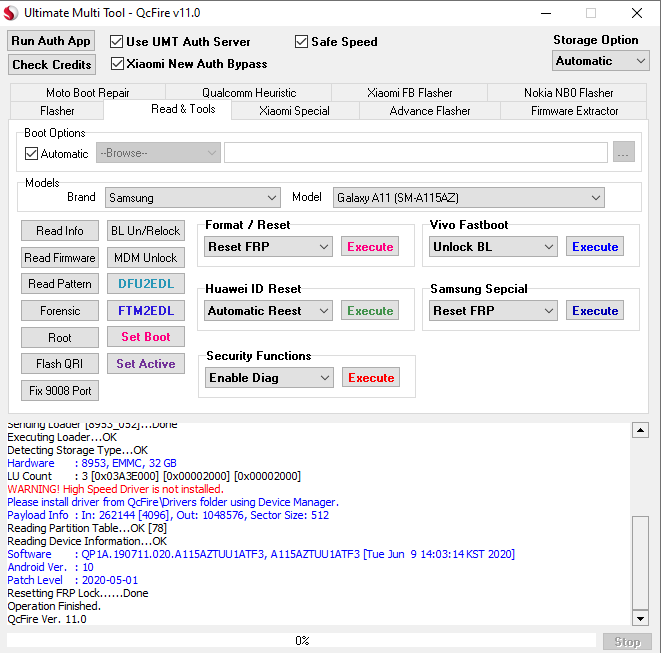
FRP Samsung SM-A115AZ Cricket by UMT BOX
Test Point

Device : Samsung Galaxy A11 (SM-A115AZ)
Operation : Reset FRP
Checking for existing devices...Found
Port : Qualcomm HS-USB QDLoader 9008 (COM93)
Driver Info : Qualcomm Incorporated, qcusbser.sys, 2.1.4.1
Opening Port...OK
Init Handshake Sequence...OK
Hardware ID : E1A00900 [8953] 00002000
OPK_DATA : CCC81D1E9F542D37EF3BBF0FBDB5DEC36A8EEBB41F832FEDE2292294DCB94B0A
Initializing Protocol...OK
Using Auto Loader Selection [1]
Preparing Loader...Done
Sending Loader [8953_052]...Done
Executing Loader...OK
Detecting Storage Type...OK
Hardware : 8953, EMMC, 32 GB
LU Count : 3 [0x03A3E000] [0x00002000] [0x00002000]
WARNING! High Speed Driver is not installed.
Please install driver from QcFire\Drivers folder using Device Manager.
Payload Info : In: 262144 [4096], Out: 1048576, Sector Size: 512
Reading Partition Table...OK [78]
Reading Device Information...OK
Software : QP1A.190711.020.A115AZTUU1ATF3, A115AZTUU1ATF3 [Tue Jun 9 14:03:14 KST 2020]
Android Ver. : 10
Patch Level : 2020-05-01
Resetting FRP Lock......Done
Operation Finished.
QcFire Ver. 11.0
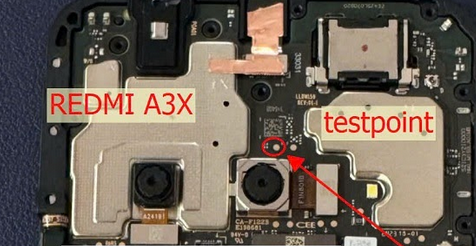
FRP Redmi A3X By Unlock Tool
Connect Test Point
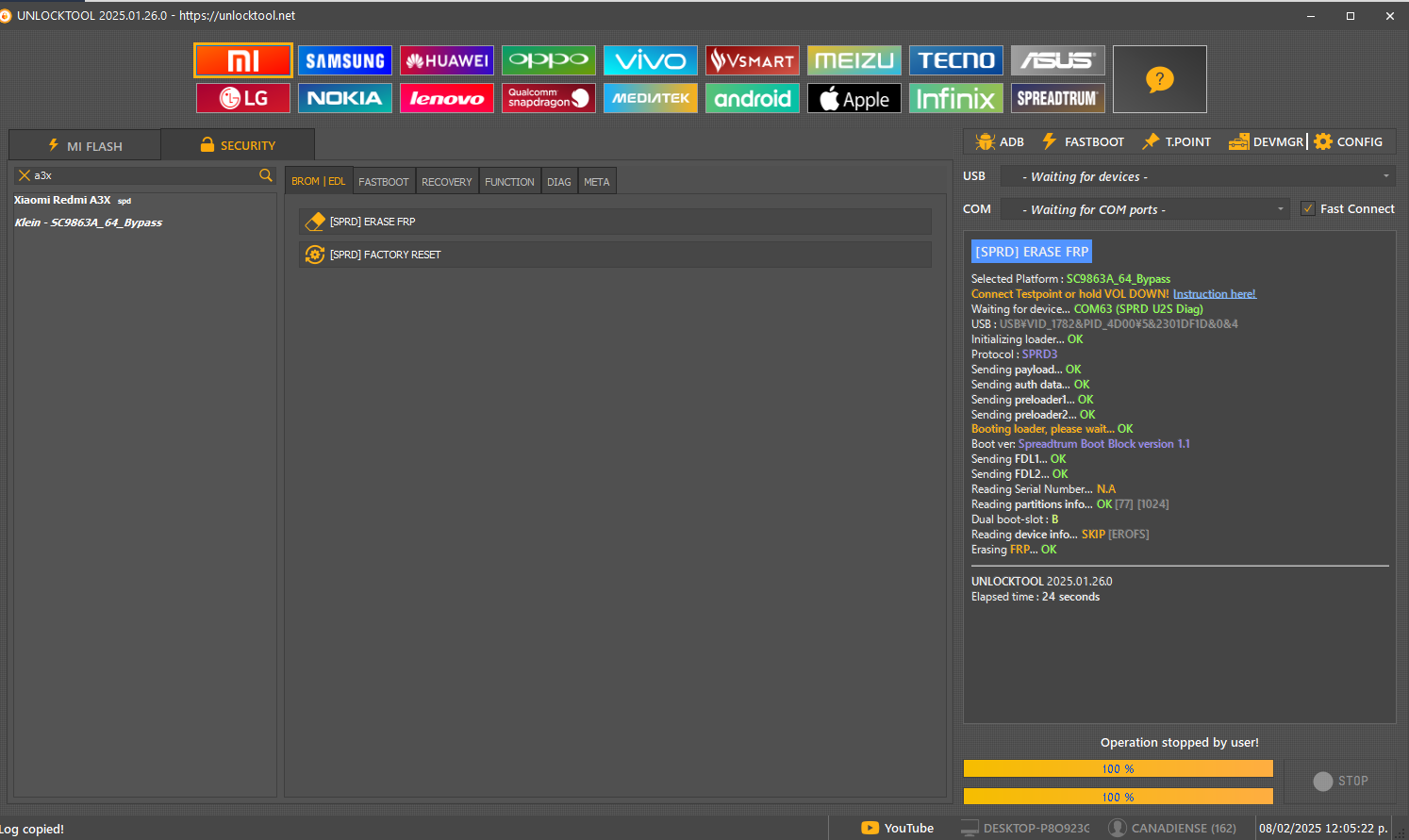
[SPRD] ERASE FRP
Selected Platform :
SC9863A_64_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM63 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\5&2301DF1D&0&4
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading Serial Number...
N.A
Reading
partitions info
...
OK
[77] [1024]
Dual boot-slot :
B
Reading
device info
...
SKIP
[EROFS]
Erasing
FRP
...
OK
UNLOCKTOOL
2025.01.26.0
Elapsed time :
24 seconds
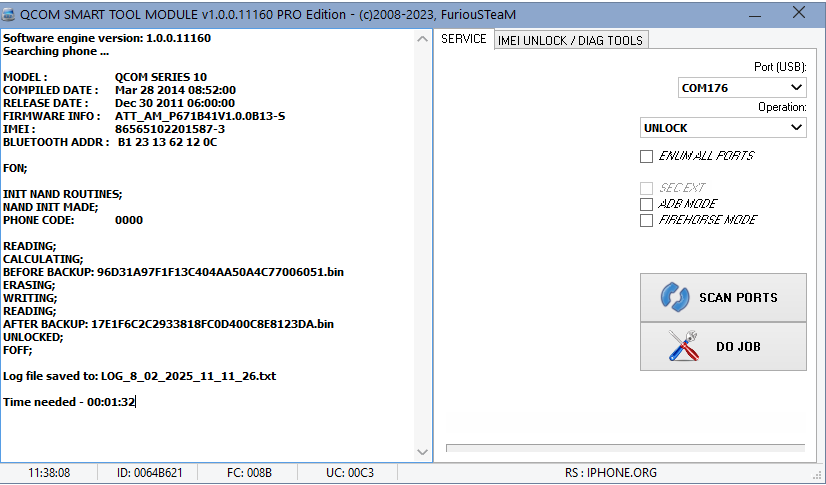
ZTE Z222 by Furious Gold
Software engine version: 1.0.0.11160
Searching phone ...
MODEL : QCOM SERIES 10
COMPILED DATE : Mar 28 2014 08:52:00
RELEASE DATE : Dec 30 2011 06:00:00
FIRMWARE INFO : ATT_AM_P671B41V1.0.0B13-S
IMEI : 86565102201587-3
BLUETOOTH ADDR : B1 23 13 62 12 0C
FON;
INIT NAND ROUTINES;
NAND INIT MADE;
PHONE CODE: 0000
READING;
CALCULATING;
BEFORE BACKUP: 96D31A97F1F13C404AA50A4C77006051.bin
ERASING;
WRITING;
READING;
AFTER BACKUP: 17E1F6C2C2933818FC0D400C8E8123DA.bin
UNLOCKED;
FOFF;
Log file saved to: LOG_8_02_2025_11_11_26.txt
Time needed - 00:01:32
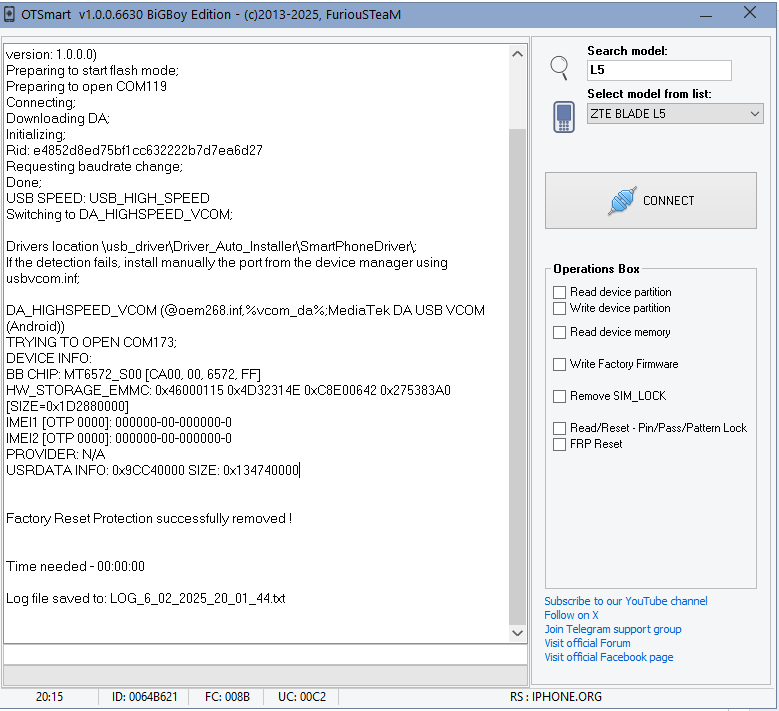
FRP ZTE BLADE L5 by Furious Gold
Using library Brom_DLL_v7.1522.2
Engine version 1.0.0.6630
Searching phone in normal mode;
[connect the phone powered off to the usb cable]
Phone detected (MediaTek PreLoader USB VCOM (Android) (COM119)) (Driver version: 1.0.0.0)
Preparing to start flash mode;
Preparing to open COM119
Connecting;
Downloading DA;
Initializing;
Rid: e4852d8ed75bf1cc632222b7d7ea6d27
Requesting baudrate change;
Done;
USB SPEED: USB_HIGH_SPEED
Switching to DA_HIGHSPEED_VCOM;
Drivers location \usb_driver\Driver_Auto_Installer\SmartPhoneDriver\;
If the detection fails, install manually the port from the device manager using usbvcom.inf;
DA_HIGHSPEED_VCOM (@oem268.inf,%vcom_da%;MediaTek DA USB VCOM (Android))
TRYING TO OPEN COM173;
DEVICE INFO:
BB CHIP: MT6572_S00 [CA00, 00, 6572, FF]
HW_STORAGE_EMMC: 0x46000115 0x4D32314E 0xC8E00642 0x275383A0 [SIZE=0x1D2880000]
IMEI1 [OTP 0000]: 000000-00-000000-0
IMEI2 [OTP 0000]: 000000-00-000000-0
PROVIDER: N/A
USRDATA INFO: 0x9CC40000 SIZE: 0x134740000
Factory Reset Protection successfully removed !
Time needed - 00:00:00
Log file saved to: LOG_6_02_2025_20_01_44.txt
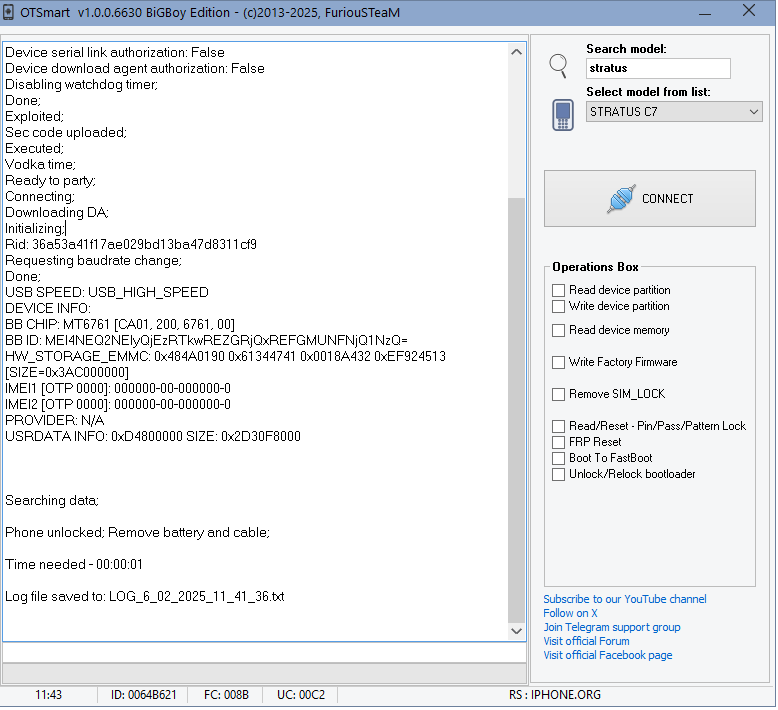
Direct Unlock Stratus C7 by Furious Gold
Using library Brom_DLL_v7.1813.3
Engine version 1.0.0.6630
Searching phone in normal mode;
[connect the phone powered off with volume down and up pressed to the usb cable]
Phone detected (MediaTek USB Port (COM136)) (Driver version: 3.0.1504.0)
Preparing to start flash mode;
Preparing to open COM136
Device hw code: 0717
Device hw sub code: 8A00
Device hw version: CA01
Device sw version: 0200
Device secure boot: False
Device serial link authorization: False
Device download agent authorization: False
Disabling watchdog timer;
Done;
Exploited;
Sec code uploaded;
Executed;
Vodka time;
Ready to party;
Connecting;
Downloading DA;
Initializing;
Rid: 36a53a41f17ae029bd13ba47d8311cf9
Requesting baudrate change;
Done;
USB SPEED: USB_HIGH_SPEED
DEVICE INFO:
BB CHIP: MT6761 [CA01, 200, 6761, 00]
BB ID: MEI4NEQ2NEIyQjEzRTkwREZGRjQxREFGMUNFNjQ1NzQ=
HW_STORAGE_EMMC: 0x484A0190 0x61344741 0x0018A432 0xEF924513 [SIZE=0x3AC000000]
IMEI1 [OTP 0000]: 000000-00-000000-0
IMEI2 [OTP 0000]: 000000-00-000000-0
PROVIDER: N/A
USRDATA INFO: 0xD4800000 SIZE: 0x2D30F8000
Searching data;
Phone unlocked; Remove battery and cable;
Time needed - 00:00:01
Log file saved to: LOG_6_02_2025_11_41_36.txt
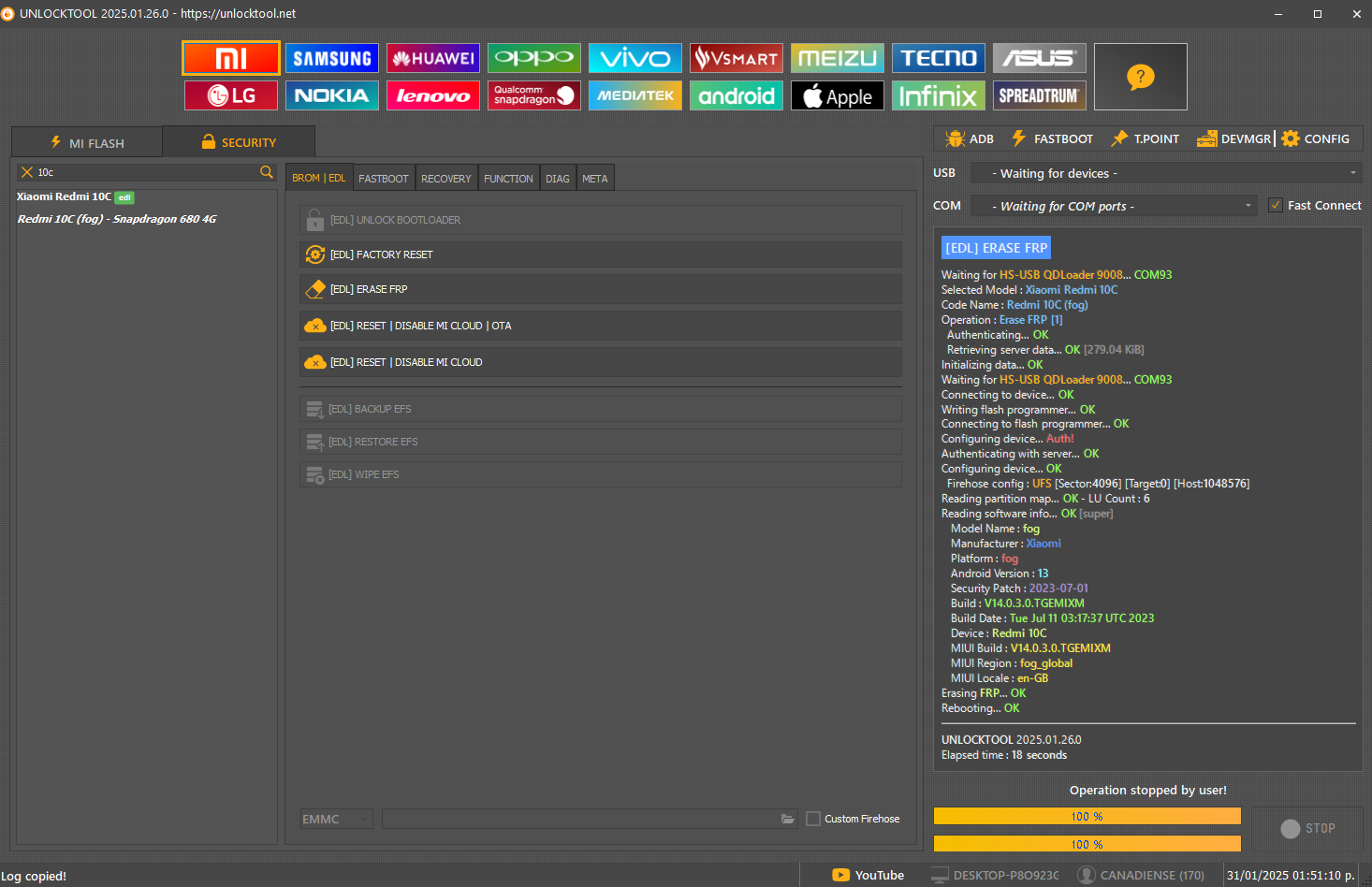
FRP Xiaomi Redmi 10C by Unlocktool
Conectar Test Point primero
[EDL] ERASE FRP
Waiting for
HS-USB QDLoader 9008
...
COM93
Selected Model :
Xiaomi Redmi 10C
Code Name :
Redmi 10C (fog)
Operation :
Erase FRP [1]
Authenticating...
OK
Retrieving server data...
OK
[279.04 KiB]
Initializing data...
OK
Waiting for
HS-USB QDLoader 9008
...
COM93
Connecting to device...
OK
Writing flash programmer...
OK
Connecting to flash programmer...
OK
Configuring device...
Auth!
Authenticating with server...
OK
Configuring device...
OK
Firehose config :
UFS
[Sector:
4096
] [Target:
0
] [Host:
1048576
]
Reading partition map...
OK
- LU Count :
6
Reading software info...
OK
[super]
Model Name :
fog
Manufacturer :
Xiaomi
Platform :
fog
Android Version :
13
Security Patch :
2023-07-01
Build :
V14.0.3.0.TGEMIXM
Build Date :
Tue Jul 11 03:17:37 UTC 2023
Device :
Redmi 10C
MIUI Build :
V14.0.3.0.TGEMIXM
MIUI Region :
fog_global
MIUI Locale :
en-GB
Erasing
FRP
...
OK
Rebooting...
OK
UNLOCKTOOL
2025.01.26.0
Elapsed time :
18 seconds
Zeus Project Tool - Reseller Oficial en Mexico & Latin America
UNLOCK.MX
Reseller Oficial en Mexico & Latin America
Zeus Project Tool
Licencia - 3, 6 , 12 Meses
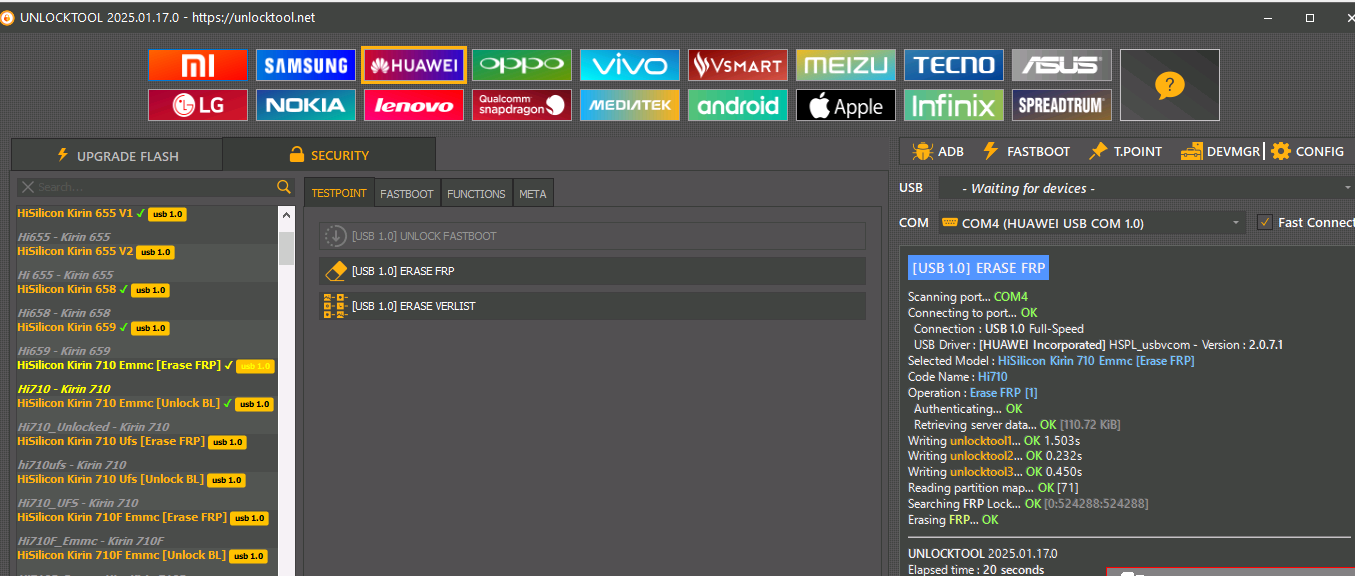
FRP Huawei P30 Lite HiSilicon Kirin 710
[USB 1.0] ERASE FRP Scanning port... COM4
Connecting to port... OK
Connection : USB 1.0 Full-Speed
USB Driver : [HUAWEI Incorporated] HSPL_usbvcom - Version : 2.0.7.1
Selected Model : HiSilicon Kirin 710 Emmc [Erase FRP]
Code Name : Hi710
Operation : Erase FRP [1]
Authenticating... OK
Retrieving server data... OK [110.72 KiB]
Writing unlocktool1... OK 1.503s
Writing unlocktool2... OK 0.232s
Writing unlocktool3... OK 0.450s
Reading partition map... OK [71]
Searching FRP Lock... OK [0:524288:524288]
Erasing FRP... OK
UNLOCKTOOL 2025.01.17.0
Elapsed time : 20 seconds
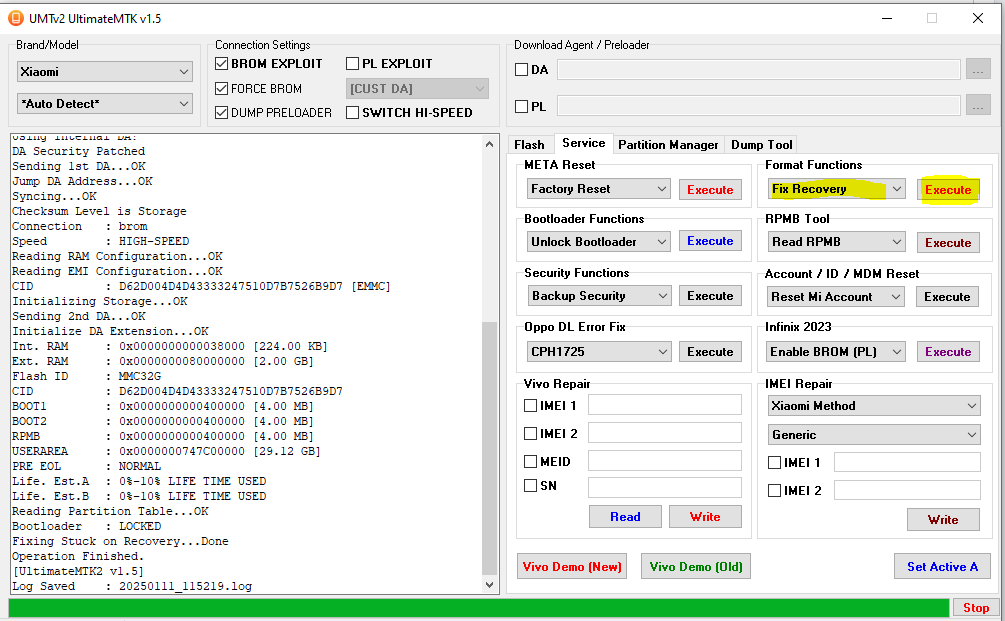
Redmi A2 Xiaomi Fix Recovery with UMT MTK
Redmi A2 Stock Recovery Mode
Brand/Model : Xiaomi / *Auto Detect*
Operation : Fix Recovery
BOOT CFG : [BROM EXPLOIT : ON]
Waiting for Device...Found
Port : MediaTek USB Port (COM144)
Device Path : \\?\usb#vid_0e8d&pid_0003#6&38a36d0c&0&5#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver : MediaTek Inc., 3.0.1504.0 [usb2ser.sys]
Mode : BROM
Hw ID : MT6765 [0766] Helio P35/G35
Details : 8A00,CA00,0000
Sec. Config : [SBA:True] [SLA:True] [DAA:True]
MEID : 3D1A8AAFCB81FE8A75B9FA250930CD4F
SoC ID[0] : 5A341E2881E5A77AE5D35B3CC8D184A5
SoC ID[1] : CE0C4FB539C1E2D1B02BD7B2D77B75BC
Running Exploit...Done
Downloading Preloader...OK
Saved as : preloader_water.bin
Loading EMI Config from Preloader...OK
Sec. Config : [SBA:False] [SLA:False] [DAA:False]
Using Internal DA!
DA Security Patched
Sending 1st DA...OK
Jump DA Address...OK
Syncing...OK
Checksum Level is Storage
Connection : brom
Speed : HIGH-SPEED
Reading RAM Configuration...OK
Reading EMI Configuration...OK
CID : D62D004D4D43333247510D7B7526B9D7 [EMMC]
Initializing Storage...OK
Sending 2nd DA...OK
Initialize DA Extension...OK
Int. RAM : 0x0000000000038000 [224.00 KB]
Ext. RAM : 0x0000000080000000 [2.00 GB]
Flash ID : MMC32G
CID : D62D004D4D43333247510D7B7526B9D7
BOOT1 : 0x0000000000400000 [4.00 MB]
BOOT2 : 0x0000000000400000 [4.00 MB]
RPMB : 0x0000000000400000 [4.00 MB]
USERAREA : 0x0000000747C00000 [29.12 GB]
PRE EOL : NORMAL
Life. Est.A : 0%-10% LIFE TIME USED
Life. Est.B : 0%-10% LIFE TIME USED
Reading Partition Table...OK
Bootloader : LOCKED
Fixing Stuck on Recovery...Done
Operation Finished.
[UltimateMTK2 v1.5]
Log Saved : 20250111_115219.log
FRP Tablet Samsung SM-P610 Android 11
Primero seleccionar Android MTP y seleccionar open youtube url y abrir Chrome
Url para abrir menu
https://frpbypass.romstage.com/
Seleccionar Open dial pad

Marcar: asterisco # 0 # asterisco y seleccionar REMOVE FRP 2023 ALL METHODS
[COM] REMOVE FRP [2023] Scanning for device... COM9
Reading Info... FAIL
Connecting to device... OK
Trying method [1]... FAIL
Trying method [2]... FAIL
Trying method [3]... OK
Waiting for device...
Please accept USB Debugging on your phone!
Model : SM-P610
Manufacturer : samsung
Platform : universal9611
CPU Arch : arm64-v8a
Android Serial : R52R40FGZGW
Security Patch : 2021-05-01
Connection : mtp,adb
Timezone : America/Mexico_City
Android Version : 11
Android SDK : 30
Build : RP1A.200720.012.P610XXU2CUE1
Build Date : Wed May 5 15:49:46 +07 2021
Product Code : SM-P610NZAAITV
Device Name : gta4xlwifi
Product Name : gta4xlwifixx
Code Name : SM-P610NZAAITV
BL : P610XXU2CUE1
PDA : P610XXU2CUE1
CSC : P610OXM2CUE2
Sales Code : ITV
Removing FRP... OK
UNLOCKTOOL 2025.01.06.0
Elapsed time : 1 minute 6 seconds
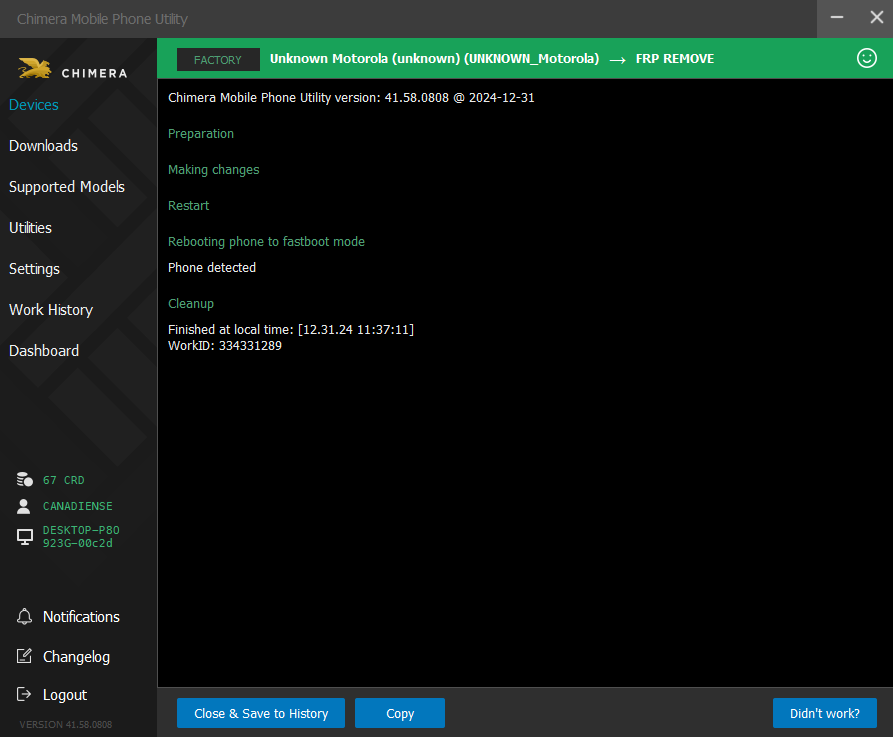
FRP Motorola one XT1941-5 by Chimera
Presiona volumen abajo + cable + encendido para entrar en Fastboot
despues seleccionar Factory Mode
seleccionar FRP
Chimera Mobile Phone Utility version: 41.58.0808 @ 2024-12-31
Preparation
Making changes
Restart
Rebooting phone to fastboot mode
Phone detected
Cleanup
Finished at local time: [12.31.24 11:37:11]
WorkID: 334331289
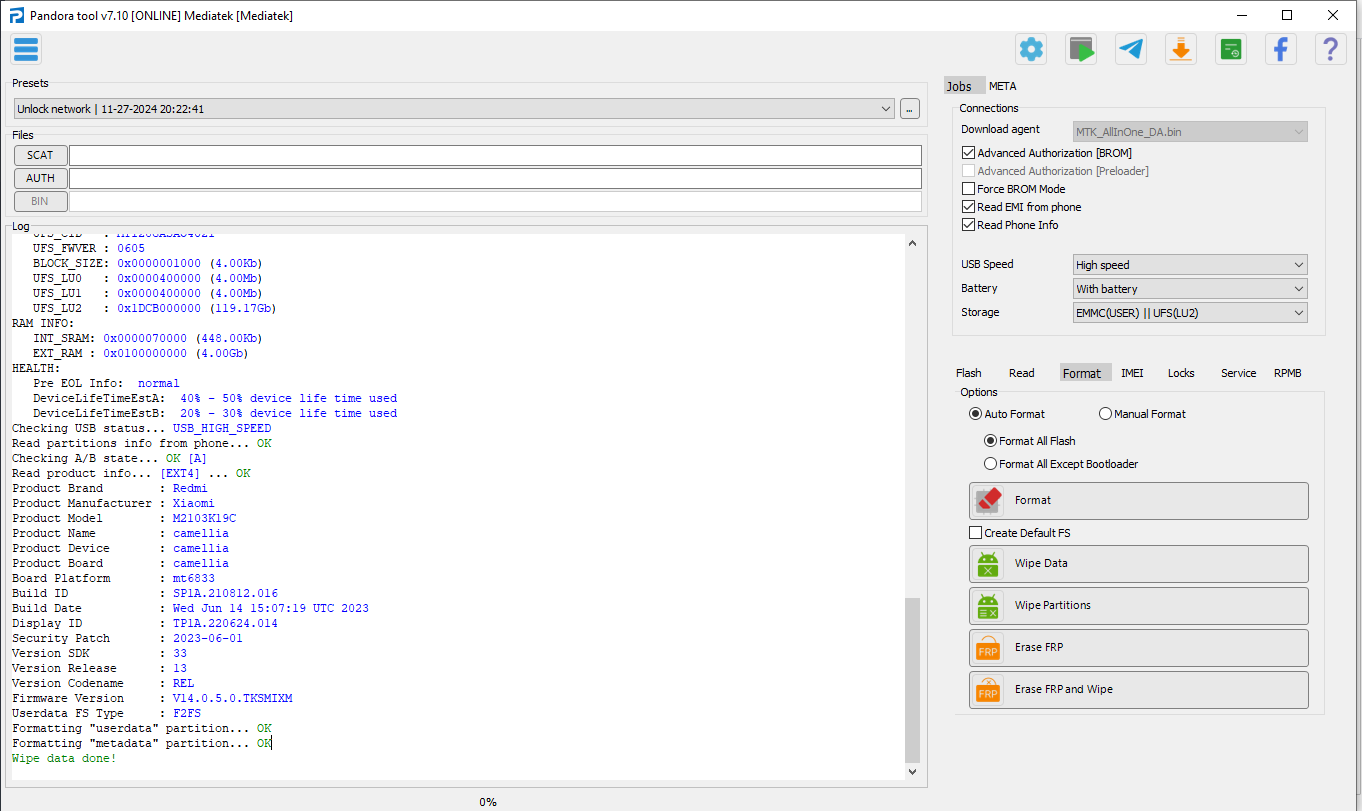
FRP ZTE Blade V10 Vita Spreadtrum SC9863A_64 by Pandora Box
Selected model: Spreadtrum Spreadtrum
Select->SC9863A_64
Operation: Erase FRP And Wipe
Software version: 7.10
Work ID: 55225623
Connect phone in BROM mode. Use volume key buttons or testpoint.
Waiting for device... OK
Device found at COM121
Port: USB\VID_1782&PID_4D00\6&38A36D0C&0&6
Driver: [UNISOC Communications Inc.,sprdvcom,SPRD U2S Diag,sprdvcom.sys,4.19.38.134]
Port type: BROM
Connecting to device... OK
Selected processor: SC9863A_64
Load files... (universal) OK
Connect preloader 1... OK
Connect preloader 2... OK
Connect loader 1... OK
Connect loader 2... OK
Serial Number: 726474003460
Read partitions info... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : ZTE
Product Manufacturer : ZTE
Product Model : ZTE Blade V10 Vita
Product Name : ZTE_Blade_V10_Vita
Product Device : P963F01
Product Board : sprout
Board Platform : sp9863a
Build ID : PPR1.180610.011
Build Date : Fri Apr 21 12:42:11 CST 2023
Display ID : TEL_MX_ZTE_Blade_V10_VitaV1.14
Security Patch : 2022-03-01
Version SDK : 28
Version Release : 9
Version Codename : REL
Firmware Version : 20230421.124235
Userdata FS Type : F2FS
Backup partitions... OK
Formatting "persist" partition... OK
Formatting "userdata" partition... OK
Formatting "cache" partition... OK
Formatting "metadata" partition... not found, skip
Creating default filesystems... [CACHE: EXT4] ... [USERDATA: F2FS] ... OK
Done!

FRP Redmi Note 10 5G
Selected model: Mediatek Mediatek
Operation: Wipe Data
Software version: 7.10
There is a risk of data loss.
This procedure will erase all User Data
Make sure that you have a backup created. Continue? YES
Work ID: 54541577
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,USBSER.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM136 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0989
Get sec config... OK [000000E7]
Active sec flags: [SBC SLA DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6833]
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,USBSER.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM136 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0989
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6833]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xF0C6391A, 0xA2A3305A, 0x99D1BA4D, 0x7F3BF8EC
Get Chip ID... [MT6833]
Get SOC ID... [35EE8E5A09EDFC02D95B196FDD96F752B3ECF20EE121900BFCF44E086995CDB5]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [14]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
UFS CID (FW VER): MT128GASAO4U21 (0605)
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
UFS INFO:
UFS_CID : MT128GASAO4U21
UFS_FWVER : 0605
BLOCK_SIZE: 0x0000001000 (4.00Kb)
UFS_LU0 : 0x0000400000 (4.00Mb)
UFS_LU1 : 0x0000400000 (4.00Mb)
UFS_LU2 : 0x1DCB000000 (119.17Gb)
RAM INFO:
INT_SRAM: 0x0000070000 (448.00Kb)
EXT_RAM : 0x0100000000 (4.00Gb)
HEALTH:
Pre EOL Info: normal
DeviceLifeTimeEstA: 40% - 50% device life time used
DeviceLifeTimeEstB: 20% - 30% device life time used
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK [A]
Read product info... [EXT4] ... OK
Product Brand : Redmi
Product Manufacturer : Xiaomi
Product Model : M2103K19C
Product Name : camellia
Product Device : camellia
Product Board : camellia
Board Platform : mt6833
Build ID : SP1A.210812.016
Build Date : Wed Jun 14 15:07:19 UTC 2023
Display ID : TP1A.220624.014
Security Patch : 2023-06-01
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : V14.0.5.0.TKSMIXM
Userdata FS Type : F2FS
Formatting "userdata" partition... OK
Formatting "metadata" partition... OK
Formatting "frp" partition... OK
Wipe data done!
FRP data done!
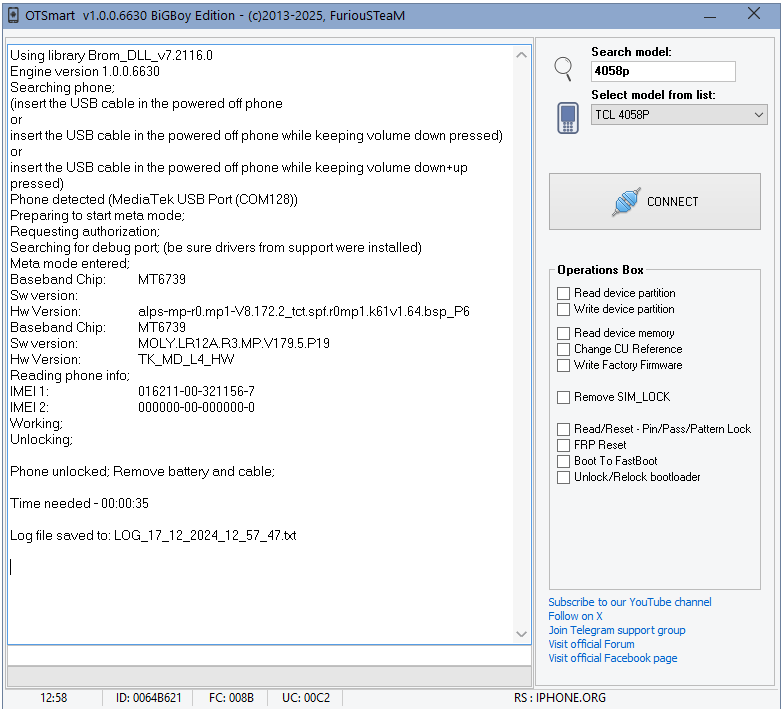
Unlock TCL 4058P by Furious Gold
Using library Brom_DLL_v7.2116.0
Engine version 1.0.0.6630
Searching phone;
(insert the USB cable in the powered off phone
or
insert the USB cable in the powered off phone while keeping volume down pressed)
or
insert the USB cable in the powered off phone while keeping volume down+up pressed)
Phone detected (MediaTek USB Port (COM128))
Preparing to start meta mode;
Requesting authorization;
Searching for debug port; (be sure drivers from support were installed)
Meta mode entered;
Baseband Chip: MT6739
Sw version:
Hw Version: alps-mp-r0.mp1-V8.172.2_tct.spf.r0mp1.k61v1.64.bsp_P6
Baseband Chip: MT6739
Sw version: MOLY.LR12A.R3.MP.V179.5.P19
Hw Version: TK_MD_L4_HW
Reading phone info;
IMEI 1: 016211-00-321156-7
IMEI 2: 000000-00-000000-0
Working;
Unlocking;
Phone unlocked; Remove battery and cable;
Time needed - 00:00:35
Log file saved to: LOG_17_12_2024_12_57_47.txt
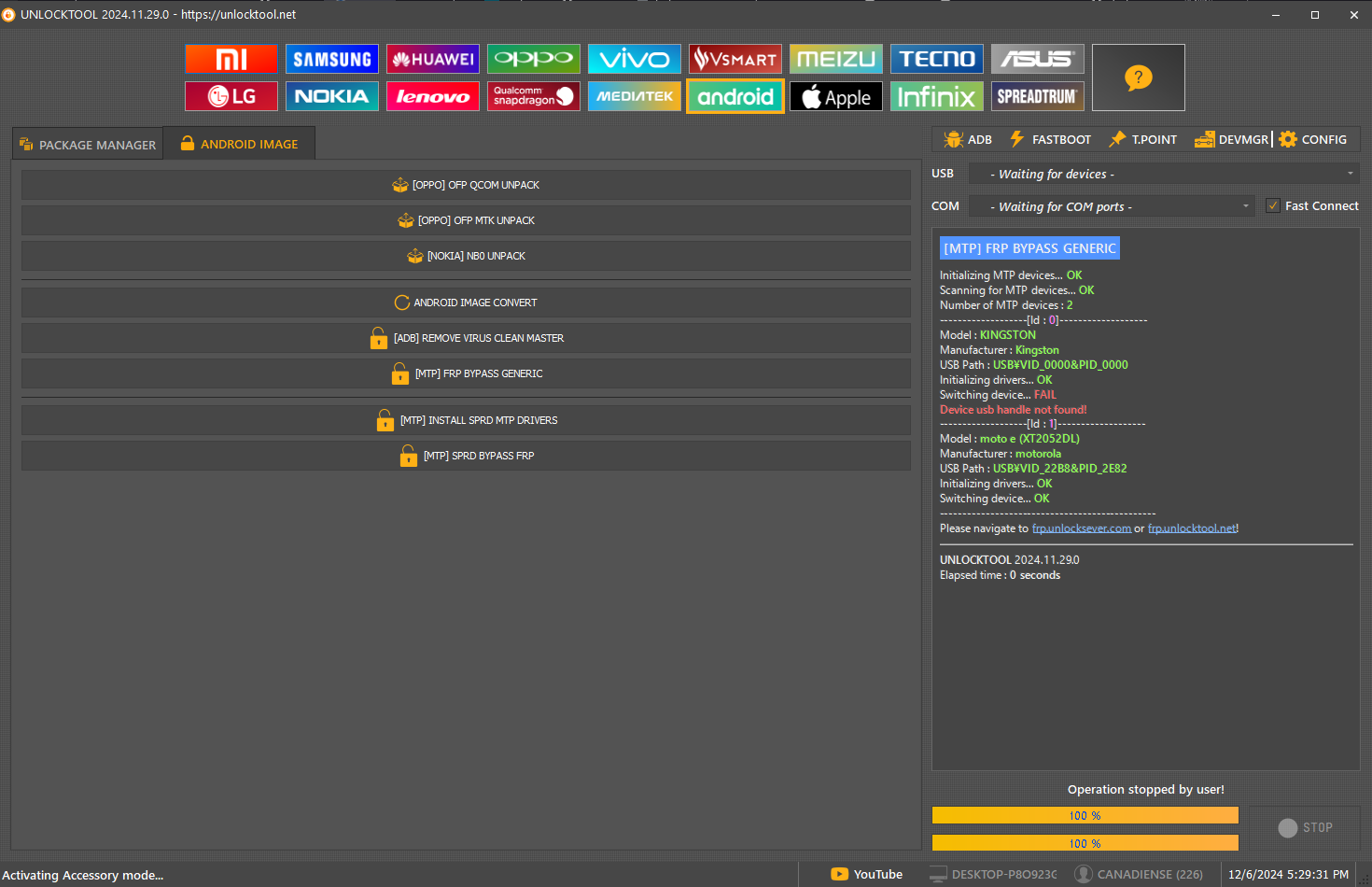
FRP Moto e (XT2052DL)
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:001724 SourceURL:file%3a%2f%2f
[MTP] FRP BYPASS GENERIC
Initializing MTP devices...
OK
Scanning for MTP devices...
OK
Number of MTP devices :
2
-------------------[Id :
0
]-------------------
Model :
KINGSTON
Manufacturer :
Kingston
USB Path :
USB\VID_0000&PID_0000
Initializing drivers...
OK
Switching device...
FAIL
Device usb handle not found!
-------------------[Id :
1
]-------------------
Model :
moto e (XT2052DL)
Manufacturer :
motorola
USB Path :
USB\VID_22B8&PID_2E82
Initializing drivers...
OK
Switching device...
OK
-----------------------------------------------
Please navigate to
or
!
UNLOCKTOOL
2024.11.29.0
Elapsed time :
0 seconds
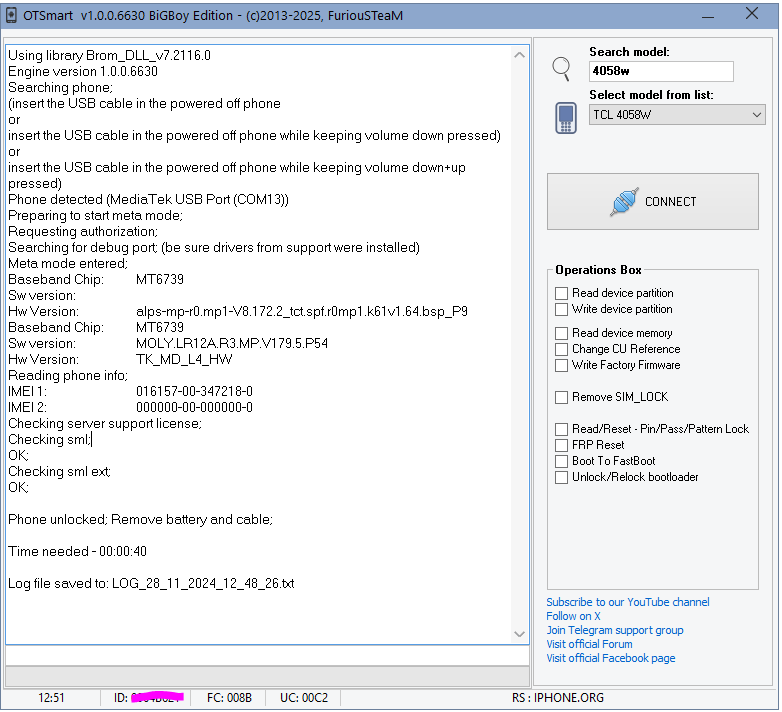
Direct Unlock TCL 4058W by Furious Gold Box
Alcatel TCL 4058W Device Unlock T-mobile
Using library Brom_DLL_v7.2116.0
Engine version 1.0.0.6630
Searching phone;
(insert the USB cable in the powered off phone
or
insert the USB cable in the powered off phone while keeping volume down pressed)
or
insert the USB cable in the powered off phone while keeping volume down+up pressed)
Phone detected (MediaTek USB Port (COM13))
Preparing to start meta mode;
Requesting authorization;
Searching for debug port; (be sure drivers from support were installed)
Meta mode entered;
Baseband Chip: MT6739
Sw version:
Hw Version: alps-mp-r0.mp1-V8.172.2_tct.spf.r0mp1.k61v1.64.bsp_P9
Baseband Chip: MT6739
Sw version: MOLY.LR12A.R3.MP.V179.5.P54
Hw Version: TK_MD_L4_HW
Reading phone info;
IMEI 1: 016157-00-347218-0
IMEI 2: 000000-00-000000-0
Checking server support license;
Checking sml;
OK;
Checking sml ext;
OK;
Phone unlocked; Remove battery and cable;
Time needed - 00:00:40
Log file saved to: LOG_28_11_2024_12_48_26.txt
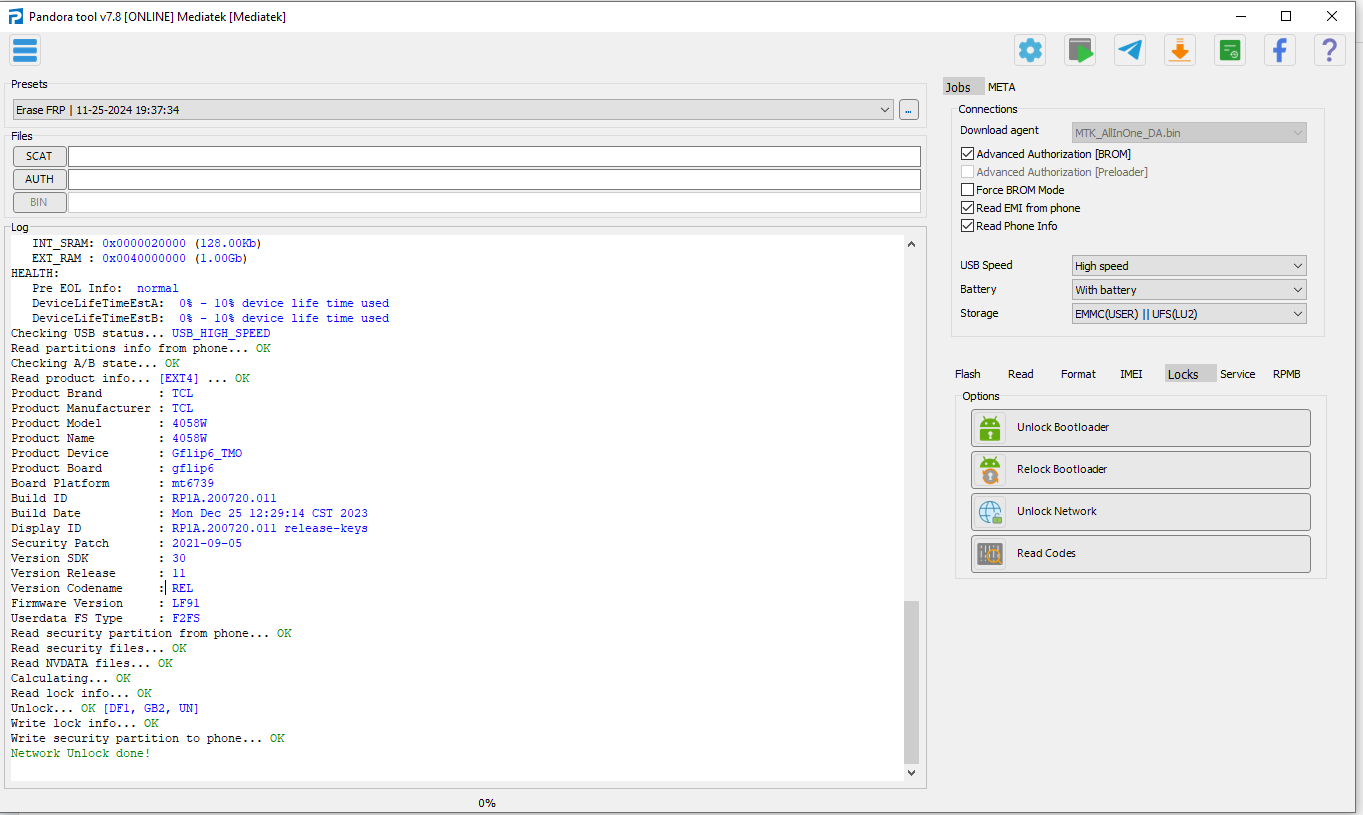
Direct Unlock TCL 4058W Go flip 6 TMO by Pandora Box
Selected model: Mediatek Mediatek
Operation: Unlock network
Software version: 7.8
Work ID: 51395372
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM13 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0699
Get sec config... OK [000000E7]
Active sec flags: [SBC SLA DAA]
Get HW & SW version from device... OK
HW VER: CB00, SW VER: 0002, HW SUB CODE: 8A00
Detect chip [MT6739]
Install LibUSB... OK
Waiting for device... OK
Open port... OK
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM13 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0699
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CB00, SW VER: 0002, HW SUB CODE: 8A00
Detect chip [MT6739]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xE594EF34, 0x7B372037, 0x373E4BC9, 0xBDA71E87
Get Chip ID... [MT6739]
Get SOC ID... [E15426D8C2F5EDD64E571F2AFC6EE57171D30D27194593D83FAA2F285C900AB5]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [1]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x150100464E36324242092434D3B01BD3
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: FN62BB
EMMC_ID : 0x150100464E36324242092434D3B01BD3
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0000080000 (512.00Kb)
EMMC_USER : 0x01D2000000 (7.28Gb)
RAM INFO:
INT_SRAM: 0x0000020000 (128.00Kb)
EXT_RAM : 0x0040000000 (1.00Gb)
HEALTH:
Pre EOL Info: normal
DeviceLifeTimeEstA: 0% - 10% device life time used
DeviceLifeTimeEstB: 0% - 10% device life time used
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : TCL
Product Manufacturer : TCL
Product Model : 4058W
Product Name : 4058W
Product Device : Gflip6_TMO
Product Board : gflip6
Board Platform : mt6739
Build ID : RP1A.200720.011
Build Date : Mon Dec 25 12:29:14 CST 2023
Display ID : RP1A.200720.011 release-keys
Security Patch : 2021-09-05
Version SDK : 30
Version Release : 11
Version Codename : REL
Firmware Version : LF91
Userdata FS Type : F2FS
Read security partition from phone... OK
Read security files... OK
Read NVDATA files... OK
Calculating... OK
Read lock info... OK
Unlock... OK [DF1, GB2, UN]
Write lock info... OK
Write security partition to phone... OK
Network Unlock done!
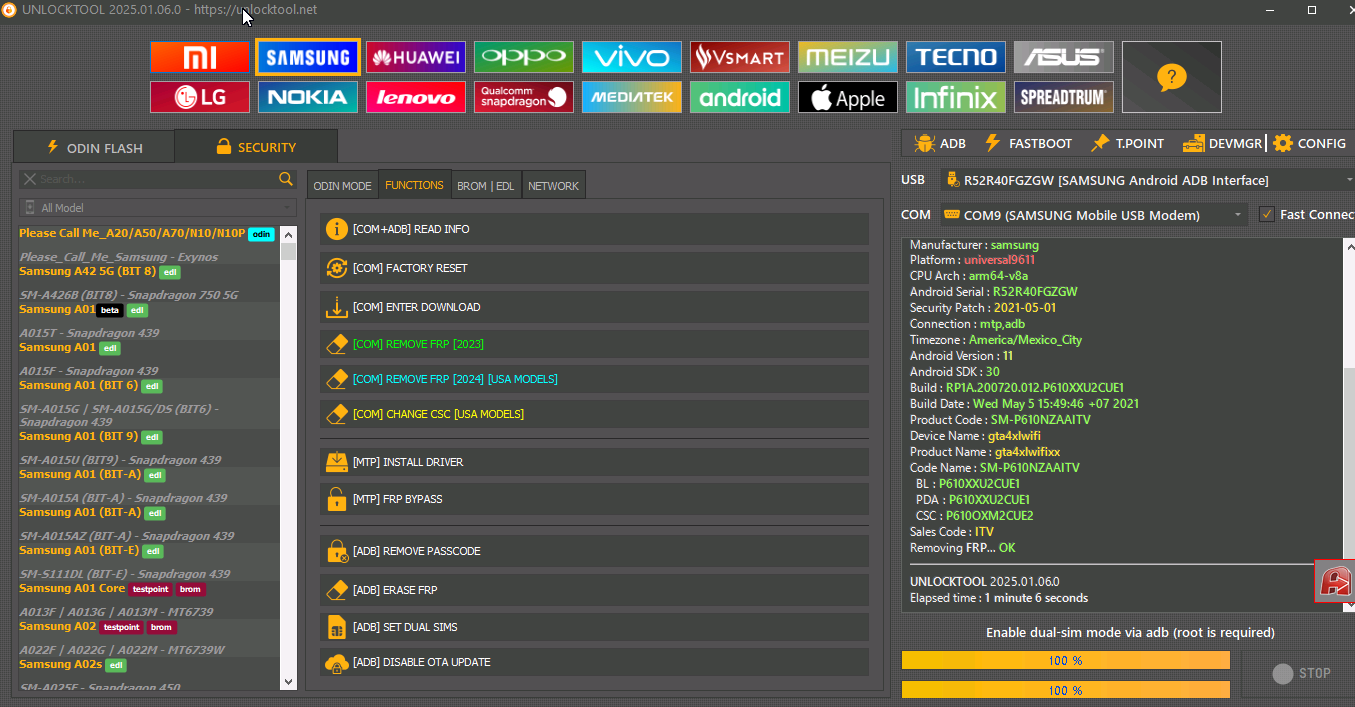
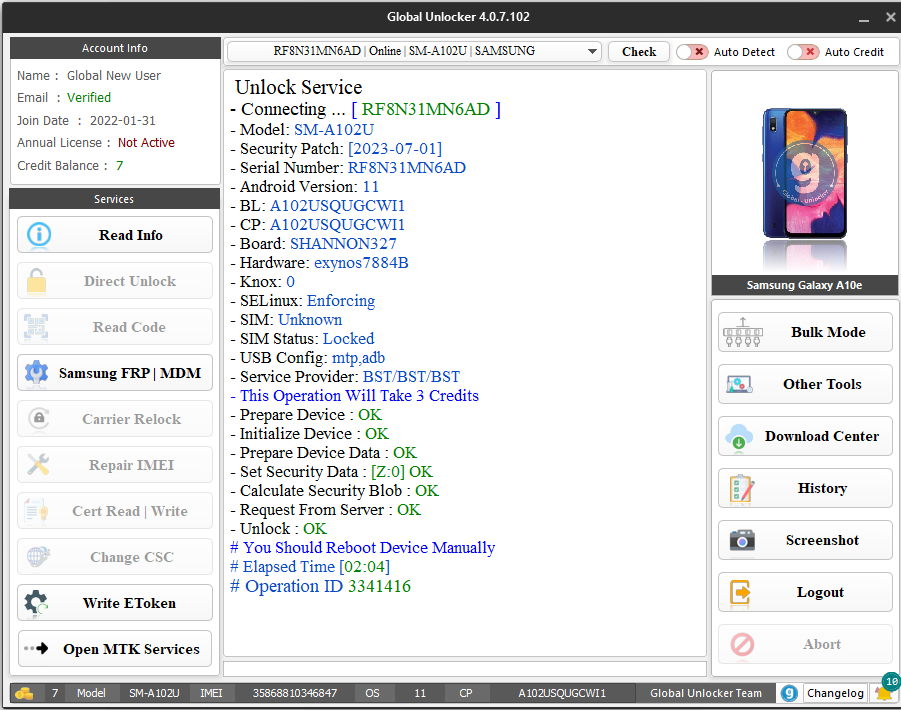
Direct Unlock Samsung SM-A102U by Global Unlocker
First Upgrade from 9 to 11 Android
Unlock Service
- Connecting ... [ RF8N31MN6AD ]
- Model: SM-A102U
- Security Patch: [2023-07-01]
- Serial Number: RF8N31MN6AD
- Android Version: 11
- BL: A102USQUGCWI1
- CP: A102USQUGCWI1
- Board: SHANNON327
- Hardware: exynos7884B
- Knox: 0
- SELinux: Enforcing
- SIM: Unknown
- SIM Status: Locked
- USB Config: mtp,adb
- Service Provider: BST/BST/BST
- This Operation Will Take 3 Credits
- Prepare Device : OK
- Initialize Device : OK
- Prepare Device Data : OK
- Set Security Data : [Z:0] OK
- Calculate Security Blob : OK
- Request From Server : OK
- Unlock : OK
# You Should Reboot Device Manually
# Elapsed Time [02:04]
# Operation ID 3341416
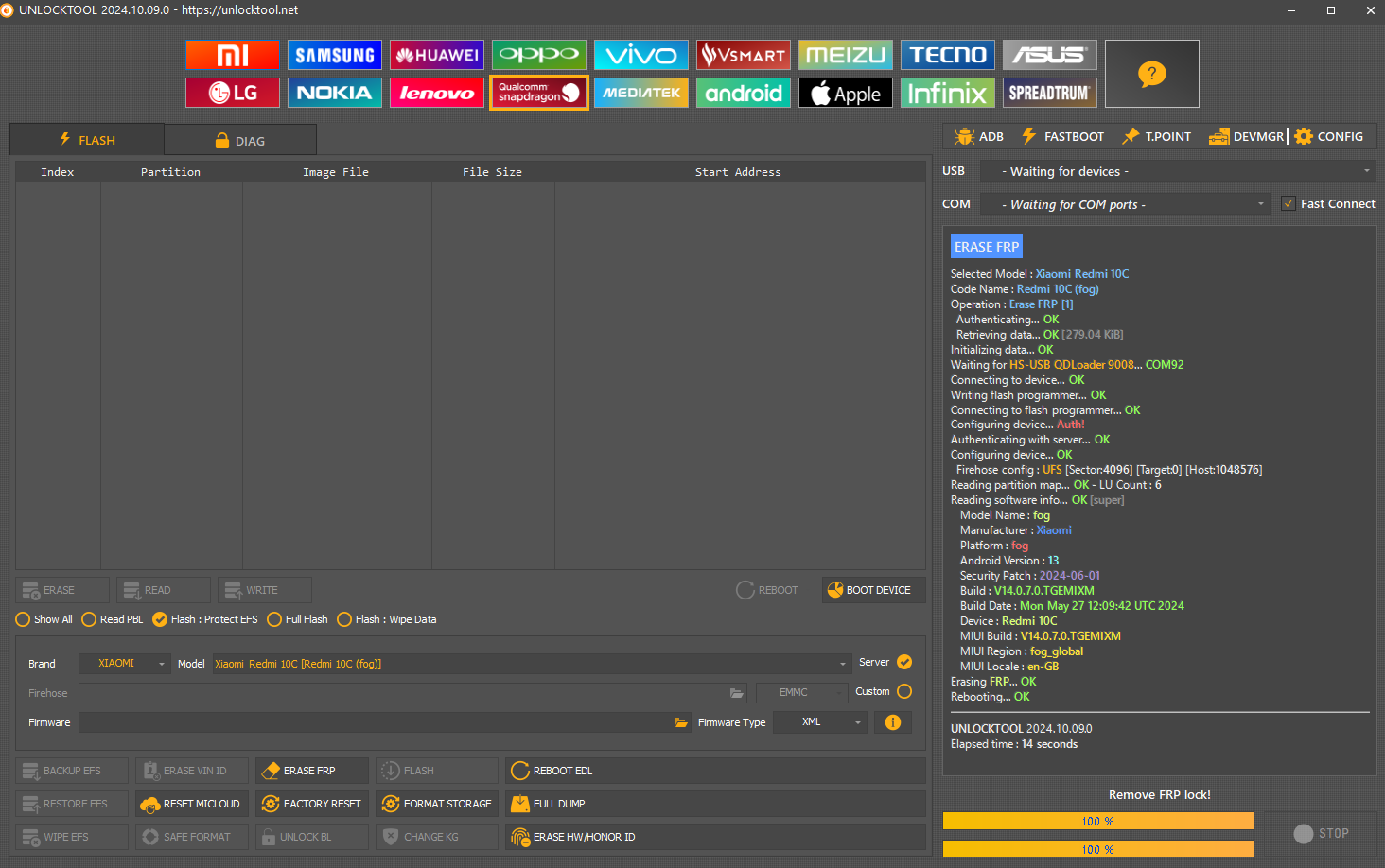
FRP Xiomi Redmi 10C By Unlocktool

ERASE FRP
Selected Model :
Xiaomi Redmi 10C
Code Name :
Redmi 10C (fog)
Operation :
Erase FRP [1]
Authenticating...
OK
Retrieving data...
OK
[279.04 KiB]
Initializing data...
OK
Waiting for
HS-USB QDLoader 9008
...
COM92
Connecting to device...
OK
Writing flash programmer...
OK
Connecting to flash programmer...
OK
Configuring device...
Auth!
Authenticating with server...
OK
Configuring device...
OK
Firehose config :
UFS
[Sector:
4096
] [Target:
0
] [Host:
1048576
]
Reading partition map...
OK
- LU Count :
6
Reading software info...
OK
[super]
Model Name :
fog
Manufacturer :
Xiaomi
Platform :
fog
Android Version :
13
Security Patch :
2024-06-01
Build :
V14.0.7.0.TGEMIXM
Build Date :
Mon May 27 12:09:42 UTC 2024
Device :
Redmi 10C
MIUI Build :
V14.0.7.0.TGEMIXM
MIUI Region :
fog_global
MIUI Locale :
en-GB
Erasing
FRP
...
OK
Rebooting...
OK
UNLOCKTOOL
2024.10.09.0
Elapsed time :
14 seconds
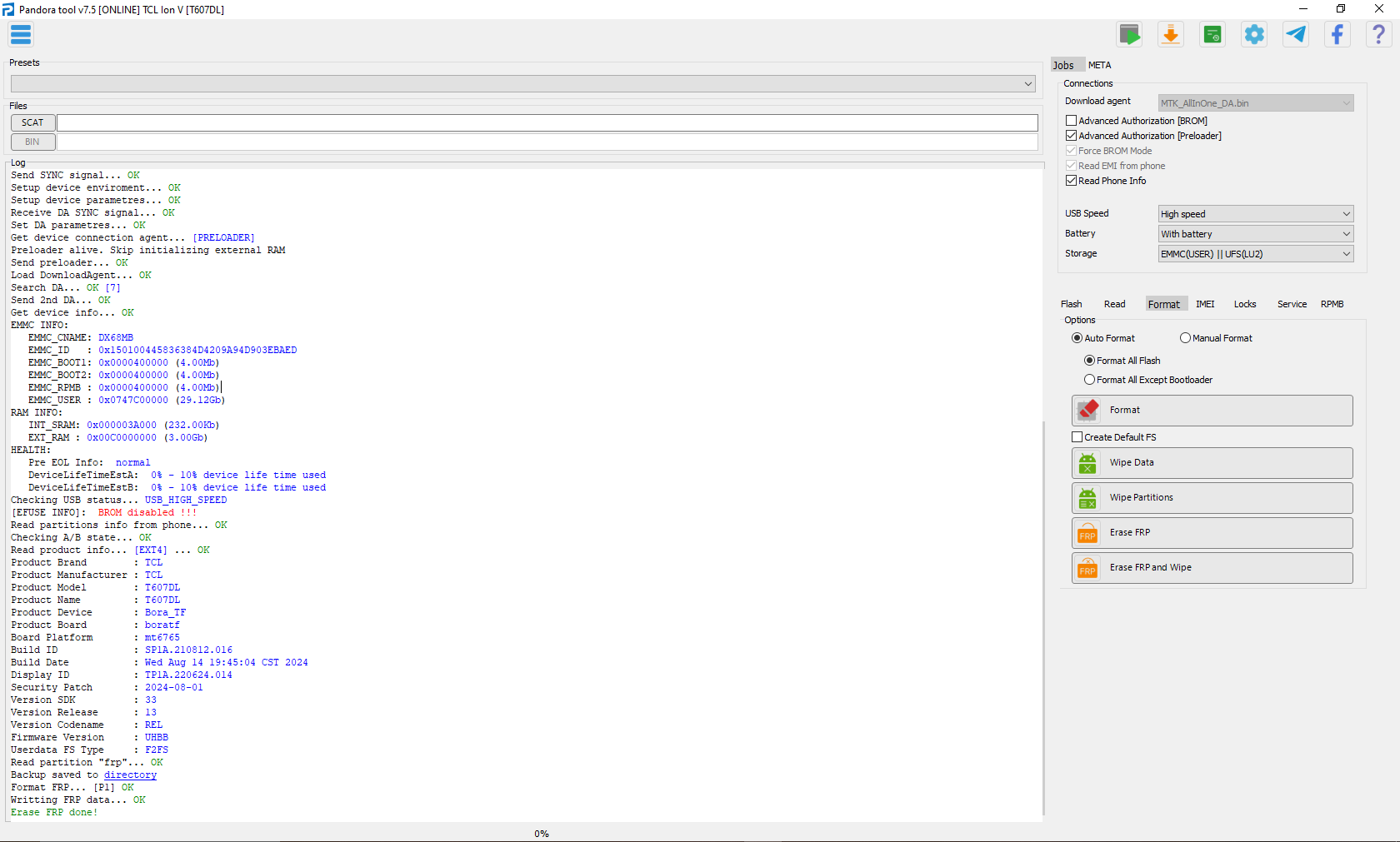
FRP TCL T607DL (TCL Ion V) By Pandora Tool
Selected model: TCL T607DL (TCL Ion V)
Operation: Erase FRP
Software version: 7.5
Work ID: 46591401
Connect phone in PRELOADER Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek PreLoader USB VCOM (Android),usb2ser.sys,3.0.1504.0]
Device found at COM45 [PRELOADER]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [00000007]
Active sec flags: [SBC SLA DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Preloader exist. Skip connection verification.
Get ME ID... OK
ME_ID = 0xD98CBD1E, 0x0CCF2849, 0x1FAA967F, 0x80D99633
Get hw mode... OK
Load DownloadAgent... OK
Search DA... OK [0]
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [PRELOADER]
Preloader alive. Skip initializing external RAM
Send preloader... OK
Load DownloadAgent... OK
Search DA... OK [7]
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: DX68MB
EMMC_ID : 0x150100445836384D4209A94D903EBAED
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0000400000 (4.00Mb)
EMMC_USER : 0x0747C00000 (29.12Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x00C0000000 (3.00Gb)
HEALTH:
Pre EOL Info: normal
DeviceLifeTimeEstA: 0% - 10% device life time used
DeviceLifeTimeEstB: 0% - 10% device life time used
Checking USB status... USB_HIGH_SPEED
[EFUSE INFO]: BROM disabled !!!
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : TCL
Product Manufacturer : TCL
Product Model : T607DL
Product Name : T607DL
Product Device : Bora_TF
Product Board : boratf
Board Platform : mt6765
Build ID : SP1A.210812.016
Build Date : Wed Aug 14 19:45:04 CST 2024
Display ID : TP1A.220624.014
Security Patch : 2024-08-01
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : UHBB
Userdata FS Type : F2FS
Read partition "frp"... OK
Backup saved to C:/Program%20Files%20(x86)/Z3X/Pandora/Backup/MTK/TCL_T607DL%20(TCL%20Ion%20V)/FRP_BACKUP_(2024-10-18_13-51-45)/
Format FRP... [P1] OK
Writting FRP data... OK
Erase FRP done!
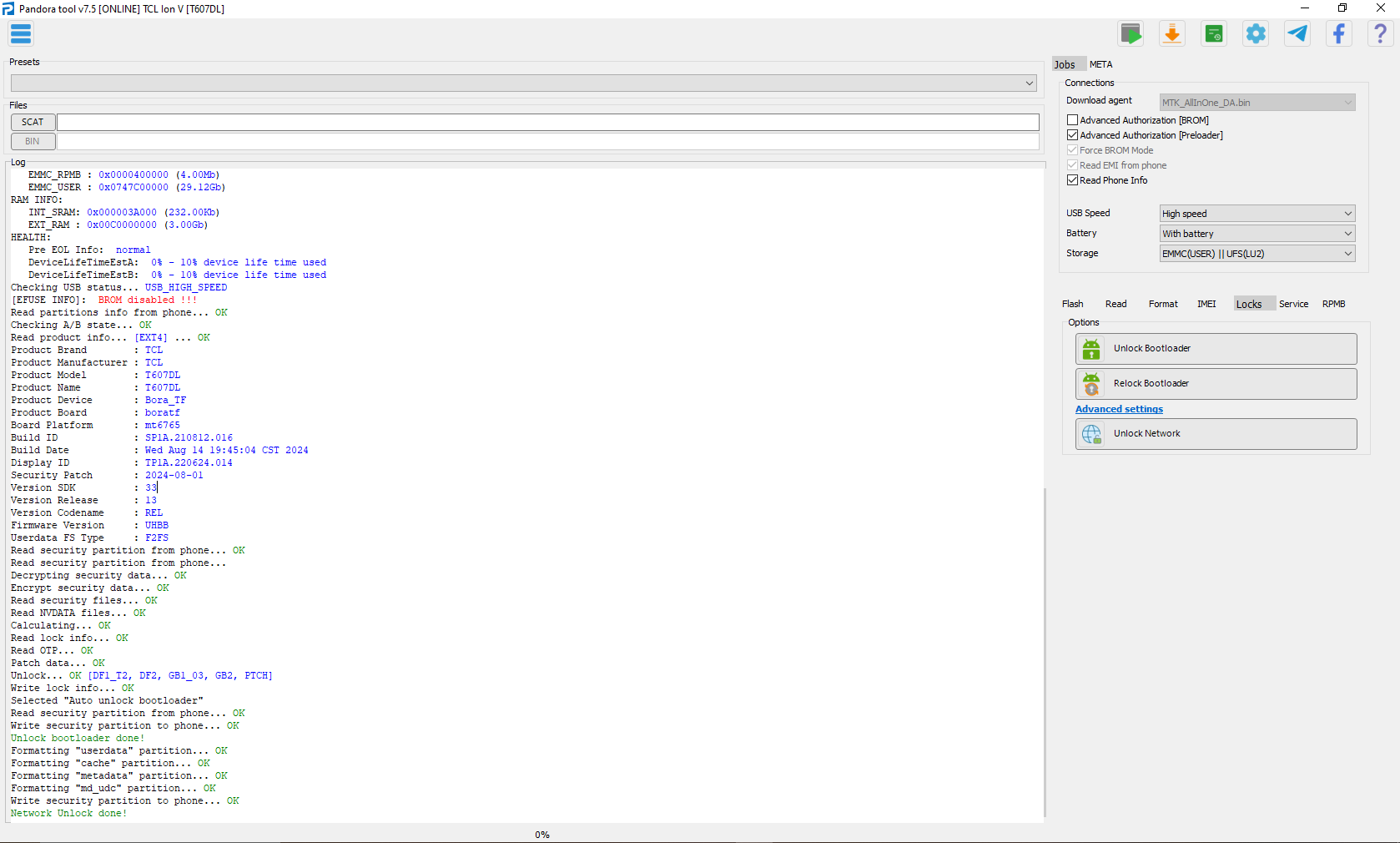
Direct Unlock TCL T607DL (TCL Ion V) Tracfone by Pandora
- Seleccionar Advance Authorization(Preloader)
- Seleccionar Direct Unlock
Selected model: TCL T607DL (TCL Ion V)
Operation: Unlock network
Software version: 7.5
Work ID: 46591000
Connect phone in PRELOADER Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek PreLoader USB VCOM (Android),usb2ser.sys,3.0.1504.0]
Device found at COM45 [PRELOADER]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [00000007]
Active sec flags: [SBC SLA DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Preloader exist. Skip connection verification.
Get ME ID... OK
ME_ID = 0xD98CBD1E, 0x0CCF2849, 0x1FAA967F, 0x80D99633
Get hw mode... OK
Load DownloadAgent... OK
Search DA... OK [0]
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [PRELOADER]
Preloader alive. Skip initializing external RAM
Send preloader... OK
Load DownloadAgent... OK
Search DA... OK [7]
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: DX68MB
EMMC_ID : 0x150100445836384D4209A94D903EBAED
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0000400000 (4.00Mb)
EMMC_USER : 0x0747C00000 (29.12Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x00C0000000 (3.00Gb)
HEALTH:
Pre EOL Info: normal
DeviceLifeTimeEstA: 0% - 10% device life time used
DeviceLifeTimeEstB: 0% - 10% device life time used
Checking USB status... USB_HIGH_SPEED
[EFUSE INFO]: BROM disabled !!!
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : TCL
Product Manufacturer : TCL
Product Model : T607DL
Product Name : T607DL
Product Device : Bora_TF
Product Board : boratf
Board Platform : mt6765
Build ID : SP1A.210812.016
Build Date : Wed Aug 14 19:45:04 CST 2024
Display ID : TP1A.220624.014
Security Patch : 2024-08-01
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : UHBB
Userdata FS Type : F2FS
Read security partition from phone... OK
Read security partition from phone...
Decrypting security data... OK
Encrypt security data... OK
Read security files... OK
Read NVDATA files... OK
Calculating... OK
Read lock info... OK
Read OTP... OK
Patch data... OK
Unlock... OK [DF1_T2, DF2, GB1_03, GB2, PTCH]
Write lock info... OK
Selected "Auto unlock bootloader"
Read security partition from phone... OK
Write security partition to phone... OK
Unlock bootloader done!
Formatting "userdata" partition... OK
Formatting "cache" partition... OK
Formatting "metadata" partition... OK
Formatting "md_udc" partition... OK
Write security partition to phone... OK
Network Unlock done!
FRP Samsung G532M TELCEL Android 6
FRP Samsung G532M Android 6
Agregar wifi poner letras y seleccionar para abrir google
despues abrir chrome y abrir vnROM
Seleccionar Test DCP configurar
Reiniciar y listo a cobrar
https://www.youtube.com/watch?v=qIcYz5elBUE
Using port SAMSUNG Mobile USB Modem #17 (COM40)
Reading info mode MTP ... OK
Model : SM-G532M
CSC : SM-G532MZKATCE
AP version : G532MUBU1ASA1
BL version : G532MUBU1ASA1
CP version : G532MUBU1ASA1
CSC version : G532MTCE1ASC1
IMEI : 358215082180748
SN : RV8J605Q6ZW
Lock status : NONE
MCC : 334
MNC : 020
USB mode : AT,MTP
Unique number : CQN0072004FBB44
Android version : 6.0.1
FRP status : TRIGGERED
Firmware : https://samfw.com/firmware/SM-G532M/SM-G532MZKATCE
Using port SAMSUNG Mobile USB Modem #17 (COM40)
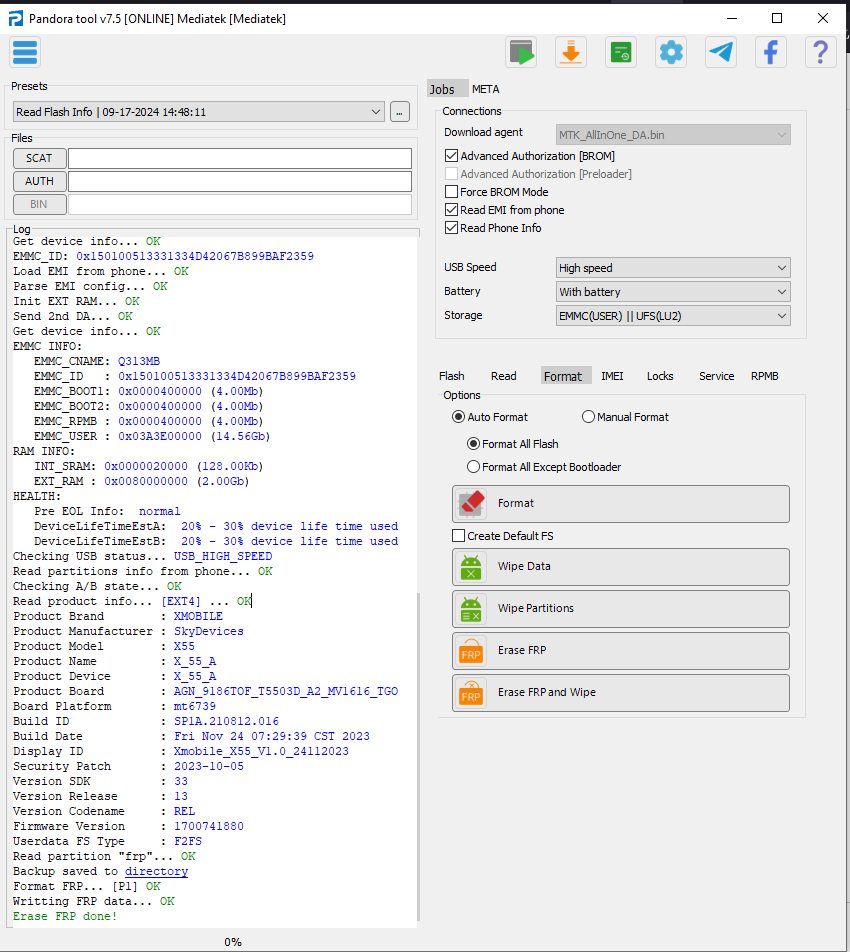
FRP XMOBILE X55 by Pandora Tool
Selected model: Mediatek Mediatek
Operation: Erase FRP
Software version: 7.5
Work ID: 44118693
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,USBSER.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM118 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0699
Get sec config... OK [00000000]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6739]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xEF5929B4, 0xD94182C0, 0x16CD59D2, 0x34927EB2
Get Chip ID... [MT6739]
Get SOC ID... [7F4F84A80646400BAA0928C1C2F952527E31D80B1B7F4857A676BDE490361AE8]
Get sec config... OK [00000000]
Load DownloadAgent... OK
Search DA... OK [1]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x150100513331334D42067B899BAF2359
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: Q313MB
EMMC_ID : 0x150100513331334D42067B899BAF2359
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0000400000 (4.00Mb)
EMMC_USER : 0x03A3E00000 (14.56Gb)
RAM INFO:
INT_SRAM: 0x0000020000 (128.00Kb)
EXT_RAM : 0x0080000000 (2.00Gb)
HEALTH:
Pre EOL Info: normal
DeviceLifeTimeEstA: 20% - 30% device life time used
DeviceLifeTimeEstB: 20% - 30% device life time used
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : XMOBILE
Product Manufacturer : SkyDevices
Product Model : X55
Product Name : X_55_A
Product Device : X_55_A
Product Board : AGN_9186TOF_T5503D_A2_MV1616_TGO
Board Platform : mt6739
Build ID : SP1A.210812.016
Build Date : Fri Nov 24 07:29:39 CST 2023
Display ID : Xmobile_X55_V1.0_24112023
Security Patch : 2023-10-05
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : 1700741880
Userdata FS Type : F2FS
Read partition "frp"... OK
Backup saved to C:/Program%20Files%20(x86)/Z3X/Pandora/Backup/MTK/Mediatek_MT6739/FRP_BACKUP_(2024-9-28_18-40-0)/
Format FRP... [P1] OK
Writting FRP data... OK
Erase FRP done!
FRP REDMI 9T
TEST POINT
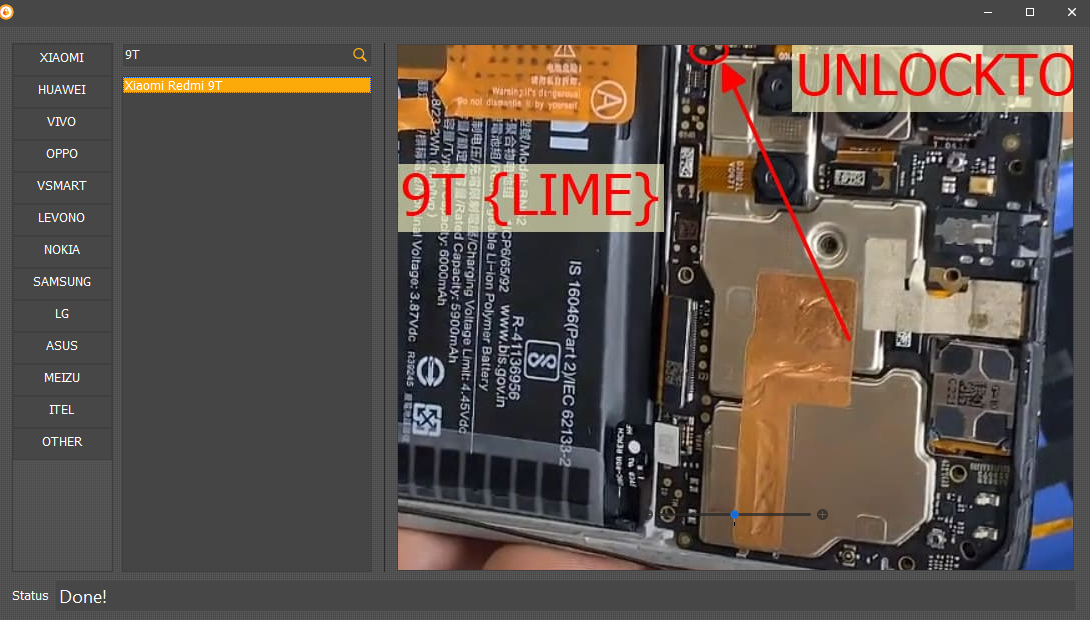
[EDL] ERASE FRP
Selected Model :
Xiaomi Redmi 9T / Redmi 9 / Redmi 9 Power
Code Name :
(lime)
Operation :
Erase FRP [1]
Authenticating...
OK
Retrieving data...
OK
[270.92 KiB]
Initializing data...
OK
Waiting for
HS-USB QDLoader 9008
...
COM80
Connecting to device...
OK
Handshaking...
OK
Reading bootloader info...
OK
Serial :
2505305946
SoC : [
Snapdragon 662
] [
SM6115
] [
0x0014D0E1
]
OEM :
Xiaomi [0x0072]
Model :
Unknown [0x0000]
PK_HASH[0] : 1BEBE3863A6781DB4B01086063007334
PK_HASH[1] : DE9E5CA14971C7C4F4358EC9D79CDA46
Writing flash programmer...
OK
Connecting to flash programmer...
OK
Configuring device...
OK
Firehose config :
UFS
[Sector:
4096
] [Target:
0
] [Host:
1048576
]
Reading partition map...
OK
- LU Count :
6
Reading software info...
OK
[super]
Model Name :
Lime for arm64
Product Name :
lime
Manufacturer :
Xiaomi
Platform :
lime
Android Version :
12
Security Patch :
2022-12-01
Build ID :
Android-Q-build-20221205011709
Build :
V13.0.2.0.SJQMIXM
Build Date :
Mon Dec 5 01:14:22 CST 2022
MIUI Version :
V130
MIUI Build :
V13.0.2.0.SJQMIXM
MIUI Region :
lime_global
MIUI Locale :
en-GB
Erasing
FRP
...
OK
Rebooting...
OK
UNLOCKTOOL
2024.09.02.0
Elapsed time :
4 minutes 27 seconds
Telefono MTK no prende pantalla negra
C:\laragon\www\mtkclient\
λ mtk reset
MTK Flash/Exploit Client V1.58 (c) B.Kerler 2018-2022
Preloader - Status: Waiting for PreLoader VCOM, please connect mobile
Port - Hint:
Power off the phone before connecting.
For brom mode, press and hold vol up, vol dwn, or all hw buttons and connect usb.
For preloader mode, don't press any hw button and connect usb.
.Port - Device detected :)
Preloader - CPU: MT6765/MT8768t(Helio P35/G35)
Preloader - HW version: 0x0
Preloader - WDT: 0x10007000
Preloader - Uart: 0x11002000
Preloader - Brom payload addr: 0x100a00
Preloader - DA payload addr: 0x201000
Preloader - CQ_DMA addr: 0x10212000
Preloader - Var1: 0x25
Preloader - Disabling Watchdog...
Preloader - HW code: 0x766
Preloader - Target config: 0xe5
Preloader - SBC enabled: True
Preloader - SLA enabled: False
Preloader - DAA enabled: True
Preloader - SWJTAG enabled: True
Preloader - EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: False
Preloader - Root cert required: False
Preloader - Mem read auth: True
Preloader - Mem write auth: True
Preloader - Cmd 0xC8 blocked: True
Preloader - Get Target info
Preloader - BROM mode detected.
Preloader - HW subcode: 0x8a00
Preloader - HW Ver: 0xca00
Preloader - SW Ver: 0x0
Preloader - ME_ID: A1A0091A4F48FECBAED948BB4AC52728
Preloader - SOC_ID: 9CF6ADDF9A7482E22764A3E91BD0B46819131CE149284763B99CD6491E9DB7DD
PLTools - Loading payload from mt6765_payload.bin, 0x264 bytes
PLTools - Kamakiri / DA Run
Kamakiri - Trying kamakiri2..
Kamakiri - Done sending payload...
PLTools - Successfully sent payload: C:\laragon\www\mtkclient\mtkclient\payloads\mt6765_payload.bin
Port - Device detected :)
DA_handler - Device is protected.
DA_handler - Device is in BROM mode. Trying to dump preloader.
DAXFlash - Uploading xflash stage 1 from MTK_AllInOne_DA_5.2152.bin
xflashext - Patching da2 ...
DAXFlash - Successfully uploaded stage 1, jumping ..
Preloader - Jumping to 0x200000
Preloader - Jumping to 0x200000: ok.
DAXFlash - Successfully received DA sync
DAXFlash - DRAM config needed for : 1501004758364241
DAXFlash - Sending emi data ...
DAXFlash - DRAM setup passed.
DAXFlash - Sending emi data succeeded.
DAXFlash - Uploading stage 2...
DAXFlash - Upload data was accepted. Jumping to stage 2...
DAXFlash - Successfully uploaded stage 2
DAXFlash - EMMC FWVer: 0x0
DAXFlash - EMMC ID: GX6BAB
DAXFlash - EMMC CID: 15010047583642414200bb0c683c295f
DAXFlash - EMMC Boot1 Size: 0x400000
DAXFlash - EMMC Boot2 Size: 0x400000
DAXFlash - EMMC GP1 Size: 0x0
DAXFlash - EMMC GP2 Size: 0x0
DAXFlash - EMMC GP3 Size: 0x0
DAXFlash - EMMC GP4 Size: 0x0
DAXFlash - EMMC RPMB Size: 0x1000000
DAXFlash - EMMC USER Size: 0x747c00000
DAXFlash - HW-CODE : 0x766
DAXFlash - HWSUB-CODE : 0x8A00
DAXFlash - HW-VERSION : 0xCA00
DAXFlash - SW-VERSION : 0x0
DAXFlash - CHIP-EVOLUTION : 0x0
DAXFlash - DA-VERSION : 1.0
DAXFlash - Upload data was accepted. Jumping to stage 2...
DAXFlash - DA Extensions successfully added
Reset command was sent. Disconnect usb cable to power off.
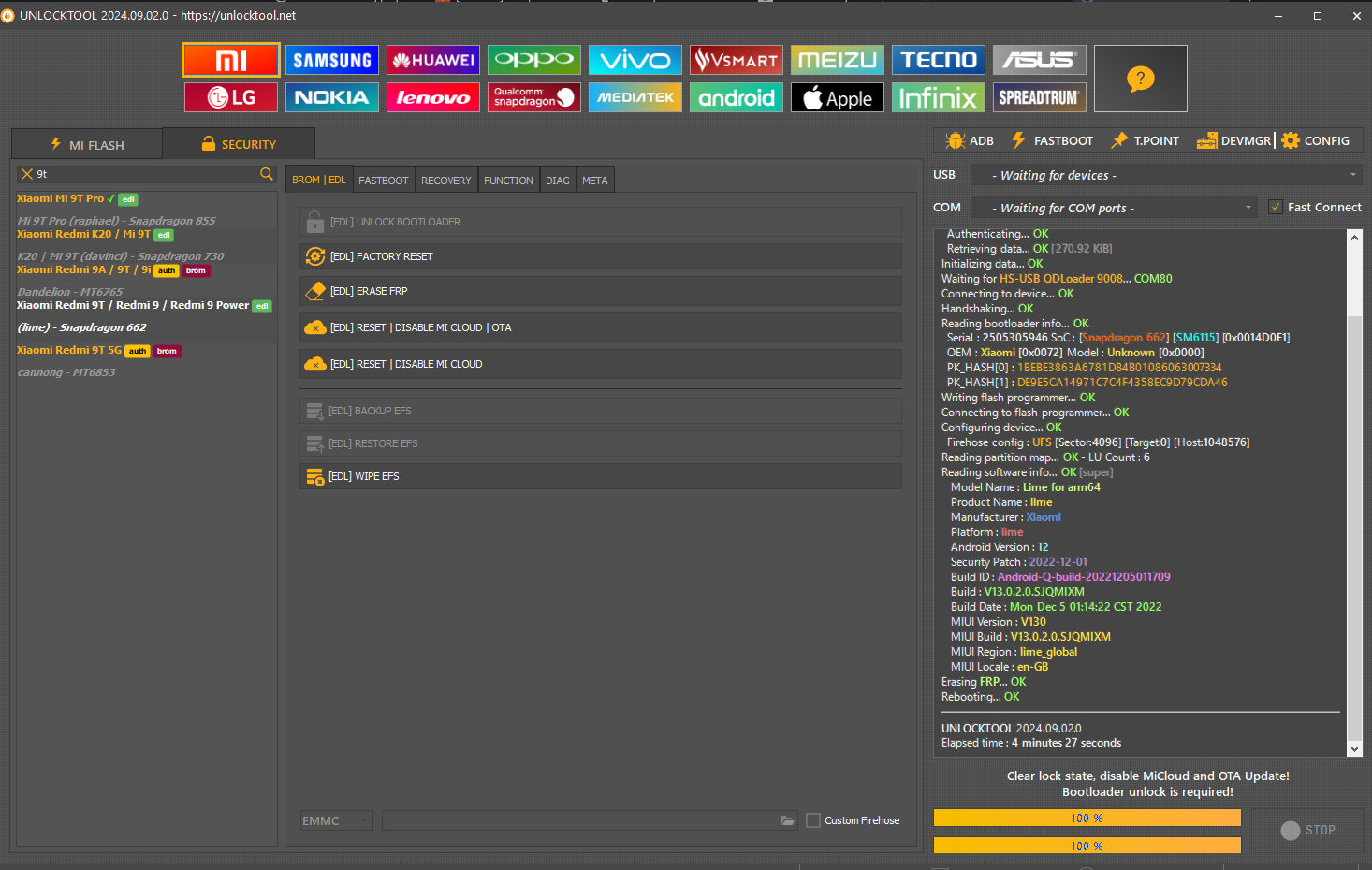
FRP Motorola XT1635-02 Moto Z Play by UMT Box
Brand : Motorola
Model : XT1635
Operation : Reset FRP
Searching for Device in FastBoot Mode...OK
Reading Phone Information...OK
Model : XT1635-02
Boot Ver. : moto-msm8953-C1.82
Baseband : M8953_10238.63.04.83.01R ADDISON_ROW_CUST
Software : Blur_Version.27.231.10.addison.retail.en.US
IMEI : 358212072705519
CPU : MSM8953
RAM : 3GB SAMSUNG LP3 DIE=6Gb M5=01 M6=05 M7=00 M8=7B
EMMC : 32GB SAMSUNG RX1BMB RV=08 PV=07 FV=0000000000000007
Setting Factory Mode...OK
Searching Network Interface...Found
Connecting to device...OK
Model : XT1635-02
Bootloader : 0xC182
Baseband : M8953_10238.63.04.83.01R ADDISON_ROW_CUST
Build : Blur_Version.27.231.10.addison.retail.en.US
Android : 8.0.0
Searching Network Interface...Found
Connecting to device...OK
Model : XT1635-02
Bootloader : 0xC182
Baseband : M8953_10238.63.04.83.01R ADDISON_ROW_CUST
Build : Blur_Version.27.231.10.addison.retail.en.US
Android : 8.0.0
Retetting FRP...OK
Searching for Device in FastBoot Mode...OK
Removing Factory Mode...OK
Operation Finished.
UltimateFRP Ver. 0.5.1
Samsung Worldwide FRP SM-A356E By IMEI Unlock INSTANT Galaxy A35 5G
Unlock.mx offer Samsung FRP by IMEI instant service
Model Name : Galaxy A35 5G Model Number : SM-A356E IMEI : 35460034XXXXXXX Status : Register successful, Enter the phone into recovery mode and choose repair apps Or factory reset It will take 3-4 minutes, then connect wifi and complete the setup. If you are late, the order will be cancelled
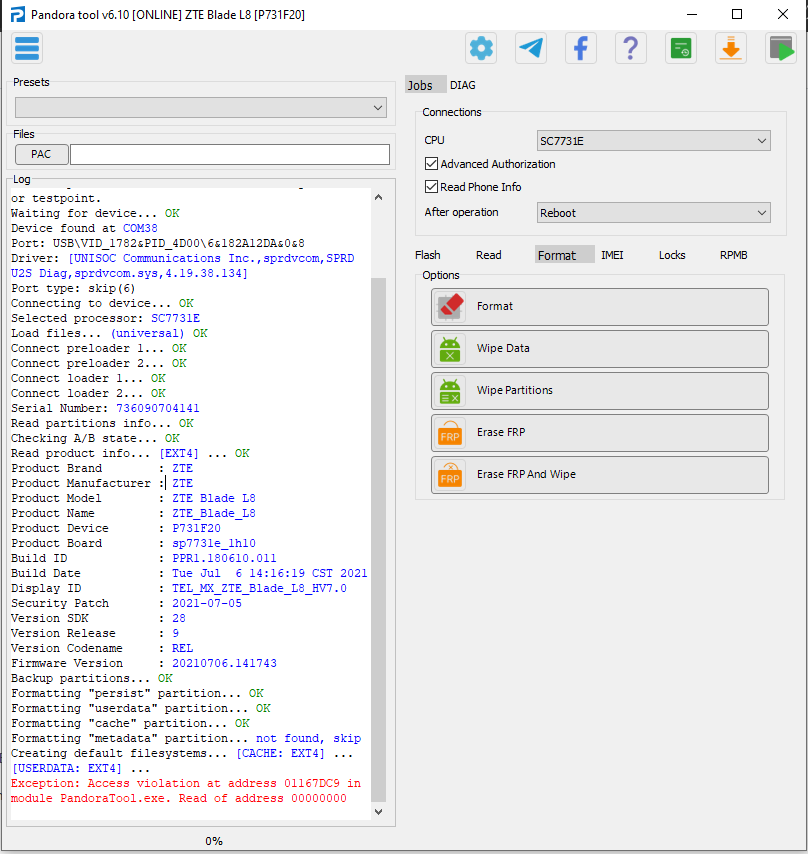
FRP ZTE Blade L8 SPD Unisoc sp7731e by Pandora Box
Apagado presionar volumen - conectar cable USB
Selected model: ZTE P731F20 (ZTE Blade L8)
Operation: Erase FRP And Wipe
Software version: 6.10
Work ID: 34580165
Connect phone in BROM mode. Use volume key buttons or testpoint.
Waiting for device... OK
Device found at COM38
Port: USB\VID_1782&PID_4D00\6&182A12DA&0&8
Driver: [UNISOC Communications Inc.,sprdvcom,SPRD U2S Diag,sprdvcom.sys,4.19.38.134]
Port type: skip(6)
Connecting to device... OK
Selected processor: SC7731E
Load files... (universal) OK
Connect preloader 1... OK
Connect preloader 2... OK
Connect loader 1... OK
Connect loader 2... OK
Serial Number: 736090704141
Read partitions info... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : ZTE
Product Manufacturer : ZTE
Product Model : ZTE Blade L8
Product Name : ZTE_Blade_L8
Product Device : P731F20
Product Board : sp7731e_1h10
Build ID : PPR1.180610.011
Build Date : Tue Jul 6 14:16:19 CST 2021
Display ID : TEL_MX_ZTE_Blade_L8_HV7.0
Security Patch : 2021-07-05
Version SDK : 28
Version Release : 9
Version Codename : REL
Firmware Version : 20210706.141743
Backup partitions... OK
Formatting "persist" partition... OK
Formatting "userdata" partition... OK
Formatting "cache" partition... OK
Formatting "metadata" partition... not found, skip
Creating default filesystems... [CACHE: EXT4] ... [USERDATA: EXT4] ...
Exception: Access violation at address 01167DC9 in module PandoraTool.exe. Read of address 00000000
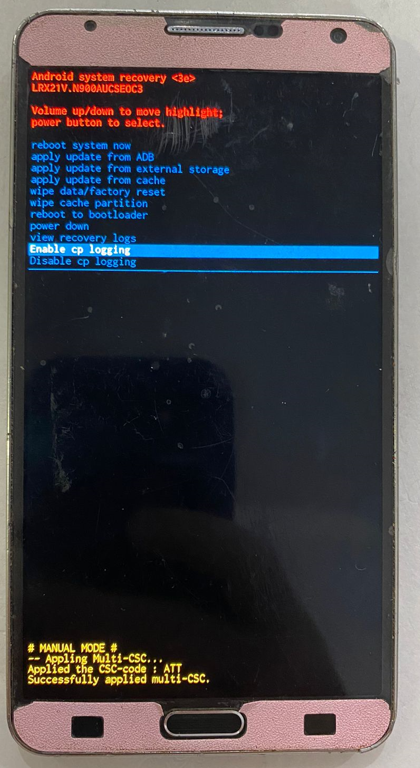
Direct Unlock Samsung SM-N900A by Z3X
Entrar en Recovery Volumen Up + Home + Power on
Select Enable cp logging + Select Power
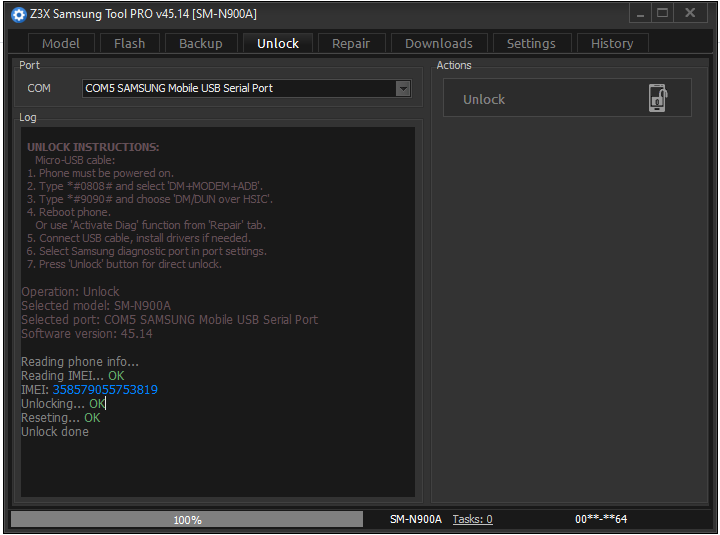
UNLOCK INSTRUCTIONS:
Micro-USB cable:
1. Phone must be powered on.
2. Type *#0808# and select 'DM+MODEM+ADB'.
3. Type *#9090# and choose 'DM/DUN over HSIC'.
4. Reboot phone.
Or use 'Activate Diag' function from 'Repair' tab.
5. Connect USB cable, install drivers if needed.
6. Select Samsung diagnostic port in port settings.
7. Press 'Unlock' button for direct unlock.
Done with Samsung Tool PRO v.45.14 [SM-N900A,Unlock]
Operation: Unlock
Selected model: SM-N900A
Selected port: COM5 SAMSUNG Mobile USB Serial Port
Software version: 45.14
Reading phone info...
Reading IMEI... OK
IMEI: 358579055753819
Unlocking... OK
Reseting... OK
Unlock done
Done with Samsung Tool PRO v.45.14 [SM-N900A,Unlock]
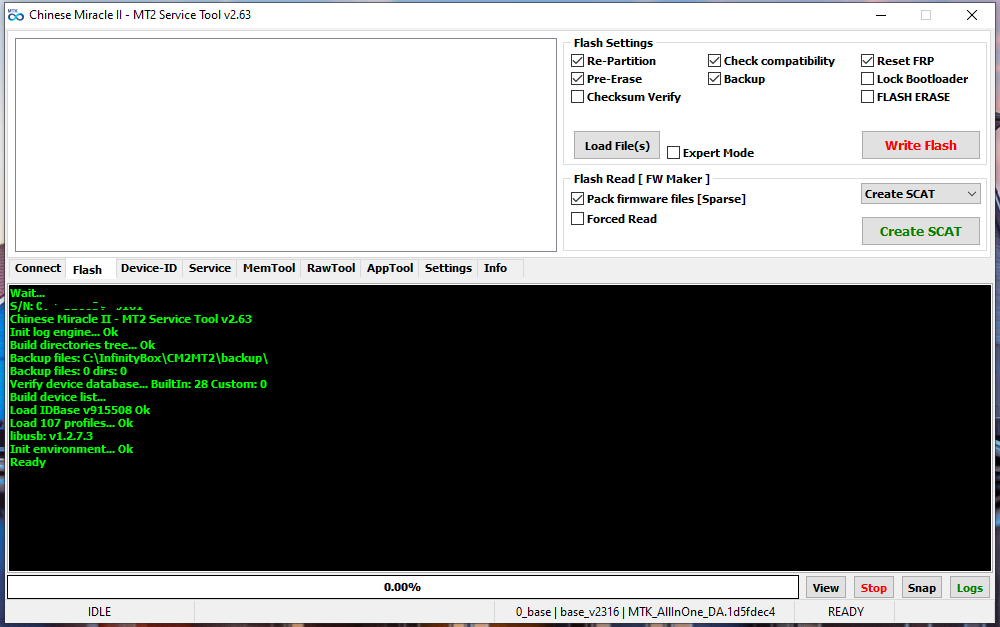
Como leer Scatter file con Infinity Box
- Abrir MT2 by Infinity Box
- Seleccionar la Pestaña Flash
- Donde Dice Read Flash Seleccionan y cambian Create SCAT
- Presionan el boton Create SCAT
- conectar el telefono apagado con volumen + y volumen - si es necesario conecatar Test Point
- Creara un archivo similar a este MT6739_Android_scatter.txt
- este archivo es necesario para hacer flash
#I##########################################################################################################
# General Setting
# Version: Infinity CM2MT2 v2.63 2024-07-03
#I##########################################################################################################
- general: MTK_PLATFORM_CFG
info:
- config_version: V1.1.3
platform: MT6739
project:
storage: EMMC
boot_channel: MSDC_0
block_size: 0x20000
#I##########################################################################################################
#
# Layout Setting
#
#I##########################################################################################################
- partition_index: SYS0
partition_name: preloader
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x0
physical_start_addr: 0x0
partition_size: 0x400000
region: EMMC_BOOT1_BOOT2
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: BOOTLOADERS
is_upgradable: true
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS1
partition_name: pgpt
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x0
physical_start_addr: 0x0
partition_size: 0x8000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS2
partition_name: proinfo
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x8000
physical_start_addr: 0x8000
partition_size: 0x300000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: PROTECTED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS3
partition_name: nvram
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x308000
physical_start_addr: 0x308000
partition_size: 0x500000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: BINREGION
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS4
partition_name: pad4nvramwp
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x808000
physical_start_addr: 0x808000
partition_size: 0x7f8000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS5
partition_name: redbend
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x1000000
physical_start_addr: 0x1000000
partition_size: 0x300000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: PROTECTED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS6
partition_name: fota
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x1300000
physical_start_addr: 0x1300000
partition_size: 0x500000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS7
partition_name: persist
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x1800000
physical_start_addr: 0x1800000
partition_size: 0x1000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: PROTECTED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS8
partition_name: boot_para
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x2800000
physical_start_addr: 0x2800000
partition_size: 0x100000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS9
partition_name: para
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x2900000
physical_start_addr: 0x2900000
partition_size: 0x80000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS10
partition_name: expdb
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x2980000
physical_start_addr: 0x2980000
partition_size: 0x1400000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS11
partition_name: frp
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x3d80000
physical_start_addr: 0x3d80000
partition_size: 0x100000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS12
partition_name: nvcfg
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x3e80000
physical_start_addr: 0x3e80000
partition_size: 0x800000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: PROTECTED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS13
partition_name: nvdata
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x4680000
physical_start_addr: 0x4680000
partition_size: 0x2000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS14
partition_name: metadata
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x6680000
physical_start_addr: 0x6680000
partition_size: 0x2000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS15
partition_name: protect1
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x8680000
physical_start_addr: 0x8680000
partition_size: 0x800000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: PROTECTED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS16
partition_name: protect2
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x8e80000
physical_start_addr: 0x8e80000
partition_size: 0x800000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: PROTECTED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS17
partition_name: mobile_info
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x9680000
physical_start_addr: 0x9680000
partition_size: 0x1180000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: PROTECTED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS18
partition_name: seccfg
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0xa800000
physical_start_addr: 0xa800000
partition_size: 0x80000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS19
partition_name: recovery
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0xa880000
physical_start_addr: 0xa880000
partition_size: 0x1780000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS20
partition_name: sec1
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0xc000000
physical_start_addr: 0xc000000
partition_size: 0x200000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS21
partition_name: efuse
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0xc200000
physical_start_addr: 0xc200000
partition_size: 0x80000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS22
partition_name: md1img
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0xc280000
physical_start_addr: 0xc280000
partition_size: 0x4000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS23
partition_name: md1dsp
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x10280000
physical_start_addr: 0x10280000
partition_size: 0x1000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS24
partition_name: spmfw
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x11280000
physical_start_addr: 0x11280000
partition_size: 0x100000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS25
partition_name: mcupmfw
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x11380000
physical_start_addr: 0x11380000
partition_size: 0x100000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS26
partition_name: gz1
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x11480000
physical_start_addr: 0x11480000
partition_size: 0x1000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS27
partition_name: gz2
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x12480000
physical_start_addr: 0x12480000
partition_size: 0x1000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS28
partition_name: simlock
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x13480000
physical_start_addr: 0x13480000
partition_size: 0x500000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: PROTECTED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS29
partition_name: lk
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x13980000
physical_start_addr: 0x13980000
partition_size: 0x100000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS30
partition_name: lk2
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x13a80000
physical_start_addr: 0x13a80000
partition_size: 0x100000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS31
partition_name: loader_ext1
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x13b80000
physical_start_addr: 0x13b80000
partition_size: 0x10000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: BOOTLOADERS
is_upgradable: true
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS32
partition_name: loader_ext2
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x13b90000
physical_start_addr: 0x13b90000
partition_size: 0x10000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: BOOTLOADERS
is_upgradable: true
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS33
partition_name: boot
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x13ba0000
physical_start_addr: 0x13ba0000
partition_size: 0x1000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS34
partition_name: logo
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x14ba0000
physical_start_addr: 0x14ba0000
partition_size: 0x800000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS35
partition_name: odmdtbo
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x153a0000
physical_start_addr: 0x153a0000
partition_size: 0x1000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS36
partition_name: tee1
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x163a0000
physical_start_addr: 0x163a0000
partition_size: 0x500000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS37
partition_name: tee2
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x168a0000
physical_start_addr: 0x168a0000
partition_size: 0x760000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS38
partition_name: vendor
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x17000000
physical_start_addr: 0x17000000
partition_size: 0x43800000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS39
partition_name: system
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x5a800000
physical_start_addr: 0x5a800000
partition_size: 0xca800000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS40
partition_name: cache
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x125000000
physical_start_addr: 0x125000000
partition_size: 0x14000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS41
partition_name: userdata
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0x139000000
physical_start_addr: 0x139000000
partition_size: 0xc0000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: true
is_reserved: false
operation_type: INVISIBLE
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS42
partition_name: otp
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0xffff01d8
physical_start_addr: 0xffff01d8
partition_size: 0x2b00000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: false
is_reserved: true
operation_type: RESERVED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS43
partition_name: flashinfo
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0xffff0080
physical_start_addr: 0xffff0080
partition_size: 0x1000000
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: false
is_reserved: true
operation_type: RESERVED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
- partition_index: SYS44
partition_name: sgpt
file_name: NONE
is_download: false
type: NORMAL_ROM
linear_start_addr: 0xffff0000
physical_start_addr: 0xffff0000
partition_size: 0x4200
region: EMMC_USER
storage: HW_STORAGE_EMMC
boundary_check: false
is_reserved: true
operation_type: RESERVED
is_upgradable: false
empty_boot_needed: false
reserve: 0x00
FRP Samsung SM-J700T1 by Chimera
- llamada de emergencia asterisco # 0 asterisco #
- conectar el cable usb y seleccionar FRP
Chimera Mobile Phone Utility version: 39.90.1044 @ 2024-07-04
Reset FRP lock started
Gathering phone info...
Collecting information. Be patient! Do NOT disconnect the phone!
Model: SM-J700T1
Sales Code: TMK
Country Code: USA
Timezone: America/Mexico_City
Android Version: 6.0.1 [MMB29K] [SDK 23]
Build Date: Thu Nov 24 15:00:54 KST 2016
PDA Version: J700T1UVU2APK6 [november 2016, rev6]
Phone Version: J700T1UVU2APK6 [november 2016, rev6]
CSC Version: J700T1TMK2APK6 [november 2016, rev6]
Board Platform: EXYNOS5
Modem Platform: SHANNON310
Serial Number: R58H857A2SM
Imei: 357217074141572
Battery Status: 3.75V (39%)
Network Type: GSM
SIM Status: ABSENT
Knox Version: v30
Warranty Bit: 0
Security Patch: 2016-11-01
Resetting FRP by engineering boot-based method.
Processing...
Processing. Be patient! Do NOT disconnect the phone!
Resetting FRP lock...
Done.
Succeeded.
Successfully finished.
Finished at local time: [07.04.24 13:02:54]
WorkID: 288023326
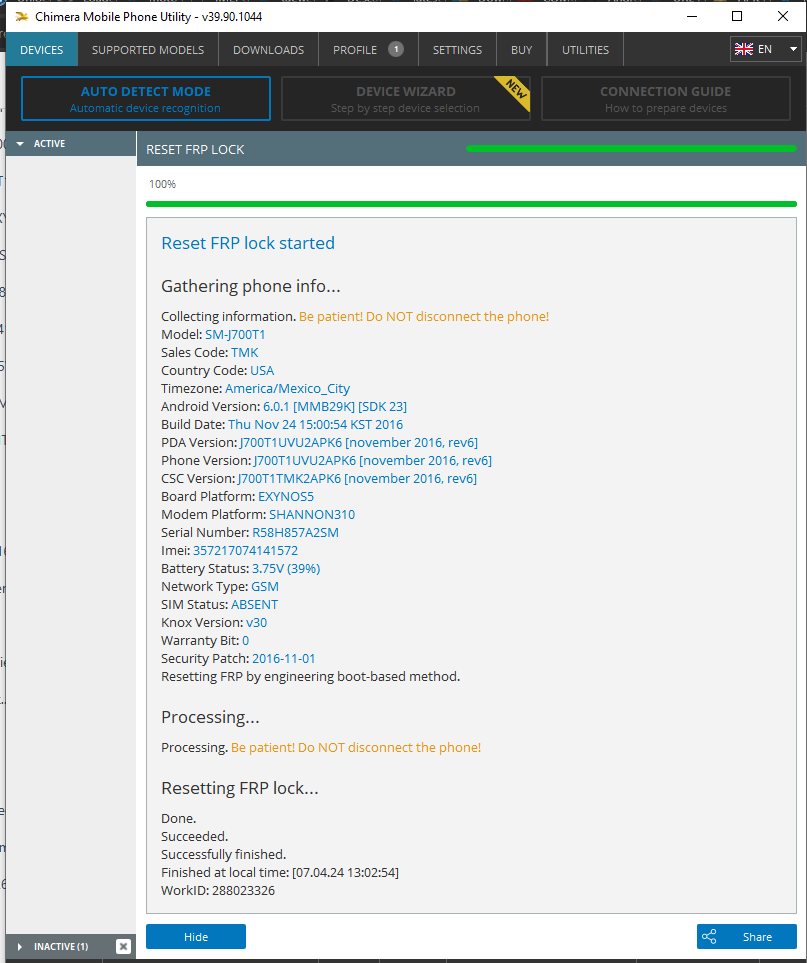
Install and Setup EDL Client
Install and Setup EDL Client
- Download and Install https://github.com/leokhoa/laragon/releases/download/6.0.0/laragon-wamp.exe
- Download and Select Custom Install with path C:\laragon\bin\python\Python312\ https://www.python.org/ftp/python/3.12.4/python-3.12.4-amd64.exe
- Download and Install https://winfsp.dev/rel/
- Download and Install https://github.com/daynix/UsbDk/releases/
- Clone Repo https://github.com/bkerler/edl.git
- git submodule update --init --recursive
- pip3 install -r requirements.txt
- pip3 install .
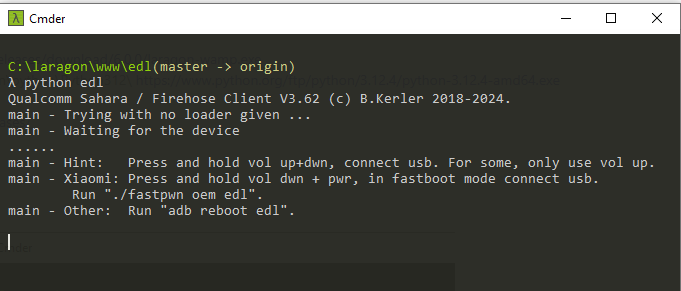
$ edl --serial
$ edl --portname \\.\COM1
Buscar el puerto COM en Device Manager
Presionar la tecla Windows + R
devmgmt.msc Ejecturar
FRP Xiaomi Redmi A2 MT6765
Selected model: Xiaomi Redmi A2 (Water)
Operation: Erase FRP
Software version: 6.10
Work ID: 33909264
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM24 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E7]
Active sec flags: [SBC SLA DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Install LibUSB... OK
Waiting for device... OK
Open port... OK
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM24 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xDEA08034, 0x8D71ED74, 0xCC0F1640, 0x56DA47C3
Get Chip ID... [MT6765]
Get SOC ID... [E670C7046E455F8CE0D586A36BE347B1CFB0902C86CC4CE9B18DBAECC5309667]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [7]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x9B01005932503033320042430D0FA965
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: Y2P032
EMMC_ID : 0x9B01005932503033320042430D0FA965
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0001000000 (16.00Mb)
EMMC_USER : 0x0747C00000 (29.12Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x0080000000 (2.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK [A]
Read product info... [EROFS] ... OK
Product Brand : Redmi
Product Manufacturer : Xiaomi
Product Model : water
Product Name : water_global
Product Device : water
Product Board : water
Board Platform : mt6765
Build ID : SP1A.210812.016
Build Date : Tue Apr 4 19:56:56 CST 2023
Display ID : 13 V14.0.10.0.TGOMIXM
Security Patch : 2023-03-01
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : V14.0.10.0.TGOMIXM
Userdata FS Type : F2FS
Read partition "frp"... OK
Backup saved to C:/Program%20Files%20(x86)/Z3X/Pandora/Backup/MTK/Xiaomi_Redmi%20A2%20(Water)/FRP_BACKUP_(2024-7-3_15-16-21)/
Writting FRP data... OK
Erase FRP done!
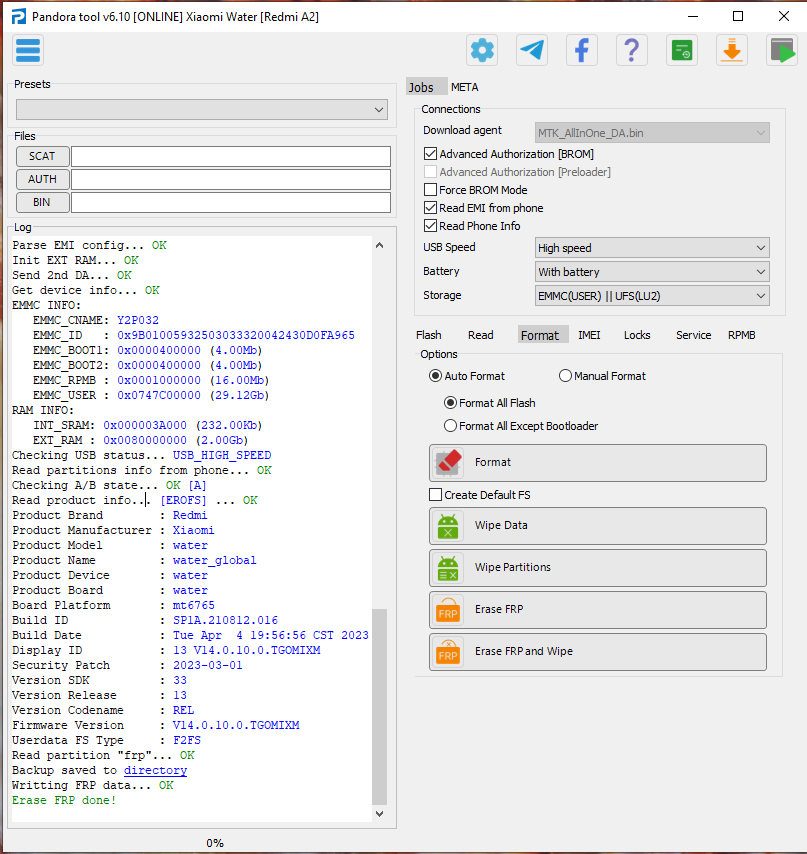
Reset Protection Recovery Key Lumia 640 RM-1073
C:\iutool>iutool
(IUTool Version: 11:52:10/Feb 7 2014)
Command-Line Usage:
Command lines
-?
-p path [-s name] [-n name] [-m manufacturer] [-t model] [-a] [-v] [-V]
-l
Options
-? Show list of commands and usage
-V show VERY detailed progress messages
-a update all connected devices in parallel
-l list the connected devices
-m the phone's manufacturer
-n the phone's friendly name
-p directory path or semicolon-delimited list of package paths
-s the phone's serial number
-t the phone's type (model name)
-v show detailed progress messages
Install update files onto a device.
Command failed. (HRESULT = 0x80dd0001)

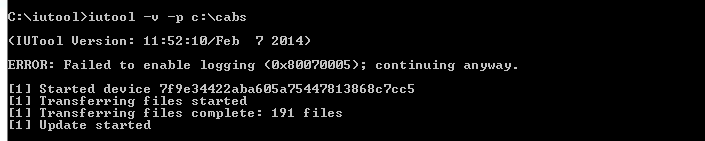
FRP Oppo A53 UFS (CPH2127) by UMT QC
- Conectar el cable USB con el telefono prendido
- Seleccionar Apagar y presionar al mismo tiempo volumen arriba + volumen abajo
- activar casilla Reset FRP y presionar Execute
Model : Oppo A53 UFS (CPH2127)
Operation : Erase Userdata
Checking for existing devices...Not Found
Turn Off phone, hold Vol UP + Vol DOWN and insert USB cable.
Some phones may need Special Boot Cable or TestPoint for EDL mode.
Found Port : Qualcomm HS-USB QDLoader 9008 (COM11)
Driver Info : Qualcomm Incorporated, qcusbser.sys, 2.1.2.0
Connecting to phone...OK
Waiting for response...OK
Init Handshake Sequence...OK
Hardware ID : E1601300 [SDM460] 00005100
OPK_DATA : 19CF99D55CA3B2E11EA19E52E3541DEDF01898FD9F8C40E62548F1C7F60ABD47
Initializing Protocol...OK
Preparing Loader...Done
Sending Loader [CPH2127]...Done
Executing Loader...OK
Initializing Storage...OK
Read : Allowed
Write : Protected
Alt. Write : Allowed
Alt. Write is allowed, using Factory Format Method...Done
Erasing FRP Data...Done
Operation Finished.
QcFire Ver. 10.2
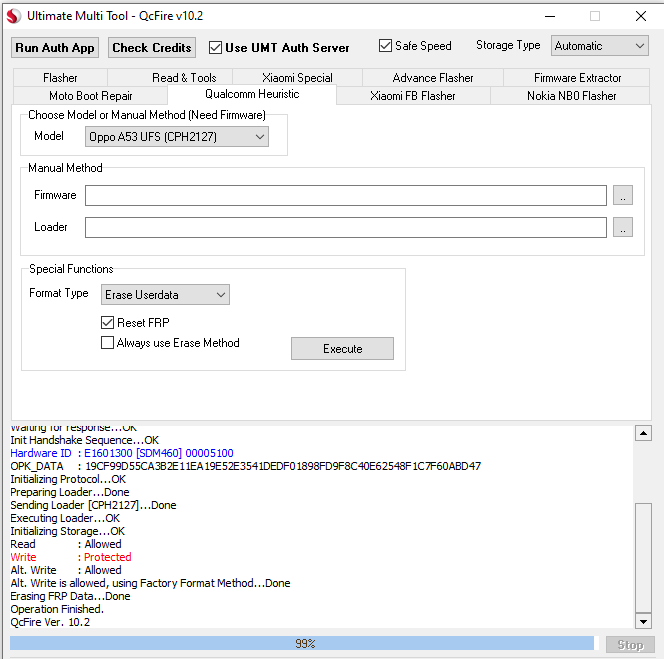
Install and Setup MTKCLIENT 2
How Install MTK CLIENT
- Download and Install https://github.com/leokhoa/laragon/releases/download/6.0.0/laragon-wamp.exe
- Download and Select Custom Install with path C:\laragon\bin\python\Python312\ https://www.python.org/ftp/python/3.12.4/python-3.12.4-amd64.exe
- Download and Install https://winfsp.dev/rel/
- Download and Install https://github.com/daynix/UsbDk/releases/
- Clone Repo
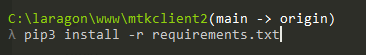
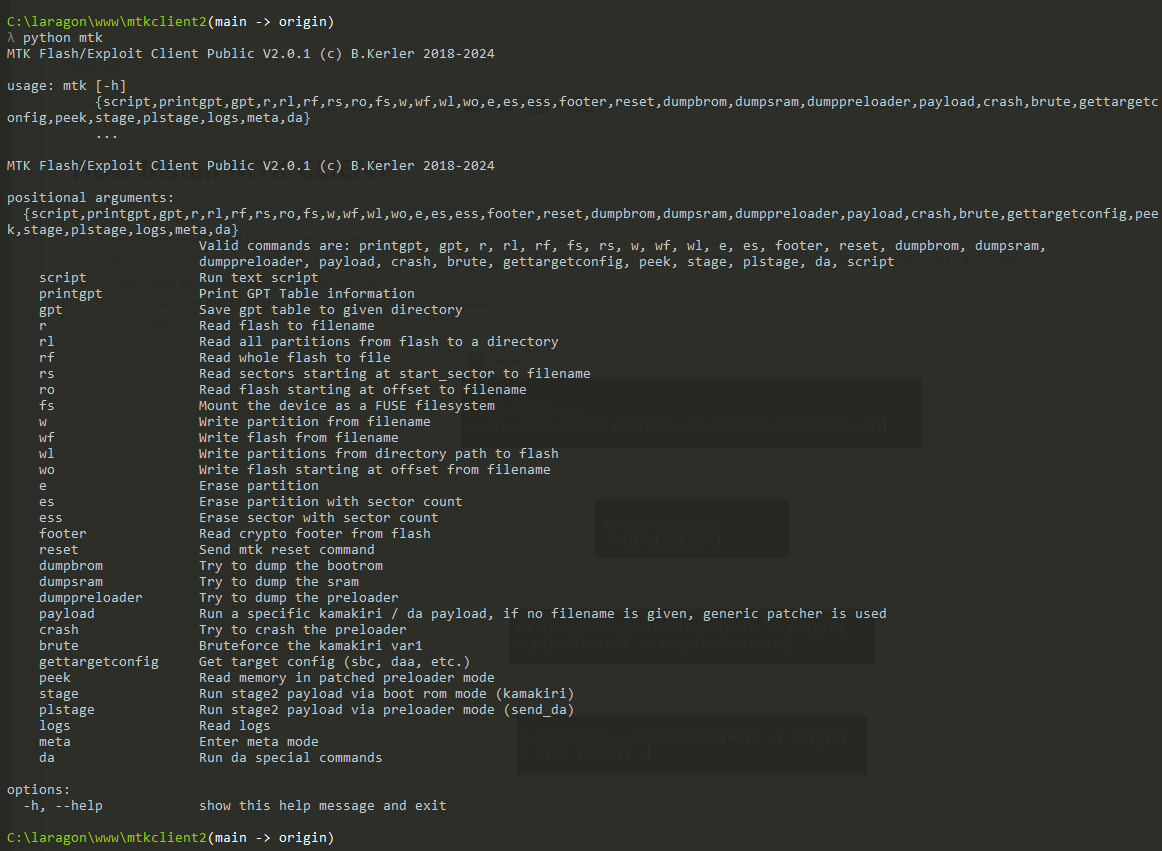
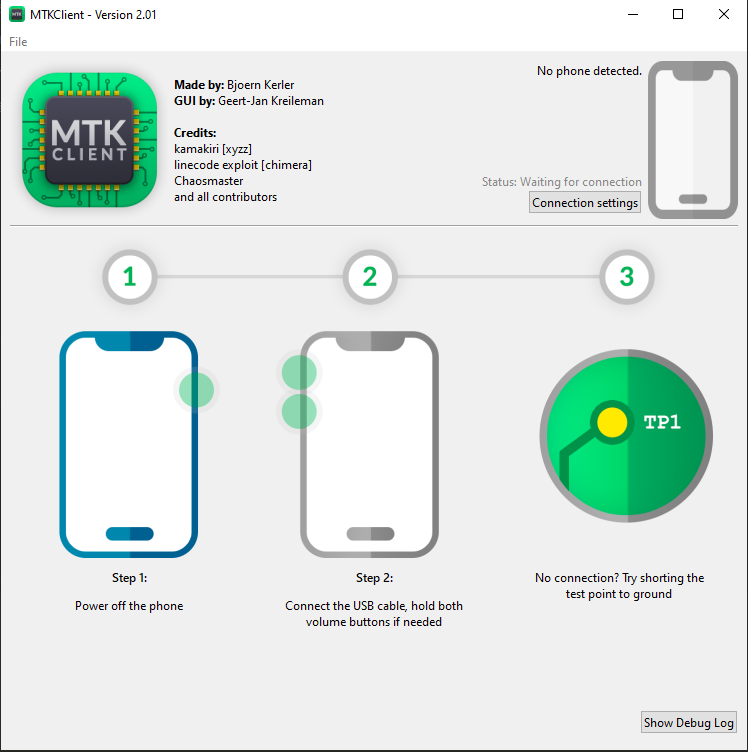
- Exit Brom Mode Phone is Blank Mode or Lcd Black $ python mtk reset
- Read Full Flash $ python mtk rf flash.bin
- Erase partition FRP $ python mtk e frp
- Show gpt $ python mtk printgpt
- Generate and display rpmb1-3 key $ python mtk da generatekeys
- MTK Unlock Bootloader $ python mtk da seccfg unlock
- Bypass SLA, DAA and SBC (using generic_patcher_payload) $ python mtk payload
If you can switch any version mtkclient or install seversal version with git checkout
Example clone mtkclient 1.63
- eba887b9bb3764abf2a56775f6708be1c7589854 refs/tags/1.4
- a70d552fb605c0b8a422ad5899f4a95541079c3d refs/tags/1.41
- 3d4c3f0115ab4c89b823d1d123ec13c24c861dfc refs/tags/1.42
- 1e7f37e5ccdcecc553a8a2363898a6954b6fbdb4 refs/tags/1.52
- 81694c4aae9af5190e9ea1d037e727bf1f7dbe5a refs/tags/1.63
- 537c8c76bccfc5fe7615ecf578081257e45b2591 refs/tags/1.9
you can read official documentation for more use
Best Regard
Samsung SM-A025M GPT
Samsung SM-A025M GPT by edl with test point mode
1. Partition Name: sbl1 Start LBA: 0x00002028 Size in LBA: 0x00000400
2. Partition Name: rpm Start LBA: 0x00002428 Size in LBA: 0x00000400
3. Partition Name: tz Start LBA: 0x00002828 Size in LBA: 0x00001000
4. Partition Name: devcfg Start LBA: 0x00003828 Size in LBA: 0x00000200
5. Partition Name: dsp Start LBA: 0x00003a28 Size in LBA: 0x00008000
6. Partition Name: mdtp Start LBA: 0x0000ba28 Size in LBA: 0x00010000
7. Partition Name: sbl1bak Start LBA: 0x0001ba28 Size in LBA: 0x00000400
8. Partition Name: rpmbak Start LBA: 0x0001be28 Size in LBA: 0x00000400
9. Partition Name: tzbak Start LBA: 0x0001c228 Size in LBA: 0x00001000
10. Partition Name: devcfgbak Start LBA: 0x0001d228 Size in LBA: 0x00000200
11. Partition Name: reserved0 Start LBA: 0x0001d428 Size in LBA: 0x00002bd8
12. Partition Name: lksecapp Start LBA: 0x00020000 Size in LBA: 0x00000100
13. Partition Name: cmnlib Start LBA: 0x00020100 Size in LBA: 0x00000800
14. Partition Name: cmnlib64 Start LBA: 0x00020900 Size in LBA: 0x00000800
15. Partition Name: keymaster Start LBA: 0x00021100 Size in LBA: 0x00000800
16. Partition Name: aboot Start LBA: 0x00021900 Size in LBA: 0x00001000
17. Partition Name: vbmeta Start LBA: 0x00022900 Size in LBA: 0x00000080
18. Partition Name: vk Start LBA: 0x00022980 Size in LBA: 0x00001000
19. Partition Name: em Start LBA: 0x00023980 Size in LBA: 0x00002000
20. Partition Name: bksecapp Start LBA: 0x00025980 Size in LBA: 0x00000400
21. Partition Name: btd Start LBA: 0x00025d80 Size in LBA: 0x00000400
22. Partition Name: lksecappbak Start LBA: 0x00026180 Size in LBA: 0x00000100
23. Partition Name: cmnlibbak Start LBA: 0x00026280 Size in LBA: 0x00000800
24. Partition Name: cmnlib64bak Start LBA: 0x00026a80 Size in LBA: 0x00000800
25. Partition Name: keymasterbak Start LBA: 0x00027280 Size in LBA: 0x00000800
26. Partition Name: abootbak Start LBA: 0x00027a80 Size in LBA: 0x00001000
27. Partition Name: dtbo Start LBA: 0x00028a80 Size in LBA: 0x00004000
28. Partition Name: vbmetabak Start LBA: 0x0002ca80 Size in LBA: 0x00000080
29. Partition Name: logdump Start LBA: 0x0002cb00 Size in LBA: 0x00020000
30. Partition Name: reserved4 Start LBA: 0x0004cb00 Size in LBA: 0x00010000
31. Partition Name: param Start LBA: 0x0005cb00 Size in LBA: 0x00006000
32. Partition Name: reserved1 Start LBA: 0x00062b00 Size in LBA: 0x00001500
33. Partition Name: fsc Start LBA: 0x00064000 Size in LBA: 0x00001a00
34. Partition Name: ssd Start LBA: 0x00065a00 Size in LBA: 0x00000200
35. Partition Name: mota Start LBA: 0x00065c00 Size in LBA: 0x00000400
36. Partition Name: dip Start LBA: 0x00066000 Size in LBA: 0x00000800
37. Partition Name: reserved2 Start LBA: 0x00066800 Size in LBA: 0x00001800
38. Partition Name: ddr Start LBA: 0x00068000 Size in LBA: 0x00000400
39. Partition Name: sec Start LBA: 0x00068400 Size in LBA: 0x00000200
40. Partition Name: fsg Start LBA: 0x00068600 Size in LBA: 0x00005000
41. Partition Name: limits Start LBA: 0x0006d600 Size in LBA: 0x00000040
42. Partition Name: devinfo Start LBA: 0x0006d640 Size in LBA: 0x00000800
43. Partition Name: mcfg Start LBA: 0x0006de40 Size in LBA: 0x00002000
44. Partition Name: reserved3 Start LBA: 0x0006fe40 Size in LBA: 0x000001c0
45. Partition Name: pad Start LBA: 0x00070000 Size in LBA: 0x00000200
46. Partition Name: modemst1 Start LBA: 0x00070200 Size in LBA: 0x00002000
47. Partition Name: modemst2 Start LBA: 0x00072200 Size in LBA: 0x00002000
48. Partition Name: sec_efs Start LBA: 0x00074200 Size in LBA: 0x00008000
49. Partition Name: efs Start LBA: 0x0007c200 Size in LBA: 0x00008000
50. Partition Name: splash Start LBA: 0x00084200 Size in LBA: 0x00005800
51. Partition Name: apdp Start LBA: 0x00089a00 Size in LBA: 0x00000200
52. Partition Name: msadp Start LBA: 0x00089c00 Size in LBA: 0x00000200
53. Partition Name: reserved5 Start LBA: 0x00089e00 Size in LBA: 0x00006000
54. Partition Name: persist Start LBA: 0x0008fe00 Size in LBA: 0x00010000
55. Partition Name: misc Start LBA: 0x0009fe00 Size in LBA: 0x00000800
56. Partition Name: syscfg Start LBA: 0x000a0600 Size in LBA: 0x00000400
57. Partition Name: dpo Start LBA: 0x000a0a00 Size in LBA: 0x00000010
58. Partition Name: keystore Start LBA: 0x000a0a10 Size in LBA: 0x00000400
59. Partition Name: config Start LBA: 0x000a0e10 Size in LBA: 0x00000040
60. Partition Name: oem Start LBA: 0x000a0e50 Size in LBA: 0x000811b0
61. Partition Name: recovery Start LBA: 0x00122000 Size in LBA: 0x00020000
62. Partition Name: boot Start LBA: 0x00142000 Size in LBA: 0x00020000
63. Partition Name: dtbobak Start LBA: 0x00162000 Size in LBA: 0x00004000
64. Partition Name: bota Start LBA: 0x00166000 Size in LBA: 0x00022000
65. Partition Name: steady Start LBA: 0x00188000 Size in LBA: 0x00002000
66. Partition Name: persistent Start LBA: 0x0018a000 Size in LBA: 0x00000400
67. Partition Name: apnhlos Start LBA: 0x0018a400 Size in LBA: 0x00020008
68. Partition Name: modem Start LBA: 0x001aa408 Size in LBA: 0x000223f8
69. Partition Name: keyrefuge Start LBA: 0x001cc800 Size in LBA: 0x00008000
70. Partition Name: keydata Start LBA: 0x001d4800 Size in LBA: 0x00008000
71. Partition Name: metadata Start LBA: 0x001dc800 Size in LBA: 0x00010000
72. Partition Name: super Start LBA: 0x001ec800 Size in LBA: 0x00908000
73. Partition Name: prism Start LBA: 0x00af4800 Size in LBA: 0x000fa000
74. Partition Name: optics Start LBA: 0x00bee800 Size in LBA: 0x0002d000
75. Partition Name: cache Start LBA: 0x00c1b800 Size in LBA: 0x00050000
76. Partition Name: omr Start LBA: 0x00c6b800 Size in LBA: 0x00019000
77. Partition Name: debug Start LBA: 0x00c84800 Size in LBA: 0x00005000
78. Partition Name: userdata Start LBA: 0x00c89800 Size in LBA: 0x067f27d8
Reset MI CLOUD Xiaomi Redmi Note 10S 4G
[BROM] RESET | DISABLE MI CLOUD | OTA Initializing usb... OK
Waiting for device... COM24 [BOOTROM:0E8D:0003]
Bypassing authentication... OK
Analyzing... preloader_k85v1_64.bin [MT6875/6781:9:1552] [Internal]
Handshaking... OK
Reading hardware info... OK
Hardware : MT6785 [Helio G90|G90T|G95] 0813 8A00 CA00 0000
Security Config : SCB SLA DAA
MEID : 94916C63ACBB5C7040406A72C741AE61
Sending Download-Agent [1]... OK
Syncing with device... OK
Booting device... OK
Syncing with DA... OK
Storage : UFS - FWVer : - CID : MT128GASAO4U21
Vendor ID : Micron MP [0x12C]
UFS: LU0 Size : 4 MiB - LU1 Size : 4 MiB - LU2 Size : 119.17 GiB
Reading partition info... OK [62]
Reading device info... OK [super]
Model Name : rosemary
Manufacturer : Xiaomi
Platform : rosemary
Android Version : 13
Security Patch : 2023-06-01
Build ID : TP1A.220624.014
Build : V14.0.2.0.TKLMXTC
Build Date : Thu May 25 06:16:34 UTC 2023
Device : Redmi Note 10s
MIUI Build : V14.0.2.0.TKLMXTC
MIUI Region : rosemary_mx_tc_global
MIUI Locale : en-GB
Checking lockstate... LOCKED
Reading unlock data... OK
Unlocking bootloader... OK
Disabling MiCloud... OK
Resetting MiCloud... SKIP (not found)
Erasing FRP... OK
Please do not relock bootloader after this operation!
UNLOCKTOOL 2024.06.07.0
Elapsed time : 18 seconds
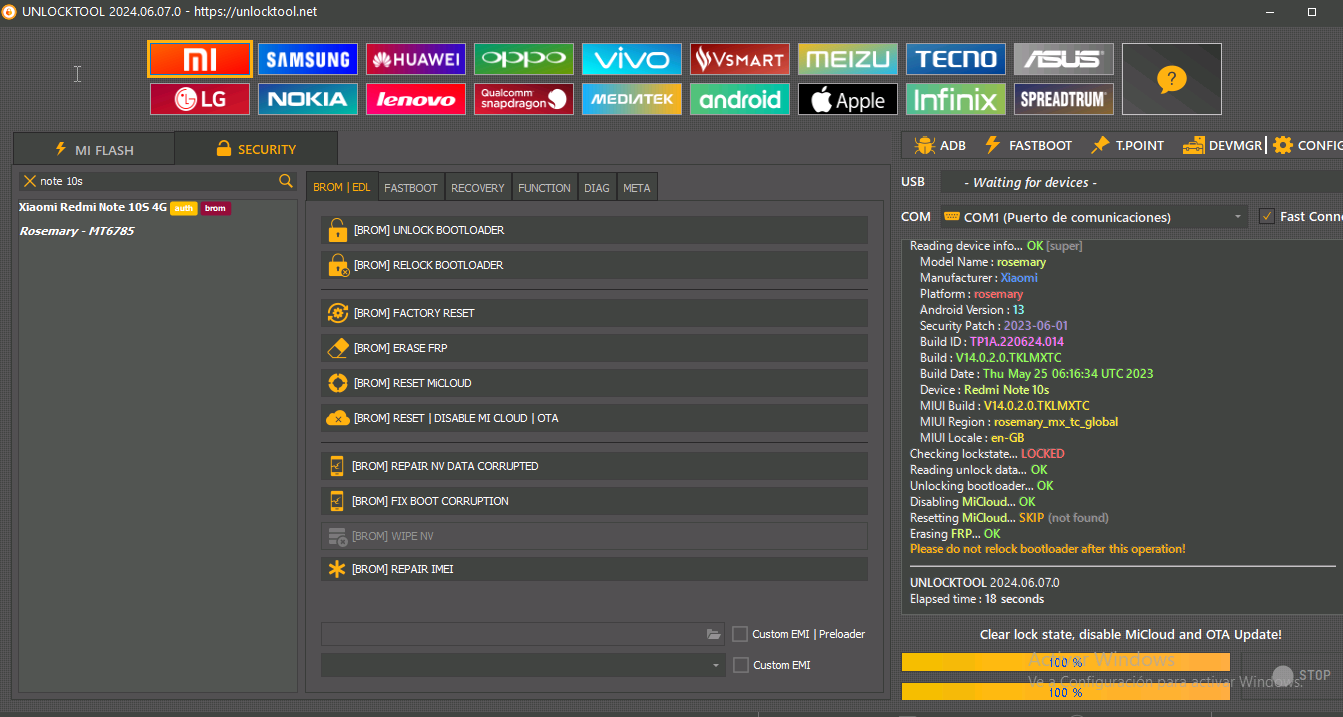
Direct Unlock OPPO A54 CPH2239
Selected model: OPPO CPH2239 (OPPO A54)
Operation: Read Codes
Software version: 6.10
Work ID: 29630118
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM24 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E5]
Active sec flags: [SBC DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Install LibUSB... OK
Waiting for device... OK
Open port... OK
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM24 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xDE91D612, 0x84C11270, 0xEB756089, 0x289FF38A
Get Chip ID... [MT6765]
Get SOC ID... [A1813026142AC122E9975D8FDFDB5A32A3A99CD8ED5DFEA390B1CC2A2CBB8F18]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [7]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x13014E53304A394B3910278DA05F5845
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: S0J9K9
EMMC_ID : 0x13014E53304A394B3910278DA05F5845
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0001000000 (16.00Mb)
EMMC_USER : 0x1D1F000000 (116.48Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x0100000000 (4.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : OPPO
Product Manufacturer : alps
Product Model : CPH2239
Product Name : vnd_oppo6765
Product Device : oppo6765
Product Board : oppo6765
Board Platform : mt6765
Build ID : RP1A.200720.011
Build Date : Tue Feb 8 15:34:11 CST 2022
Display ID : CPH2239_11_C.18
Security Patch : 2022-02-05
Version SDK : 30
Version Release : 11
Version Codename : REL
Firmware Version : 1644304518397
Userdata FS Type : EXT4
Read security partition from phone... OK
Read security files... OK
Calculating... OK
Read lock info... OK
N Code : 12345678
NS Code : 56781234
SP Code : 11112222
C Code : 33334444
SIM Code : 55556666
NS_SP Code: 77778888
SIM_C Code: 99990000
Read Codes done!
Selected model: OPPO CPH2239 (OPPO A54)
Operation: Unlock network
Software version: 6.10
Work ID: 29630487
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM24 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E5]
Active sec flags: [SBC DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM24 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xDE91D612, 0x84C11270, 0xEB756089, 0x289FF38A
Get Chip ID... [MT6765]
Get SOC ID... [A1813026142AC122E9975D8FDFDB5A32A3A99CD8ED5DFEA390B1CC2A2CBB8F18]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [7]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x13014E53304A394B3910278DA05F5845
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: S0J9K9
EMMC_ID : 0x13014E53304A394B3910278DA05F5845
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0001000000 (16.00Mb)
EMMC_USER : 0x1D1F000000 (116.48Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x0100000000 (4.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : OPPO
Product Manufacturer : alps
Product Model : CPH2239
Product Name : vnd_oppo6765
Product Device : oppo6765
Product Board : oppo6765
Board Platform : mt6765
Build ID : RP1A.200720.011
Build Date : Tue Feb 8 15:34:11 CST 2022
Display ID : CPH2239_11_C.18
Security Patch : 2022-02-05
Version SDK : 30
Version Release : 11
Version Codename : REL
Firmware Version : 1644304518397
Userdata FS Type : EXT4
Read security partition from phone... OK
Read security files... OK
Read NVDATA files... OK
Calculating... OK
Read lock info... OK
Read partition "nvdata"... OK
Read partition "protect1"... OK
Read security files... OK
Read NVDATA files... OK
Read IMEI... OK
Unlock... OK [DF1, DF2, GB1, GB2, SM, OPL]
Write lock info... OK
Write security partition to phone... OK
Network Unlock done!
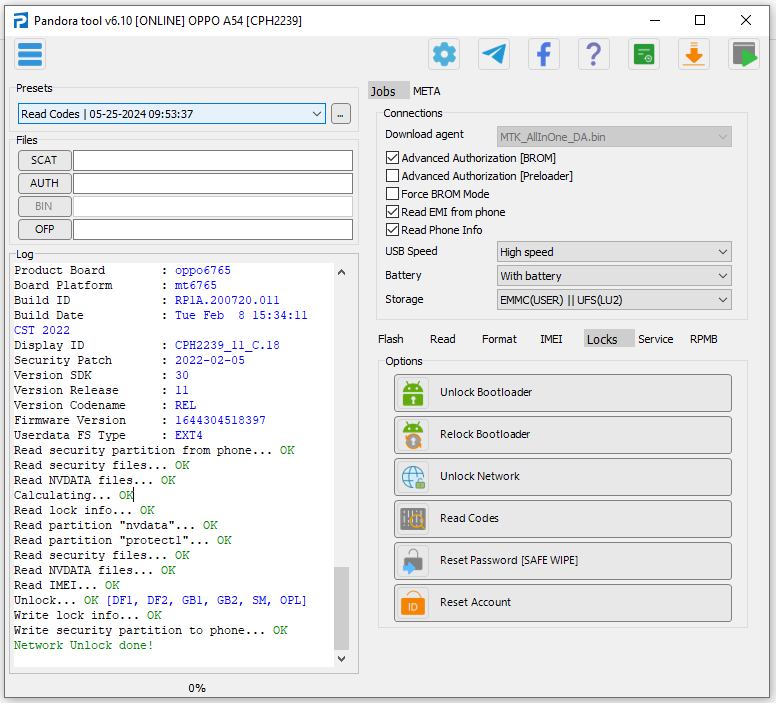
FRP Motorola E5 XT1944-3
Searching fastboot device ...
Device found
Reading device Info ...
Modal : XT1944-3
IMEI : 355561091633265
Version : 0.5
Bootloader : moto-msm8917-BE.4F
Stroage Type : emmc
Ram : 2GB SAMSUNG LP3 DIE=8Gb M5=01 M6=06 M7=00 M8=1F
UID : BAF3BB1B00000000000000000000
Relased Date : 06-12-2018
CPU : MSM8917
Serial No. : ZY322SC6B8
Cid : 0x0032
Secure : yes
eMMC : 16GB SAMSUNG QE63MB RV=08 PV=03 FV=0000000000000003
Warranty Void : no
Kernel Version : Linux version 3.18.71-perf-gc1d4a268e3b8
Setting Factory Mode... Done
Connecting to device... OK
Android Version :
Bootloader : moto-msm8917-BE.4F
Baseband :
Connecting to device... OK
Android Version :
Bootloader : moto-msm8917-BE.4F
Baseband :
Model : moto e5
Manufucture : motorola
Android Version : 8.0.0
Android OS : Oreo
CPU : armeabi-v7a
Security Patch : 2020-05-01
Platform : msm8937
Hardware : qcom
Board : msm8937
Bootloader : 0xBE4F
USB Config : usbnet,adb
User : hudsoncm
Display ID : OPPS27.91-176-11-16
Build ID : OPPS27.91-176-11-16
Build Date : Mon Apr 27 13:12:40 CDT 2020
Build Tags : release-keys
LCD Density : 320
Data Encryption : encrypted
Resetting Frp..... DONE
All done Successfully.
UAT PRO : 170.01 | 22 - May - 2024 [ 10:47:41 AM ] MEXICO
Elapsed Time : 3 minutes 12 seconds

Direct Unlock LG STYLOS 4 LG-Q710AL Bost Mobile
Unlock Service
- Connecting ... [ LGQ710ALY599S4LR99 ]
- Model: LG-Q710AL
- IMEI: 35538209088293
- Carrier ID: SPR
- Security Patch: 2018-11-01
- Software: Q710P11e
- Android Version: 8.1.0
- SIM: Unknown
- SIM Status: ABSENT
- USB Config: charge_only,adb
- Check Device Server Info : OK
- This Operation Will Take 3 Credits
- Prepare Device : OK
- Initialize Device : OK
- Read Simlock Security : OK
- Calculate Simlock Blob : OK
- Wait For Server : OK
- Unlock : OK
# You Should Reboot Device Manually
# Elapsed Time [00:13]
# Operation ID : 2962651
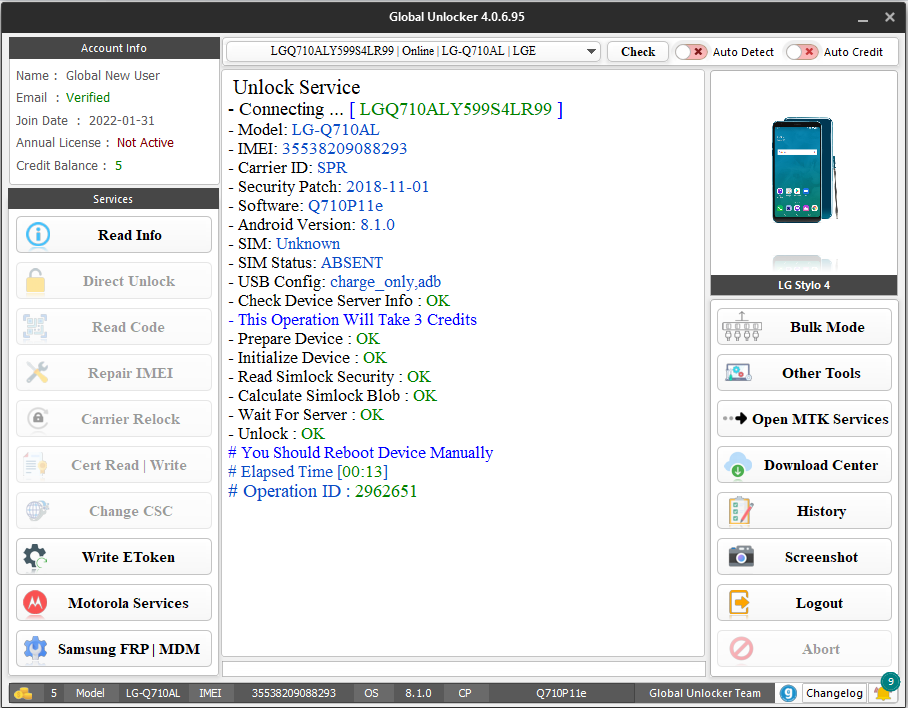
Samsung SM-A145M by Global Unlocker
Costo 8 Creditos
CPU EXYNOS 3830
Press button Samsung FRP / MDM seleccionar modo Samsung primera opcion
* # 0 * #
Remove FRP Service
- Search For Samsung MTP USB Device : OK
- Connect To [COM40] : OK
- Reading info : OK
- Model: SM-A145M
- Baseband: A145MUBS4AWJ2
- Software: A145MUBS4AWJ2
- Carrier: TPA
- Serial Number: R58W30FS8EX
- IMEI: 35298340215052
- Device ID: CDV003CCCD095C9
- Check Status : TRIGGERED
- Check If Service Available : OK
- This Operation Will Take 8 Credits
- Connect To Server : OK
- Read Device Lock Data : OK
- Hash ID : [0x7C031D3A]
- Get Data From Server : OK
- Remove FRP Lock : OK
- Check FRP Lock : OK
- Reboot : OK
# Elapsed Time [00:12]
# Operation ID 2955397
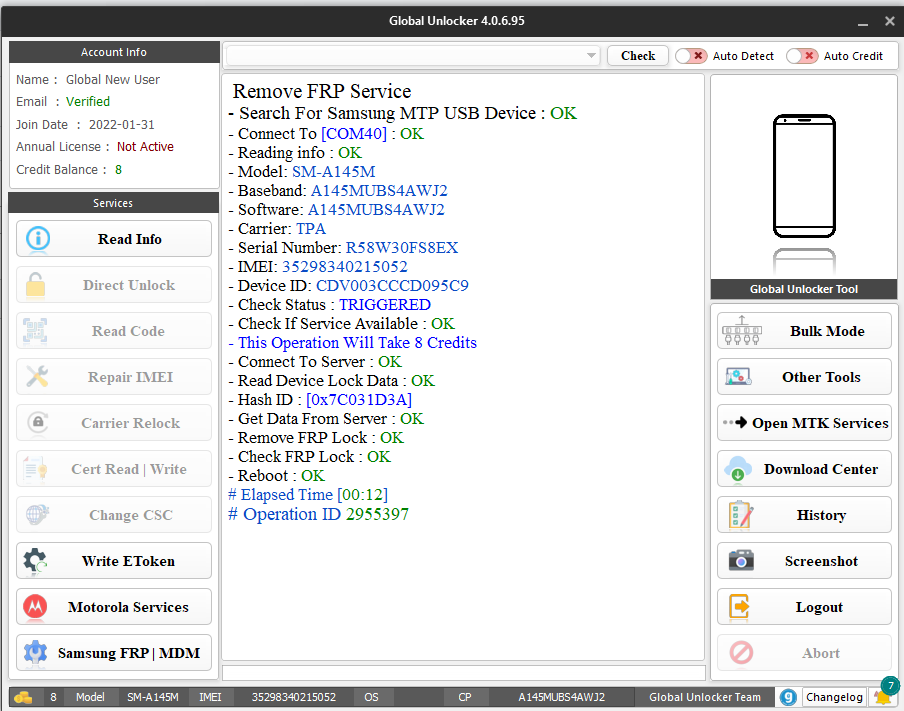
FRP Samsung SM-A145M by Chimera Tool
CPU INSIDE - EXYNOS 3830
Test Point

Chimera Mobile Phone Utility version: 38.99.1217 @ 2024-04-07
Reset FRP lock started
Unable to detect IMEI number.
Gathering phone info...
Collecting information. Be patient! Do NOT disconnect the phone!
Model: SM-A145M
Carrier ID: TPA
Sales Code: TPA
Country Code: PANAMA
Timezone: GMT
Android Version: 13 [TP1A.220624.014] [SDK 33]
Build Date: Tue Apr 11 01:37:12 KST 2023
PDA Version: A145MUBS1AWD1 [april 2023, rev1]
Phone Version: A145MUBU1AWB2 [february 2023, rev2]
CSC Version: A145MOWO1AWB6 [february 2023, rev6]
Board Platform: ERD3830
Modem Platform: SHANNON318
Network Type: GSM
SIM Status: LOADED,LOADED
Multisim Config: DSDS
Warranty Bit: 0
Security Patch: 2023-04-01
Em Did: 200B35AF45CA0811
Resetting FRP...
Resetting FRP...
To complete resetting FRP, go to 'Settings/General management/Reset' then select 'Factory data reset'
Restarting phone
Successfully finished.
Finished at local time: [04.07.24 17:13:42]
WorkID: 269534335
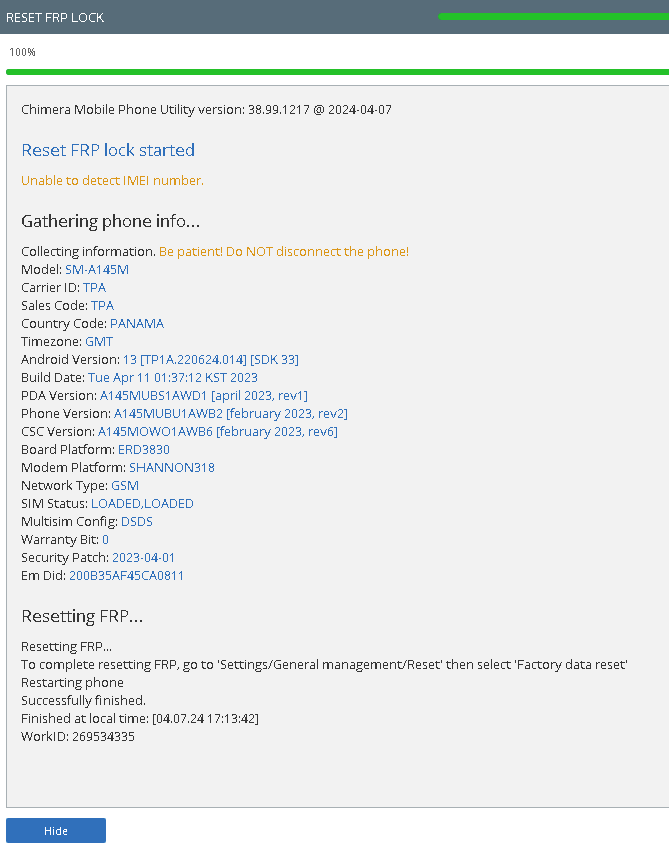
FRP Samsung SM-A025M
Conectar Test Point + Cable
ERASE FRP Selected Platform : SC9863A_32_Bypass
Connect Testpoint or hold VOL DOWN! Instruction here!
Waiting for device... COM68 (SPRD U2S Diag)
USB : USB\VID_1782&PID_4D00\5&1B14D878&0&3
Initializing loader... OK
Protocol : SPRD3
Sending payload... OK
Sending auth data... OK
Sending preloader1... OK
Sending preloader2... OK
Booting loader, please wait... OK
Boot ver: Spreadtrum Boot Block version 1.1
Sending FDL1... OK
Sending FDL2... OK
Reading Serial Number... N.A
Reading partitions info... OK [56] [1024]
Reading device info... OK [super]
Model Name : SM-A032M
Product Name : a3coreub
Manufacturer : samsung
Android Version : 12
Security Patch : 2023-06-01
Build ID : SP1A.210812.016.A032MUBS2BWG1
Build Date : Thu Jul 13 05:46:17 KST 2023
Code Name : SM-A032M
PDA : A032MUBS2BWG1
Erasing FRP... OK
Erasing FRP... OK
UNLOCKTOOL 2024.02.27.0
Elapsed time : 42 seconds
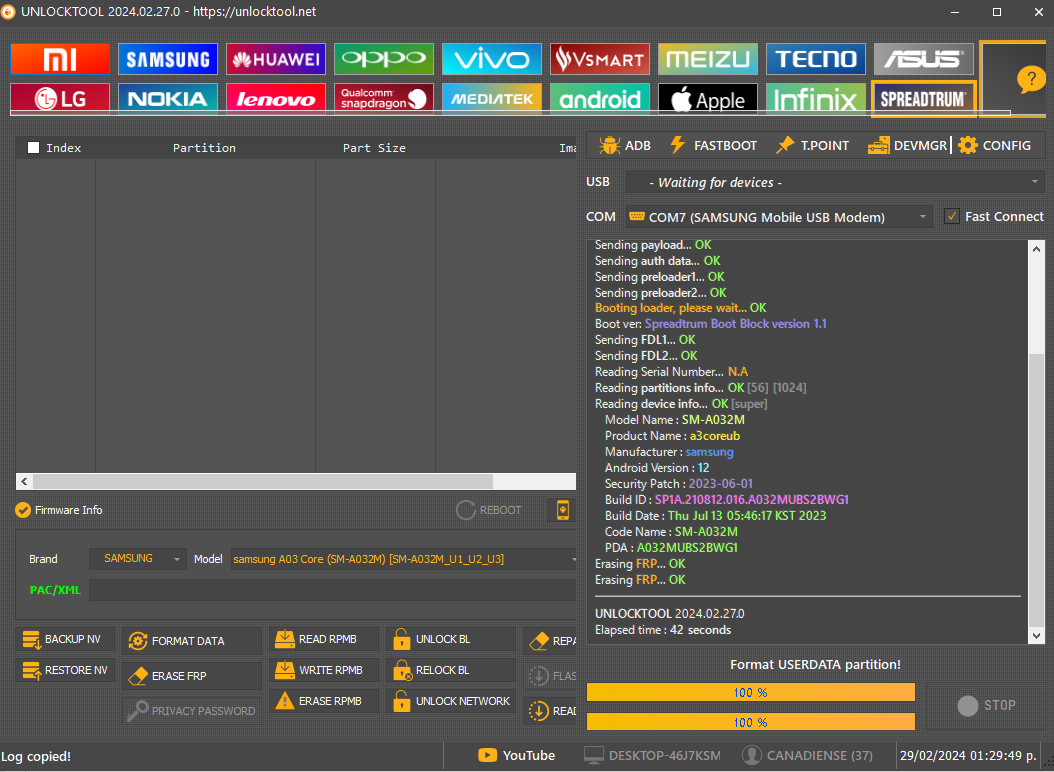
SM-A042M
Work ID: 00000000018EAB16
Starting Unlock MDM (Apr.2023)
Selected model: SM-A042M
Make factory data reset and connect the phone on first page of activation stage to PC via USB.
Phone must be in Setup Wizard mode
Connect powered-on device to PC!
Searching modem port...
OK
Input IMEI: 351536631170931
Input SN: R9PTB0943KX
Connecting to server...
Username: octopus038
Your balance: 50 credits
Sending device information..
OK
Choose unlock method!
QR code method choosen!
Please check device using this QR before unlocking!
Follow these steps :
1. In Android Setup Wizard mode tap on the blank space 6 times.
2. Scan this QR code to install MDM Guard service on your device.
3. Connect to Wi-Fi.
4. Follow the instructions on the screen.
5. Allow USB debugging mode when prompt appears on the screen.
Your account will be charged for 100 credits. Do you want to continue?
Searching ADB devices...
Press "OK" button on the device to allow USB debugging
OK
QR Code is scanned
Reading info...
Detected model: SM-A042M
Fingerprint: samsung/a04eub/a04e:12/SP1A.210812.016/A042MUBU1AVJ2:user/release-keys
Firmware compiled date: Wed Oct 5 23:11:52 KST 2022
PDA version: A042MUBU1AVJ2
CSC version: A042MOWO1AVJ2
SW version: A042MUBU1AVJ1
Build number: A04E_LTN_OPEN
Phone SN: R9PTB0943KX
Android version: 12 (SP1A.210812.016)
Sales code: MXO
Carrier Id: MXO
Country: Mexico
HW platform: mt6765
HW Chip: mt6765
HW Modem: REV1.0
Security patch level: 2022-10-01
Warranty Void: 0
Codename: a04eub
SIM 1 status: ABSENT
SIM 2 status: ABSENT
Modem board: MT6768
Starting exploit...
Activating service...
Using method #2
Warning: After rebooting the device, a MDM lock may appear. MDM Guard service will turn off the screen and the MDM lock will disappear. This may happen a few times after reboot.
MDM Guard service was activated.
Complete the Setup Wizard on the device.
MDM Guard service will restrict OTA updates on your device to prevent relock.
Unlock MDM (Apr.2023) done
Execution time 14 minute(s) 22 second(s)
Performed by 4.2.8 Software version.
FRP Vivo Y11s
Hacer Test Point
[EDL] ERASE FRP
Selected Model :
Vivo Y11s
Code Name :
PD2042F
Operation :
Erase FRP [5]
Authenticating...
OK
Retrieving data...
OK
[270.68 KiB]
Initializing data...
OK
Waiting for
HS-USB QDLoader 9008
...
COM74
Connecting to device...
OK
Handshaking...
OK
Reading bootloader info...
OK
Serial :
4181427947
SoC : [
Snapdragon 460
] [
SM4250-AA
] [
0x001360E1
]
OEM :
Vivo [0x0073]
Model :
Unknown [0x0000]
PK_HASH[0] : A7DF36FFD7AB557C67A6C26675E2795C
PK_HASH[1] : 922CF671308CFD7169BEDB84424C862B
Writing flash programmer...
OK
Connecting to flash programmer...
OK
Configuring device...
OK
Firehose config :
eMMC
[Sector:
512
] [Target:
0
] [Host:
1048576
]
Erasing
FRP
...
OK
Rebooting...
OK
UNLOCKTOOL
2024.01.27.0
Elapsed time :
44 seconds
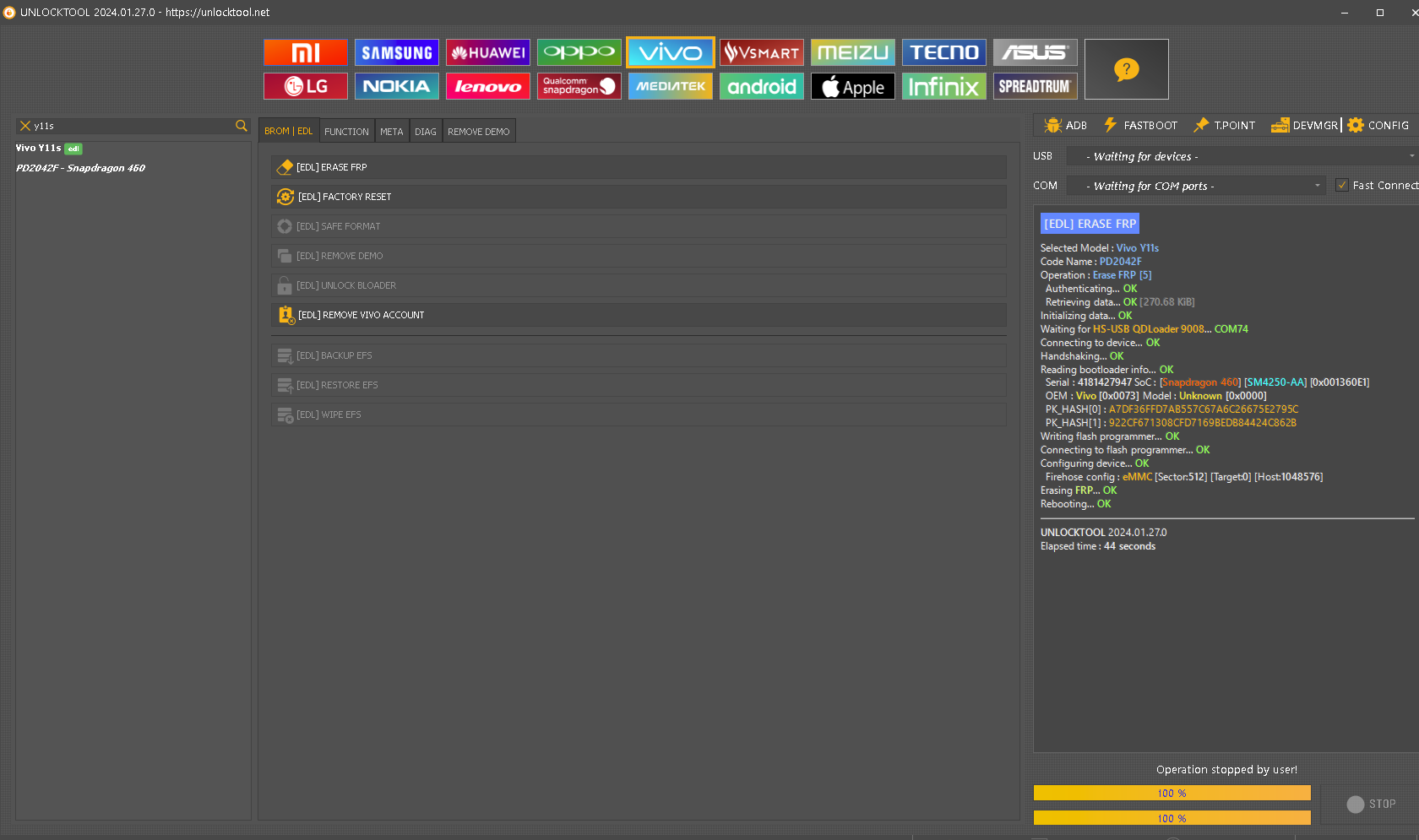
Como Flashear Motorola XT
- Tener instalados los drivers motorola
- Cable USB
- Volumen menos - insertar cable o power on
- mfastboot.exe y archivos adb files juntos en tu computadora es MFastboot el fastboot normal no funciona
revisar este archivo que viene dentro del firmware o flash
vamos a convertir estos parametros en un archivo listo para flashear cualquier Motorola
<?xml version="1.0" ?>
<flashing>
<header>
<phone_model model="surnia_lra"/>
<software_version version="surnia_lra-user 5.1 LPI23.29-23 33 release-keysM8916_2020604.09.03.21.10R"/>
<subsidy_lock_config MD5="00b1a7c46832ca619f9090d3fc80ecce" name="slcf_rev_b_default_v1.0.nvm"/>
<sparsing enabled="true" max-sparse-size="268435456"/>
<interfaces>
<interface name="AP"/>
</interfaces>
</header>
<steps interface="AP">
<step operation="getvar" var="max-sparse-size"/>
<step operation="oem" var="fb_mode_set"/>
<step MD5="8977094e6633500a3db3d4ef71d8639b" filename="gpt.bin" operation="flash" partition="partition"/>
<step MD5="c3f07afe7cd06ffeadffc8d098748e8e" filename="bootloader.img" operation="flash" partition="bootloader"/>
<step MD5="af89b4f5f32b6a16e6b8611e5b7051e0" filename="logo.bin" operation="flash" partition="logo"/>
<step MD5="376dbd65a8e59f804b6a534c6c6ca937" filename="boot.img" operation="flash" partition="boot"/>
<step MD5="f191d273b9e340bc961b83c4b9841dc7" filename="recovery.img" operation="flash" partition="recovery"/>
<step MD5="a58212b860f0aef856278c523c175d60" filename="system.img_sparsechunk.0" operation="flash" partition="system"/>
<step MD5="55b8aa132d2166355eb12ee925b22fb0" filename="system.img_sparsechunk.1" operation="flash" partition="system"/>
<step MD5="279a20e3f8aae29817e6ed99f62bd446" filename="system.img_sparsechunk.2" operation="flash" partition="system"/>
<step MD5="320da2f8ccd308c3333025fe161ffff9" filename="system.img_sparsechunk.3" operation="flash" partition="system"/>
<step MD5="f2ef0c98b99828612b87fd564f2a2cdd" filename="system.img_sparsechunk.4" operation="flash" partition="system"/>
<step MD5="e45d1b47fa90354f5a343a4b30353681" filename="system.img_sparsechunk.5" operation="flash" partition="system"/>
<step MD5="ae978e15a3e18dde72f7f7570bd7259b" filename="NON-HLOS.bin" operation="flash" partition="modem"/>
<step operation="erase" partition="modemst1"/>
<step operation="erase" partition="modemst2"/>
<step MD5="f7338299fb59a5fb5840f5c8658a2265" filename="fsg.mbn" operation="flash" partition="fsg"/>
<step operation="erase" partition="carrier"/>
<step operation="erase" partition="cache"/>
<step operation="erase" partition="userdata"/>
<step operation="oem" var="fb_mode_clear"/>
</steps>
</flashing>
Windows + R
Notepad.exe
Ingresar al archivo todo las configuraciones
empieza aqui
mfastboot getvar max-sparse-size
mfastboot oem fb_mode_set
mfastboot flash partition gpt.bin
mfastboot flash bootloader bootloader.img
mfastboot flash motoboot motoboot.img
mfastboot flash logo logo.bin
mfastboot flash boot boot.img
mfastboot flash recovery recovery.img
mfastboot.exe flash system system.img_sparsechunk.0
mfastboot.exe flash system system.img_sparsechunk.1
mfastboot.exe flash system system.img_sparsechunk.2
mfastboot.exe flash system system.img_sparsechunk.3
mfastboot.exe flash system system.img_sparsechunk.4
mfastboot.exe flash system system.img_sparsechunk.5
mfastboot flash modem NON-HLOS.bin
mfastboot erase modemst1
mfastboot erase modemst2
mfastboot flash fsg fsg.mbn
mfastboot erase carrier
mfastboot erase cache
mfastboot erase userdata
mfastboot oem fb_mode_clear
mfastboot reboot
Archivo -> Guardar Como -> Guardar como tipo -> Todos los archivos
Nombre del Archivo -> Flash.bat
Despues solo dar doble click al archivo y listo esperar a que termine la instalacion del nuevo software
FRP Samsung SM-S737TL
[COM] REMOVE FRP [2023]
Scanning for device...
COM59
Reading Info...
OK
Model Number :
SM-S737TL
Bootloader :
S737TLUDU1AQF2
Country Code :
TFN
Serial Number :
R28K538NMYF
Unique Number :
CAJ0022C4FE5345
Connecting to device...
OK
Trying method [1]...
OK
Waiting for device...
Model :
SM-S737TL
Manufacturer :
samsung
Platform :
exynos5
CPU Arch :
armeabi-v7a
Android Serial :
520022c4fe534555
Manufacturing Date :
20180531
Security Patch :
2017-06-01
Connection :
mtp,adb
Timezone :
America/Mexico_City
Knox Warranty :
0 - valid
Android Version :
7.0
Android SDK :
24
Build :
NRD90M.S737TLUDU1AQF2
Build Date :
Tue Jun 6 12:56:57 KST 2017
Product Code :
SM-S737TZKATFN
Samsung Serial :
R28K538NMYF
Device Name :
j7popeltetfntmo
Product Name :
j7popeltetfntmo
Code Name :
SM-S737TZKATFN
BL :
S737TLUDU1AQF2
PDA :
S737TLUDU1AQF2
CP :
S737TLUDU1AQF2
CSC :
S737TLTFN1AQF2
Sales Code :
TFN
Removing
FRP
...
OK
UNLOCKTOOL
2024.01.27.0
Elapsed time :
53 seconds
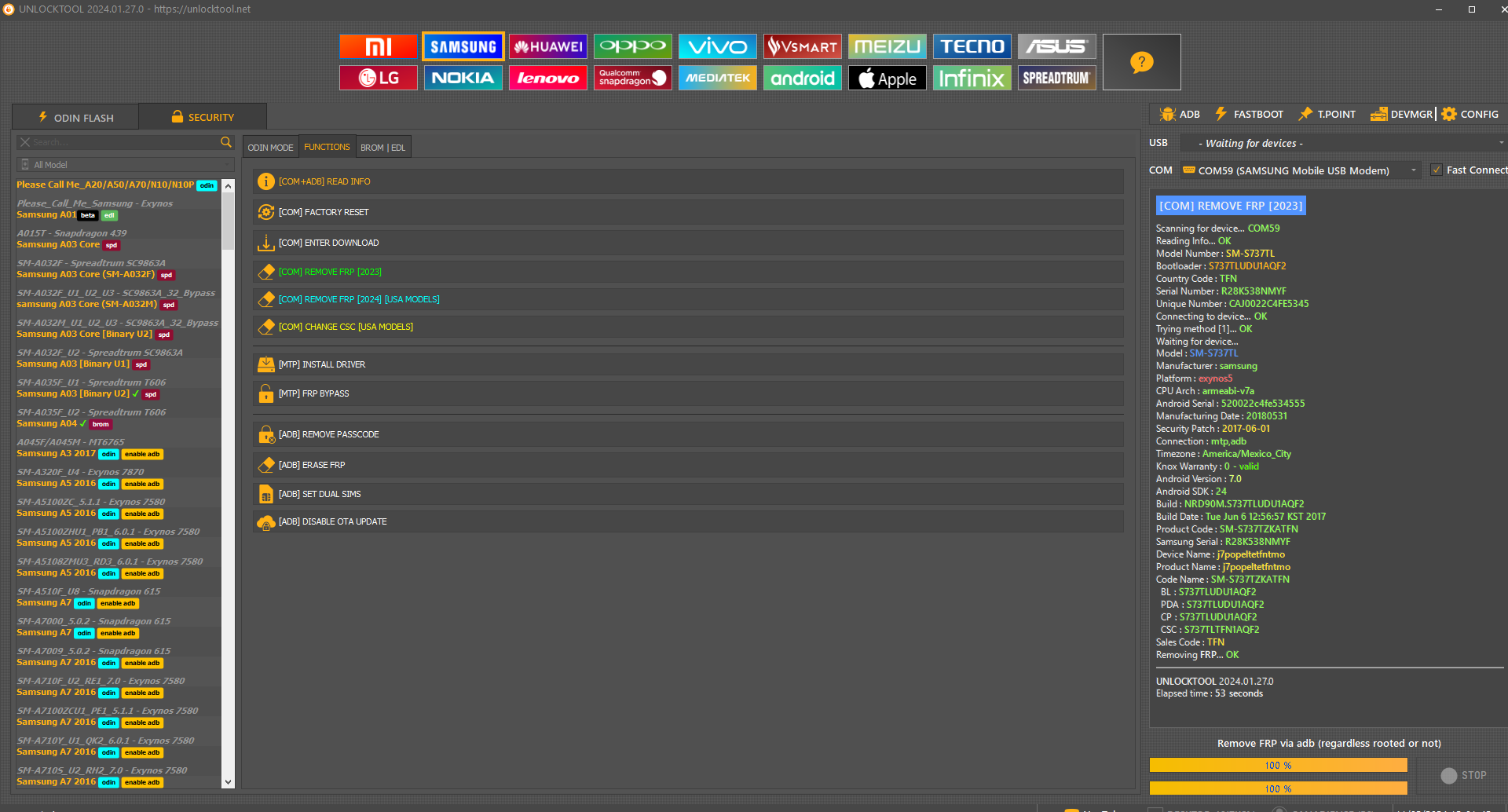
FRP Samsung SM-A146U
Test point SM-A146M

Chimera Mobile Phone Utility version: 38.43.1129 @ 2024-02-10
Printing phone history
Auto Detect
10/02/2024
3:40
PM
Auto Detect
10/02/2024
3:38
PM
Factory reset
10/02/2024
3:32
PM
Auto Detect
10/02/2024
3:31
PM
Auto Detect
10/02/2024
3:26
PM
FRP Remove
Successfully finished.
Finished at local time: [02.10.24 09:02:19]
WorkID: 259113154
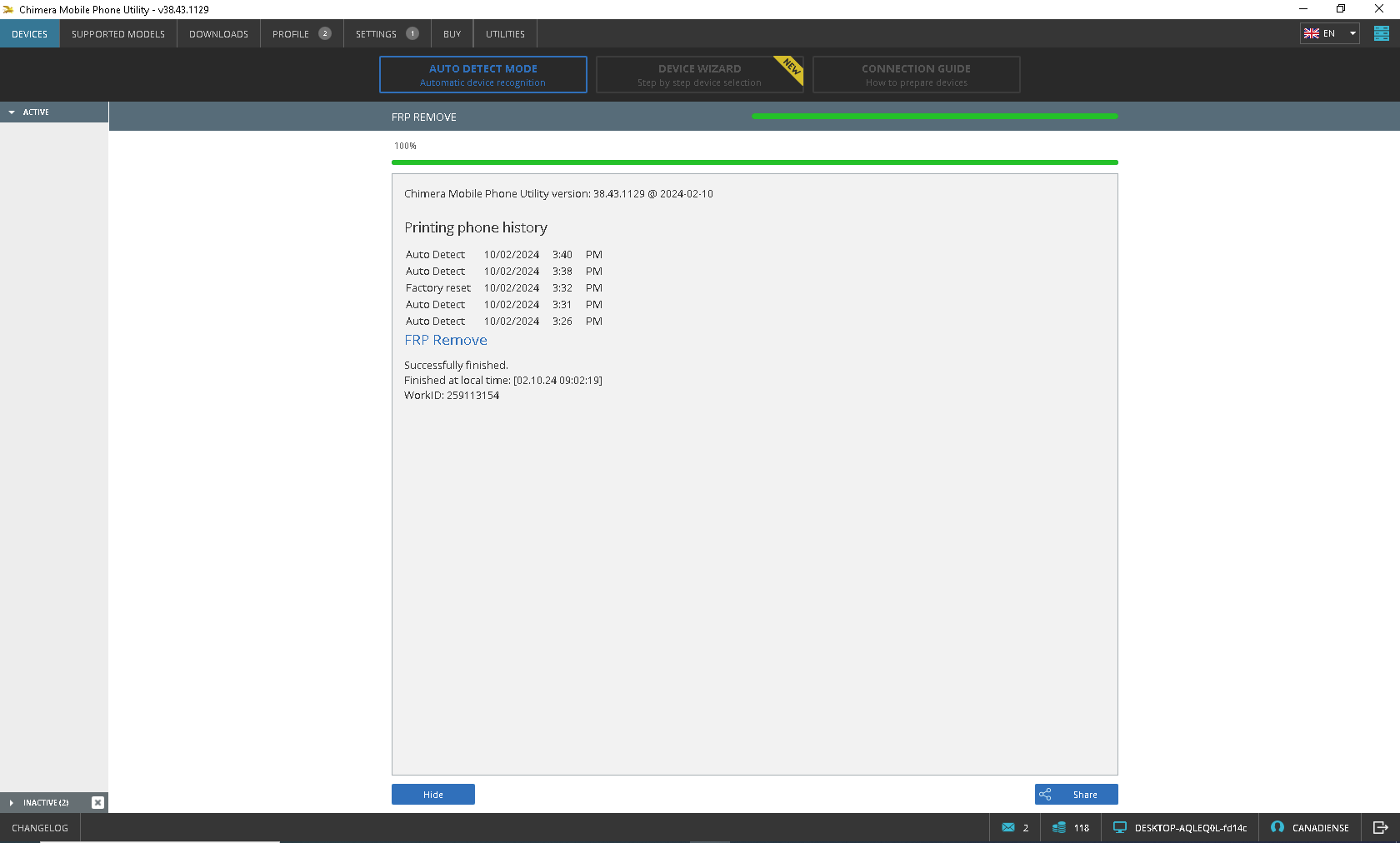
FRP Samsung A20 SM-A205U by Unlock Tool
[COM] REMOVE FRP [2023] Method : [2]
Scanning for device... COM48
Reading Info... OK
Model Number : SM-A205U
Bootloader : A205USQSDBWC2
Country Code : TMB
Serial Number : R58M70YTC9T
Unique Number : CBJ005BCAD40866
Enabling ADB... OK
Waiting for device...
Please accept USB Debugging on your phone!
Model : SM-A205U
Manufacturer : samsung
Platform : universal7904
CPU Arch : arm64-v8a
Android Serial : R58M70YTC9T
Manufacturing Date : 20191115
Security Patch : 2023-02-01
Connection : mtp,adb
Timezone : America/New_York
Android Version : 10
Android SDK : 29
Build : QP1A.190711.020.A205USQSDBWC2
Build Date : Thu Mar 16 12:21:38 KST 2023
Product Code : SM4A205UZKATMB
Device Name : a20p
Product Name : a20psq
Code Name : SM4A205UZKATMB
BL : A205USQSDBWC2
PDA : A205USQSDBWC2
CP : A205USQSDBWC2
CSC : A205UOYNDBWC2
Sales Code : TMB
Removing FRP... OK
UNLOCKTOOL 2024.01.27.0
Elapsed time : 52 seconds
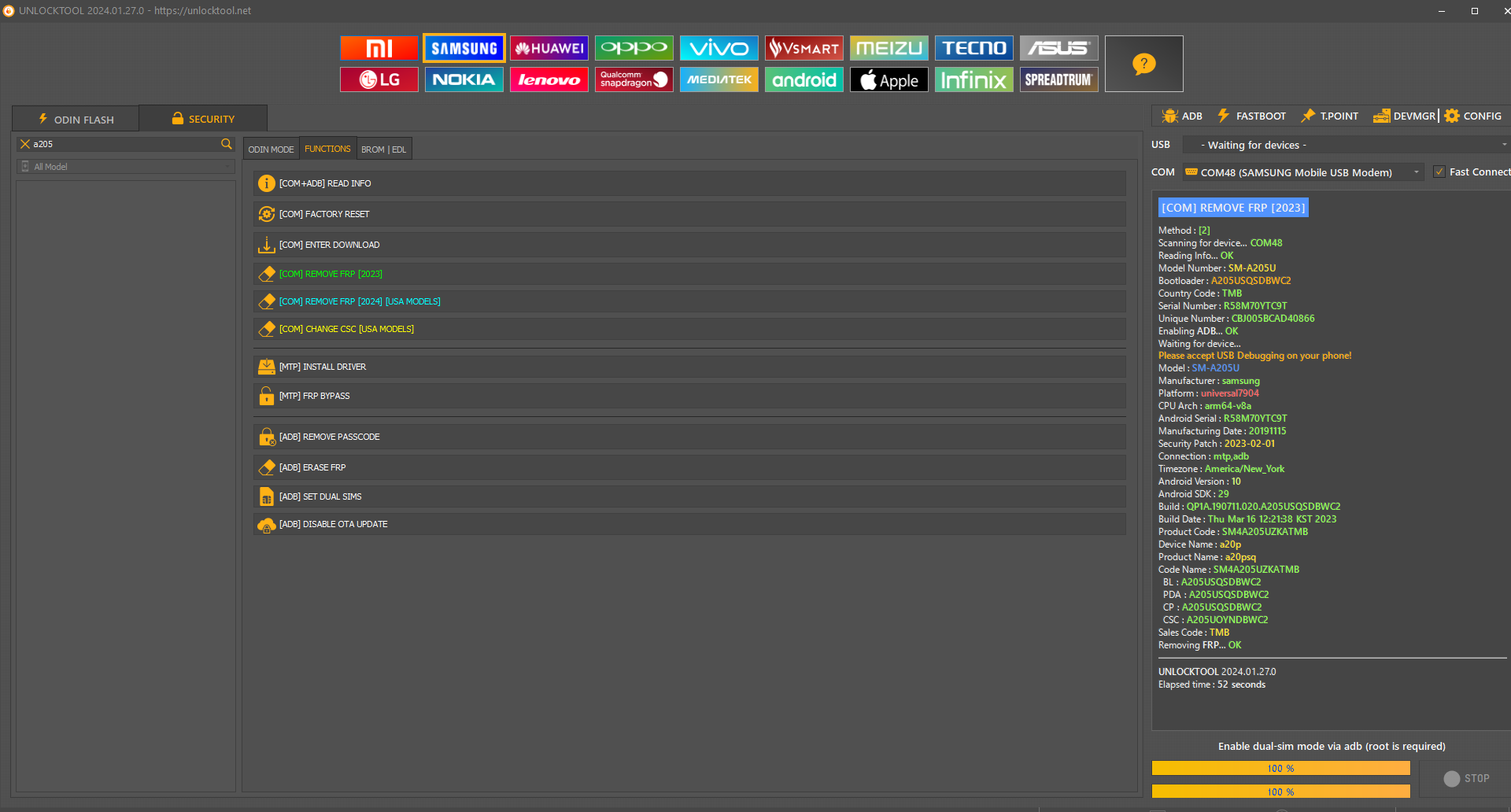
FRP OPPO A15 CPH2185
Selected model: OPPO CPH2185 (OPPO A15)
Operation: Erase FRP
Software version: 6.3
Work ID: 18084608
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,usbser.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM188 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E5]
Active sec flags: [SBC DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,usbser.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM188 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0x87A55CC9, 0x07F1400C, 0xB464618D, 0xAF6325BF
Get Chip ID... [MT6765]
Get SOC ID... [5196F77473B4BA8C62204C01BC08E0FEABABCD663AE4BE520E3BCDB6AC3FFB1F]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [7]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x90014A68423861503E030033DE68C791
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: hB8aP>
EMMC_ID : 0x90014A68423861503E030033DE68C791
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0001000000 (16.00Mb)
EMMC_USER : 0x0747C00000 (29.12Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x00C0000000 (3.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : OPPO
Product Manufacturer : OPPO
Product Model : CPH2185
Product Device : OP4F2F
Product Board : oppo6765
Board Platform : mt6765
Build ID : QP1A.190711.020
Build Date : Fri Nov 26 23:22:35 CST 2021
Display ID : CPH2185_11_A.35
Security Patch : 2021-12-05
Version SDK : 29
Version Release : 10
Version Codename : REL
Userdata FS Type : EXT4
Read partition "frp"... OK
Backup saved to C:/Program%20Files/Z3X/Pandora/Backup/MTK/OPPO_CPH2185%20(OPPO%20A15)/FRP_BACKUP_(2024-1-26_15-42-13)/
Writting FRP data... OK
Erase FRP done!
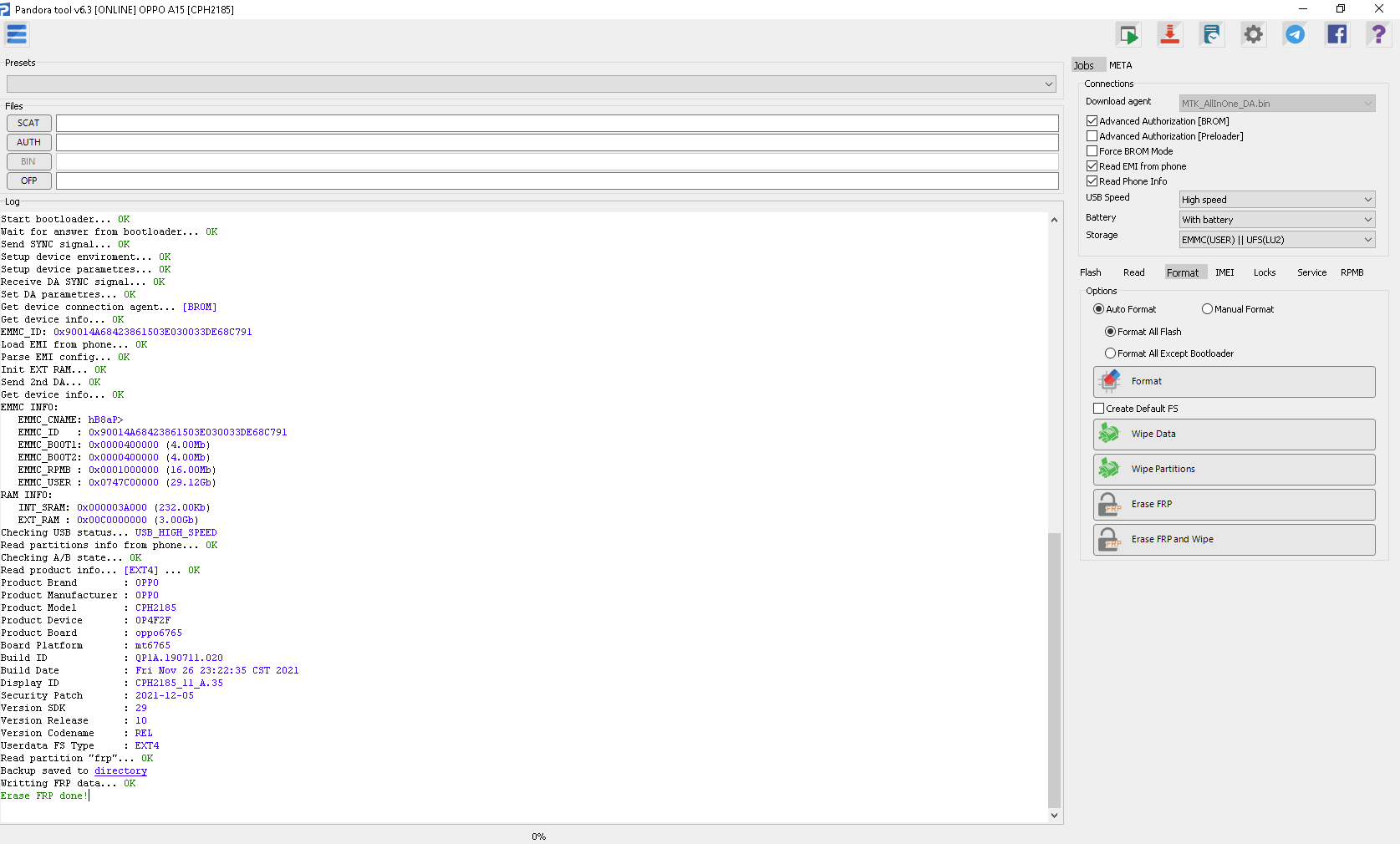
Read Unlock Codes OPPO CPH2185 (OPPO A15) by Pandora Tool
Selected model: OPPO CPH2185 (OPPO A15)
Operation: Read Codes
Software version: 6.3
Work ID: 18084450
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,usbser.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM188 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E5]
Active sec flags: [SBC DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,usbser.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM188 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0x87A55CC9, 0x07F1400C, 0xB464618D, 0xAF6325BF
Get Chip ID... [MT6765]
Get SOC ID... [5196F77473B4BA8C62204C01BC08E0FEABABCD663AE4BE520E3BCDB6AC3FFB1F]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [7]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x90014A68423861503E030033DE68C791
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: hB8aP>
EMMC_ID : 0x90014A68423861503E030033DE68C791
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0001000000 (16.00Mb)
EMMC_USER : 0x0747C00000 (29.12Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x00C0000000 (3.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : OPPO
Product Manufacturer : OPPO
Product Model : CPH2185
Product Device : OP4F2F
Product Board : oppo6765
Board Platform : mt6765
Build ID : QP1A.190711.020
Build Date : Fri Nov 26 23:22:35 CST 2021
Display ID : CPH2185_11_A.35
Security Patch : 2021-12-05
Version SDK : 29
Version Release : 10
Version Codename : REL
Userdata FS Type : EXT4
Read security partition from phone... OK
Read security files... OK
Read lock info... OK
N Code : 12345678
NS Code : 56781234
SP Code : 11112222
C Code : 33334444
SIM Code : 55556666
NS_SP Code: 77778888
SIM_C Code: 99990000
Read Codes done!
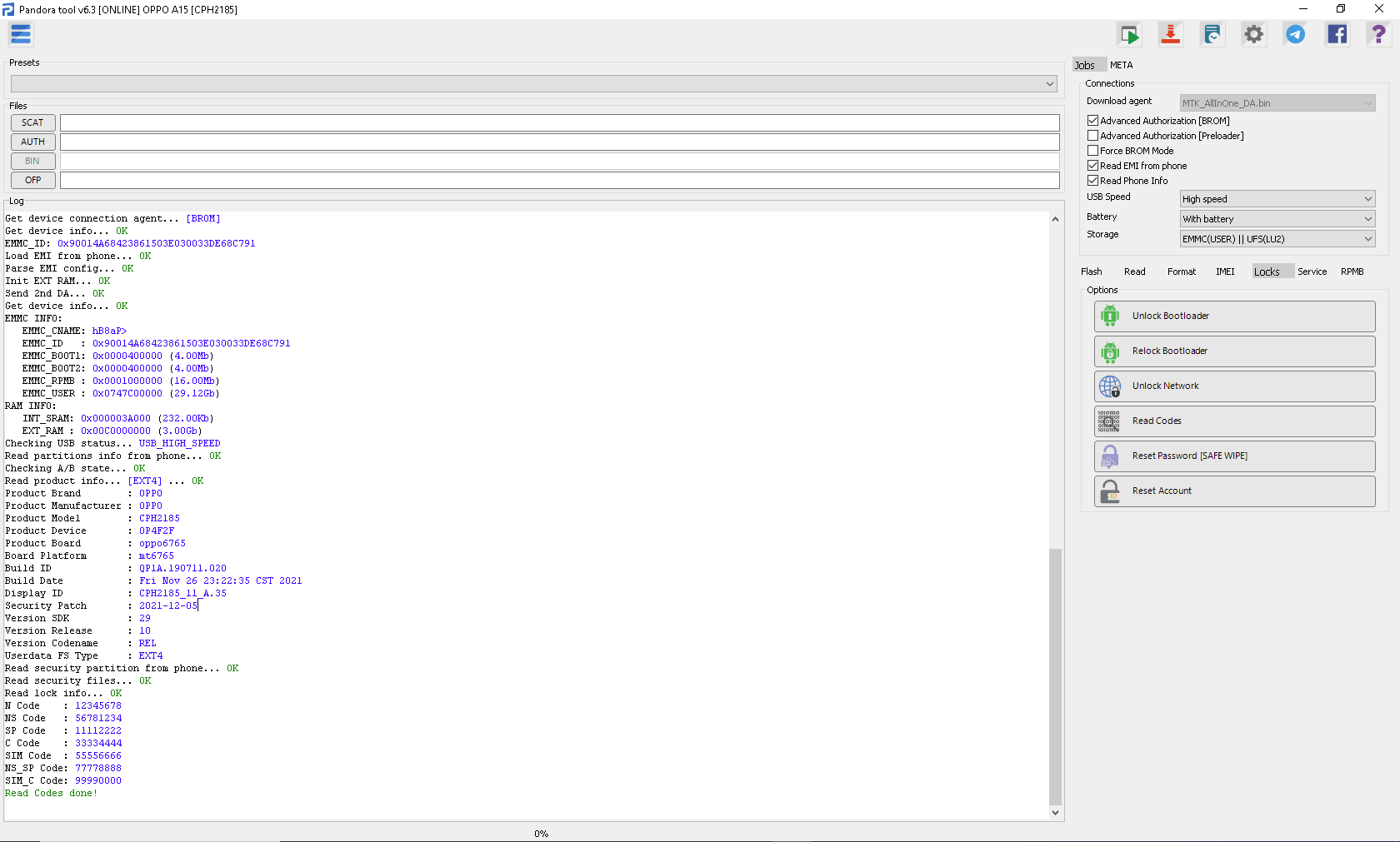
Unlock Alcatel 4052R
Connect the phone powered off with both volume down and up pressed or connect the phone powered off and leave it connected to the usb till it shows the battery/charging screen ;
Phone detected (@oem180.inf,%qcomdevice90080%;Qualcomm HS-USB QDLoader 9008)
Preparing to start flash mode;
Preparing to open COM74
Connecting;
Loading;
Init;
Port opened;
Hello Received;
MSM_ID: 0x009600E1
OEM_ID: 0x0042
MODEL_ID: 0x004D
PK_HASH: B451BD3B38D9EDD197CCADF0838D5F8652B8F4642E5BF70411C8153D1AC40ADBB451BD3B38D9EDD197CCADF0838D5F8652B8F4642E5BF70411C8153D1AC40ADBB451BD3B38D9EDD197CCADF0838D5F8652B8F4642E5BF70411C8153D1AC40ADB
BOOT Loaded;
Getting config;
Getting mem info;
Found an eMMC memory size 3.5 GB, target id 8909
IMEI: 01590700319229-0
PTH: 04
PTS: X4O
PROV_ID: 4052R-2AAQUS3-R
SBTADDR: 0C:71:8C:D7:0A:C5
SWIFIADDR: 0C:71:8C:DE:0F:AC
HS_PN: SAA66A0AA12C
SSN: D7LC23CF8OE01DD
Work id: 22021984
Done;
Stype: 00000001
SECURITY: XZX4UAO0CL00 Size: 00000313
Backup saved to: 01590700319229-0
Unlocking;
SIM_LOCK REMOVED !
FRP has been Reset Successfully;
Erase Setup Done;
Erase Done;
Erase Done;
FRPEx Done;
Log file saved to: LOG_25_01_2024_15_07_50.txt
Time needed - 00:00:56
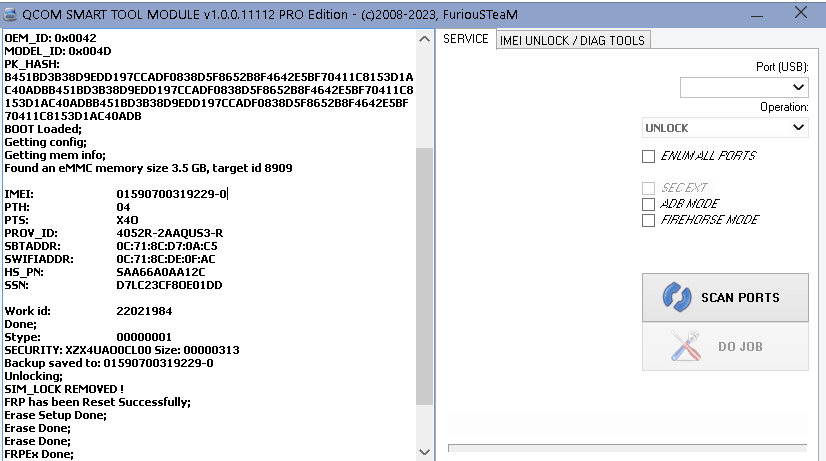
FRP Samsung SM-A045M
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:001667 SourceURL:file%3a%2f%2f
[ODIN] [MTK] ERASE FRP 2023
Scanning port...
OK
Reading Info...
OK
Model :
SM-A045M
Storage Capacity :
32G
Manufacturer :
SAMSUNG
Firmware Version :
4
CSC :
VZW
AP :
A045MUBU1BWB2
Device ID :
13af1567e4b5
Connecting to device...
OK
Device Platform :
MEDIATEK
Backup :
\SAMSUNG_FRP\SM-A045M_W153458300B987E422A9_A045MUBU1BWB2_2024-01-25_14-43-27
Patching FRP...
OK
Waiting for device...
OK
Connecting to device...
OK
Erasing protection...
OK
Erasing
FRP
...
OK
UNLOCKTOOL
2024.01.09.0
Elapsed time :
23 seconds
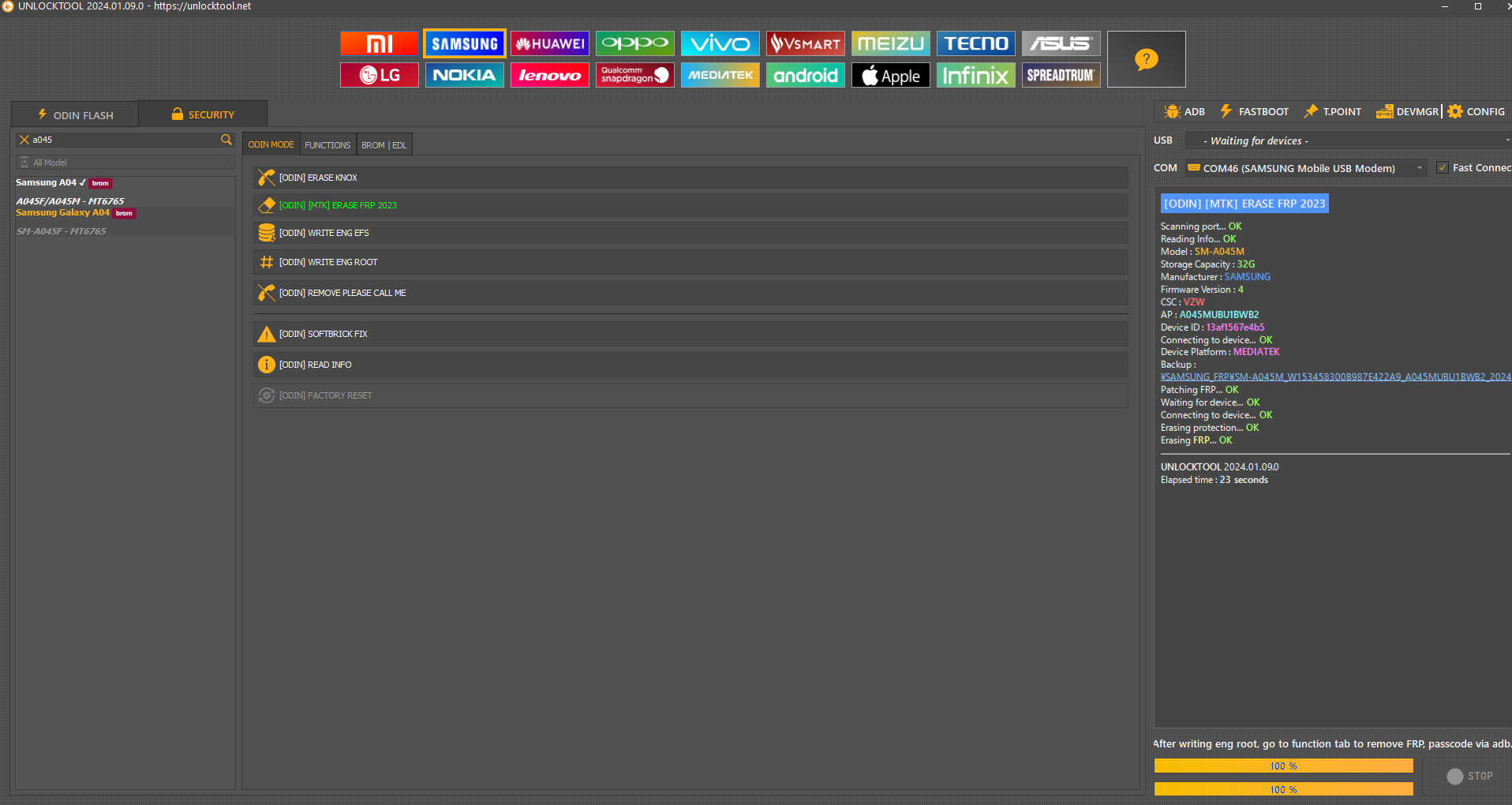
Direct Unlock Huawei Honor X8a CRT-LX3 ATT Mexico by Pandora Box
Selected model: Huawei Mediatek
Operation: Unlock network
Software version: 6.3
Work ID: 17196365
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,usbser.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM39 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0707
Get sec config... OK [000000E5]
Active sec flags: [SBC DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6768]
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,usbser.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM39 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0707
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6768]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0x0B227245, 0xA4D54416, 0x3242E584, 0x6302EB58
Get Chip ID... [MT6768]
Get SOC ID... [61452DD862004892F4A871B2DD0A56FEE6B5E571ECC3CEE45074FCCD1ADAE8D5]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [8]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x13014E47324D323132102CF43ED74A01
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: G2M212
EMMC_ID : 0x13014E47324D323132102CF43ED74A01
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0001000000 (16.00Mb)
EMMC_USER : 0x1D1F000000 (116.48Gb)
RAM INFO:
INT_SRAM: 0x0000070000 (448.00Kb)
EXT_RAM : 0x0100000000 (4.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK [B]
Read product info... [EROFS] ... OK
Product Brand : HONOR
Product Manufacturer : alps
Product Model : k69v1_64_6382_k419
Product Name : vnd_k69v1_64_6382_k419
Product Device : HNCRT-M1
Product Board : CRTL
Board Platform : mt6768
Build ID : SKQ1.210908.001
Build Date : Thu Nov 9 11:48:22 CST 2023
Display ID : System 6.1.0(0KSS)
Security Patch : 2023-11-01
Version SDK : 31
Version Release : 12
Version Codename : REL
Firmware Version : eng.root.20231109.112609
Userdata FS Type : F2FS
Read security partition from phone... OK
Read security files... OK
Read security files... OK
Read lock info... OK
Unlock... OK [DF1, UN]
Write lock info... OK
Write security partition to phone... OK
Network Unlock done!
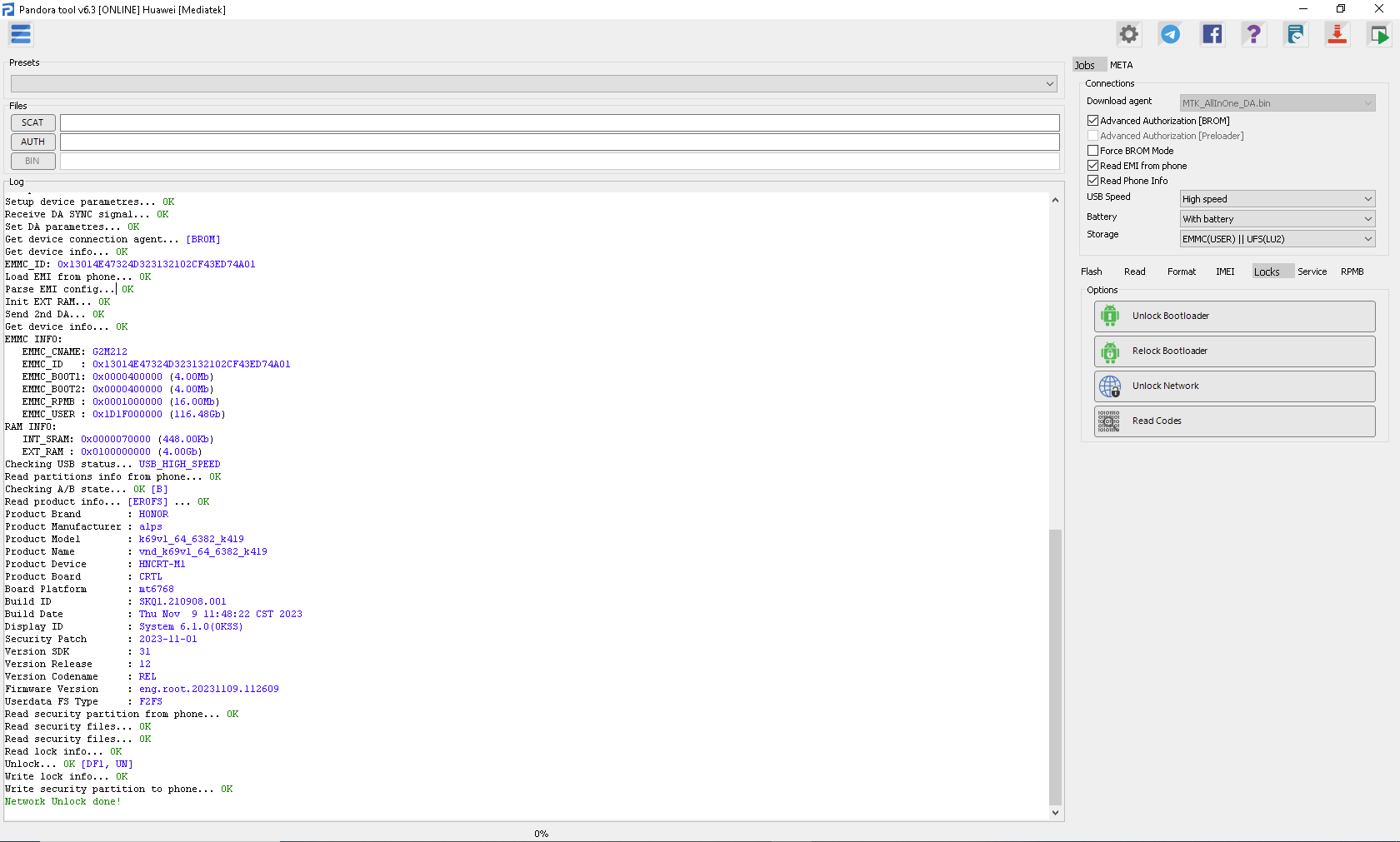
FRP Huawei Y9 Prime 2019 Done by DTPro Tool
Test Point

3:18:42 PM - Selected SOC/Loader : Huawei & Honor HiSilicon|Kriin 710F
3:18:42 PM - Auto Detecting Device Interface..
3:18:42 PM - Device Found : \\?\usb#vid_12d1&pid_3609#6&3492803a&0&4#
3:18:42 PM - Port : COM10 - HUAWEI USB COM 1.0 (COM10)
3:18:42 PM - Device Mode : [USB COM 1.0]
3:18:43 PM - Driver Description : HUAWEI Incorporated, hw_usbvcom.sys
3:18:43 PM - Drivers Date : 11-6-2015
3:18:43 PM - Drivers Version : 2.0.6.725
3:18:43 PM - Waiting for Phone..
3:18:43 PM - Configuring Device Mode..
3:18:43 PM - Writing Boot Block [1 of 1]..
3:18:46 PM - Verifying ok..
3:18:46 PM - Writing Boot Block [2 of 2]..
3:18:48 PM - Verifying ok..
3:18:49 PM - Writing Boot Block [3 of 3]..
3:18:51 PM - Verifying ok..
3:18:51 PM - Selected Storage : Auto
3:18:51 PM - Reading Partition Table..
3:18:51 PM - Partition Count : 71
3:18:51 PM - Userdata : 116.48 GB
3:18:51 PM - Detecting Frp Signature..
3:18:51 PM - Frp Signature Found..
3:18:51 PM - Removing Frp Lock..
3:18:53 PM - Frp Remove Okay..
3:18:53 PM - Note : please press and Hold power On button!..
3:18:53 PM - Note : Hold for 10-15 Seconds for device powering ON!!!
3:18:54 PM - Done..
13/01/2024 4:40:43 PM Initializing..
13/01/2024 4:40:43 PM Connected Device in Fastboot Mode Now..
13/01/2024 4:40:44 PM Model : STK-LX3
13/01/2024 4:40:44 PM Build : STK-L23B 12.0.0.225(C605E2R2P1)
13/01/2024 4:40:45 PM Bootloader : LOCKED
13/01/2024 4:40:45 PM Factory Resetting..
13/01/2024 4:40:45 PM Done!
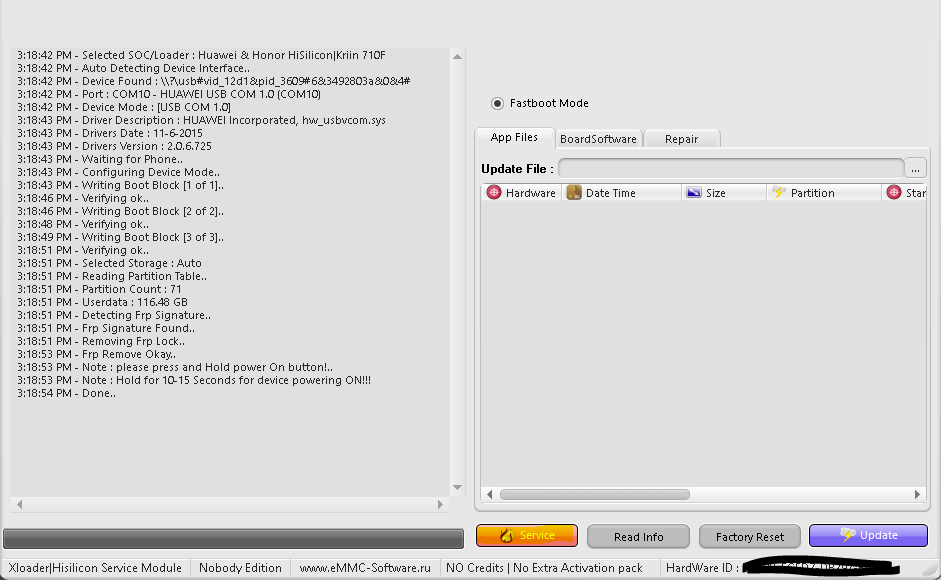
FRP Motorola XT1670 Ultimate Multi Tool UMT PRO
Volumen abajo + boton encendido para fastboot
Port : Fastboot Inteface
Baud Rate : Not Applicable
Device : Motorola
Operation : New FRP Reset
Searching for Device in FastBoot Mode... OK
Reading Phone Information...
Model : XT1670
Boot Ver. : moto-msm8937-B8.09
Baseband : M8937_8000.122.02.40R CEDRIC_LATAM_CUST
Software : Blur_Version.25.11.13.cedric.retail.en.US
IMEI : 351871081087123
CPU : MSM8937
RAM : 2GB SAMSUNG LP3 DIE=8Gb M5=01 M6=05 M7=00 M8=1F
EMMC : 32GB SAMSUNG QX13MB RV=08 PV=07 FV=0000000000000007
Setting Factory Mode... OK
Searching Network Interface... Found
Connecting to device... OK
Model : Moto G (5)
Bootloader : 0xB809
Baseband : M8937_8000.122.02.40R CEDRIC_LATAM_CUST
Build : Blur_Version.25.11.13.cedric.retail.en.US
Android : 7.0
Searching Network Interface... Found
Connecting to device... OK
Model : Moto G (5)
Bootloader : 0xB809
Baseband : M8937_8000.122.02.40R CEDRIC_LATAM_CUST
Build : Blur_Version.25.11.13.cedric.retail.en.US
Android : 7.0
Resetting FRP... OK
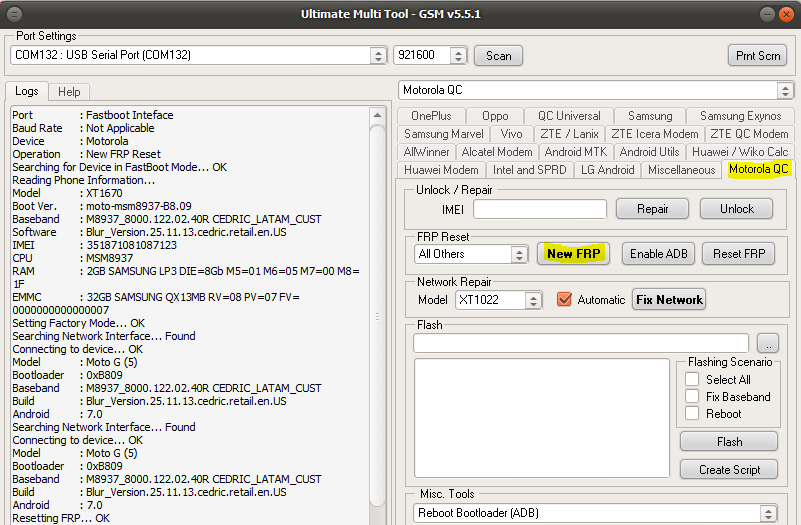
Direct Unlock Motorola M. G PURE XT2163DL
Direct Unlock + FRP
Factory Enabler - 5 Creditos una vez habilitado el commserver habilita el adb y podras quitar FRP
Despues haces el proceso de liberacion
Direct Unlock - 25 Creditos
Using USA Server #2.
Waiting for Device in Factory Mode.....Found!
Reading Information...Done
Android Version: 12 (ellis_trac)
Carrier: TRACFONE
FSG: DFLT_FSG
SN: ZY22FFXS68
XcvrModel: SA78D21306
IMEI #1: 356676309542899
Memory Size: 32GB
HwRev: C100
Battery Level: 87%
SKU: XT2163DL
Firmware: S3RH32.20-42-13-2-3
Model: M. G PURE
Checking Device Connection...Done
Checking Price for Device....Done
Creating Order ID....Done
Operation ID: 1846243
Erasing UTAG IMEI ... Done
Reading Device Configuration ... Done
Wiping IMEI ... Done
Writing IMEI ... Done
New IMEI 1: 356676309542899
Writing New Security ... Done.
Writing UTAG IMEI ... Done
Erasing Factory Mode ... Done
Rebooting to Fastboot ... Done
Elapsed Time: 1:29.66
FRP Huawei Y7 2019 Done by EFT Pro
Huawei test point Y7 2019 FRP Done
Wait for device...
Download port: Qualcomm HS-USB QDLoader 9008 (COM62)
Port: Qualcomm HS-USB QDLoader 9008 (COM62)
Manufacturer: Qualcomm Incorporated
Waiting for server........ OK
Connect to comport... OK
Read chip info... OK
Hardware ID: 0x9A0E1
OEM Private key: 0x6BC369511DA9CADB3A7AF61574F89DB385003D6241BDD1FF573DBA61BF6AE119
Vendor: HUAWEI
Load loader... OK
Send Loader... OK
Ping Device... OK
Load Config... OK
Server ... OK
Get Partition ...
Server ... OK
Get Partition ...
Server ... OK
Get Partition ...
Read Build Prop Info... OK
Manufacturer: UNKNOWN
Android Version: 8.1.0 (Oreo)
Security Patch: 2020-09-01
Build ID: OPM1.171019.011
Build Date: THU AUG 12 15:30:59 CST 2021
Display ID: SYSTEM 8.2.0.036(2E2Y)
Build: b
Read Internal Storage Info... OK
USERDATA: 24.53 GB
USERDATA: ENCRYPTED
Remove FRP Lock... OK
Reboot... OK
Elapsed Time: 19 secs, 934 msecs
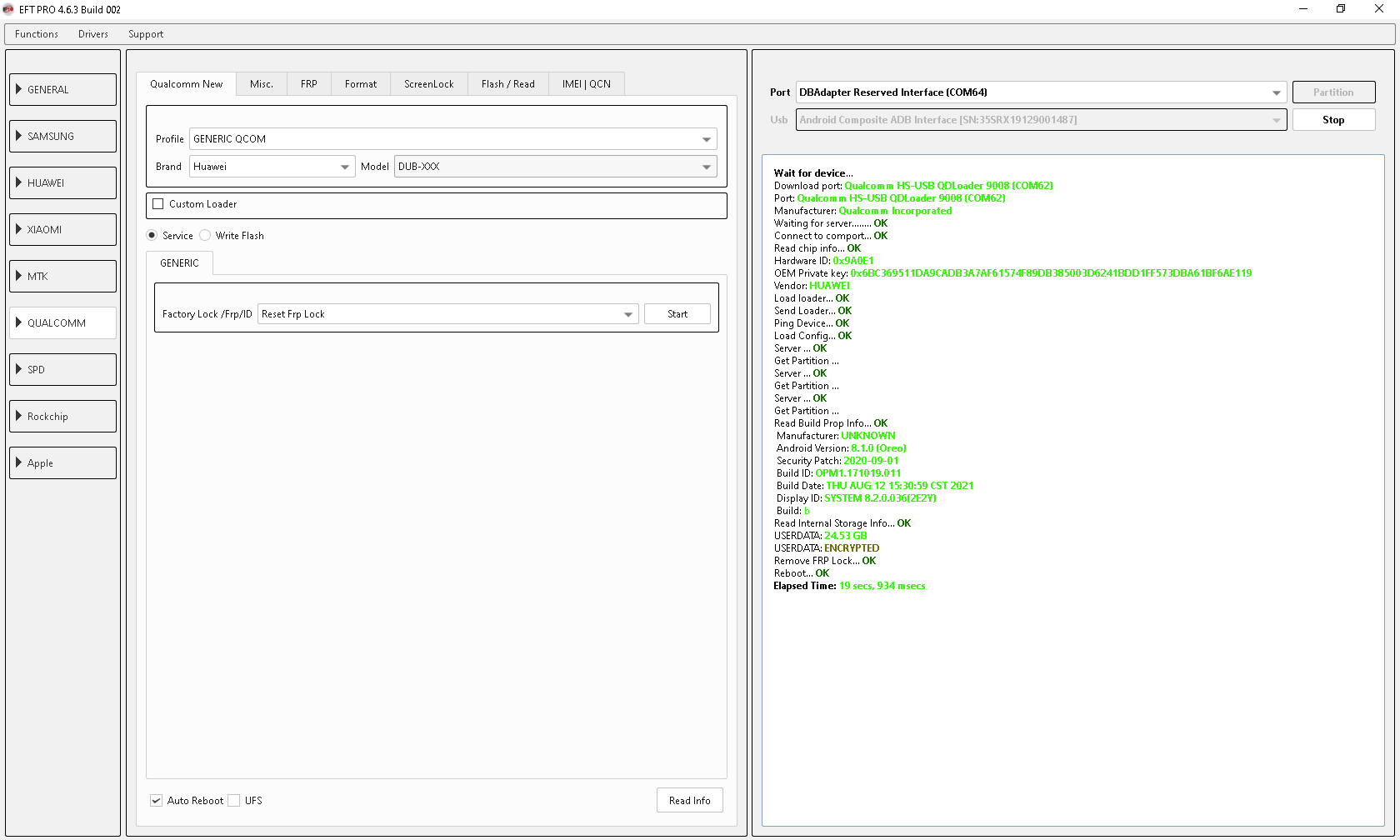
Direct Unlock Samsung SM-G925A ATT by SAMKEY Client Reader
Searching for SAMSUNG Mobile USB Modem...OK
SAMSUNG USB Modem detected on [COM14]
Looking for DEVICE......OK
Reading USB MODEM information...OK
MODEL : SM-G925A
VER : G925AUCS7ERC1/G925AATT7ERC1/G925AUCS7ERC1/G925AUCS7ERC1
IMEI : 357741062415946
S/N : R38G60NFFE
U/N : 06157DF64838623
Loading ADB module..............OK
Starting ADB module...OK
Searching for SAMSUNG ADB device...OK
Checking device authorization...OK
Reading device information via ADB...
ADB Serial Number : 06157df648386238
SIM State : ABSENT (OK)
Warranty VOID : 0
Debug Level : OK
CP Ver : G925AUCS7ERC1
AP Ver : G925AUCS7ERC1
Carrier ID :
Sales Code (Buyer) : ATT
Android Version : 7.0
Loading RIL applet...OK
Starting RIL applet...OK
Reading RADIO information...
IMEI : 357741062415946
Initializing RIL applet....OK
Reading HW signature...OK
Reading data...OK
Calculating security...[KEY:OK]...OK
Sending data to SERVER...OK
Waiting for SERVER response...OK
Sending Unlock Codes to phone...[ACK:1]...[ACK:2]...[ACK:3]...[ACK:4]...N/A
NOTA: Insertar chip no aceptado y agregar NETWORK CODE y aceptar
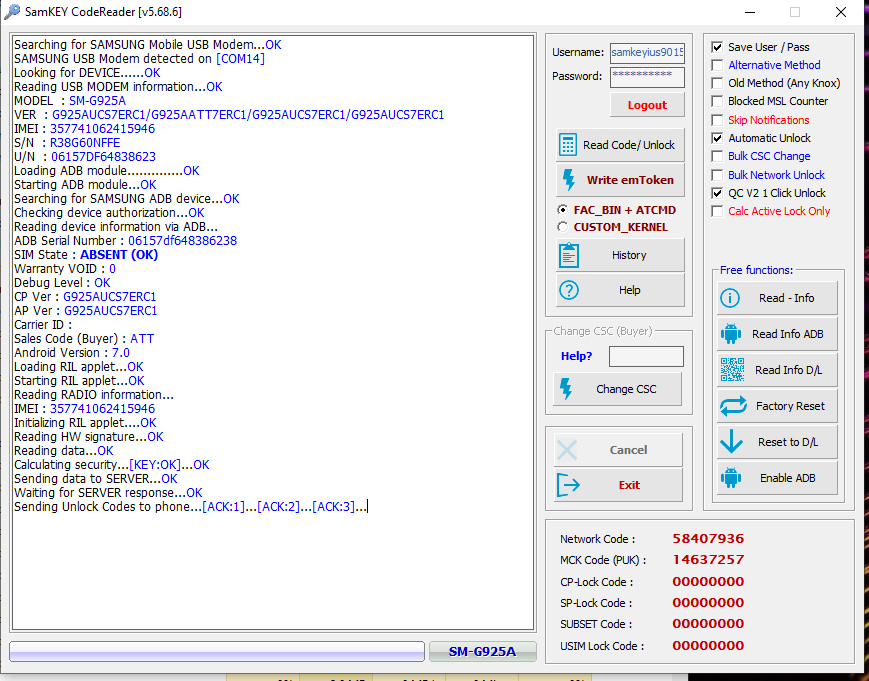
FRP and full Format Sky Unisoc SPRD
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM4]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&4
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Sync with node for I2C communication...
Handshake with BootROM... Done
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM7]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\skyn552202015113
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Connecting to MODEM...
● Reading Device Information...
Platform Version: MOCORTM_20A_W21.15.3_Debug
Project Version: sharklp
BASE Version: 4G_MODEM_20A_W21.15.3
HW Version: sc9832e_modem
04-14-2021 17: 43
BuildDesc: Elite_N55-user 11 R01005 1662364826 release-keys
Resetting to factory default settings... Done
●●● Log file saved to => C:/Users/Celulares Montreal/Downloads/AndroidUtilityPRO.v122.00.2022/Logs/2023_11_30_12_30_26.log
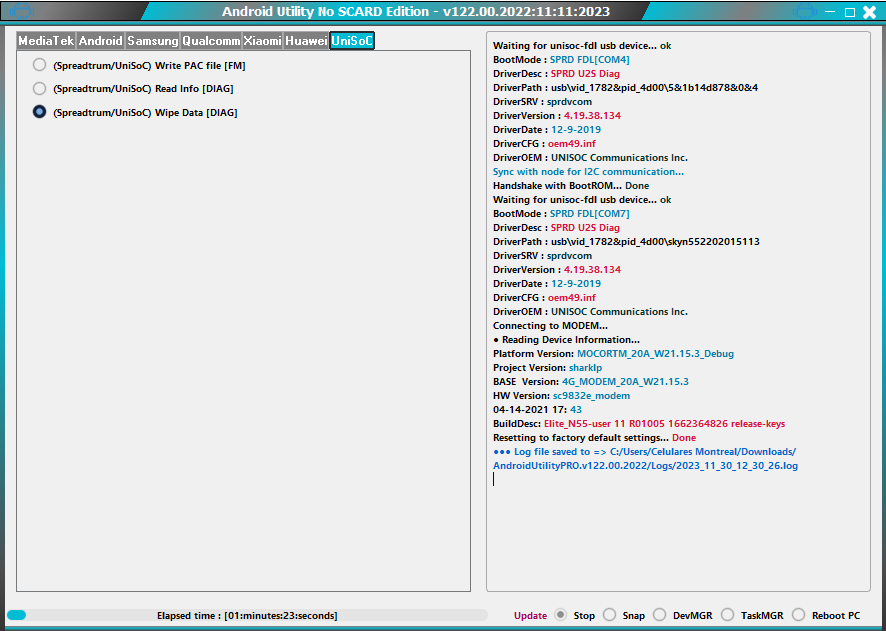
FRP Tablet PRITOM M10 sp7731e s8631e cuenta google
FRP Tablet PRITOM M10 sp7731e s8631e
Google Account Tablet PRITOM M10 sp7731e s8631e
Cuenta Google Tablet PRITOM M10 sp7731e s8631e
Volumen abajo + cable USB
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM68]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&3
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Sync with node for I2C communication...
Handshake with BootROM... Done
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM68]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&3
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Connecting to MODEM...
● Reading Device Information...
BuildDesc: sp7731e_1h30__s8631e_2g-user 9 PPR1.180610.011 13117 release-keys~
Rebooting device... Done
●●● Log file saved to => C:/Users/Downloads/AndroidUtilityPRO.v122.00.2022/Logs/2023_11_24_13_36_35.log
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM68]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&3
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Sync with node for I2C communication...
Handshake with BootROM... Done
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM68]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&3
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Connecting to MODEM...
● Reading Device Information...
BuildDesc: sp7731e_1h30__s8631e_2g-user 9 PPR1.180610.011 13117 release-keys~
Resetting to factory default settings... Done
●●● Log file saved to => C:/Users/Downloads/AndroidUtilityPRO.v122.00.2022/Logs/2023_11_24_13_39_18.log
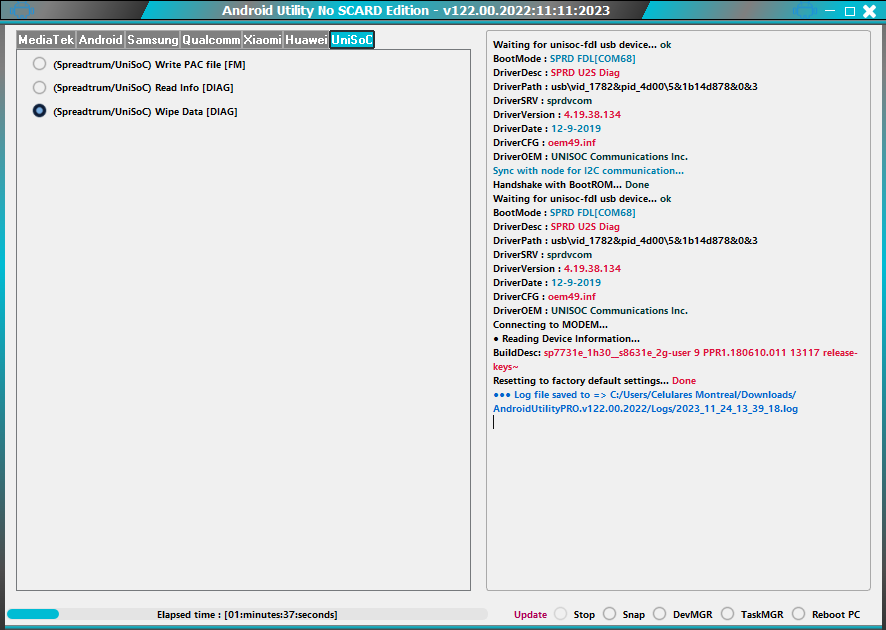
Bruteforce Nokia SL3 by Hash File
Nokia Bruteforce Service
FILE Cheap Nokia LBF SL3
Nokia Bruteforce Service
$ 173.34 MXN 12-24 Hours
FILE Nokia LBF SL3 (Instant)
Nokia Bruteforce Service
$ 202.88 MXN 1-12 Hours
FILE Nokia LBF SL3 #Server 2
Nokia Bruteforce Service
$ 173.34 MXN 12-24 Hours
Lista de Servicios 4
ANDROID MULTI TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Andriod multi tool credits
ANDROID MULTI TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.96 MXN Instant
FENRIS SAMSUNG FRP TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Fenris Sam Frp Tool [Exising Users]✅
FENRIS SAMSUNG FRP TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.28 MXN Instant
SIGMA PLUS [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Sigma Plus 1 Year Activation BOX /DONGLE
SIGMA PLUS [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1303.31 MXN Instant
SERVER Sigma Plus 6 Month Activation BOX /DONGLE
SIGMA PLUS [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 942.17 MXN Instant
HYDRA TOOL
SERVER Hydra Tool Digital License (12 Months)
HYDRA TOOL
$ 1456.59 MXN 1-6 Hours
SERVER Hydra Tool Digital License (3 Months)
HYDRA TOOL
$ 693.36 MXN 1-6 Hours
SERVER Hydra Tool Digital License (6 Months)
HYDRA TOOL
$ 1034.47 MXN 1-6 Hours
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Cheetah Tool PRO - 3 Month ACTIVATION ID - PASSWORD
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 673.3 MXN Instant
SERVER Cheetah Tool PRO - 6 Month ACTIVATION ID - PASSWORD
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 873.95 MXN Instant
UnLocker-Pro Tool Credits
SERVER UnLocker-Pro [ Coolpad,LG,Motorola,OnePlus,Samsung,ZTE ] Direct UnLock/Read Code/EmToken/FRP - Credits for Existing user [ Auto API ]
UnLocker-Pro Tool Credits
$ 23.96 MXN Instant
PHOENIX SERVICE TOOL [ NOKIA HMD TOOL ] CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Phoenix Service Tool [ Nokia HMD TOOL ] (FLASH - FRP - FACTORY RESET)
PHOENIX SERVICE TOOL [ NOKIA HMD TOOL ] CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 22.79 MXN Instant
PRAGMAFIX SCHEMATICS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER PragmaFix Hardware Tool 3 MONTHS
PRAGMAFIX SCHEMATICS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 193.03 MXN Instant
XIAMOIKEY.NET GENERATE - FRP KEY + EDL KEY BY TOKEN - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER XiaomiKEY - Generate EDL KEY by Token - [MEDL] |API
XIAMOIKEY.NET GENERATE - FRP KEY + EDL KEY BY TOKEN - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 151.98 MXN Instant
SERVER XiaomiKEY - Generate FRP KEY by Token - [MFRP] |API
XIAMOIKEY.NET GENERATE - FRP KEY + EDL KEY BY TOKEN - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 33.91 MXN Instant
SERVER XiaomiKEY - Generate FRP KEY by Token - [SFRP]
XIAMOIKEY.NET GENERATE - FRP KEY + EDL KEY BY TOKEN - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 33.91 MXN Instant
SERVER XiaomiKEY - Generate UBL KEY by Token - [RUBL]
XIAMOIKEY.NET GENERATE - FRP KEY + EDL KEY BY TOKEN - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 673.3 MXN Instant
SERVER XiaomiKEY - Telegrambot Credit Transfer
XIAMOIKEY.NET GENERATE - FRP KEY + EDL KEY BY TOKEN - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 22.2 MXN Instant
ALSEERY UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER AlseerY-UnLocker [ Samsung + LG + Alcatel + TINNO + Google + Moto ] unlock / repair / Frp / change css /bypass T-token - Credits for new user
ALSEERY UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 16.35 MXN Instant
ORION ESTECH SCHEMATIC - OFFICAL WORLDWIDE DISTRIBUTOR
SERVER Orion estechschematics Activation Code 1 (Month)
ORION ESTECH SCHEMATIC - OFFICAL WORLDWIDE DISTRIBUTOR
$ 132.56 MXN Instant
SERVER Orion estechschematics Activation Code 12 (Month) Double User
ORION ESTECH SCHEMATIC - OFFICAL WORLDWIDE DISTRIBUTOR
$ 673.3 MXN Instant
SERVER Orion estechschematics Activation Code 12 (Month) Single User
ORION ESTECH SCHEMATIC - OFFICAL WORLDWIDE DISTRIBUTOR
$ 480.54 MXN Instant
SERVER Orion estechschematics Activation Code 6 (Month)
ORION ESTECH SCHEMATIC - OFFICAL WORLDWIDE DISTRIBUTOR
$ 307 MXN Instant
GRIFFIN TOOL [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Griffin-Unlocker Activation - 6 Months
GRIFFIN TOOL [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 934.15 MXN Instant
SERVER Griffin-Unlocker Create New Account - 12 Months
GRIFFIN TOOL [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1190.91 MXN Instant
SERVER Griffin-Unlocker Create New Account - 3 Months
GRIFFIN TOOL [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 643.2 MXN Instant
RTC TOOL [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER RTC Tool - 12 Months Activation
RTC TOOL [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 850.48 MXN Instant
SERVER RTC Tool - 3 Months Activation
RTC TOOL [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 478.36 MXN Instant
SERVER RTC Tool - 6 Months Activation
RTC TOOL [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 574.58 MXN Instant
SERVER RTC Tool - Transfer Credits to Existing Account (Instant/Auto API)
RTC TOOL [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 20.06 MXN Instant
MEOW REALME LOGIN TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Meow RealMe Login Tool OTP (Realme Rcsm Flashing) (NO REFUND )
MEOW REALME LOGIN TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 18.3 MXN Instant
HUNTER UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER HUNTER UNLOCKER [ Samsung + LG + XIAOMI + Alcatel + TINNO + Google + Vivo + Realme + MOTO ] unlock / repair / Frp / change css /bypass T-token EXIST USER
HUNTER UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 16.93 MXN Instant
SERVER HUNTER UNLOCKER [ Samsung + LG + XIAOMI + Alcatel + TINNO + Google + Vivo + Realme + MOTO ] unlock / repair / Frp / change css /bypass T-token NEW USER
HUNTER UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 16.93 MXN Instant
MH Unlocker Pro TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER MH Unlocker Pro Tool Credits [Get Unlock Code By imei Instant]MH Unlocker Pro Tool Credits [Get Unlock Code By imei Instant]
MH Unlocker Pro TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 20.25 MXN Instant
BEST UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Best Unlocker [ Samsung + LG + XIAOMI + Alcatel + TINNO + Google + Vivo + Realme + MOTO ] unlock / repair / Frp / change css /bypass T-token Credits
BEST UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 18.3 MXN Instant
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER EFT pro tool activation -1 Month (No Need Dongle)
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 343.38 MXN Instant
SERVER EFT pro tool activation -3 Months (No Need Dongle)
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 725.47 MXN Instant
SERVER EFT pro tool activation -6 Months (No Need Dongle)
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1182.73 MXN Instant
TERA TOOL ACTIVATIONS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Tera Tool 1 Year Activation
TERA TOOL ACTIVATIONS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 753.56 MXN Instant
SERVER Tera Tool 3 Months Activation
TERA TOOL ACTIVATIONS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 331.45 MXN Instant
SERVER Tera Tool 6 Months Activation
TERA TOOL ACTIVATIONS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 512.78 MXN Instant
Xiaomi OTP TooL
SERVER Xiaomi OTP TooL ( NO REFUND )
Xiaomi OTP TooL
$ 132.56 MXN Instant
XinZhiZao schematic program
SERVER RENEW- XinZhiZao [ Mobile Phone/Computer Maintenance Query System ] 1 account/1 year
XinZhiZao schematic program
$ 552.91 MXN Instant
SERVER XinZhiZao [ Mobile Phone/Computer Maintenance Query System ] Redeem Code 1 account/1 month
XinZhiZao schematic program
$ 163.49 MXN Instant
SERVER XinZhiZao [ Mobile Phone/Computer Maintenance Query System ] Redeem Code 1 account/1 year
XinZhiZao schematic program
$ 552.91 MXN Instant
SERVER XinZhiZao [ Mobile Phone/Computer Maintenance Query System ]Redeem Code 3 account/1 year
XinZhiZao schematic program
$ 1252.22 MXN Instant
GAPro Login Tool
SERVER GAPro Login Tool - Oneplus OTP For Flash
GAPro Login Tool
$ 151.98 MXN Instant
SERVER GAPro Login Tool: Realme RCSM OTP (Flash Auth)
GAPro Login Tool
$ 22.2 MXN Instant
JCID Intelligent Mobile Phone Repair Drawing
SERVER JCID Intelligent Maintenance Diagram-Season card( 3 months)one PC only
JCID Intelligent Mobile Phone Repair Drawing
$ 351.33 MXN Instant
SERVER JCID Intelligent Mobile Phone Repair Drawing 1 Year one PC only
JCID Intelligent Mobile Phone Repair Drawing
$ 853.89 MXN Instant
USA - Xiaomi Auth Server Tool
SERVER USA - Xiaomi Auth Server Tool New User Credits ( 1 Device Flashing 5 Credits ) ✖️ NOT SUPPORT FMI ON Device ✖️
USA - Xiaomi Auth Server Tool
$ 132.56 MXN Instant
Mifixpro Auth Tool
SERVER MIFIX PRO OTP Xiaomi Fix Pro Tool
Mifixpro Auth Tool
$ 132.56 MXN Instant
SERVER Xiaomi frp MI FIX TOOL
Mifixpro Auth Tool
$ 33.91 MXN Instant
Sprint Unlock Tool " s2sprint"
SERVER Sprint Unlock Tool Create New Account (Instant/Auto API)
Sprint Unlock Tool " s2sprint"
$ 23.96 MXN Instant
SERVER Sprint Unlock Tool Create New Account Transfer Credits to Existing Account (Instant/Auto API)
Sprint Unlock Tool " s2sprint"
$ 23.96 MXN Instant
XIIAMOI RECOVERY FORMAT TOOL RFT - GENERATE FRP KEY BY TOKEN
SERVER Tera Tool 1 Year Activation
XIIAMOI RECOVERY FORMAT TOOL RFT - GENERATE FRP KEY BY TOKEN
$ 773.63 MXN Instant
Android Root Tool [ART]
SERVER Android Root Tool [ART] 1 Year Activation 1 Pc
Android Root Tool [ART]
$ 713.43 MXN Instant
TFM Tool Pro
SERVER TFM Tool Pro Activation (2 Years)
TFM Tool Pro
$ 853.89 MXN Instant
Uni-Android-Tool (UAT)
SERVER Uni Android Tool (UAT PRO) 2 Year Activation -New
Uni-Android-Tool (UAT)
$ 1374.84 MXN Instant
SERVER Uni Android Tool (UAT PRO) 3 Months Activation -New
Uni-Android-Tool (UAT)
$ 331.45 MXN Instant
F-KEY TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER F-KEY TOOL MI FRP (1 CREDIT 1 PHONE ) EXISTING USER
F-KEY TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 13.42 MXN Instant
SHARK SAMSUNG FRP/CPID TOOL BULK PURCHASE CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Shark Tool 100 Credits For Existing User
SHARK SAMSUNG FRP/CPID TOOL BULK PURCHASE CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 2049.25 MXN Instant
SERVER Shark Tool 1000 Credits For Existing User
SHARK SAMSUNG FRP/CPID TOOL BULK PURCHASE CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19154.85 MXN Instant
SERVER Shark Tool 50 Credits For Existing User
SHARK SAMSUNG FRP/CPID TOOL BULK PURCHASE CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1054.54 MXN Instant
SERVER Shark Tool 500 Credits For Existing User
SHARK SAMSUNG FRP/CPID TOOL BULK PURCHASE CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 9958.29 MXN Instant
Lista de Servicios 3
laelo Samsung Unlock Tool
SERVER laelo Samsung Unlock Tool Exisitng User
laelo Samsung Unlock Tool
$ 11.28 MXN Instant
SERVER laelo Samsung Unlock Tool New user
laelo Samsung Unlock Tool
$ 11.28 MXN Instant
GCPro
SERVER GCPRO Credits Any Quantity Auto INSTANT API
GCPro
$ 27.08 MXN Instant
Gsm Server Team [Bootloader Activation Code,SmartClip Pack4, Pack5 Activation
SERVER Boot loader Activation Code
Gsm Server Team [Bootloader Activation Code,SmartClip Pack4, Pack5 Activation
$ 470.6 MXN 1-12 Hours
SERVER Smart-Clip2 Pack 6 Activation
Gsm Server Team [Bootloader Activation Code,SmartClip Pack4, Pack5 Activation
$ 1231.78 MXN Instant
SERVER Smart-Clip2 Pack 7 Activation
Gsm Server Team [Bootloader Activation Code,SmartClip Pack4, Pack5 Activation
$ 1252.22 MXN Instant
SERVER Smart-Clip2 Pack4 Activation
Gsm Server Team [Bootloader Activation Code,SmartClip Pack4, Pack5 Activation
$ 1272.65 MXN 1-12 Hours
SERVER Smart-Clip2 Pack5 Activation
Gsm Server Team [Bootloader Activation Code,SmartClip Pack4, Pack5 Activation
$ 1231.78 MXN 1-12 Hours
HUA DONGLE
SERVER HUA Dongle Reactivation
HUA DONGLE
$ 753.56 MXN 1-12 Hours
Easy-Box Credits Pack
SERVER Easy Box 1000 pack
Easy-Box Credits Pack
$ 1895.98 MXN Instant
SERVER Easy Box 200 Pack
Easy-Box Credits Pack
$ 763.59 MXN Instant
HalabTech Credits
SERVER HalabTech Credits Any Quantity (instant)
HalabTech Credits
$ 21.23 MXN Instant
FTP Dongle Activation
SERVER FTP Dongle Activation
FTP Dongle Activation
$ 450.72 MXN Instant
Magma for HXC Dongle
SERVER Magma for HXC Dongle
Magma for HXC Dongle
$ 2363.24 MXN 6-24 Hours
HCU Time license
SERVER HCU 2 Year Unlimited Activation
HCU Time license
$ 1374.84 MXN Instant
Miracle Samsung Unlock Credits
SERVER Miracle samsung unlock credits
Miracle Samsung Unlock Credits
$ 18.69 MXN Instant
DC-Unlocker and HCU credits
SERVER Credits for existing user/reseller
DC-Unlocker and HCU credits
$ 16.35 MXN Instant
SERVER Credits for new reseller
DC-Unlocker and HCU credits
$ 16.35 MXN Instant
SERVER Credits for new user
DC-Unlocker and HCU credits
$ 16.35 MXN Instant
SERVER Credits to dongle
DC-Unlocker and HCU credits
$ 16.35 MXN Instant
Miracle Activation's [1Year,FRP,Huawei]
SERVER Miracle 1Year Account Activation
Miracle Activation's [1Year,FRP,Huawei]
$ 914.08 MXN Instant
SERVER Miracle Credits for (Meizu Login)
Miracle Activation's [1Year,FRP,Huawei]
$ 24.15 MXN Instant
SERVER Miracle Digital Edition (Login Edition)
Miracle Activation's [1Year,FRP,Huawei]
$ 1640.52 MXN Instant
SERVER Miracle FRP Pack
Miracle Activation's [1Year,FRP,Huawei]
$ 713.43 MXN Instant
SERVER Miracle Huawei Pack
Miracle Activation's [1Year,FRP,Huawei]
$ 713.43 MXN Instant
SERVER Miracle Meizu Login Pack
Miracle Activation's [1Year,FRP,Huawei]
$ 450.72 MXN Instant
SERVER Miracle Schematics Pro (login Edition)
Miracle Activation's [1Year,FRP,Huawei]
$ 420.9 MXN Instant
SERVER Miracle Schematics Pro for Miracle Users
Miracle Activation's [1Year,FRP,Huawei]
$ 341.39 MXN Instant
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER EFT Dongle 1 Year Support Activation
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 525.82 MXN Instant
SERVER EFT Pro Tool Renew - 1 year (No Need Dongle)
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 821.78 MXN Instant
SERVER EFT Dongle 2 Year Support Activation
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 657.25 MXN Instant
SERVER EFT pro tool activation - 1 year (No Need Dongle)
EFT PRO TOOL/DONGLE [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1686.5 MXN Instant
Inferno Tool Activation 1 Year
SERVER Inferno Tool Activation [1 Year] Volcano Box only
Inferno Tool Activation 1 Year
$ 793.69 MXN 1-12 Hours
SERVER Inferno Tool Activation [1 Year] For inferno Key
Inferno Tool Activation 1 Year
$ 773.63 MXN Instant
GB-Key Activation 1 Year License, Huawei Module
SERVER GB-Key Activation 1 Year License
GB-Key Activation 1 Year License, Huawei Module
$ 1252.22 MXN 1-12 Hours
SERVER GB-Key Huawei Module
GB-Key Activation 1 Year License, Huawei Module
$ 1252.22 MXN 1-12 Hours
CS-TOOL
SERVER S-Module Activation for CS-Tool
CS-TOOL
$ 512.78 MXN 1-2 Hours
Uni-Android-Tool (UAT)
SERVER Uni Android Tool (UAT PRO) 12 Months Activation-New
Uni-Android-Tool (UAT)
$ 914.08 MXN Instant
DC Unlocker Support Extension
SERVER Support for 1 year
DC Unlocker Support Extension
$ 291.69 MXN Instant
SERVER Support for 2 years
DC Unlocker Support Extension
$ 381.15 MXN Instant
DC-Unlocker - Additional Feature Activation
SERVER DC Phoenix activation
DC-Unlocker - Additional Feature Activation
$ 1014.41 MXN Instant
SERVER HCU activation for dongle
DC-Unlocker - Additional Feature Activation
$ 2628.91 MXN Instant
SERVER HCU for dongle who has valid support
DC-Unlocker - Additional Feature Activation
$ 1783.57 MXN Instant
SERVER HCU for dongle who have Phoenix and support
DC-Unlocker - Additional Feature Activation
$ 1014.41 MXN Instant
SERVER Unlimited FRP Unlock
DC-Unlocker - Additional Feature Activation
$ 1014.41 MXN Instant
SERVER Unlimited ZTE Icera firmware writer
DC-Unlocker - Additional Feature Activation
$ 512.78 MXN Instant
SERVER ZTE Icera UNLIMITED direct unlock
DC-Unlocker - Additional Feature Activation
$ 512.78 MXN Instant
SERVER ZTE Qualcomm and Huawei Hisilicon modems Flasher
DC-Unlocker - Additional Feature Activation
$ 512.78 MXN Instant
PUBG Mobile UC GLOBAL(PIN)
SERVER PUBG Mobile 1,500 + 300 UC Code Minimum Quantity 10 (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 552.91 MXN Instant
SERVER PUBG Mobile 3,000 + 850 UC Code (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 1014.41 MXN Instant
SERVER PUBG Mobile 3,000 + 850 UC Code Minimum Quantity 10 (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 974.28 MXN Instant
SERVER PUBG Mobile 300 + 25 UC Code (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 161.68 MXN Instant
SERVER PUBG Mobile 300 + 25 UC CodeMinimum Quantity 50 (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 166.54 MXN Instant
SERVER PUBG Mobile 6,000 + 2,100 UC Code (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 1947.07 MXN Instant
SERVER PUBG Mobile 6,000 + 2,100 UC Code Minimum quantity 5 (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 1906.2 MXN Instant
SERVER PUBG Mobile 60 UC Code (Global) ✅
PUBG Mobile UC GLOBAL(PIN)
$ 23.96 MXN Instant
SERVER PUBG Mobile 60 UC Code Minimum Quantity 100 (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 23.96 MXN Instant
SERVER PUBG Mobile 600 + 60 UC Code (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 242.27 MXN 5-60 Miniutes
SERVER PUBG Mobile 600 + 60 UC Code Minimum quantity 30 (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 237.35 MXN Instant
SERVER PUBG Mobile 1,500 + 300 UC Code (Global)
PUBG Mobile UC GLOBAL(PIN)
$ 572.97 MXN Instant
Pubg Game Credits DIRECT TOP UP [ UC ]
SERVER PUBG Mobile 1800 UC [ DIRECT TOP-UP ] ✅
Pubg Game Credits DIRECT TOP UP [ UC ]
$ 592.84 MXN Instant
SERVER Pubg Mobile 325 UC [ DIRECT TOP-UP ] ✅
Pubg Game Credits DIRECT TOP UP [ UC ]
$ 166.54 MXN 5-60 Miniutes
SERVER PUBG Mobile 3850 UC [ DIRECT TOP-UP ]
Pubg Game Credits DIRECT TOP UP [ UC ]
$ 1014.41 MXN Instant
SERVER PUBG Mobile 60 UC (Global) [ DIRECT TOP-UP ] ✅
Pubg Game Credits DIRECT TOP UP [ UC ]
$ 23.96 MXN 5-60 Miniutes
SERVER PUBG Mobile 660 UC (Global) [ DIRECT TOP-UP ] ✅
Pubg Game Credits DIRECT TOP UP [ UC ]
$ 242.07 MXN 5-60 Miniutes
SERVER PUBG Mobile 8100 UC [ DIRECT TOP-UP ]
Pubg Game Credits DIRECT TOP UP [ UC ]
$ 1926.63 MXN Instant
SERVER PUBG Mobile 8425 UC [ DIRECT TOP-UP ]
Pubg Game Credits DIRECT TOP UP [ UC ]
$ 2028.82 MXN Instant
PUBG Game Credits
SERVER PUBG Mobile 4000 UC [ DIRECT TOP-UP ]
PUBG Game Credits
$ 1170.47 MXN Instant
SERVER PUBG Mobile 63UC [ DIRECT TOP-UP ]
PUBG Game Credits
$ 23.96 MXN 5-60 Miniutes
SERVER PUBG Mobile 690 UC [ DIRECT TOP-UP ]
PUBG Game Credits
$ 257.04 MXN 5-60 Miniutes
PUBG: NEW STATE (NC)
SERVER PUBG: NEW STATE (NC) 15,000NC + 1,800 Bonus TOPUP
PUBG: NEW STATE (NC)
$ 1170.47 MXN Instant
SERVER PUBG: NEW STATE (NC) 1500NC + 80 Bonus TOPUP
PUBG: NEW STATE (NC)
$ 163.49 MXN Instant
SERVER PUBG: NEW STATE (NC) 30,000NC + 5,000 Bonus TOPUP
PUBG: NEW STATE (NC)
$ 2151.44 MXN Instant
SERVER PUBG: NEW STATE (NC) 300NC TOPUP
PUBG: NEW STATE (NC)
$ 23.96 MXN Instant
SERVER PUBG: NEW STATE (NC) 3600NC + 250 Bonus TOPUP
PUBG: NEW STATE (NC)
$ 331.45 MXN Instant
SERVER PUBG: NEW STATE (NC) 9300NC + 930 Bonus TOPUP
PUBG: NEW STATE (NC)
$ 733.49 MXN Instant
PUBG Purchase [ UC ] Top UP
SERVER PUBG Mobile 1500+375 UC [ PUBG Mobile Purchase ]
PUBG Purchase [ UC ] Top UP
$ 613.1 MXN Instant
SERVER PUBG Mobile 180+18 UC [ PUBG Mobile Purchase ]
PUBG Purchase [ UC ] Top UP
$ 132.56 MXN Instant
SERVER PUBG Mobile 30 +2 UC [ PUBG Mobile Purchase ]
PUBG Purchase [ UC ] Top UP
$ 16.35 MXN Instant
SERVER PUBG Mobile 3000+1000 UC [ PUBG Mobile Purchase ]
PUBG Purchase [ UC ] Top UP
$ 1170.47 MXN Instant
SERVER PUBG Mobile 60+3 UC [ PUBG Mobile Purchase ]
PUBG Purchase [ UC ] Top UP
$ 23.96 MXN Instant
SERVER PUBG Mobile 600+90 UC [ PUBG Mobile Purchase ]
PUBG Purchase [ UC ] Top UP
$ 261.77 MXN Instant
SERVER PUBG Mobile 6000 +2425 UC [ PUBG Mobile Purchase ]
PUBG Purchase [ UC ] Top UP
$ 2090.13 MXN Instant
PUBG New State PIN
SERVER PUBG New State 3600 NC+250 Bonus PIN
PUBG New State PIN
$ 331.45 MXN Instant
SERVER PUBG New State 9300 NC+930 Bonus PIN
PUBG New State PIN
$ 713.43 MXN Instant
Direct FRP
SERVER AlseerY-UnLocker [ Samsung + LG + Alcatel + TINNO + Google + Moto ] unlock / repair / Frp / change css /bypass T-token - Credits for new user
Direct FRP
$ 18.3 MXN Instant
SERVER Direct FRP Credits to Existing User - DirectFRP.com
Direct FRP
$ 23.96 MXN Instant
ALSEERY UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER AlseerY-UnLocker [ Samsung + LG + Alcatel + TINNO + Google + Moto] unlock / repair / frp - Credits for Existing user
ALSEERY UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 16.35 MXN Instant
SHARK SAMSUNG FRP/CPID TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Shark Tool Account existing FRP 24/7 Tool All Samsung Supported
SHARK SAMSUNG FRP/CPID TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.18 MXN Instant
SERVER Shark Tool New Account FRP 24/7 Tool All Samsung Supported
SHARK SAMSUNG FRP/CPID TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.18 MXN Instant
CF-Tools
SERVER CF-Tool 1 Month Renew
CF-Tools
$ 183.19 MXN Instant
SERVER CF-Tools 1 Month Activation
CF-Tools
$ 183.19 MXN Instant
SERVER CF-Tools 12 Month Activation
CF-Tools
$ 572.97 MXN Instant
SERVER CF-Tools 12 Month Renew
CF-Tools
$ 593.04 MXN Instant
SERVER CF-Tools 3 Credit (For Auth Xiaomi)
CF-Tools
$ 132.56 MXN Instant
SERVER CF-Tools 3 Month Activation
CF-Tools
$ 291.69 MXN Instant
SERVER CF-Tools 3 Month Renew
CF-Tools
$ 291.69 MXN Instant
SERVER CF-Tools 6 Credit (For Auth Xiaomi)
CF-Tools
$ 183.19 MXN Instant
SERVER CF-Tools 6 Month Activation
CF-Tools
$ 410.97 MXN Instant
SERVER CF-Tools 6 Month Renew
CF-Tools
$ 410.97 MXN Instant
Lista de Servicios 2
KingUnlock.net- Samsung (Cheapest Direct Remote Unlock) Activation/Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Kingunlock.net Credits for existing User
KingUnlock.net- Samsung (Cheapest Direct Remote Unlock) Activation/Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 12.06 MXN Instant
ESTECH SCHEMATIC 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Estech Schematic Active 1pc/year
ESTECH SCHEMATIC 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 351.33 MXN Instant
SERVER Estech Schematics Activation Code (1 Month) - Instant
ESTECH SCHEMATIC 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 132.56 MXN Instant
Z3X BOX Server Credits Powered by Z3X [30,50 Credits Packs] 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Z3x Unlock Credits Pack 30 Pack
Z3X BOX Server Credits Powered by Z3X [30,50 Credits Packs] 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 753.56 MXN Instant
SERVER Z3x Unlock Credits Pack 50 Pack
Z3X BOX Server Credits Powered by Z3X [30,50 Credits Packs] 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1231.78 MXN Instant
SERVER Z3x Samsung Refil Credits
Z3X BOX Server Credits Powered by Z3X [30,50 Credits Packs] 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 25.09 MXN Instant
E-GSM TOOL CREDITS/ACTIVAION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER E-GSM Tool Activation NEW - RENEW [Instant]
E-GSM TOOL CREDITS/ACTIVAION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1272.65 MXN Instant
SERVER E-GSM Tool Credits [instant]
E-GSM TOOL CREDITS/ACTIVAION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 24.15 MXN Instant
Avatar Autho Tool
SERVER Avatar Auth Tool -AAT Credit Any Qnt (AUTH, FRP, FASTBOOT TO EDL)
Avatar Autho Tool
$ 17.32 MXN Instant
SERVER E-GSM Tool Credits [instant]
Avatar Autho Tool
$ 23.96 MXN Instant
DZKJ
SERVER DZKJ PhoneRepair Tools activation CODE 1-year license accounts
DZKJ
$ 853.89 MXN Instant
SERVER DZKJ PhoneRepair Tools activation CODE 3 MONTH license accounts
DZKJ
$ 222.58 MXN Instant
SERVER DZKJ PhoneRepair Tools Activation CODE 3-Year 3 pc License Accounts
DZKJ
$ 1517.9 MXN Instant
TR TOOL
SERVER TR Tools Pro 1 Year [Existing User] service
TR TOOL
$ 1211.34 MXN Instant
SERVER TR Tools Pro 1 Year [New User] NEW
TR TOOL
$ 1211.34 MXN Instant
Avengers Box
SERVER Avengers Box /Dongle 1 Year Activation [instant]
Avengers Box
$ 532.84 MXN Instant
TFM Tool Pro
SERVER TFM Pro tool Credit
TFM Tool Pro
$ 20.25 MXN Instant
SERVER TFM PRO [3 Month Package]
TFM Tool Pro
$ 430.84 MXN 5-60 Miniutes
SERVER TFM Tool Pro Activation (1 Year)
TFM Tool Pro
$ 593.04 MXN Instant
OCTOPLUS SERVER CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Create New octopus user
OCTOPLUS SERVER CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 6.79 MXN Instant
SERVER Octoplus Box Credits For Existing Users (Instant)
OCTOPLUS SERVER CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 6.79 MXN Instant
Panda Tools
SERVER Panda Tools Unlock SAM - LG - Moto [ Cheapest and fastest Tool ] Create New Account
Panda Tools
$ 23.18 MXN Instant
SERVER Panda Tools Unlock SAM - LG - Moto [ Cheapest And Fastest Tool ] Existing Account
Panda Tools
$ 23.18 MXN Instant
PRAGMAFIX SCHEMATICS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER PragmaFix Hardware Tool 12 Month
PRAGMAFIX SCHEMATICS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 420.9 MXN Instant
SERVER PragmaFix Hardware Tool 6 MONTHS
PRAGMAFIX SCHEMATICS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 301.63 MXN Instant
App Store & iTunes [ USA ]
SERVER App Store & iTunes Gift Card $2 USA
App Store & iTunes [ USA ]
$ 113.15 MXN Instant
SERVER App Store & iTunes Gift Card $20 USA
App Store & iTunes [ USA ]
$ 512.78 MXN Instant
SERVER App Store & iTunes Gift Card $25 USA
App Store & iTunes [ USA ]
$ 613.1 MXN Instant
SERVER App Store & iTunes Gift Card $4 USA
App Store & iTunes [ USA ]
$ 151.98 MXN Instant
SERVER App Store & iTunes Gift Card $60 USA
App Store & iTunes [ USA ]
$ 1374.84 MXN Instant
SERVER App Store & iTunes Gift Card $70 USA
App Store & iTunes [ USA ]
$ 1579.21 MXN Instant
SERVER App Store & iTunes Gift Card $15 USA
App Store & iTunes [ USA ]
$ 391.09 MXN Instant
SERVER App Store & iTunes Gift Card 5$ USA
App Store & iTunes [ USA ]
$ 163.49 MXN Instant
SERVER App Store & iTunes Gift Card 10$ USA
App Store & iTunes [ USA ]
$ 291.69 MXN Instant
SERVER App Store & iTunes Gift Card $30 USA
App Store & iTunes [ USA ]
$ 713.43 MXN Instant
SERVER App Store & iTunes Gift Card $40 USA
App Store & iTunes [ USA ]
$ 914.08 MXN Instant
SERVER App Store & iTunes Gift Card 50$ USA
App Store & iTunes [ USA ]
$ 1170.47 MXN Instant
SERVER App Store & iTunes Gift Card 100$ USA
App Store & iTunes [ USA ]
$ 2322.36 MXN Instant
PlayStation Network US
SERVER PlayStation Network(Store) US-USD 10 (US)
PlayStation Network US
$ 291.69 MXN Instant
SERVER PlayStation Network(Store) US-USD 25 (US)
PlayStation Network US
$ 613.1 MXN Instant
SERVER PlayStation Network(Store) US-USD 50 (US)
PlayStation Network US
$ 1170.47 MXN Instant
SERVER PlayStation Network(Store) US-USD 60 (US)
PlayStation Network US
$ 1374.84 MXN Instant
SERVER PlayStation Network(Store) US-USD 75 (US)
PlayStation Network US
$ 1681.39 MXN Instant
SERVER PlayStation Network(Store) US-USD 100 (US)
PlayStation Network US
$ 2526.73 MXN Instant
MAGICTOOL CREDITS - [ Repair IMEI, Factory Enable, MDM ,FRP , UNLOCK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER The Magic tool Motorola [ Repair IMEI, Factory Enable, MDM ,FRP , UNLOCK] - Create Account- NEW
MAGICTOOL CREDITS - [ Repair IMEI, Factory Enable, MDM ,FRP , UNLOCK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.18 MXN Instant
SERVER The Magic tool Motorola [ Repair IMEI, Factory Enable, MDM ,FRP , UNLOCK] - themagictool EXIST Account
MAGICTOOL CREDITS - [ Repair IMEI, Factory Enable, MDM ,FRP , UNLOCK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.18 MXN Instant
Sony Xperia Android (NetworkUnlock,Unlock Google FRP,255 Counter Reset) Credits 24.7 Real Time Instant - Official Worldwide Distributor
SERVER Sony Xperia (Network Unlock,0/255 Counter Reset)
Sony Xperia Android (NetworkUnlock,Unlock Google FRP,255 Counter Reset) Credits 24.7 Real Time Instant - Official Worldwide Distributor
$ 465.63 MXN Instant
SAMHub.net- Samsung (Unlockcode,UnlockAPP,Unlock Goolge FRP,RepairIMEI) Credits 24.7 Real Time Instant - Official Worldwide Distributor
SERVER SAMHub - Create New User + Credits (Instant/Auto API)
SAMHub.net- Samsung (Unlockcode,UnlockAPP,Unlock Goolge FRP,RepairIMEI) Credits 24.7 Real Time Instant - Official Worldwide Distributor
$ 22.2 MXN Instant
SERVER SAMHub - Transfer Credits to Existing Account (Instant/Auto API)
SAMHub.net- Samsung (Unlockcode,UnlockAPP,Unlock Goolge FRP,RepairIMEI) Credits 24.7 Real Time Instant - Official Worldwide Distributor
$ 22.2 MXN Instant
CHIMERA TOOL [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER ChimeraTool PRO
CHIMERA TOOL [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 2690.22 MXN Instant
SERVER ChimeraTool Samsung
CHIMERA TOOL [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1553.66 MXN Instant
SAM-FRP Tool https://www.sam-frp.com (Samsung One Click FRP Unlock) 24.7 Real Time Instant - Official Worldwide Reseller
SERVER SAM-FRP Tool Credit Exist User- No Support - No refund
SAM-FRP Tool https://www.sam-frp.com (Samsung One Click FRP Unlock) 24.7 Real Time Instant - Official Worldwide Reseller
$ 23.96 MXN Instant
DFT PRO TOOL - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER DFT PRO TOOL ACTIVATION [New Users] 1 Year
DFT PRO TOOL - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1231.78 MXN Instant
SERVER DFT PRO TOOL ACTIVATION [Old Users] 1 Year
DFT PRO TOOL - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1231.78 MXN Instant
Sim Killer Pro Tool
SERVER Sim Killer Pro Tool Credit Any Qty 24.7 Real Time Instant
Sim Killer Pro Tool
$ 17.32 MXN Instant
Magma-Tool.com - Samsung (One Click,Unlock Goolge FRP,RepairIMEI) Credits 24.7 Real Time Instant - Official Worldwide Distributor
SERVER Magma FRP Credits For All Samsung Devices - Support All Security All countries
Magma-Tool.com - Samsung (One Click,Unlock Goolge FRP,RepairIMEI) Credits 24.7 Real Time Instant - Official Worldwide Distributor
$ 22.79 MXN Instant
SERVER Magma FRP Credits For All Samsung Devices - Support All Security All countries [ Each Phone need 7 credits ]
Magma-Tool.com - Samsung (One Click,Unlock Goolge FRP,RepairIMEI) Credits 24.7 Real Time Instant - Official Worldwide Distributor
$ 23.18 MXN Instant
GsmUnlock.org - Samsung Phone (UnlockPhone Direct via USB or USB OverNetwork) Credits 24.7 Real Time Instant - Official Worldwide Reseller
SERVER GSMUnlock- Create New Account (Instant/Auto API)
GsmUnlock.org - Samsung Phone (UnlockPhone Direct via USB or USB OverNetwork) Credits 24.7 Real Time Instant - Official Worldwide Reseller
$ 22.2 MXN Instant
SERVER GSMUnlock- Transfer Credits to Existing Account (Instant/Auto API)
GsmUnlock.org - Samsung Phone (UnlockPhone Direct via USB or USB OverNetwork) Credits 24.7 Real Time Instant - Official Worldwide Reseller
$ 22.2 MXN Instant
Sigma Key Pack Activations Powered by Gsmserver 24.7 Real Time Instant - Official Worldwide Distributor
SERVER Sigma Pack 1 Activation
Sigma Key Pack Activations Powered by Gsmserver 24.7 Real Time Instant - Official Worldwide Distributor
$ 1293.09 MXN Instant
SERVER Sigma Pack 2 Activation
Sigma Key Pack Activations Powered by Gsmserver 24.7 Real Time Instant - Official Worldwide Distributor
$ 1293.09 MXN Instant
SERVER Sigma Pack 3 Activation
Sigma Key Pack Activations Powered by Gsmserver 24.7 Real Time Instant - Official Worldwide Distributor
$ 1293.09 MXN Instant
SERVER Sigma Pack 4 Activation
Sigma Key Pack Activations Powered by Gsmserver 24.7 Real Time Instant - Official Worldwide Distributor
$ 1701.83 MXN Instant
SERVER Sigma Pack 5 Activation
Sigma Key Pack Activations Powered by Gsmserver 24.7 Real Time Instant - Official Worldwide Distributor
$ 1293.09 MXN Instant
SERVER Sigma Pack 1 + Pack 2 + Pack 3 + Pack 4 Activation
Sigma Key Pack Activations Powered by Gsmserver 24.7 Real Time Instant - Official Worldwide Distributor
$ 5237.39 MXN Instant
SERVER SigmaKey PowerPack for SigmaKey Huawei Edition Owners
Sigma Key Pack Activations Powered by Gsmserver 24.7 Real Time Instant - Official Worldwide Distributor
$ 2424.55 MXN Instant
Z3X Box Activation Powered by Z3X [Samsung,LG] Activations 24.7 Real Time Instant - Official Worldwide Reseller
SERVER Z3x Sam Tool Activation
Z3X Box Activation Powered by Z3X [Samsung,LG] Activations 24.7 Real Time Instant - Official Worldwide Reseller
$ 1293.09 MXN Instant
SERVER Z3X Box Samsung PRO Activation
Z3X Box Activation Powered by Z3X [Samsung,LG] Activations 24.7 Real Time Instant - Official Worldwide Reseller
$ 1272.65 MXN Instant
SERVER Z3x LG Tool Activation
Z3X Box Activation Powered by Z3X [Samsung,LG] Activations 24.7 Real Time Instant - Official Worldwide Reseller
$ 1272.65 MXN Instant
Infinity-box.com (Proffesional Service Software) [Support Renew,Activations,Credits] 24.7 Real Time Instant - Official Worldwide Reseller
SERVER Infiinity Server 100 credits Instant
Infinity-box.com (Proffesional Service Software) [Support Renew,Activations,Credits] 24.7 Real Time Instant - Official Worldwide Reseller
$ 693.36 MXN Instant
SERVER Infinity Server 10 Credits Instant
Infinity-box.com (Proffesional Service Software) [Support Renew,Activations,Credits] 24.7 Real Time Instant - Official Worldwide Reseller
$ 130.62 MXN Instant
SERVER Infinity-Box/Dongle 1 year Updates/Support Renew, Chinese Miracle-2 included
Infinity-box.com (Proffesional Service Software) [Support Renew,Activations,Credits] 24.7 Real Time Instant - Official Worldwide Reseller
$ 833.82 MXN Instant
SERVER Infinity-Box/Dongle 2 years Updates/Support Renew, Chinese Miracle-2 included
Infinity-box.com (Proffesional Service Software) [Support Renew,Activations,Credits] 24.7 Real Time Instant - Official Worldwide Reseller
$ 1170.47 MXN Instant
SERVER Infinity BB5 Easy Service Tool [BEST] software activation for Infinity-Box/Dongle
Infinity-box.com (Proffesional Service Software) [Support Renew,Activations,Credits] 24.7 Real Time Instant - Official Worldwide Reseller
$ 934.15 MXN 1-12 Hours
SERVER Infinity Samsung `SM` software activation for Infinity-Box/Dongle
Infinity-box.com (Proffesional Service Software) [Support Renew,Activations,Credits] 24.7 Real Time Instant - Official Worldwide Reseller
$ 570.97 MXN 1-12 Hours
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
SERVER Octoplus FRP 1 Year Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1436.15 MXN Instant
SERVER Octoplus FRP 6 Month Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1074.6 MXN Instant
SERVER Octoplus FRP Tool Activation
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 974.28 MXN Instant
SERVER Octoplus Full 1 Year Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 2833.28 MXN Instant
SERVER Octoplus Full 6 Month Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1947.07 MXN Instant
SERVER Octoplus Huawei 1 Year Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1456.59 MXN Instant
SERVER Octoplus Huawei 6 Month Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1074.6 MXN Instant
SERVER Octoplus Huawei Tool Activation
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1660.95 MXN 1-12 Hours
SERVER Octoplus LG 1 Year Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1456.59 MXN Instant
SERVER Octoplus LG 6 Month Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1074.6 MXN Instant
SERVER Octoplus Samsung 1 Year Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1456.59 MXN Instant
SERVER Octoplus Samsung 6 Month Digital License
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1074.6 MXN Instant
SERVER Octoplus Samsung Activation for Medusa PRO / Medusa Box
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1395.28 MXN Instant
SERVER Octopus/Medusa Box LG Activation
Gsm Server Team [Octopus Samsung,LG,Frp Tool,Huawei Tool] [24/7 Real Time Instant]
$ 1436.15 MXN Instant
DTPRO powerfull MultiBran Tool - (IMEIrepair.Frp,Unlock,Service,Auth -Unique) Tool Activation - Official Worldwide Distributor
SERVER DT PRO TOOL ACTIVATION-INSTANT CODE
DTPRO powerfull MultiBran Tool - (IMEIrepair.Frp,Unlock,Service,Auth -Unique) Tool Activation - Official Worldwide Distributor
$ 613.1 MXN Instant
FuriousGold.com powerfull MultiBran Tool (Credits,Activation PACKS) 24.7 Real Time Instant - Official Worldwide Reseller
SERVER Furious Gold Credits
FuriousGold.com powerfull MultiBran Tool (Credits,Activation PACKS) 24.7 Real Time Instant - Official Worldwide Reseller
$ 22.2 MXN Instant
EME Mobile Tool - powerfull MultiBran Tool Vivo,Oppo (Factory Reset,ResetFRP....) Activation/Credits 24.7 Real Time Instant - Official Worldwide Reseller
SERVER EME Mobile Tool (EMT) - Credits
EME Mobile Tool - powerfull MultiBran Tool Vivo,Oppo (Factory Reset,ResetFRP....) Activation/Credits 24.7 Real Time Instant - Official Worldwide Reseller
$ 30 MXN Instant
SERVER EME Mobile Tool (EMT) Standard Edition License
EME Mobile Tool - powerfull MultiBran Tool Vivo,Oppo (Factory Reset,ResetFRP....) Activation/Credits 24.7 Real Time Instant - Official Worldwide Reseller
$ 1252.22 MXN Instant
WUXINJI [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER WUXINJI 1Year 3 PC Activation
WUXINJI [ ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 994.34 MXN Instant
ZXW Activation
SERVER ZXW Online Account Activation (1 Year)
ZXW Activation
$ 1014.41 MXN Instant
NCK Box / Dongle Credits
SERVER NCK Online Logger Box Credits
NCK Box / Dongle Credits
$ 26.1 MXN 1-6 Hours
SERVER NCK Online Logger Dongle Credits
NCK Box / Dongle Credits
$ 26.1 MXN 1-6 Hours
Realme Auth - Flash
SERVER Realme Auth Flash Tool Any Quantity
Realme Auth - Flash
$ 132.56 MXN Instant
TMBkiller
SERVER TMBkiller - UNLOCK [ LG and Samsung ] INSTANT- New Account - Any credit Quantity
TMBkiller
$ 18.3 MXN Instant
SERVER TMBkiller - UNLOCK [ LG and Samsung ] INSTANT- Refill Existing Account
TMBkiller
$ 18.3 MXN Instant
Lista de Servicios
PUBG New State PIN
SERVER PUBG New State 1500 NC+80 Bonus PIN
PUBG New State PIN
$ 168.42 MXN Instant
SERVER PUBG New State 15000 NC+1800 Bonus PIN
PUBG New State PIN
$ 1094.67 MXN Instant
SERVER PUBG New State 300 NC PIN
PUBG New State PIN
$ 23.96 MXN Instant
SERVER PUBG New State 30000 NC+5000 Bonus PIN
PUBG New State PIN
$ 2110.56 MXN Instant
KEY-TOOL TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER KEY-Tool [ Samsung ] Direct UnLock / Change CSC - Credits for Existing user
KEY-TOOL TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 17.91 MXN Instant
FAST UNLOCKER PRO TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Fast Unlocker Pro [ Samsung + LG + Alcatel + TINNO ...etc ] unlock / repair / Frp / change css /bypass T-token - Credits for new user [ Auto API ]
FAST UNLOCKER PRO TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 16.93 MXN Instant
SERVER Fast Unlocker Pro [ Samsung + LG + Alcatel + TINNO ...etc] unlock / repair / frp - Credits for Existing user [ Auto API ]
FAST UNLOCKER PRO TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 16.93 MXN Instant
PANDORA BOX DIGITAL LICENSE ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Pandora Box 1 Year Digital license (Without box)
PANDORA BOX DIGITAL LICENSE ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1579.21 MXN Instant
GUERRATOOL CREDITS - MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER THE GUERRATOOL MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - EXISTING USER
GUERRATOOL CREDITS - MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.96 MXN Instant
SERVER THE GUERRATOOL MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - NEW USER
GUERRATOOL CREDITS - MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.96 MXN Instant
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Ultimate NCK Huawei Activation ( Unlimited )
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1660.95 MXN Instant
SERVER UMT Emmc ISP Tool Activation - Without Hardware
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 309.58 MXN Instant
SERVER UMT Ultimate Multi Tool 1 Year Activation
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 460.66 MXN Instant
NCK BOX/DONGLE 1 YEAR ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER NCK BOX Yearly Activation
NCK BOX/DONGLE 1 YEAR ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 460.66 MXN Instant
SERVER Nck Dongle Activation (Yearly)
NCK BOX/DONGLE 1 YEAR ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 460.66 MXN Instant
MOTO-KEY MOTOROLA (MWORKER-TOOL) DIRECT UNLOCK/REPAIR CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER MWorker-Tool (Moto Key) Credits any Qty
MOTO-KEY MOTOROLA (MWORKER-TOOL) DIRECT UNLOCK/REPAIR CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 22.79 MXN Instant
SERVER Moto-Key ( MWorker-Tool ) 50 Credits
MOTO-KEY MOTOROLA (MWORKER-TOOL) DIRECT UNLOCK/REPAIR CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1064.57 MXN Instant
SERVER Moto-Key 100 Credits Min Qty 100
MOTO-KEY MOTOROLA (MWORKER-TOOL) DIRECT UNLOCK/REPAIR CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 2090.13 MXN Instant
UNLOCKTOOL LICENSE ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REPAIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER UnlockTool 12 months License
UNLOCKTOOL LICENSE ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REPAIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 914.08 MXN 1-6 Hours
SERVER UnlockTool 3 months License
UNLOCKTOOL LICENSE ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REPAIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 410.97 MXN 1-6 Hours
SERVER UnlockTool 6 months License
UNLOCKTOOL LICENSE ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REPAIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 593.04 MXN 1-6 Hours
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER EVO Tool Unlock 12 Months License
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1599.64 MXN 6-24 Hours
SERVER EVO Tool Unlock 3 Months License
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 673.3 MXN 6-24 Hours
SERVER EVO Tool Unlock 6 Months License
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1054.54 MXN 6-24 Hours
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Cheetah Tool - (LG Module Activation)
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 371.21 MXN Instant
SERVER Cheetah Tool Credit Any Qnt
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 20.25 MXN Instant
SERVER Cheetah Tool Pro Activation
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1170.47 MXN Instant
SAMKEY CODE READER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER SamKey Samsung Code Reader Credits New Account Any Quantity
SAMKEY CODE READER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 30.59 MXN Instant
SERVER Transfer credits to existing Samkey User
SAMKEY CODE READER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 30.59 MXN Instant
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER SamKey TMO / SPR/MTK Account 10 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 386.12 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 20 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 643.2 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 40 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 1211.34 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 100 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 2731.1 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 200 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 5053.46 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 500 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 11552.36 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 1000 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 20213.84 MXN Instant
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Sim-Unlocker Pro Credit Create New Account [ Any Quantity ]
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.86 MXN Instant
SERVER Sim-Unlocker Pro Credit Refill / ReCharge Old Account [ Any Quantity ]
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.86 MXN Instant
SERVER Sim-Unlocker(Pro) Sprint Special Edition Credit [ Create New User ]
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 21.81 MXN Instant
SERVER Sim-Unlocker(Pro) Sprint Special Edition Credit [ Refill / Recharge ] Already Exist Users
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 21.81 MXN Instant
GENERAL UNLOCKER PRO CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER General Unlocker Pro [ Samsung + LG + Alcatel + TINNO + Google + Moto ] unlock / repair / Frp / change css /bypass T-token - Credits for new user [ Auto API ]
GENERAL UNLOCKER PRO CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 17.32 MXN Instant
SERVER General Unlocker Pro [ Samsung + LG + Alcatel + TINNO + Google + Moto] unlock / repair / frp - Credits for Existing user [ Auto API ]
GENERAL UNLOCKER PRO CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 17.32 MXN Instant
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Global Unlocker Pro [ Samsung + LG + Alcatel + TINNO + Google ] unlock / repair / Frp / change css /bypass T-token - Credits for new user [ Auto API ]
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.86 MXN Instant
SERVER Global Unlocker Pro [ Samsung + LG + Alcatel + TINNO + Google] unlock / repair / frp - Credits for Existing user [ Auto API ]
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.86 MXN Instant
SERVER Global Unlocker Pro-New Annual User
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1742.7 MXN Instant
SERVER Global Unlocker Renewal Service
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1722.26 MXN Instant
DRAG UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Drag Unlocker [ Samsung + LG + Alcatel + TINNO + Google + Moto ] unlock / repair / Frp / change css /bypass T-token - Credits for new user
DRAG UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 18.69 MXN Instant
SERVER Drag Unlocker [ Samsung + LG + Alcatel + TINNO + Google + Moto] unlock / repair / frp - Credits for Existing user
DRAG UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 18.69 MXN Instant
XIAOMI AUTH TOOL - Xiaomi Pro Tool Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Xiaomi Pro Tool Credit Any Qnt (AUTH, FRP, FASTBOOT TO EDL)
XIAOMI AUTH TOOL - Xiaomi Pro Tool Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 18.89 MXN Instant
TIRA UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Tira unlocker [ Samsung + LG + XIAOMI + Alcatel + TINNO + Google + Vivo + Realme + MOTO ] unlock / repair / Frp / change css /bypass T-token Credits for new user [ Auto API ]
TIRA UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 15.96 MXN Instant
SERVER Tira unlocker [ Samsung + LG + XIAOMI + Alcatel + TINNO + Google + Vivo + Realme + MOTO ] unlock / repair / Frp / change css /bypass T-token Credits for Existing user
TIRA UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 15.96 MXN Instant
Xiaomi FIRE TOOL Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Xiaomi Fire Tool Credits (XFT) [Existing User]
Xiaomi FIRE TOOL Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 127.71 MXN Instant
SERVER Xiaomi Fire Tool Credits [ Create New User]
Xiaomi FIRE TOOL Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 127.71 MXN Instant
Xiaomi King Tool Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Xiaomi King Tool Any Qnt (AUTH) INSTANT
Xiaomi King Tool Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 18.89 MXN Instant
Free Fire Pin
SERVER FreeFire [ 100 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 23.76 MXN Instant
SERVER FreeFire [ 1080 + 108 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 258.02 MXN Instant
SERVER FreeFire [ 210 + 21 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 43.27 MXN Instant
SERVER FreeFire [ 2200 + 220 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 486.51 MXN Instant
SERVER FreeFire [ 530 + 53 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 169.45 MXN Instant
eBay USA
SERVER eBay-USD 10 (US)
eBay USA
$ 291.69 MXN Instant
SERVER eBay-USD 100 (US)
eBay USA
$ 2322.36 MXN Instant
SERVER eBay-USD 25 (US)
eBay USA
$ 613.1 MXN Instant
SERVER eBay-USD 5 (US)
eBay USA
$ 163.49 MXN Instant
SERVER eBay-USD 50 (US)
eBay USA
$ 1170.47 MXN Instant
Free Fire
SERVER Free Fire Diamond 110 [ DIRECT TOP-UP ] NEW
Free Fire
$ 23.76 MXN Instant
SERVER Free Fire Diamond 1080 [ DIRECT TOP-UP ] NEW
Free Fire
$ 258.02 MXN Instant
SERVER Free Fire Diamond 210 [ DIRECT TOP-UP ] NEW
Free Fire
$ 43.27 MXN Instant
SERVER Free Fire Diamond 2200 [ DIRECT TOP-UP ] NEW
Free Fire
$ 480.54 MXN Instant
SERVER Free Fire Diamond 530 [ DIRECT TOP-UP ] NEW
Free Fire
$ 169.45 MXN Instant
Amazon [ USA ]
SERVER Amazon US $10
Amazon [ USA ]
$ 301.63 MXN Instant
SERVER Amazon US $100
Amazon [ USA ]
$ 2322.36 MXN Instant
SERVER Amazon US $15
Amazon [ USA ]
$ 391.09 MXN Instant
SERVER Amazon US $25
Amazon [ USA ]
$ 613.1 MXN Instant
SERVER Amazon US $50
Amazon [ USA ]
$ 1170.47 MXN Instant
Google Play Store Gift Cards - USA ONLY
SERVER Amazon US $20
Google Play Store Gift Cards - USA ONLY
$ 512.78 MXN Instant
SERVER Amazon US $5
Google Play Store Gift Cards - USA ONLY
$ 173.34 MXN Instant
SERVER Google Play USD 10 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 301.63 MXN Instant
SERVER Google Play USD 5 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 173.34 MXN Instant
SERVER Google Play USD 50 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 1180.69 MXN Instant
SERVER Google Play USD100 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 2322.36 MXN Instant
SERVER Google Play USD15 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 401.03 MXN Instant
SERVER Google Play USD20 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 522.81 MXN Instant
SERVER Google Play USD25 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 623.14 MXN Instant
ROBLOX
SERVER Roblox $10
ROBLOX
$ 291.69 MXN Instant
SERVER Roblox $15
ROBLOX
$ 391.09 MXN Instant
SERVER Roblox $25
ROBLOX
$ 613.1 MXN Instant
SERVER Roblox 50 $
ROBLOX
$ 1170.47 MXN Instant
MobileSea Service Tool CREDITS 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER MobileSea Tool 12 Month Activation
MobileSea Service Tool CREDITS 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 410.97 MXN 1-6 Hours
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER BORNEO 1 USER LICENSE 3 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 351.33 MXN Instant
SERVER BORNEO 1 USER LICENSE 6 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 532.84 MXN Instant
SERVER BORNEO 1 USER LICENSE 12 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 833.82 MXN Instant
SERVER BORNEO 1 USER LICENSE 12 MONTHS RENEW
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 753.56 MXN Instant
SERVER BORNEO 2 USER LICENSE 3 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 552.91 MXN Instant
SERVER BORNEO 2 USER LICENSE 6 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 853.89 MXN Instant
SERVER BORNEO 2 USER LICENSE 12 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 1170.47 MXN Instant
SERVER BORNEO 2 USER LICENSE 12 MONTHS RENEW
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 954.21 MXN Instant
T-Unlock Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER T-UnLock / Tunlock Credits Any Quantity [ Samsung , LG , Kyocera ] Direct unlock - ( new user , refill existing user ) Auto API
T-Unlock Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 12.84 MXN Instant
Chimeratool.com - Samsung,LG,Motorola...(Proffesional Service Software) Credits 24.7 Real Time Instant - Official Worldwide Reseller
SERVER Chimera Tool Credits
Chimeratool.com - Samsung,LG,Motorola...(Proffesional Service Software) Credits 24.7 Real Time Instant - Official Worldwide Reseller
$ 6.6 MXN Instant
KingUnlock.net- Samsung (Cheapest Direct Remote Unlock) Activation/Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Kingunlock.net Activation Service
KingUnlock.net- Samsung (Cheapest Direct Remote Unlock) Activation/Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 291.69 MXN Instant
SERVER KingUnlock.Net Create New User + Credits
KingUnlock.net- Samsung (Cheapest Direct Remote Unlock) Activation/Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 12.06 MXN Instant
PUBG New State PIN
SERVER PUBG New State 1500 NC+80 Bonus PIN
PUBG New State PIN
$ 168.42 MXN Instant
SERVER PUBG New State 15000 NC+1800 Bonus PIN
PUBG New State PIN
$ 1094.67 MXN Instant
SERVER PUBG New State 300 NC PIN
PUBG New State PIN
$ 23.96 MXN Instant
SERVER PUBG New State 30000 NC+5000 Bonus PIN
PUBG New State PIN
$ 2110.56 MXN Instant
KEY-TOOL TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER KEY-Tool [ Samsung ] Direct UnLock / Change CSC - Credits for Existing user
KEY-TOOL TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 17.91 MXN Instant
FAST UNLOCKER PRO TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Fast Unlocker Pro [ Samsung + LG + Alcatel + TINNO ...etc ] unlock / repair / Frp / change css /bypass T-token - Credits for new user [ Auto API ]
FAST UNLOCKER PRO TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 16.93 MXN Instant
SERVER Fast Unlocker Pro [ Samsung + LG + Alcatel + TINNO ...etc] unlock / repair / frp - Credits for Existing user [ Auto API ]
FAST UNLOCKER PRO TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 16.93 MXN Instant
PANDORA BOX DIGITAL LICENSE ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Pandora Box 1 Year Digital license (Without box)
PANDORA BOX DIGITAL LICENSE ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1579.21 MXN Instant
GUERRATOOL CREDITS - MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER THE GUERRATOOL MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - EXISTING USER
GUERRATOOL CREDITS - MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.96 MXN Instant
SERVER THE GUERRATOOL MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - NEW USER
GUERRATOOL CREDITS - MOTOROLA MTK/SPD (REPAIR IMEI, MDM, UNLOCK, READ NCK) - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 23.96 MXN Instant
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Ultimate NCK Huawei Activation ( Unlimited )
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1660.95 MXN Instant
SERVER UMT Emmc ISP Tool Activation - Without Hardware
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 309.58 MXN Instant
SERVER UMT Ultimate Multi Tool 1 Year Activation
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 460.66 MXN Instant
NCK BOX/DONGLE 1 YEAR ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER NCK BOX Yearly Activation
NCK BOX/DONGLE 1 YEAR ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 460.66 MXN Instant
SERVER Nck Dongle Activation (Yearly)
NCK BOX/DONGLE 1 YEAR ACTIVATION - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 460.66 MXN Instant
MOTO-KEY MOTOROLA (MWORKER-TOOL) DIRECT UNLOCK/REPAIR CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER MWorker-Tool (Moto Key) Credits any Qty
MOTO-KEY MOTOROLA (MWORKER-TOOL) DIRECT UNLOCK/REPAIR CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 22.79 MXN Instant
SERVER Moto-Key ( MWorker-Tool ) 50 Credits
MOTO-KEY MOTOROLA (MWORKER-TOOL) DIRECT UNLOCK/REPAIR CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1064.57 MXN Instant
SERVER Moto-Key 100 Credits Min Qty 100
MOTO-KEY MOTOROLA (MWORKER-TOOL) DIRECT UNLOCK/REPAIR CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 2090.13 MXN Instant
UNLOCKTOOL LICENSE ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REPAIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER UnlockTool 12 months License
UNLOCKTOOL LICENSE ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REPAIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 914.08 MXN 1-6 Hours
SERVER UnlockTool 3 months License
UNLOCKTOOL LICENSE ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REPAIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 410.97 MXN 1-6 Hours
SERVER UnlockTool 6 months License
UNLOCKTOOL LICENSE ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REPAIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 593.04 MXN 1-6 Hours
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER EVO Tool Unlock 12 Months License
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1599.64 MXN 6-24 Hours
SERVER EVO Tool Unlock 3 Months License
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 673.3 MXN 6-24 Hours
SERVER EVO Tool Unlock 6 Months License
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1054.54 MXN 6-24 Hours
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Cheetah Tool - (LG Module Activation)
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 371.21 MXN Instant
SERVER Cheetah Tool Credit Any Qnt
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 20.25 MXN Instant
SERVER Cheetah Tool Pro Activation
CHEETAH TOOL - SAMSUNG,LG [ ACTIVATION,CREDITS] - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1170.47 MXN Instant
SAMKEY CODE READER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER SamKey Samsung Code Reader Credits New Account Any Quantity
SAMKEY CODE READER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 30.59 MXN Instant
SERVER Transfer credits to existing Samkey User
SAMKEY CODE READER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 30.59 MXN Instant
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER SamKey TMO / SPR/MTK Account 10 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 386.12 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 20 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 643.2 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 40 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 1211.34 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 100 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 2731.1 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 200 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 5053.46 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 500 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 11552.36 MXN Instant
SERVER SamKey TMO / SPR/MTK Account 1000 Credit (Instant)
Samkey TMO- Samsung (T-Mobile, MetroPCS, Verizon, Sprint APP UNLOCK) Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 20213.84 MXN Instant
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Sim-Unlocker Pro Credit Create New Account [ Any Quantity ]
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.86 MXN Instant
SERVER Sim-Unlocker Pro Credit Refill / ReCharge Old Account [ Any Quantity ]
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.86 MXN Instant
SERVER Sim-Unlocker(Pro) Sprint Special Edition Credit [ Create New User ]
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 21.81 MXN Instant
SERVER Sim-Unlocker(Pro) Sprint Special Edition Credit [ Refill / Recharge ] Already Exist Users
SIM-UNLOCKER PRO- app.sim-unlocker.net CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 21.81 MXN Instant
GENERAL UNLOCKER PRO CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER General Unlocker Pro [ Samsung + LG + Alcatel + TINNO + Google + Moto ] unlock / repair / Frp / change css /bypass T-token - Credits for new user [ Auto API ]
GENERAL UNLOCKER PRO CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 17.32 MXN Instant
SERVER General Unlocker Pro [ Samsung + LG + Alcatel + TINNO + Google + Moto] unlock / repair / frp - Credits for Existing user [ Auto API ]
GENERAL UNLOCKER PRO CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 17.32 MXN Instant
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Global Unlocker Pro [ Samsung + LG + Alcatel + TINNO + Google ] unlock / repair / Frp / change css /bypass T-token - Credits for new user [ Auto API ]
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.86 MXN Instant
SERVER Global Unlocker Pro [ Samsung + LG + Alcatel + TINNO + Google] unlock / repair / frp - Credits for Existing user [ Auto API ]
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 19.86 MXN Instant
SERVER Global Unlocker Pro-New Annual User
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1742.7 MXN Instant
SERVER Global Unlocker Renewal Service
GLOBAL-UNLOCKER-PRO.COM SAMSUNG,LG,ALCATEL,NOKIA(PROFFESIONAL SERVICE SOFTWARE) CREDITS 24.7 REAL TIME INSTANT- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 1722.26 MXN Instant
DRAG UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Drag Unlocker [ Samsung + LG + Alcatel + TINNO + Google + Moto ] unlock / repair / Frp / change css /bypass T-token - Credits for new user
DRAG UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 18.69 MXN Instant
SERVER Drag Unlocker [ Samsung + LG + Alcatel + TINNO + Google + Moto] unlock / repair / frp - Credits for Existing user
DRAG UNLOCKER TOOL CREDITS - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 18.69 MXN Instant
XIAOMI AUTH TOOL - Xiaomi Pro Tool Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Xiaomi Pro Tool Credit Any Qnt (AUTH, FRP, FASTBOOT TO EDL)
XIAOMI AUTH TOOL - Xiaomi Pro Tool Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 18.89 MXN Instant
TIRA UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER Tira unlocker [ Samsung + LG + XIAOMI + Alcatel + TINNO + Google + Vivo + Realme + MOTO ] unlock / repair / Frp / change css /bypass T-token Credits for new user [ Auto API ]
TIRA UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 15.96 MXN Instant
SERVER Tira unlocker [ Samsung + LG + XIAOMI + Alcatel + TINNO + Google + Vivo + Realme + MOTO ] unlock / repair / Frp / change css /bypass T-token Credits for Existing user
TIRA UNLOCKER TOOL CREDITS- OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 15.96 MXN Instant
Xiaomi FIRE TOOL Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Xiaomi Fire Tool Credits (XFT) [Existing User]
Xiaomi FIRE TOOL Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 127.71 MXN Instant
SERVER Xiaomi Fire Tool Credits [ Create New User]
Xiaomi FIRE TOOL Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 127.71 MXN Instant
Xiaomi King Tool Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Xiaomi King Tool Any Qnt (AUTH) INSTANT
Xiaomi King Tool Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 18.89 MXN Instant
Free Fire Pin
SERVER FreeFire [ 100 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 23.76 MXN Instant
SERVER FreeFire [ 1080 + 108 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 258.02 MXN Instant
SERVER FreeFire [ 210 + 21 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 43.27 MXN Instant
SERVER FreeFire [ 2200 + 220 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 486.51 MXN Instant
SERVER FreeFire [ 530 + 53 ] [ GARENA ] Diamonds Pin
Free Fire Pin
$ 169.45 MXN Instant
eBay USA
SERVER eBay-USD 10 (US)
eBay USA
$ 291.69 MXN Instant
SERVER eBay-USD 100 (US)
eBay USA
$ 2322.36 MXN Instant
SERVER eBay-USD 25 (US)
eBay USA
$ 613.1 MXN Instant
SERVER eBay-USD 5 (US)
eBay USA
$ 163.49 MXN Instant
SERVER eBay-USD 50 (US)
eBay USA
$ 1170.47 MXN Instant
Free Fire
SERVER Free Fire Diamond 110 [ DIRECT TOP-UP ] NEW
Free Fire
$ 23.76 MXN Instant
SERVER Free Fire Diamond 1080 [ DIRECT TOP-UP ] NEW
Free Fire
$ 258.02 MXN Instant
SERVER Free Fire Diamond 210 [ DIRECT TOP-UP ] NEW
Free Fire
$ 43.27 MXN Instant
SERVER Free Fire Diamond 2200 [ DIRECT TOP-UP ] NEW
Free Fire
$ 480.54 MXN Instant
SERVER Free Fire Diamond 530 [ DIRECT TOP-UP ] NEW
Free Fire
$ 169.45 MXN Instant
Amazon [ USA ]
SERVER Amazon US $10
Amazon [ USA ]
$ 301.63 MXN Instant
SERVER Amazon US $100
Amazon [ USA ]
$ 2322.36 MXN Instant
SERVER Amazon US $15
Amazon [ USA ]
$ 391.09 MXN Instant
SERVER Amazon US $25
Amazon [ USA ]
$ 613.1 MXN Instant
SERVER Amazon US $50
Amazon [ USA ]
$ 1170.47 MXN Instant
Google Play Store Gift Cards - USA ONLY
SERVER Amazon US $20
Google Play Store Gift Cards - USA ONLY
$ 512.78 MXN Instant
SERVER Amazon US $5
Google Play Store Gift Cards - USA ONLY
$ 173.34 MXN Instant
SERVER Google Play USD 10 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 301.63 MXN Instant
SERVER Google Play USD 5 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 173.34 MXN Instant
SERVER Google Play USD 50 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 1180.69 MXN Instant
SERVER Google Play USD100 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 2322.36 MXN Instant
SERVER Google Play USD15 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 401.03 MXN Instant
SERVER Google Play USD20 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 522.81 MXN Instant
SERVER Google Play USD25 Gift Card (US) Google Play US Store ONLY
Google Play Store Gift Cards - USA ONLY
$ 623.14 MXN Instant
ROBLOX
SERVER Roblox $10
ROBLOX
$ 291.69 MXN Instant
SERVER Roblox $15
ROBLOX
$ 391.09 MXN Instant
SERVER Roblox $25
ROBLOX
$ 613.1 MXN Instant
SERVER Roblox 50 $
ROBLOX
$ 1170.47 MXN Instant
MobileSea Service Tool CREDITS 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
SERVER MobileSea Tool 12 Month Activation
MobileSea Service Tool CREDITS 24.7 REAL TIME INSTANT - OFFICIAL WORLDWIDE DISTRIBUTOR ✅
$ 410.97 MXN 1-6 Hours
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER BORNEO 1 USER LICENSE 3 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 351.33 MXN Instant
SERVER BORNEO 1 USER LICENSE 6 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 532.84 MXN Instant
SERVER BORNEO 1 USER LICENSE 12 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 833.82 MXN Instant
SERVER BORNEO 1 USER LICENSE 12 MONTHS RENEW
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 753.56 MXN Instant
SERVER BORNEO 2 USER LICENSE 3 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 552.91 MXN Instant
SERVER BORNEO 2 USER LICENSE 6 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 853.89 MXN Instant
SERVER BORNEO 2 USER LICENSE 12 MONTHS
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 1170.47 MXN Instant
SERVER BORNEO 2 USER LICENSE 12 MONTHS RENEW
Borneo Schematic Hardware Solutions Activations 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 954.21 MXN Instant
T-Unlock Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER T-UnLock / Tunlock Credits Any Quantity [ Samsung , LG , Kyocera ] Direct unlock - ( new user , refill existing user ) Auto API
T-Unlock Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 12.84 MXN Instant
Chimeratool.com - Samsung,LG,Motorola...(Proffesional Service Software) Credits 24.7 Real Time Instant - Official Worldwide Reseller
SERVER Chimera Tool Credits
Chimeratool.com - Samsung,LG,Motorola...(Proffesional Service Software) Credits 24.7 Real Time Instant - Official Worldwide Reseller
$ 6.6 MXN Instant
KingUnlock.net- Samsung (Cheapest Direct Remote Unlock) Activation/Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
SERVER Kingunlock.net Activation Service
KingUnlock.net- Samsung (Cheapest Direct Remote Unlock) Activation/Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 291.69 MXN Instant
SERVER KingUnlock.Net Create New User + Credits
KingUnlock.net- Samsung (Cheapest Direct Remote Unlock) Activation/Credits 24.7 Real Time Instant - Official Worldwide Distributor ✅
$ 12.06 MXN Instant
Direct Unlock Motorola G STYLUS 5G (2022)
Waiting for Device in Factory Mode.....Found!
Reading Data...Done
FSG: MILANF_PVT_NA_CUST
Firmware: S2SDS32.21-85-3-2-1-2
Android Version: 12
Model: G STYLUS 5G (2022)
SKU: XT2215-4
SN: ZY22GTVGCR
IMEI 1: 351475466048716
Carrier: tmo
Checking Device Connection ... Done
Checking Price for Device....Done
Creating Order ID....Done
Operation ID: 1748806
Erasing UTAG IMEI ... Done
Reading Device Configuration ... Done
Wiping IMEI ... Done
Writing New Security (0C03)... Done.
Writing IMEI ... Done
New IMEI 1: 351475466048716
Writing New Security (0C03)... Done.
Writing UTAG IMEI ... Done
Erasing Factory Mode ... Done
Rebooting to Fastboot ... Done
Elapsed Time: 2:07.32
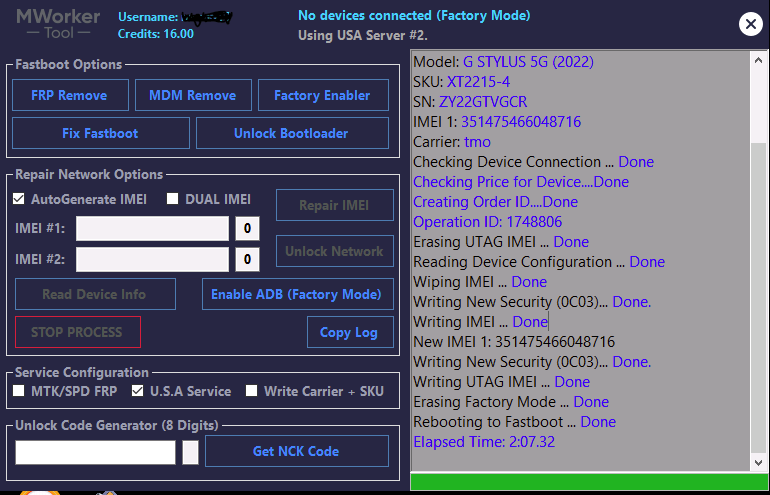
FRP Samsung SM-J106H
- Shark Tool (V0.0.0.5)
- Operation : [Remove FRP]
- Detecting Samsung modem port : SAMSUNG Mobile USB Modem
- Selected ComPort : COM52
- Connecting : OK
- Reading info : OK
- Model: SM-J106H
- Baseband: J106HDDS0ARH1
- Software: J106HDDS0ARH1
- Sales Code: SM-
- SN: RV1K106YCHX
- IMEI: 35481009193775
- UN: CFN00278AF20AB4
- Software REV: BIT[0]
- Software Build Date: 2018-08-01
- Checking device lock : TRIGGERED
- Checking server data : OK
- This operation takes 5 credits. Continue? Confirmed
- Connecting to shark server : OK
- Work id : [886315]
- Requesting device data : OK
- Generating lock hash : OK
- Calculating phone data : OK
- Removing lock state : OK
- Verifying lock state : verified
- Rebooting : OK
- FRP-Account removed successfully
- Operation finished (00:12) 2023-10-27 04:13:02 PM
Direct Unlock OVATION U705AC by Furious Gold
Using library Brom_DLL_v7.1813.3
Engine version 1.0.0.6367
Searching phone;
(insert the USB cable in the powered off phone
or
insert the USB cable in the powered off phone while keeping volume down pressed)
or
insert the USB cable in the powered off phone while keeping volume down+up pressed)
Phone detected (MediaTek USB Port (COM39))
Preparing to start meta mode;
Disabling watchdog timer;
Done;
Exploited;
Sec code uploaded;
Executed;
Vodka time;
Ready to party;
Searching for debug port; (be sure drivers from support were installed)
Meta mode entered;
Baseband Chip: MT6765
Sw version:
Hw Version: alps-mp-q0.mp1-V9.23_tinno.sh.q0mp1.k61v1.64.bsp_P74
Baseband Chip: MT6765
Sw version: MOLY.LR12A.R3.MP.V101.3.P55
Hw Version: TK_MD_L4_HW
Reading phone info;
IMEI 1: 869072-04-192189-0
IMEI 2: N/A
BB ID: QzFGQzY2QzYwMDQ0MjlCMDY0Q0QzNjlENDRFMUFFMUE=
Working;
Connecting to server;
Authorisation process started;
Furious Multipurpose Credits: 14
Done;
Requesting data from server ! Wait please ...
Checking data integrity;
Data integrity: OK;
SIM_LOCK: ENABLED
Rebuilding security;
Unlocking;
Phone unlocked; Remove battery and cable;
Time needed - 00:01:50
Log file saved to: LOG_23_10_2023_17_45_59.txt
FRP Motorola Moto G20 XT2128-1
FORMAT DATA
Selected Platform :
Tiger T700_64_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM68 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\5&1B14D878&0&3
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
[72]
Reading
device info
...
OK
[super]
Model Name :
moto g(20)
Product Name :
java_retail
Manufacturer :
motorola
Android Version :
11
Security Patch :
2023-03-01
Build ID :
RTAS31.68-66-3
Build Date :
Tue Feb 21 13:40:32 CST 2023
Erasing
FRP (persist)
...
OK
Erasing
USERDATA
...
OK
UNLOCKTOOL
2023.09.23.0
Elapsed time :
28 seconds
Direct Unlock Samsung SM-G950U
Chimera Mobile Phone Utility version: 37.16.1131 @ 2023-10-06
Read codes started
Gathering phone info...
Unlock.mx......
Collecting information. Be patient! Do NOT disconnect the phone!
Model: SM-G950U
Carrier ID: ATT
Sales Code: ATT
Country Code: USA
Timezone: America/Los_Angeles
Android Version: 8.0.0 [R16NW] [SDK 26]
Build Date: Fri Sep 28 17:51:06 KST 2018
PDA Version: G950USQU5CRIB [september 2018, revB]
Phone Version: G950USQU5CRIB [september 2018, revB]
CSC Version: G950UOYN5CRIB [september 2018, revB]
Board Platform: MSM8998
Modem Platform: MSM8998
Serial Number: R38J307BLKF
Imei: 357724080002375
Battery Status: 4.12V (77%)
Network Type: GSM
SIM Status: READY
Multisim Config: SS
Knox Version: v30
Warranty Bit: 0
Security Patch: 2018-10-01
Em Did: 205E9B7A5F4B
Preparing...
Restarting phone.
Waiting for ADB connection. Be patient! Do NOT disconnect the phone!
Restarting phone.
Waiting for ADB connection. Be patient! Do NOT disconnect the phone!
The phone will restart in upload mode.
Switching to upload mode. Be patient! Do NOT disconnect the phone!
Waiting for upload interface...
Waiting for upload interface. Be patient! Do NOT disconnect the phone!
Upload interface: SAMSUNG Mobile USB Modem (COM27)
Reading data...
Reading data is in progress. Be patient! Do NOT disconnect the phone!
Communicating with the server...
The phone can be unplugged now.
Waiting for server response...
This operation costed 49 credits.
Freeze/PUK: 00000000
Network Lock: 86952685
Subset Lock: 00000000
SP Lock: 00000000
CP Lock: 00000000
Successfully finished.
Finished at local time: [10.06.23 08:25:04]
WorkID: 237983000
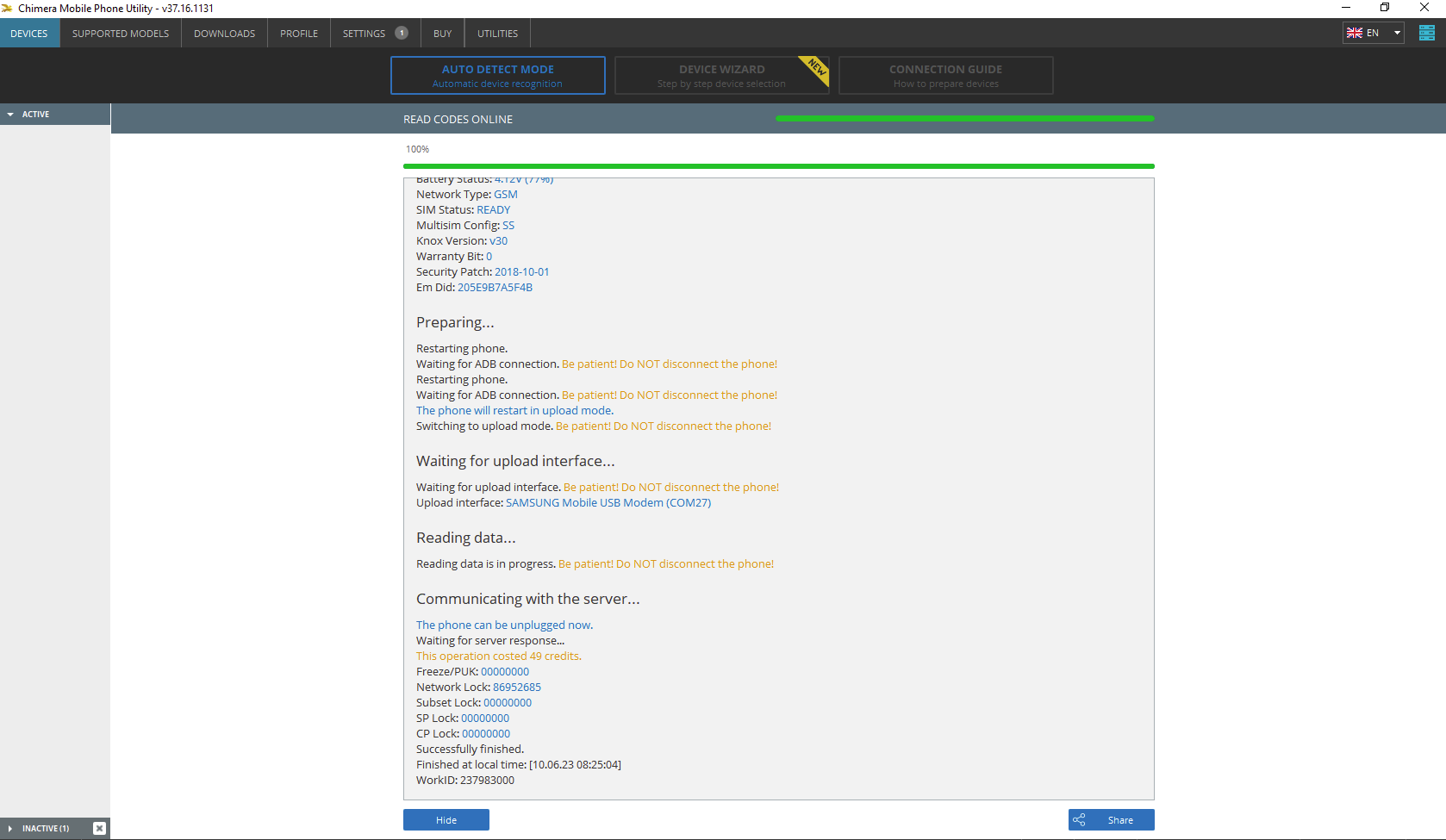
Direct Unlock Samsung J3 Star SM-J337T T-mobile by SamKey TMO
Searching for SAMSUNG Mobile USB Modem...OK
SAMSUNG USB Modem detected on [COM29]
Looking for DEVICE...OK
Reading USB MODEM information...OK
MODEL : SM-J337T
VER : J337TUVSAAUB2/J337TTMBAAUB2/J337TUVSAAUB2/J337TUVSAAUB2
IMEI : 354272096377947
S/N : R28KB0XSW8
U/N : CQE00E7BB060DA5
Loading ADB module............OK
Starting ADB module...OK
Searching for SAMSUNG ADB device...OK
Checking device authorization...OK
Device CodeName : J3TOPLTETMO
ADB Serial Number : 4200e7bb060da5ad
AP Version : J337TUVSAAUB2
CP Version : J337TUVSAAUB2
CSC Version : J337TTMBAAUB2
Android Version : 8.0.0
Algorithm : New 2021 SDK
SIM State : OK
IMEI : 354272096377947
Debug Level : 0x4f4c
Setting DEBUG level to HIGH.........OK
Waiting for Reboot...OK
Checking data validity...PASS
Executing RIL applet...OK
Starting RIL applet...OK
Creating CpDump data...OK
Rebooting device........OK
Waiting for Reboot...OK
Analysing CpDump data...[CHK:OK]...[CPY:OK]...OK
Sending data to SERVER...OK
Waiting for SERVER response...OK
Starting RIL applet...OK
Unlocking phone...OK
Operation successful.
PLEASE REBOOT PHONE MANUALLY TO FINISH UNLOCK!
SamKEY Team (2017)
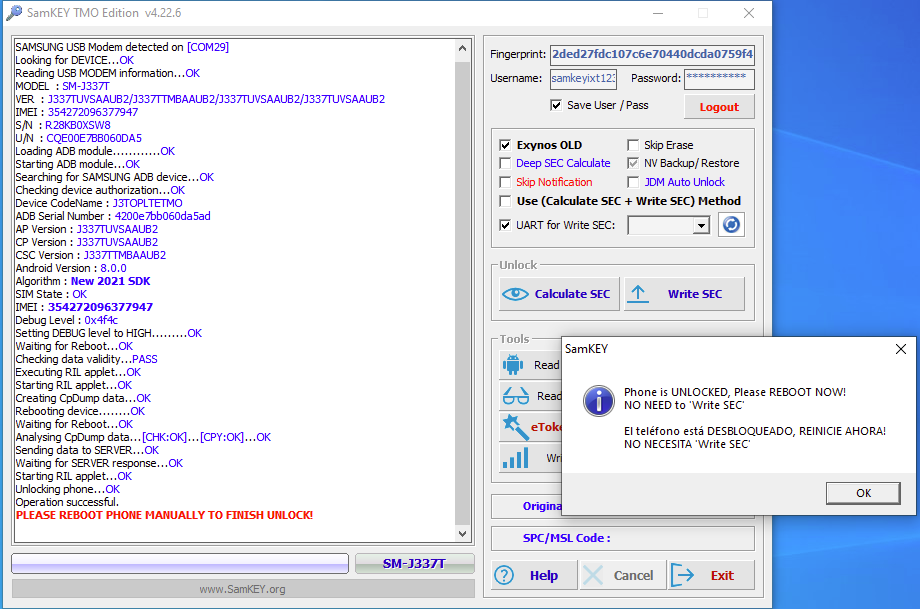
FRP Samsung SM-J337T
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:002473 SourceURL:file%3a%2f%2f
[COM] REMOVE FRP [2023]
Scanning for device...
COM59
Reading Info...
FAIL
Trying method [1]...
OK
Waiting for device...
Please accept USB Debugging on your phone!
Model :
SM-J337T
Manufacturer :
samsung
Platform :
exynos5
CPU Arch :
armeabi-v7a
Android Serial :
4200e7bb060da5ad
Manufacturing Date :
20181109
Security Patch :
2021-01-01
Connection :
mtp,adb
Timezone :
America/Mexico_City
Knox Warranty :
0 - valid
Android Version :
8.0.0
Android SDK :
26
Build :
R16NW.J337TUVSAAUB2
Build Date :
Wed Feb 10 17:05:00 KST 2021
Product Code :
SM2J337TZDATMB
Samsung Serial :
R28KB0XSW8N
Device Name :
j3topltetmo
Product Name :
j3topltetmo
Code Name :
SM2J337TZDATMB
BL :
J337TUVSAAUB2
PDA :
J337TUVSAAUB2
CP :
J337TUVSAAUB2
CSC :
J337TTMBAAUB2
Sales Code :
TMB
Removing
FRP
...
OK
UNLOCKTOOL
2023.09.23.0
Elapsed time :
37 seconds
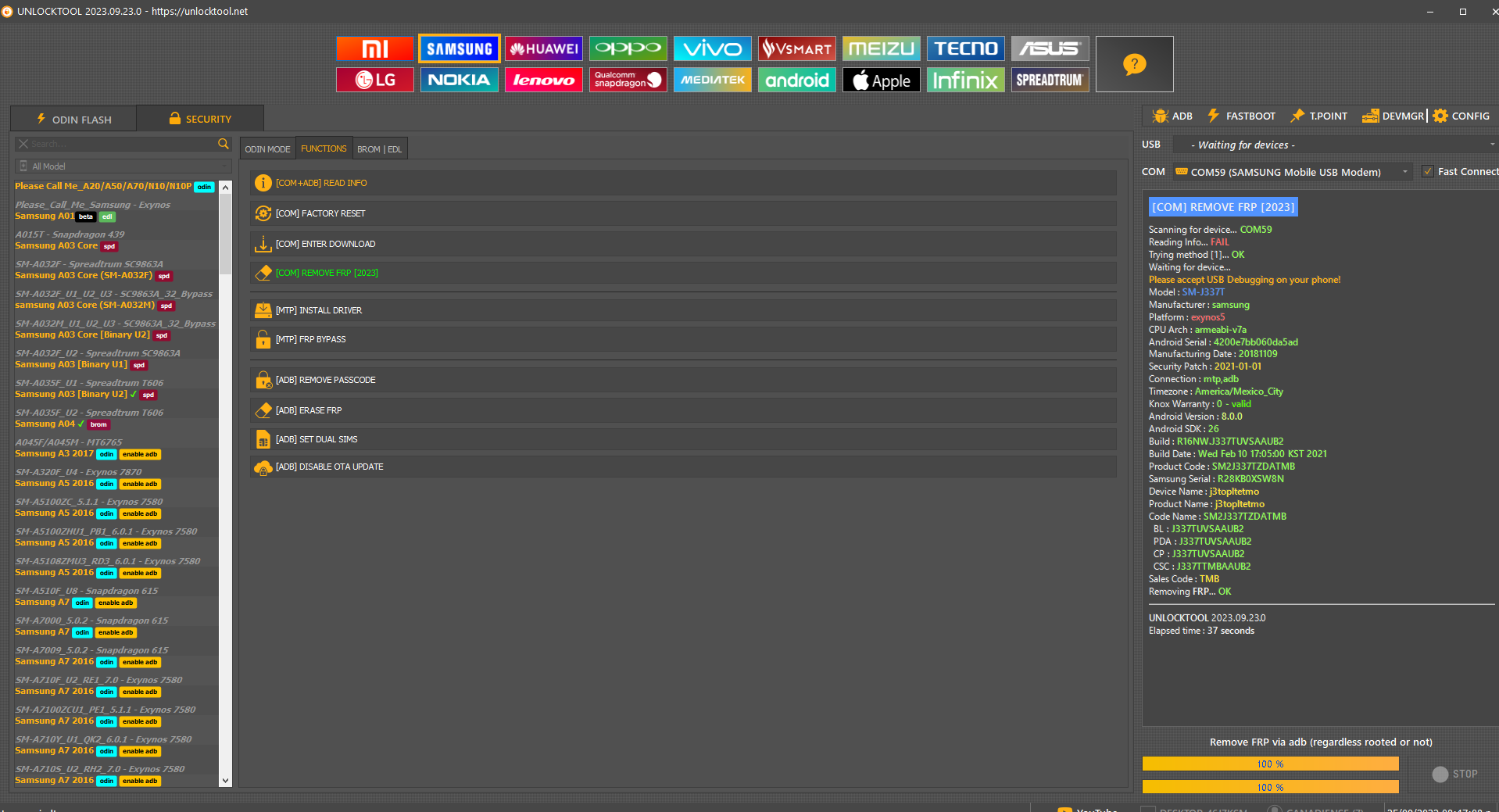
Direct Unlock Samsung A12 SM-A125U T-mobile by SamKey MTK
Searching for SAMSUNG USB Modem ...COM28
● Model ...SM-A125U
● Sw version ...A125USQU3BUG7/A125UOYN3BUG7/A125USQU3BUG7/A125USQU3BUG7
● Carrier ...TMB
● Serial Number ...R58R84LNFXH
● IMEI ...359011833379781
Checkig Security.......PASS
Waiting For ADB Device : OK
● Product Model ...SM-A125U
● Brand ...samsung
● Android ...11
● Manufacturer ...samsung
● Security Patch ...2021-07-01
● SDK Version ...30
● Encryption State ...encrypted
● Protection FRP ...PERSISTENT
● Hardware ...mt6765
● Platform ...mt6765
● Product locale ...en-US
Rebooting to Download Mode...OK
Searching for SAMSUNG USB Modem ...COM27
Writing custom bootloader...OK
Unlock Network
Waiting for bootrom usb device... ok
BootMode : BootRom[COM39]
● BBChip ID MT6765
● BBChip Inf 766:8A00:CA00:0
● Chip PID Helio P35
● Chip UID cervino
● Chip Ver CHIP_VER_E1
BRom::SEC:{0xe5}[SBC:ON:SLA:OFF:DAA:ON]
BRom stage Re-configuration
● BR_MEID:0xF261765D27361E720154FC2FAEB6339E
Sending registers
Dumping Dram data(0x6c8e0300)...
Re-connecting to BootROM...
BRom::SEC:{0x0}[SBC:OFF:SLA:OFF:DAA:OFF]
BRom::SEC:{0x0}[SBC:OFF:SLA:OFF:DAA:OFF]
Sending DA..
Successfully DA 1 Loaded
Successfully DA 2 Loaded
Ram Info
● Sram 224.00KB
● Dram 3.00GB
●●●●Hardware Info●●●●
● Storage eMMC
● BOOT1 4.00MB
● BOOT2 4.00MB
● RPMB 16.00MB
● USRDT 29.12GB
● CID 150100445836384D4200D858906988D7
● MFRID 0x15
● Vendor Samsung
● Card BGA BGA (Discrete embedded)
● OEMID 0x0
● Product DX68MB
● Revision 0.0
● Card SN 0xd8589069
● MFDate 8/2021
● EMCP KMDX60018M_B425
● Capacity 29.14GB
● RNID DE4287E9EC4A22170FCE2B83EBF60ABF
Trying to Connect to usb high-speed.
Waiting for bootrom usb device... ok
BootMode : DAVcom[COM21]
● USBSpeed high-speed
● ManfcID SAMSUNG
● MName A12USQ
● Model SM-A125U
● Product SAMSUNG
● Fw Ver RP1A.200720.012.A125USQU3BUG7
● BuildID RP1A.200720.012
● Android 11 (Red Velvet Cake)
● EMI ID A12USQ
● S Patch 2021-07-01
● Region EN-US
● CPUApi ARM64-V8A
● SVer A125USQU3BUG7
● Host 21DJF604
● BT Addr 00:00:46:00:00:01
Making Security Backup[#1] ...Success
Making Security Backup[#2] ...Success
Making Security Backup[#3] ...Success
Making Security Backup[#4] ...Success
Rebooting Device... [PLEASE POWER ON MANUALLY IF IS NOT DONE AUTO]
Rebooting.OK
Waiting For ADB Device : OK
Rebooting to Download Mode...OK
Searching for SAMSUNG USB Modem ...COM27
Writing custom bootloader...OK
Waiting for bootrom usb device... ok
BootMode : BootRom[COM39]
● BBChip ID MT6765
● BBChip Inf 766:8A00:CA00:0
● Chip PID Helio P35
● Chip UID cervino
● Chip Ver CHIP_VER_E1
BRom::SEC:{0xe5}[SBC:ON:SLA:OFF:DAA:ON]
BRom stage Re-configuration
● BR_MEID:0xF261765D27361E720154FC2FAEB6339E
Sending registers
Dumping Dram data(0x6c8e0300)...
Re-connecting to BootROM...
BRom::SEC:{0x0}[SBC:OFF:SLA:OFF:DAA:OFF]
BRom::SEC:{0x0}[SBC:OFF:SLA:OFF:DAA:OFF]
Sending DA..
Successfully DA 1 Loaded
Successfully DA 2 Loaded
Ram Info
● Sram 224.00KB
● Dram 3.00GB
●●●●Hardware Info●●●●
● Storage eMMC
● BOOT1 4.00MB
● BOOT2 4.00MB
● RPMB 16.00MB
● USRDT 29.12GB
● CID 150100445836384D4200D858906988D7
● MFRID 0x15
● Vendor Samsung
● Card BGA BGA (Discrete embedded)
● OEMID 0x0
● Product DX68MB
● Revision 0.0
● Card SN 0xd8589069
● MFDate 8/2021
● EMCP KMDX60018M_B425
● Capacity 29.14GB
● RNID DE4287E9EC4A22170FCE2B83EBF60ABF
Trying to Connect to usb high-speed.
Waiting for bootrom usb device... ok
BootMode : DAVcom[COM21]
● USBSpeed high-speed
● ManfcID SAMSUNG
● MName A12USQ
● Model SM-A125U
● Product SAMSUNG
● Fw Ver RP1A.200720.012.A125USQU3BUG7
● BuildID RP1A.200720.012
● Android 11 (Red Velvet Cake)
● EMI ID A12USQ
● S Patch 2021-07-01
● Region EN-US
● CPUApi ARM64-V8A
● SVer A125USQU3BUG7
● Host 21DJF604
● BT Addr 00:00:46:00:00:01
Restoring Security ...Done
Writing Security [#1] ...Success
Writing Security [#2] ...Success
Writing Security [#3] ...Success
Network Unlock Successfully Done!
Rebooting device... Done
● Time elapsed ...02:min:32:sec
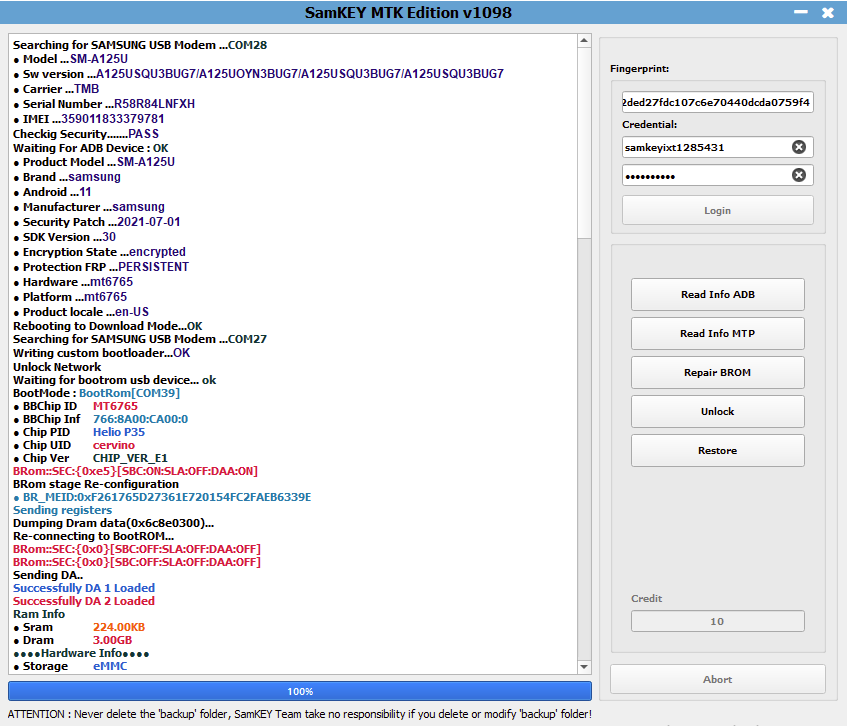
Direct Unlock Samsung A12 SM-A125U T-mobile
Searching for SAMSUNG USB Modem ...COM22
● Model ...SM-A125U
● Sw version ...A125USQU3BVB1/A125UOYN3BVB1/A125USQU3BVB1/A125USQU3BVB1
● Carrier ...TMB
● Serial Number ...R58R90645QX
● IMEI ...359011836731004
Checkig Security.......PASS
Waiting For ADB Device : OK
● Product Model ...SM-A125U
● Brand ...samsung
● Android ...11
● Manufacturer ...samsung
● Security Patch ...2022-01-01
● SDK Version ...30
● Encryption State ...encrypted
● Protection FRP ...PERSISTENT
● Hardware ...mt6765
● Platform ...mt6765
● Product locale ...en-US
Rebooting to Download Mode...OK
Searching for SAMSUNG USB Modem ...COM27
fail get access to port
Unlock Network
Waiting for bootrom usb device... device not found!
Waiting For ADB Device : OK
Rebooting to Download Mode...OK
Searching for SAMSUNG USB Modem ...COM27
Writing custom bootloader...OK
Waiting for bootrom usb device... ok
BootMode : BootRom[COM39]
● BBChip ID MT6765
● BBChip Inf 766:8A00:CA00:0
● Chip PID Helio P35
● Chip UID cervino
● Chip Ver CHIP_VER_E1
BRom::SEC:{0xe5}[SBC:ON:SLA:OFF:DAA:ON]
BRom stage Re-configuration
● BR_MEID:0x096ABACB3B390775C421FE0330282E74
Sending registers
Dumping Dram data(0x9c8e0300)...
Re-connecting to BootROM...
BRom::SEC:{0x0}[SBC:OFF:SLA:OFF:DAA:OFF]
BRom::SEC:{0x0}[SBC:OFF:SLA:OFF:DAA:OFF]
Sending DA..
Successfully DA 1 Loaded
Successfully DA 2 Loaded
Ram Info
● Sram 224.00KB
● Dram 3.00GB
●●●●Hardware Info●●●●
● Storage eMMC
● BOOT1 4.00MB
● BOOT2 4.00MB
● RPMB 16.00MB
● USRDT 29.12GB
● CID 150100445836384D42008554905C68A9
● MFRID 0x15
● Vendor Samsung
● Card BGA BGA (Discrete embedded)
● OEMID 0x0
● Product DX68MB
● Revision 0.0
● Card SN 0x8554905c
● MFDate 6/2021
● EMCP KMDX60018M_B425
● Capacity 29.14GB
● RNID A4ABBDEFA576DCB1E28352C456F77FB2
Trying to Connect to usb high-speed.
Waiting for bootrom usb device... ok
BootMode : DAVcom[COM21]
● USBSpeed high-speed
● ManfcID SAMSUNG
● MName A12USQ
● Model SM-A125U
● Product SAMSUNG
● Fw Ver RP1A.200720.012.A125USQU3BVB1
● BuildID RP1A.200720.012
● Android 11 (Red Velvet Cake)
● EMI ID A12USQ
● S Patch 2022-01-01
● Region EN-US
● CPUApi ARM64-V8A
● SVer A125USQU3BVB1
● Host 21DJ6707
● BT Addr 00:00:46:00:00:01
Restoring Security ...Done
Network Unlock Successfully Done!
Rebooting device... Done
● Time elapsed ...05:min:11:sec
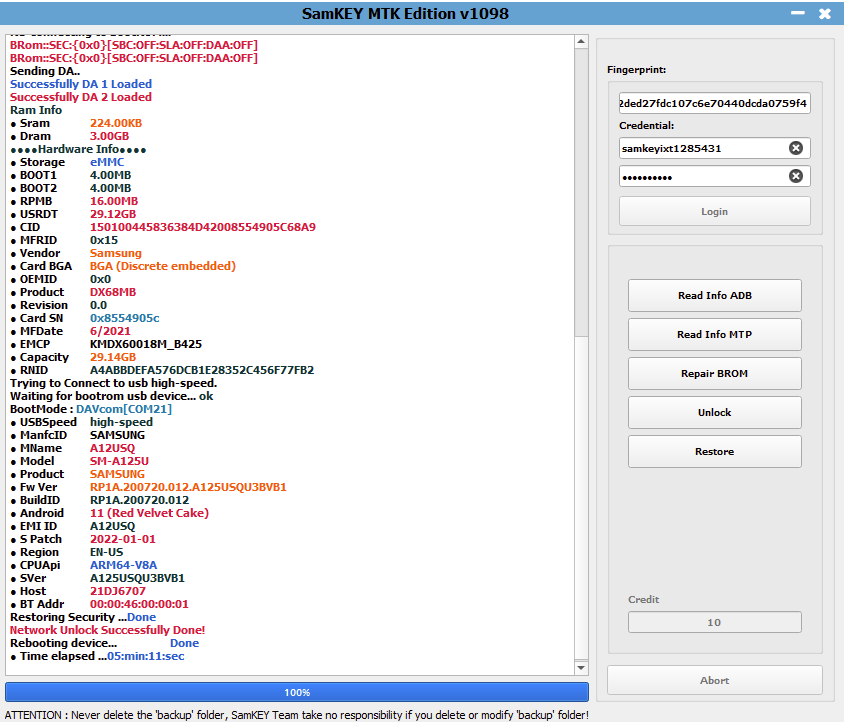
FRP Samsung Tablet SM-T580
- Shark Tool (V0.0.0.5)
- Operation : [Remove FRP]
- Detecting Samsung modem port : SAMSUNG Mobile USB Modem
- Selected ComPort : COM21
- Connecting : OK
- Reading info : OK
- Model: SM-T580
- Baseband: T580UEU4CSC1
- Software: T580UEU4CSC1
- Sales Code: XAR
- SN: R52KA02PXXP
- IMEI: NONE
- UN: CAJ033D4CEA67B4
- Software REV: BIT[4]
- Software Build Date: 2019-03-01
- Checking device lock : TRIGGERED
- Checking server data : OK
- This operation takes 5 credits. Continue? Confirmed
- Connecting to shark server : OK
- Work id : [594502]
- Requesting device data : OK
- Generating lock hash : OK
- Calculating phone data : OK
- Removing lock state : OK
- Verifying lock state : verified
- Rebooting : OK
- FRP-Account removed successfully
- Operation finished (00:07) 2023-09-22 01:04:54 PM
Remove Samsung Account Note 10 plus SM-N975U
Primer paso
Microsoft Windows [Versión 10.0.19045.3324]
(c) Microsoft Corporation. Todos los derechos reservados.
C:\Users\Celulares>cd \adb
C:\adb>adb shell
adb server version (39) doesn't match this client (41); killing...
* daemon started successfully
d2q:/ $ pm uninstall -k --user 0 com.osp.app.signin
Success
d2q:/ $ pm install-existing com.osp.app.signin
Package com.osp.app.signin installed for user: 0
d2q:/ $
Segundo Paso
[COM] REMOVE FRP [2023] Scanning for device... COM52
Reading Info... FAIL
Trying method [1]... OK
Waiting for device...
Model : SM-N975U
Manufacturer : samsung
Platform : msmnile
CPU Arch : arm64-v8a
Android Serial : RF8M838YD2F
Manufacturing Date : 2021.06.15
Security Patch : 2022-04-01
Connection : mtp,conn_gadget,adb
Timezone : America/Los_Angeles
Android Version : 12
Android SDK : 31
Build : SP1A.210812.016.N975USQS7HVCD
Build Date : Thu Mar 24 17:46:56 KST 2022
Product Code : SM-N975UZSATMB
Device Name : d2q
Product Name : d2qsq
Code Name : SM-N975UZSATMB
BL : N975USQS7HVCD
PDA : N975USQS7HVCD
CP : N975USQS7HVCD
CSC : N975UOYN7HVCD
Sales Code : TMB
Removing FRP... OK
UNLOCKTOOL 2023.09.14.0
Elapsed time : 21 seconds
FRP Samsung SM-A205U
Chimera Mobile Phone Utility version: 36.89.1322 @ 2023-09-13
Reset FRP lock started
Resetting FRP...
Model: SM-A205U
SW Version: A205USQSDBWC2/A205UOYNDBWC2/A205USQSDBWC2/A205USQSDBWC2
Serial: R58N141HRNJ
IMEI: 352741119001934
Product Code: TMK
Unique Number: CBJ00E6159479C6
Operation in progress. Be patient! Do NOT disconnect the phone!
Please 'Allow USB debugging' in the popup window
Waiting for ADB device...
Resetting FRP...
To complete resetting FRP, go to 'Settings/General management/Reset' then select 'Factory data reset'
Restarting phone
Successfully finished.
Finished at local time: [09.13.23 16:04:31]
WorkID: 234512950
FRP Samsung Tablet T580 by Z3X Box
Escribir firmware Combination para habilitar ADB
You must activate ADB before reset FRP Yes
Goto 'Terms and conditions' press 'NEXT' and 'AGREE' EULA Yes
Waiting ADB device... OK
Reading phone info...
Model: SM-T580
Android version: 6.0.1
PDA version: FA60_T580XXU4ARJ1
CSC version:
Phone version:
Product code:
CSC country code:
CSC sales code:
Phone SN: R52KA02PXXP
IMEI:
HW version:
RF cal date:
Chip name: EXYNOS7870
Modem board:
Security patch: 2016-05-01
Boot Warranty bit: 0
Bypass FRP... OK
For complete reset FRP, goto 'Backup and reset' and make 'Factory data reset'
Done with Samsung Tool PRO v.45.14 [SM-T580,Reset FRP]
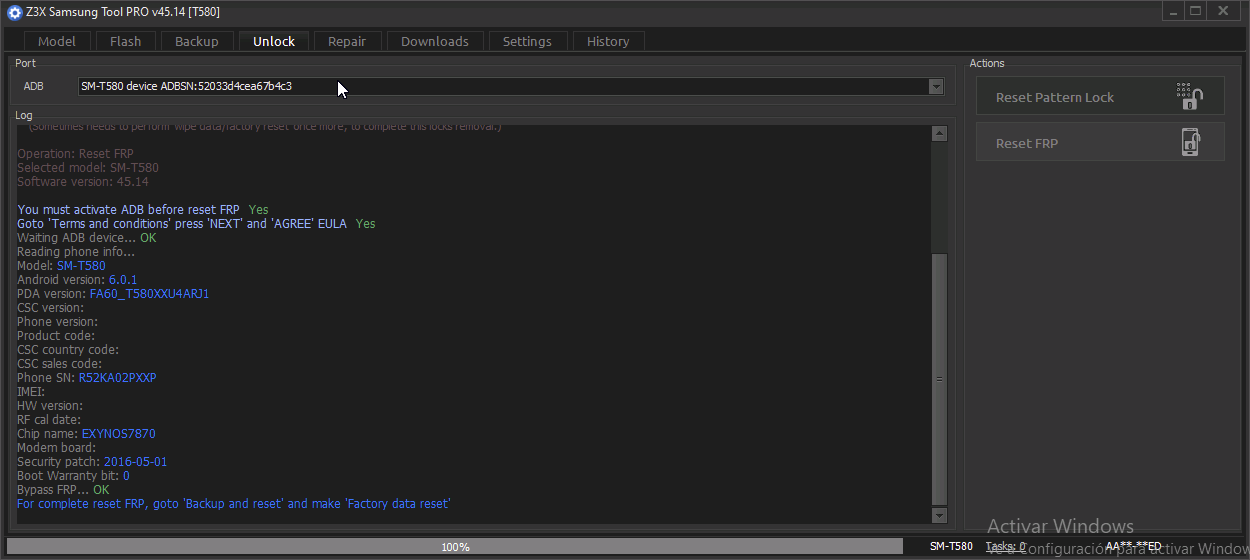
Samsung S23 ULTRA Cuenta Samsung Account Eliminar
Aqui les dejo como quitar la cuenta Samsung
primero marcar *#0*# conectar con Unlocktool buscar cualquier samsung y dale FRP seleccionar - All Methods despues de habilitar adb ya podras quitar la cuenta para siempre
5. Now, type pm uninstall -k --user 0 com.osp.app.signin ( Don't worry it won't completely uninstall the Samsung Accounts app )
6. You will see that the Samsung Accounts app is gone from your phone and the account gets logged out too.
7. Now type pm install-existing com.osp.app.signin ( This will reinstall the Samsung Accounts app and you can login with any other account you want )
FRP Motorola E40 XT2159-3 SPD Tiger T700 64 by Unlocktool
FRP Motorola E40 SPD
Apagado Presionar volumen -
Conectar cable USB
ERASE FRP
Selected Platform :
Tiger T700_64_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM23 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
Reading
device info
...
OK
[super]
Model Name :
cyprus64
Manufacturer :
motorola
Android Version :
11
Security Patch :
2023-07-05
Build ID :
ROQS31.166-87-9 release-keys
Build Date :
Thu Jul 13 23:07:42 CST 2023
Erasing
FRP
...
OK
UNLOCKTOOL
2023.09.03.2
Elapsed time :
33 seconds
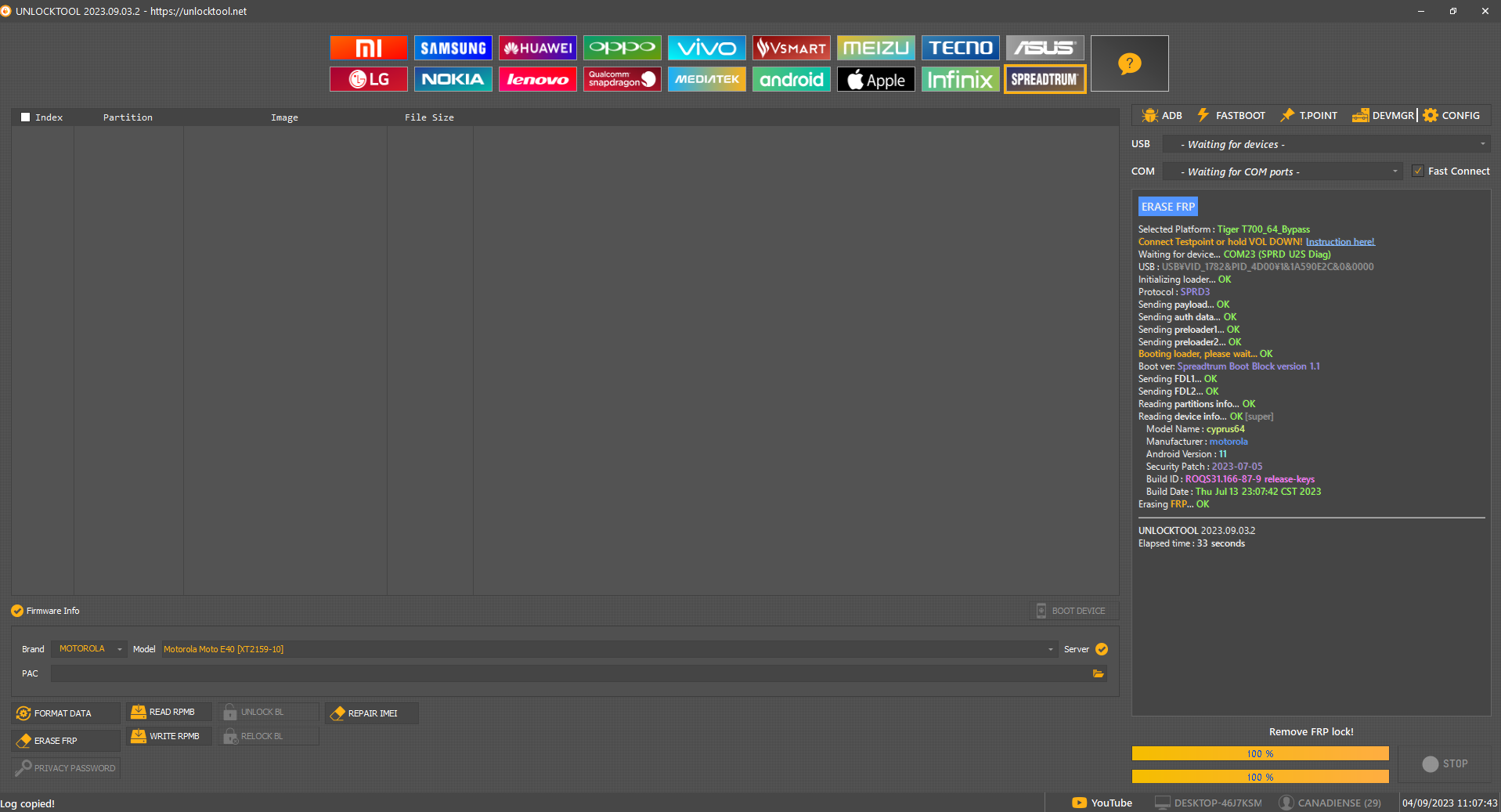
Direct Unlock Model: G PLAY - 2023 XT2271-3
Direct Unlock Model: G PLAY - 2023 XT2271-3
Waiting for Device in Factory Mode.....Found!
Reading Data...Done
FSG: DFLT_FSG
Firmware: S3SG32.39-90-1
Android Version: 12
Model: G PLAY - 2023
SKU: XT2271-3
SN: ZY22GRKMMD
IMEI 1: 358390900429310
Carrier: attpre
Checking Device Connection ... Done
Checking Price for Device....Done
Creating Order ID....Done
Operation ID: 1688665
Erasing UTAG IMEI ... Done
Reading Device Configuration ... Done
Wiping IMEI ... Done
Writing IMEI ... Done
New IMEI 1: 358390900429310
Writing New Security (0C03)... Done.
Writing UTAG IMEI ... Done
Erasing Factory Mode ... Done
Rebooting to Fastboot ... Done
Elapsed Time: 2:05.06
Direct Unlock Motorola G STYLUS 5G XT2131-4
Motorola G STYLUS 5G XT2131-4
Waiting for Device in Factory Mode.....Found!
Reading Data...Done
FSG: DENVER_NA_CUST
Firmware: S2RES32.29-16-1-15
Android Version: 12
Model: G STYLUS 5G
SKU: XT2131-4
SN: ZY22DWR3BR
IMEI 1: 357160653042383
Carrier: cricket
Checking Device Connection ... Done
Checking Price for Device....Done
Creating Order ID....Done
Operation ID: 1688496
Erasing UTAG IMEI ... Done
Reading Device Configuration ... Done
Wiping IMEI ... Done
Writing New Security (0C03)... Done.
Writing IMEI ... Done
New IMEI 1: 357160653042383
Writing New Security (0C03)... Done.
Writing UTAG IMEI ... Done
Erasing Factory Mode ... Done
Rebooting to Fastboot ... Done
Elapsed Time: 0:46.84
Direct Unlock Samsung SM-S134DL Tracfone Straight Talk
Direct Unlock Samsung SM-S134DL
Operation : Unlock Network
Load Devices List : OK
Connect ADB Device [R9WW408MQRJ] : DONE
Model : SM-S134DL
Brand : samsung
AP/CP Version : S134DLUDU6CWB6/S134DLUDU6CWB6
Android Version : 13
CSC : TFV/TFV/TFN
Hardware ID : MT6765
SIM State : LOADED
Security Patch : 2022-12-01
USB Config : mtp,adb
Warranty Void Bit : 0
IMEI : 358880860372195
Checking if Model Supported : ok
Operation : Direct Unlock
User Agreetments [6 Credit] : OK
Searching For SAMSUNG Mobile USB Modem : DONE
Checking Phone Security : PASS
Searching For SAMSUNG Mobile USB Modem : DONE
Reading Phone Data : OK
Sending Data to Server : OK
Unlocking : OK
Network Unlock Successful! :
PLEASE TYPE #TFUNLOCK# (#83865625#) AND ENTER 0000000000000000 FOR CODE1 AND CODE2
Elapsed Time : (01:57)
#- SIM-UNLOCKER (PRO) 8.1.3 [Build:2023.08.18]
Saving Log[Logs/Unlock Network SM-S134DL-R9WW408MQRJ (2023_8_28 15.40.39).log] : DONE
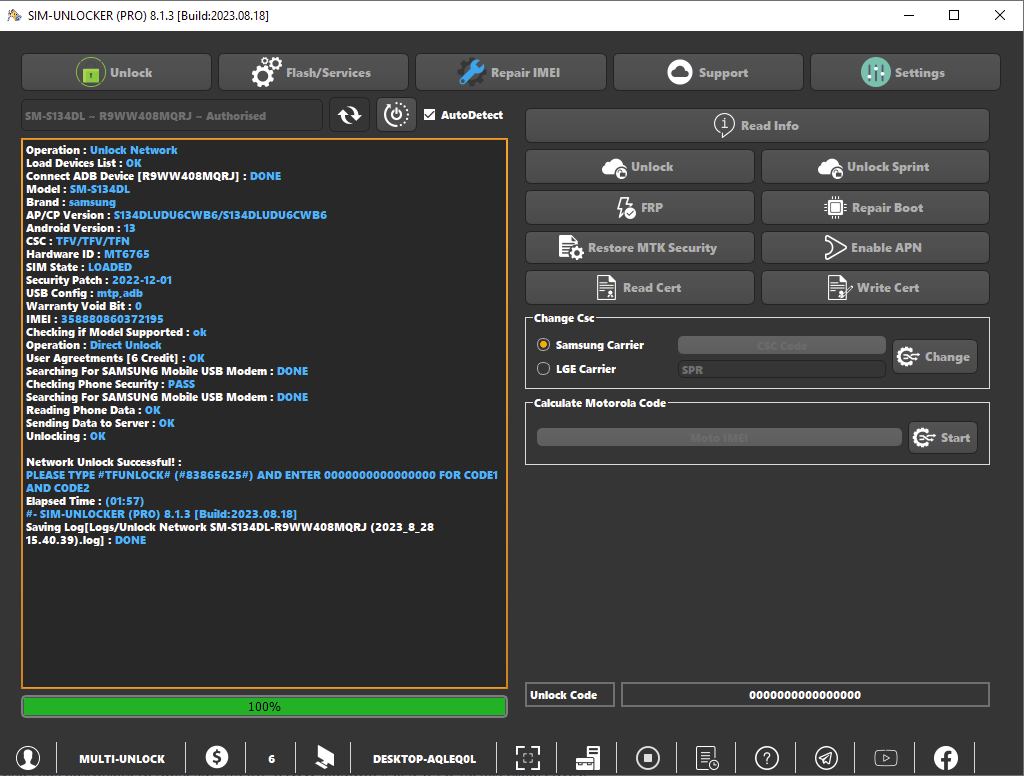
Direct Unlock Motorola G(7) SUPRA XT1955-5 by MWORKER Tool
Direct Unlock Motorola G(7) SUPRA XT1955-5
Waiting for Device in Factory Mode.....Found!
Reading Data...Done
FSG: DFLT_FSG
Firmware: PCOS29.114-134-5
Android Version: 9
Model: G(7) SUPRA
SKU: XT1955-5
SN: ZY326XGGMD
IMEI 1: 359526093630896
Carrier: cricket
Checking Device Connection ... Done
Checking Price for Device....Done
Creating Order ID....Done
Operation ID: 1682335
Erasing UTAG IMEI ... Done
Reading Device Configuration ... Done
Wiping IMEI ... Done
Writing IMEI ... Done
New IMEI 1: 359526093630896
Writing UTAG IMEI ... Done
Erasing Factory Mode ... Done
Rebooting to Fastboot ... Done
Elapsed Time: 0:20.29
Direct Unlock SM-A326U By SAMKEY SPR
Direct Unlock SM-A326U SPRINT USA
Loading ADB module..............OK
Starting ADB module...OK
Searching for SAMSUNG ADB device...OK
Checking device authorization...OK
Reading device information via ADB...
ADB Serial Number : RFCR40WK42R
Model Name : SM-A326U
Serial Number : RFCR40WK42R
Android Version : 12
Security Patch : 2022-04-01
Carrier : SPR
This operation takes 5 credits with NO REFUND, Continue? YES
AP Version : A326USQU7BVD1
CP Version : A326USQU7BVD1
Warranty VOID : 0
Algorithm : FEB 2023 SDK
Debug Level : 0x4f4c
Rebooting phone.......OK
Waiting for Reboot...OK
Waiting for phone to initialize...OK
Loading RIL applet...OK
Starting RIL applet...RETRY
Loading RIL applet...OK
Starting RIL applet...RETRY
Loading RIL applet...OK
Starting RIL applet...OK
Reading CP information...OK
IMEI : 356017291222259
SimLock status : NETWORK LOCKED
Sending data to SERVER...OK
Waiting for SERVER response...OK
Unlocking phone...OK
Clearing ADB buffer...OK
Verifying SimLock Status...UNLOCKED
Rebooting device...OK
Operation successful.
FRP Motorola G Pure XT2163-4 by Magic Tool
FRP Motorola G Pure XT2163-4
Start FRP Unlock Task on 8/19/2023 12:34:51 PM -06:00
Waiting for device arrival.... OK
Model SKU: XT2163-4
Carrier: RETUS
Serial: ZY22H8Q5T7
Authorizing FRP Access...OK
Reboot bootloader...OK
Waiting for device arrival.... OK
Erasing FRP...OK
Erasing UserData...OK
Erasing Cache...OK
Final Step...OK
Rebooting...OK
FRP Unlock Task Successful!
FRP Hisense E50 Lite by Chimera Tool
FRP Cuenta Google Hisense E50 Lite
Abrir Chimera Tool presionar volumen + - Apagado y conectar cable USB
Seleccionar -> CPU Spectrum UNISOC -> SC9863A 64Bit
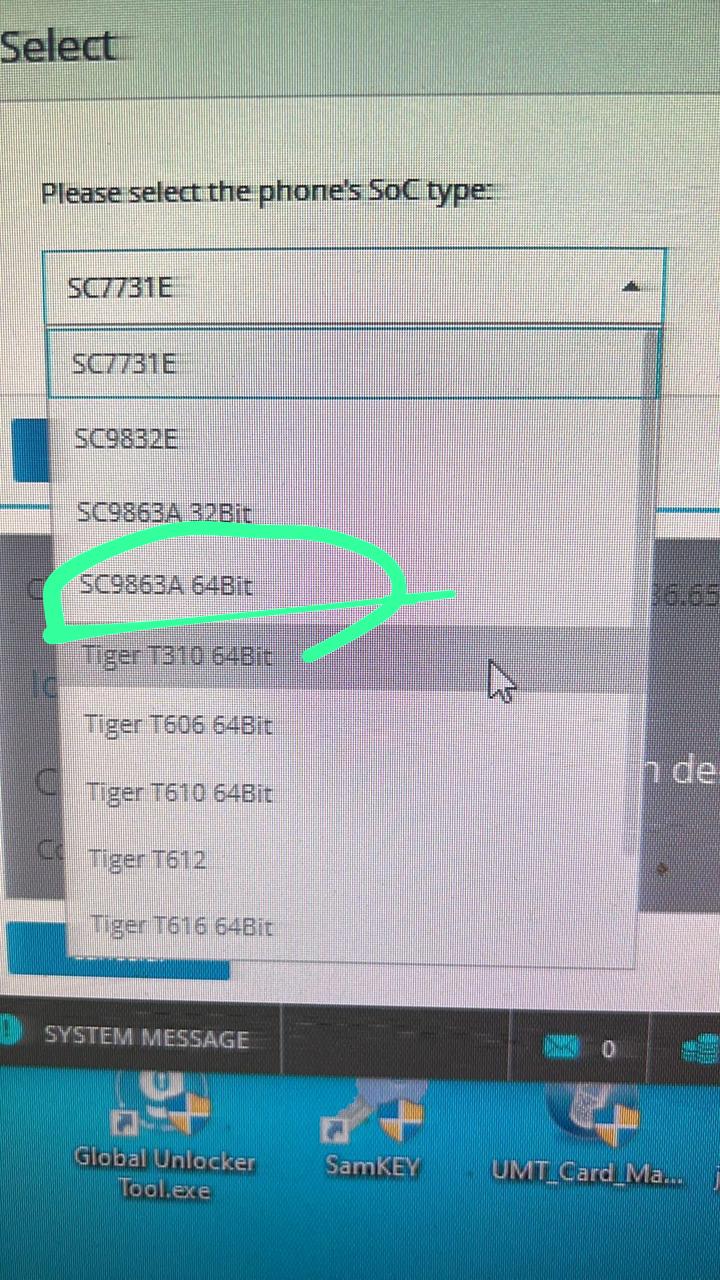
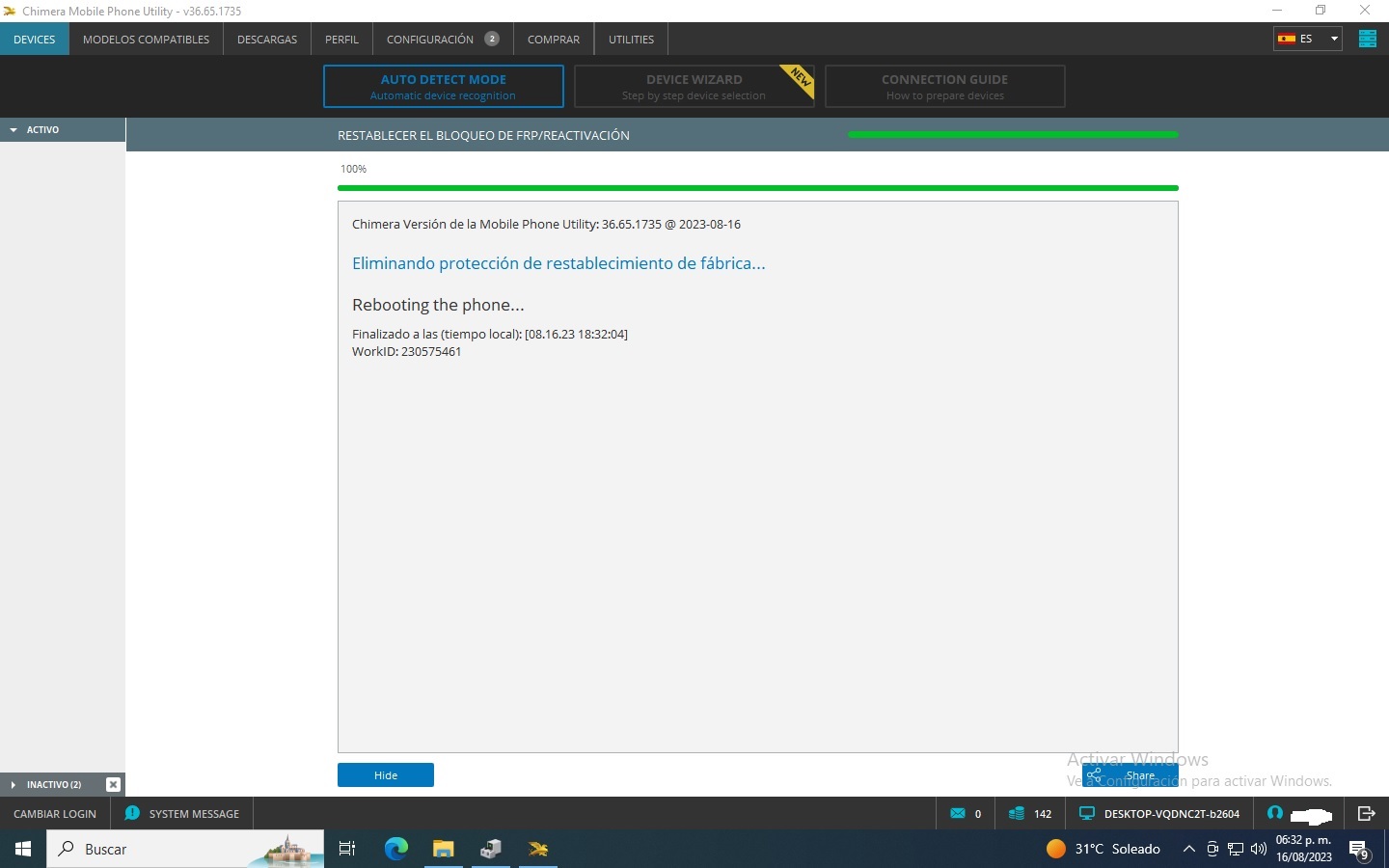
FRP ZTE V40 Smart
Select - > Tiger T606_64_Bypass
ERASE FRP Selected Platform : Tiger T606_64_Bypass
Connect Testpoint or hold VOL DOWN! Instruction here!
Waiting for device... COM7 (SPRD U2S Diag)
USB : USB\VID_1782&PID_4D00\5&390FD7C2&0&4
Initializing loader... OK
Protocol : SPRD3
Sending payload... OK
Sending auth data... OK
Sending preloader1... OK
Sending preloader2... OK
Booting loader, please wait... OK
Boot ver: Spreadtrum Boot Block version 1.1
Sending FDL1... OK
Sending FDL2... OK
Reading partitions info... OK
Reading device info... OK [super]
Model Name : ZTE A7040
Product Name : P606F01
Manufacturer : ZTE
Platform : ums9230_4h10
Android Version : 11
Security Patch : 2023-06-05
Build ID : MyOS11.0.8_A7040_TEL
Build Date : Fri Jun 16 19:38:47 CST 2023
Erasing FRP... OK
UNLOCKTOOL 2023.07.30.0
Elapsed time : 52 seconds
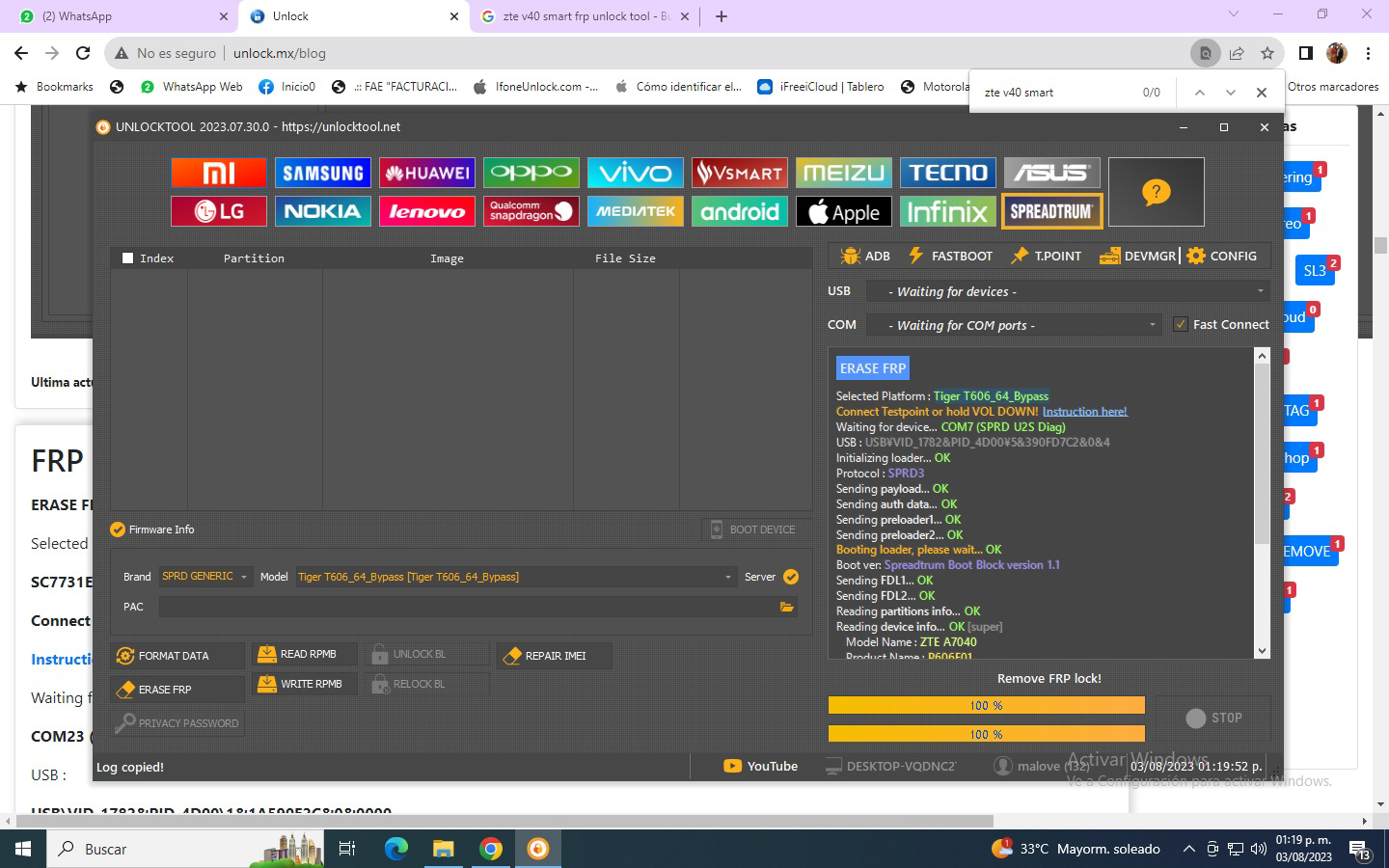
Unlock TCL T430W by Furious Gold Done
Using library Brom_DLL_v7.2116.0
Engine version 1.0.0.6279
Searching phone in normal mode;
[connect the phone powered off to the usb cable]
Phone detected (MediaTek PreLoader USB VCOM (Android) (COM26)) (Driver version: 3.2.0.0)
Preparing to start flash mode;
Preparing to open COM26
Connecting;
Downloading DA;
Initializing;
Checking server support license;
Done;
Rid: 8f3a26f36565536c360fb47c647b1c4c
Requesting baudrate change;
Done;
USB SPEED: USB_HIGH_SPEED
DEVICE INFO:
BB CHIP: MT6765 [CA00, 00, 6765, 00]
BB ID: REZDQ0JBQkMxQjUzQTFDMDJBRTdGQUMxNTg2ODI5OUI=
HW_STORAGE_EMMC: 0x44000115 0x4D383658 0x3B280942 0xBD6954D0 [SIZE=0x748800000]
IMEI1 [OTP 0001]: 016298-00-143442-4
IMEI2 [OTP 0001]: 000000-00-000000-0
PROVIDER: T430W-2ATBUS11
USRDATA INFO: 0x249000000 SIZE: 0x4FB0F8000
SPECIAL NOTE: If you are using windows 10 x64 be sure that the installed mtk driver version is 3.0.1504.0 . Any different drivers will create random read bugs on newer chipset phones.
As usual the correct drivers come inside OTSMart archive inside the "usb_driver" folder
Searching data;
Phone unlocked; Remove battery and cable;
Time needed - 00:00:00
Log file saved to: LOG_2_08_2023_10_24_38.txt
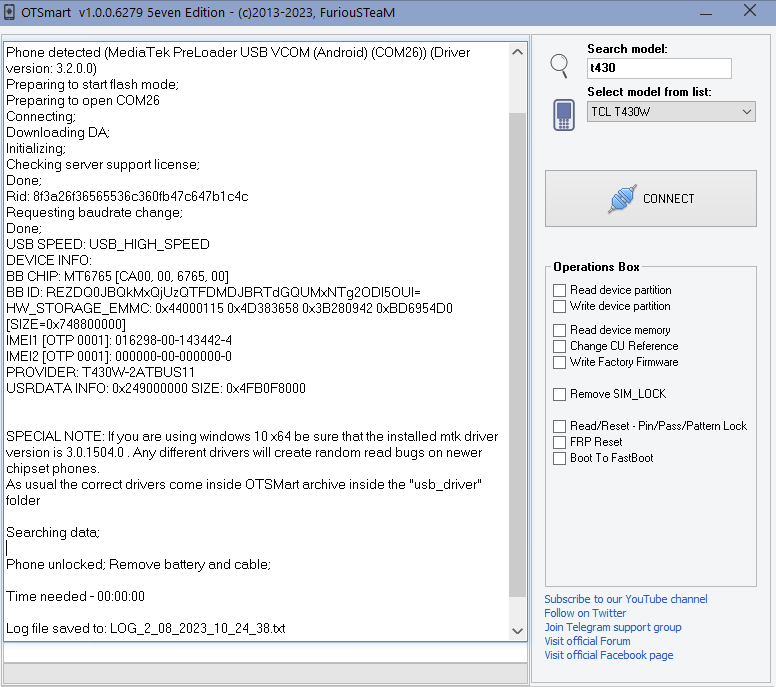
FRP Realme C21-Y RMX3263 by Unlocktool
FRP Realme C21-Y RMX3263 by Unlocktool
ERASE FRP Selected Platform : Tiger T610_64_Bypass
Connect Testpoint or hold VOL DOWN! Instruction here!
Waiting for device... COM23 (SPRD U2S Diag)
USB : USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader... OK
Unlock.mx....Done
Protocol : SPRD3
Sending payload... OK
Sending auth data... OK
Sending preloader1... OK
Sending preloader2... OK
Booting loader, please wait... OK
Boot ver: Spreadtrum Boot Block version 1.1
Sending FDL1... OK
Sending FDL2... OK
Reading partitions info... OK
Reading device info... OK [super]
Model Name : RMX3261
Manufacturer : realme
Android Version : 11
Security Patch : 2022-03-05
Build ID : RMX3261_11_A.81
Build Date : Sun Apr 3 11:44:02 CST 2022
OTA Version : RMX3261_11_A.81_20220403103755
Erasing FRP... OK
UNLOCKTOOL 2023.07.22.0
Elapsed time : 28 seconds
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:002518 SourceURL:file%3a%2f%2f
FORMAT DATA
Selected Platform :
Tiger T610_64_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM23 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader...
OK
Unlock.mx....OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
Reading
device info
...
OK
[super]
Model Name :
RMX3261
Manufacturer :
realme
Android Version :
11
Security Patch :
2022-03-05
Build ID :
RMX3261_11_A.81
Build Date :
Sun Apr 3 11:44:02 CST 2022
OTA Version :
RMX3261_11_A.81_20220403103755
Erasing
FRP
...
OK
Erasing
USERDATA
...
OK
UNLOCKTOOL
2023.07.22.0
Elapsed time :
27 seconds
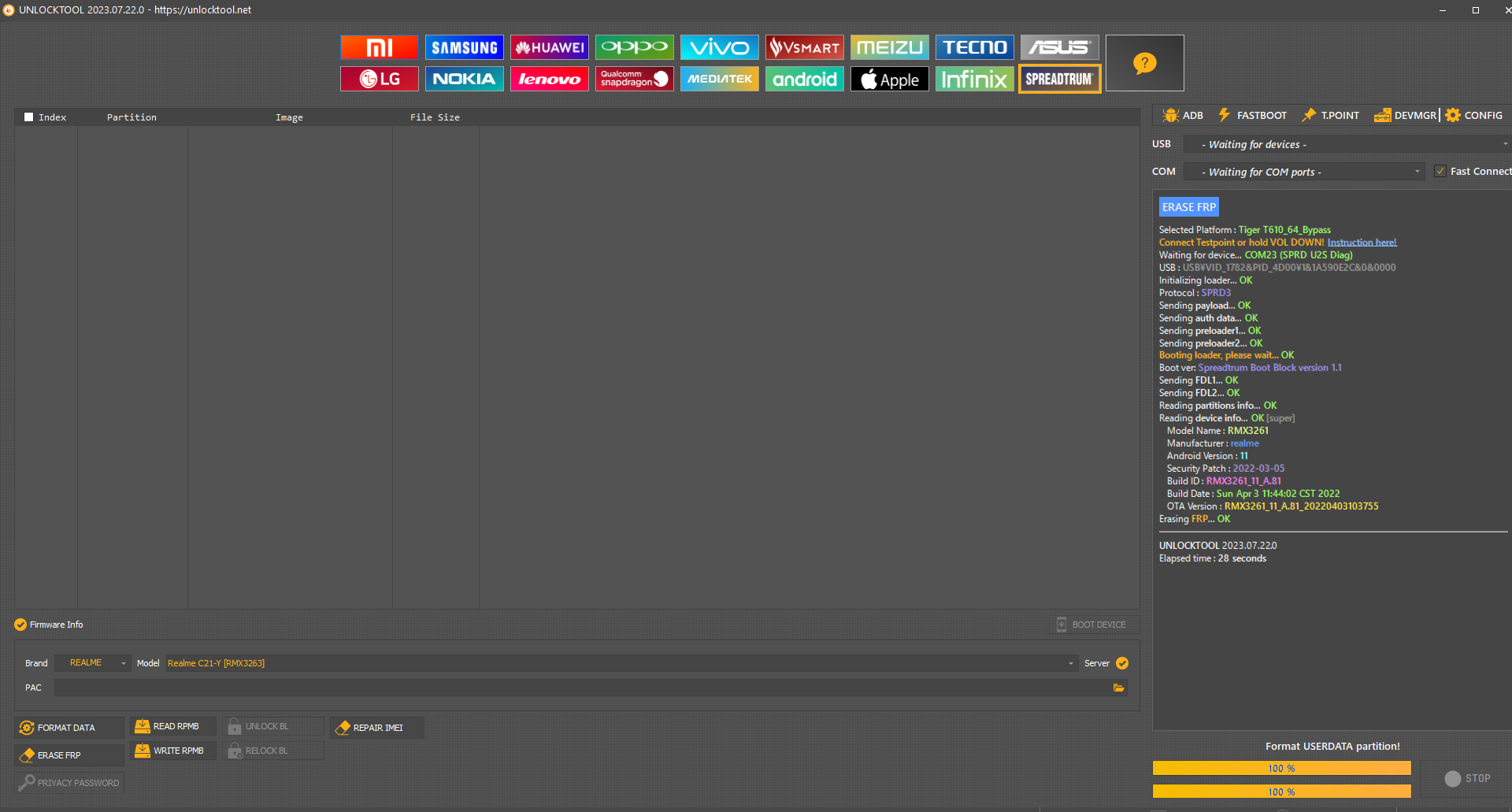
Unlock & Root Samsung J700p 7.1.1 Sprint
Unlock and Root
Unlock Service
- Connecting ... [ 3b0de722 ]
- Model: SM-J700P
- Serial Number: 00000000000
- Android Version: 7.1.1
- BL: J700PVPU2BQJ2
- CP: J700PVPU2BQJ2
- Board: MSM8929
- Hardware: qcom
- Knox: 1
- SELinux: Enforcing
- SIM: Samsung
- SIM Status: LOADED
- USB Config: mtp,adb
- Service Provider: BST/USA/BST
- This Operation Will Take 1 Credits
- Check Root : OK
- IMEI : 35562807409149
- Prepare Device : OK
- Check Data : OK
- Read Data : OK
- Unlock : OK
# Elapsed Time [00:15]
# Operation ID 2044547
ROOT Samsung J700P 7.1.1 ... Done
https://download.chainfire.eu/1152/CF-Root/CF-Auto-Root/CF-Auto-Root-j7ltespr-j7ltespr-smj700p.zip
<ID:0/036> Added!!
<OSM> Enter CS for MD5..
<OSM> Check MD5.. Do not unplug the cable..
<OSM> Please wait..
<OSM> CF-Auto-Root-j7ltespr-j7ltespr-smj700p.tar.md5 is valid.
<OSM> Checking MD5 finished Sucessfully..
<OSM> Leave CS..
<ID:0/036> Removed!!
<ID:0/011> Added!!
<ID:0/011> Odin engine v(ID:3.1005)..
<ID:0/011> File analysis..
<ID:0/011> SetupConnection..
<ID:0/011> Initialzation..
<ID:0/011> Get PIT for mapping..
<ID:0/011> Firmware update start..
<ID:0/011> SingleDownload.
<ID:0/011> recovery.img
<ID:0/011> NAND Write Start!!
<ID:0/011> cache.img.ext4
<ID:0/011> RQT_CLOSE !!
<ID:0/011> RES OK !!
<ID:0/011> Removed!!
Direct Unlock Octoplus Samsung SM-A037U A03s Carrier DSH con logo Bost Mobile
Full Señal TELCEL & LTE 4G
Primero hacer este paso
Change CSC a VERIZON
Work ID: 0000000002197594
Starting Change CSC
Selected model: SM-A037U
www.Unlock.MX.....Done
Turn on USB debugging on the phone.
Connect powered-on phone to PC using USB via ADB.
Searching ADB devices...
Press "OK" button on the device to allow USB debugging
OK
Reading info...
Detected model: SM-A037U
Fingerprint: samsung/a03susq/a03su:11/RP1A.200720.012/A037USQS2AVD3:user/release-keys
Firmware compiled date: Thu Apr 21 15:47:43 KST 2022
PDA version: A037USQS2AVD3
CSC version: A037UOYN2AVD3
SW version: A037USQS2AVD3
Build number: A03S_USA_SINGLE
Phone SN: R9WT70WMVAE
Android version: 11 (RP1A.200720.012)
Sales code: XAA
Carrier Id: DSH
Country: USA
HW platform: mt6765
HW Chip: mt6765
HW Modem: REV1.0
Security patch level: 2022-05-01
Warranty Void: 0
Codename: a03susq
SIM 1 status: ABSENT
SIM 2 status: ABSENT
Modem board: MT6765
Searching modem port...
OK
New CSC: VZW
Changing CSC...
Change CSC done
Execution time 1 minute(s) 17 second(s)
Performed by 4.2.4 Software version.
Work ID: 00000000021975D3
Starting Read Info (ADB)
Selected model: SM-A037U
Turn on USB debugging on the phone.
Connect powered-on phone to PC using USB via ADB.
Searching ADB devices...
Press "OK" button on the device to allow USB debugging
OK
Reading info...
Detected model: SM-A037U
Fingerprint: samsung/a03susq/a03su:11/RP1A.200720.012/A037USQS2AVD3:user/release-keys
Firmware compiled date: Thu Apr 21 15:47:43 KST 2022
PDA version: A037USQS2AVD3
CSC version: A037UOYN2AVD3
SW version: A037USQS2AVD3
Build number: A03S_USA_SINGLE
Phone SN: R9WT70WMVAE
Android version: 11 (RP1A.200720.012)
Sales code: VZW
Carrier Id: DSH
Country: USA
HW platform: mt6765
HW Chip: mt6765
HW Modem: REV1.0
Security patch level: 2022-05-01
Warranty Void: 0
Codename: a03susq
SIM 1 status: NETWORK_LOCKED
SIM 2 status: NETWORK_LOCKED
Modem board: MT6765
Read Info (ADB) done
Execution time 4 second(s)
Performed by 4.2.4 Software version.
Aqui viene el segundo paso
Presionar Unlock
Seleccionar Unlock (Jul.2022)
Work ID: 00000000019E5ECC
Starting Unlock (Jul.2022)
Selected model: SM-A037U
www.Unlock.MX.....Done
Turn on USB debugging on the phone.
For work with MTK devices install "MTK USB Driver"(How to install).
Connect powered-on phone to PC using USB via ADB.
Searching ADB devices...
Press "OK" button on the device to allow USB debugging
OK
Reading info...
Detected model: SM-A037U
Fingerprint: samsung/a03susq/a03su:11/RP1A.200720.012/A037USQS2AVD3:user/release-keys
Firmware compiled date: Thu Apr 21 15:47:43 KST 2022
PDA version: A037USQS2AVD3
CSC version: A037UOYN2AVD3
SW version: A037USQS2AVD3
Build number: A03S_USA_SINGLE
Phone SN: R9WT70WMVAE
Android version: 11 (RP1A.200720.012)
Sales code: VZW
Carrier Id: DSH
Country: USA
HW platform: mt6765
HW Chip: mt6765
HW Modem: REV1.0
Security patch level: 2022-05-01
Warranty Void: 0
Codename: a03susq
SIM 1 status: NETWORK_LOCKED
SIM 2 status: NETWORK_LOCKED
Modem board: MT6765
You will need to enter zero code ("0000000000000000") after every reboot
Searching modem port...
OK
Connecting to server...
Username: octopus038
Your balance: 150 credits
Sending device information..
OK
Your account will be charged for 60 credits. Do you want to continue?
Preparing to unlock...
Start unlocking operation.
Rebooting device...
OK
HW Chip : MT6765
HW Version : 8a00.ca00.0.0
Reconnecting...
OK
Reading preloader...
OK
Mobile Status: brom
Sending bootloader info...
Initializing memory flash...
Initializing successfully completed
Detected EMMC flash
Bypassing security...
Unlocking. Please wait...
You will need to enter zero code ("0000000000000000") after every reboot
OK
Unlock (Jul.2022) done
Execution time 1 minute(s) 38 second(s)
Performed by 4.2.4 Software version.
Unlock Motorola Moto G 5G XT2213-1 Cricket USA
Starting Factory Enabler process...
Unlock.mx....Done
Waiting for device in Fastboot Mode....Done.
Reading Data....Done
Firmware: S1SAS32.47-59-19
Android: 12
CPU: MT6833V/NZA
Model: XT2213-1
SN: ZD2228LNCN
IMEI: 351279771141293
Channel ID: 0x89
Carrier: cricket
Factory Mode: disabled
Reading Data ... Done
Creating Order ID....Done
Operation ID: 1631077
Sending Data to Server ... Done
Setting Factory Mode ... Done
Rebooting Phone ... Done
Elapsed Time: 0:13.91
Waiting for Device in Factory Mode.....Found!
Unlock.mx....Done
Reading Data...Done
FSG: DFLT_FSG
Firmware: S1SAS32.47-59-19
Android Version: 12
Model: G 5G (2022)
SKU: XT2213-1
SN: ZD2228LNCN
IMEI 1: 351279771141293
Carrier: cricket
Checking Price for Device....Done
Creating Order ID....Done
Operation ID: 1631080
Erasing UTAG IMEI ... Done
Reading Device Configuration ... Done
Wiping IMEI ... Done
Writing New Security ... Done.
Writing IMEI ... Done
New IMEI 1: 351279771141293
Writing New Security ... Done.
Writing UTAG IMEI ... Done
Erasing Factory Mode ... Done
Rebooting to Fastboot ... Done
Elapsed Time: 0:39.52
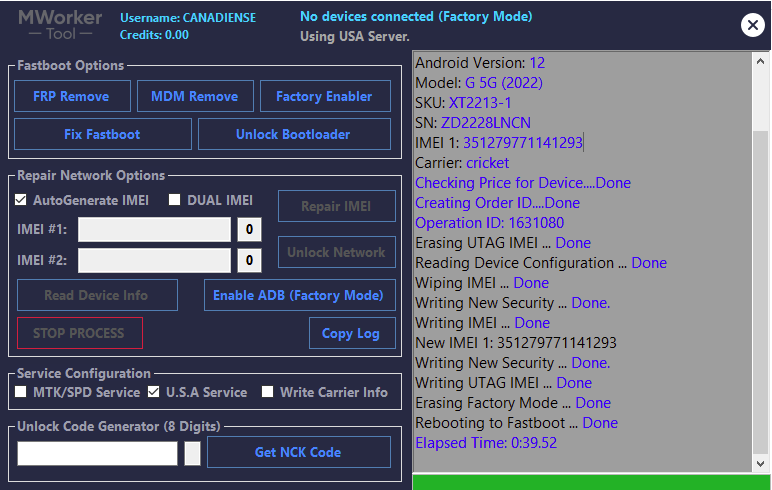
FRP Motorola Moto G GO G Pure XT2163-7
Starting Factory Enabler process...
Unlock.mx.....Done
Waiting for device in Fastboot Mode....Done.
Reading Data....Done
Firmware: RRHGS31.Q3-37-43-43-5-4-6
Android: 11
CPU: MT6762G
Model: XT2163-6
SN: ZY22G4HZ8B
IMEI: 357151881507388
Channel ID: 0x88
Carrier: attpre
Factory Mode: disabled
Reading Data ... Done
Creating Order ID....Done
Operation ID: 1630251
Sending Data to Server ... Done
Setting Factory Mode ... Done
Rebooting Phone ... Done
Elapsed Time: 6:47.07
Unlock.mx.....Done
FSG: MT6762_TC2.PR2.SP.V8.2.P89.01.66.119R
Firmware: RRHGS31.Q3-37-43-43-5-4-6
Model: G GO
SKU: XT2163-7
SN: ZY22G4HZ8B
IMEI 1: 357151881507388
Carrier: attpre
Checking Price for Device....Done
Wiping IMEI ... Done
Writing IMEI ... Done
New IMEI 1: 357151881507388
Writing New Security ... Done.
Elapsed Time: 0:38.79
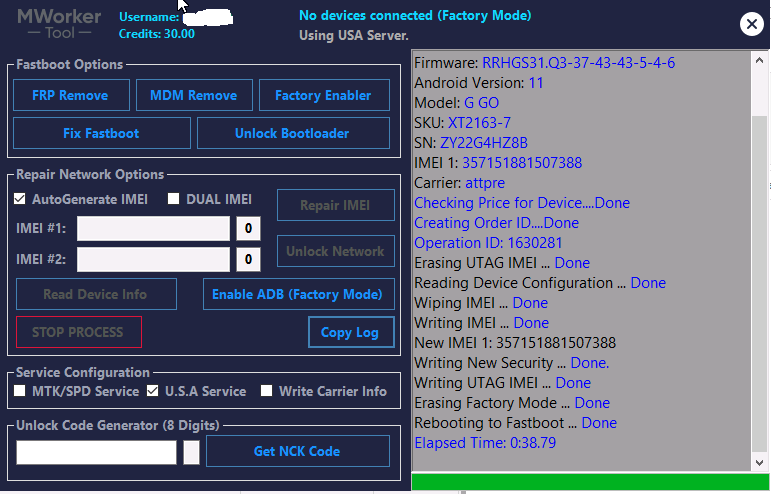
FRP Samsung A32 SM-A325M by UnlockTool
[COM] REMOVE FRP [2023]
Scanning for device...
COM32
Reading Info...
FAIL
Trying method [1]...
OK
Waiting for device...
Please accept USB Debugging on your phone!
Model :
SM-A325M
Manufacturer :
samsung
Platform :
mt6768
CPU Arch :
arm64-v8a
Android Serial :
R58RB1VK5BK
Manufacturing Date :
20211109
Security Patch :
2021-09-01
Connection :
mtp,adb
Timezone :
GMT
Android Version :
11
Android SDK :
30
Build :
RP1A.200720.012.A325MUBU1AUH1
Build Date :
Sat Sep 4 05:01:13 KST 2021
Product Code :
SM-A325MZKMMXO
Device Name :
a32
Product Name :
a32ub
Code Name :
SM-A325MZKMMXO
BL :
A325MUBU1AUH1
PDA :
A325MUBU1AUH1
CP :
A325MUBU1AUH1
CSC :
A325MOWO1AUH1
Sales Code :
MXO
Removing
FRP
...
OK
UNLOCKTOOL
2023.07.12.0
Elapsed time :
42 seconds
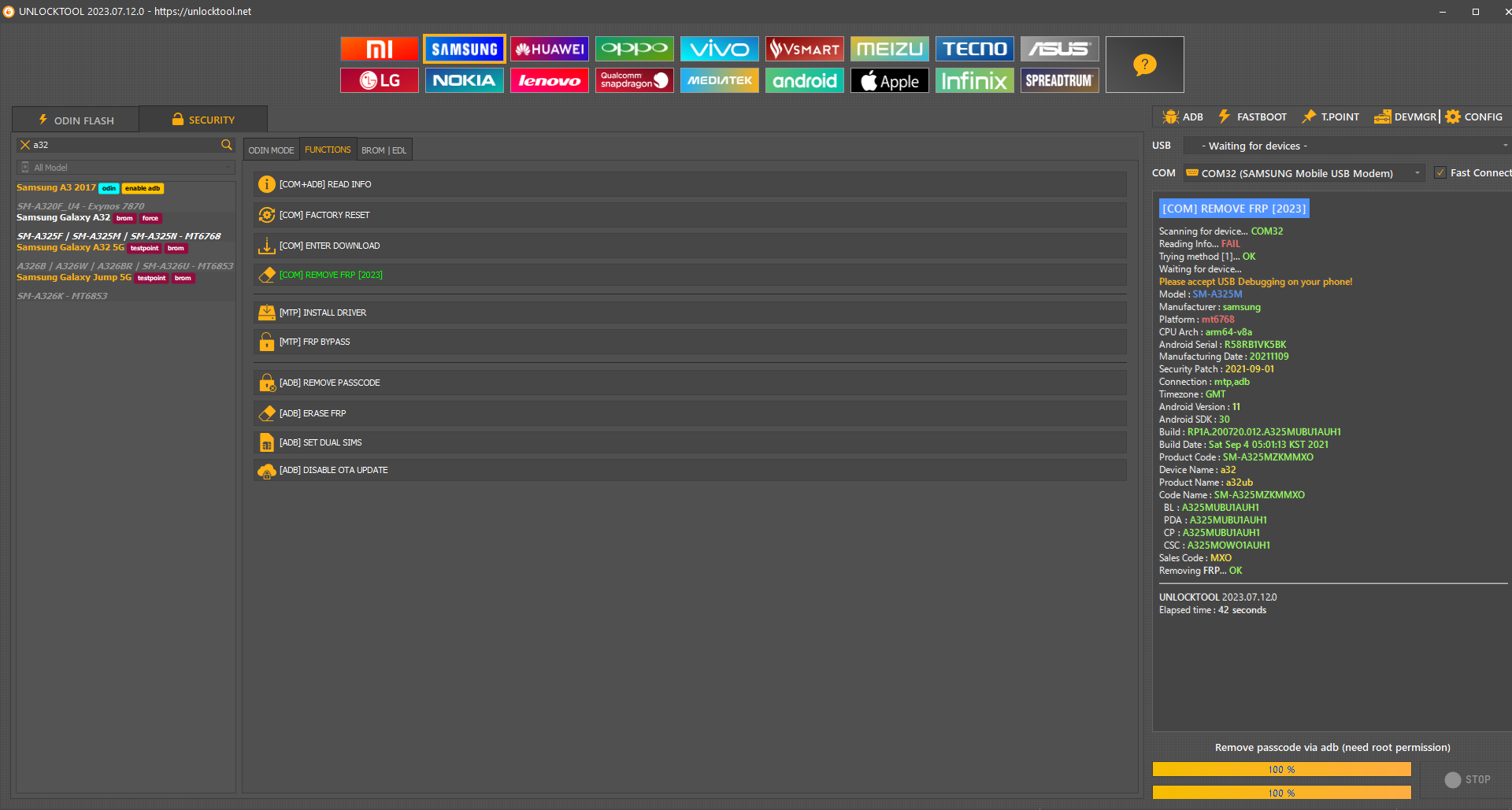
FRP Samsung A23 SM-A235M by UnlockTool
[COM] REMOVE FRP [2023]
Unlock.mx...Done
Scanning for device...
COM31
Reading Info...
FAIL
Trying method [1]...
OK
Waiting for device...
Please accept USB Debugging on your phone!
Model :
SM-A235M
Manufacturer :
samsung
Platform :
bengal
CPU Arch :
arm64-v8a
Android Serial :
R58T30AWG2L
Manufacturing Date :
2022.03.03
Security Patch :
2022-03-01
Connection :
mtp,adb
Timezone :
GMT
Android Version :
12
Android SDK :
31
Build :
SP1A.210812.016.A235MUBU1AVB8
Build Date :
Wed Feb 23 14:41:14 KST 2022
Product Code :
SM-A235MZKDTPA
Device Name :
a23
Product Name :
a23ub
Code Name :
SM-A235MZKDTPA
BL :
A235MUBU1AVB8
PDA :
A235MUBU1AVB8
CP :
A235MUBU1AVB8,A235MUBU1AVB8
CSC :
A235MOWO1AVB9
Sales Code :
TPA
Removing
FRP
...
OK
UNLOCKTOOL
2023.07.12.0
Elapsed time :
57 seconds
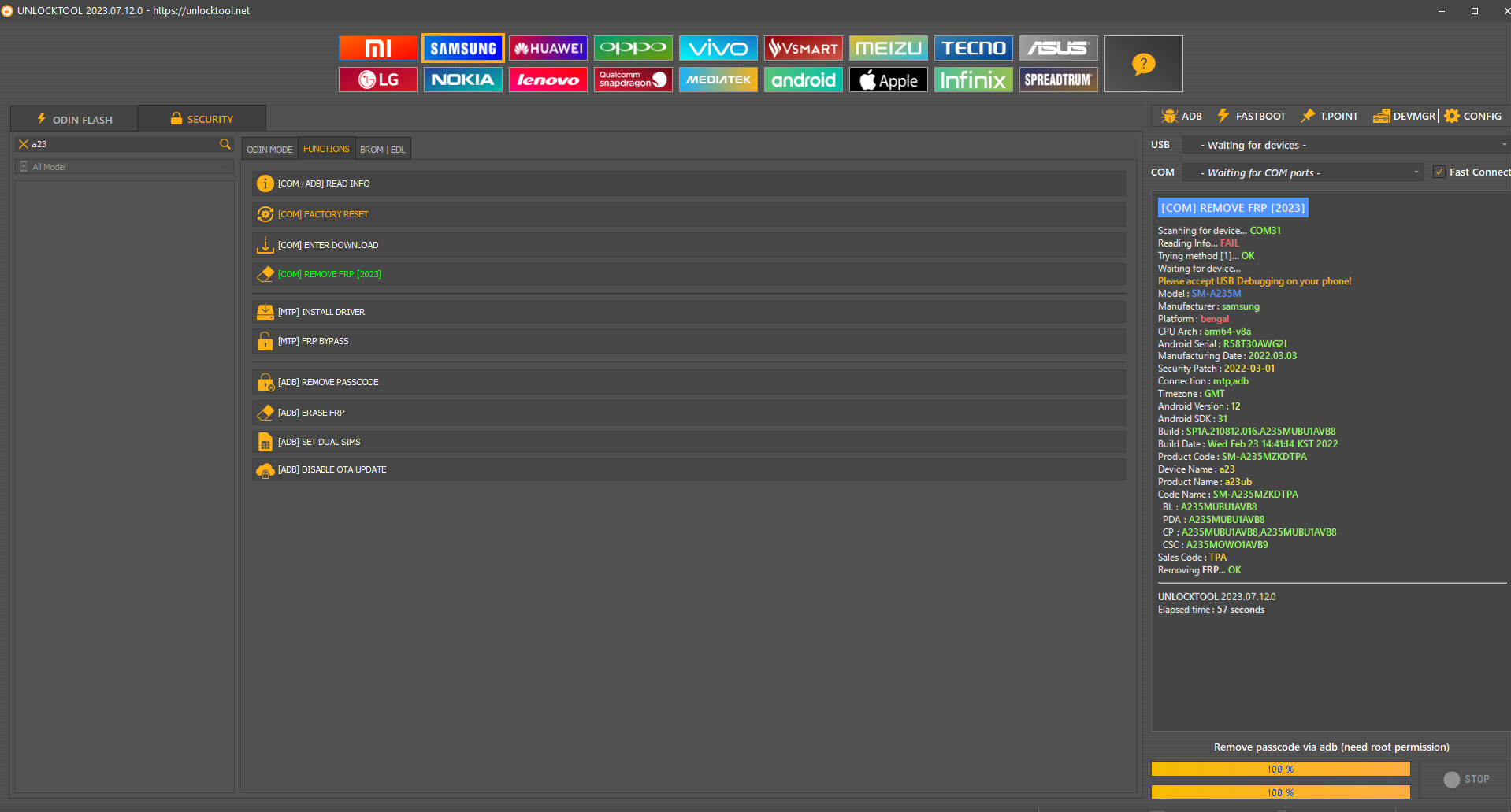
FRP ZTE L210 SC7731E
ERASE FRP
Selected Platform :
SC7731E_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM23 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
Reading
device info
...
OK
[super]
Model Name :
ZTE Blade L210
Product Name :
P731F50
Manufacturer :
ZTE
Platform :
sp7731e_1h10
Android Version :
10
Security Patch :
2022-04-05
Build ID :
TEL_MX_ZTE_Blade_L210V2.2
Build Date :
Fri Apr 15 12:15:46 CST 2022
Erasing
FRP
...
OK
UNLOCKTOOL
2023.07.12.0
Elapsed time :
42 seconds
FORMAT DATA
Selected Platform :
SC7731E_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM23 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
Reading
device info
...
OK
[super]
Model Name :
ZTE Blade L210
Product Name :
P731F50
Manufacturer :
ZTE
Platform :
sp7731e_1h10
Android Version :
10
Security Patch :
2022-04-05
Build ID :
TEL_MX_ZTE_Blade_L210V2.2
Build Date :
Fri Apr 15 12:15:46 CST 2022
Erasing
FRP
...
OK
Erasing
USERDATA
...
OK
UNLOCKTOOL
2023.07.12.0
Elapsed time :
37 seconds
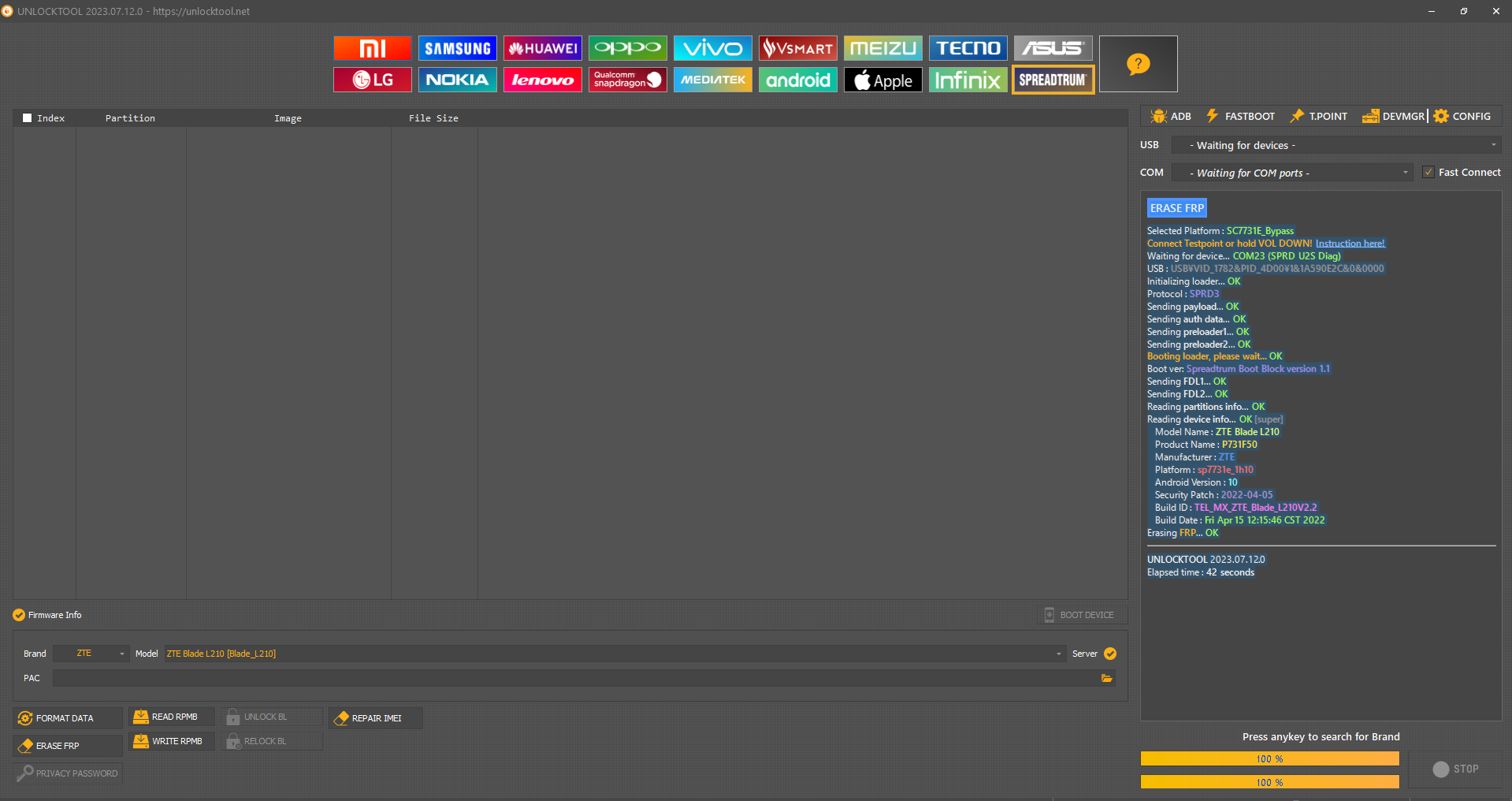
FRP Motorola moto g power (2022) XT2165-5
Starting FRP Remove process...
Waiting for device in Fastboot Mode....Done.
Reading Data....Done
Unlock.mx....Done
Firmware: S3RQS32.20-42-10-14-3
Android: 12
CPU: MT6765H
Model: XT2165-5
SN: ZY22GHDC54
IMEI: 351024744081170
Channel ID: 0x80
CID: 0x0032
Carrier: retca
Reading Data ... Done
Creating Order ID....Done
Operation ID: 1627867
Setting Device Config ... Done
Unlocking Bootloader...Done
Verify Factory CID ... Done.
Reboot Bootloader ... Done.
Wait for Bootloader Reboot ... Done
Wait for Fastboot Mode ... Done
Erase FRP ... Done.
Wait for FRP Clear ... Done
Configuring Bootloader...Done
Erase User Data ... Done.
Erase MetaData ... Done.
Erase misc ... Error.
Clear Mode ... Done.
Fastboot Reboot ... Done.
Elapsed Time: 0:44.15
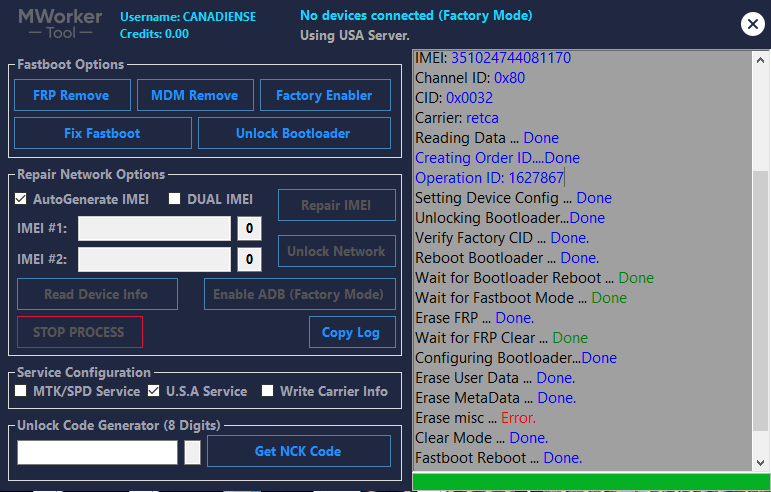
Motorola Moto G 5G (2022) XT2213-1 Direct Unlock
Motorola Moto G 5G (2022) XT2213-1 Direct Unlock
Waiting for Device in Factory Mode.....Found!
Unlock.mx......Done
Reading Data...Done
FSG: DFLT_FSG
Firmware: S1SAS32.47-59-13
Android Version: 12
Model: G 5G (2022)
SKU: XT2213-1
SN: ZD2228LCYY
IMEI 1: 351279771054843
Carrier: cricket
Checking Price for Device....Done
Creating Order ID....Done
Operation ID: 1625851
Erasing UTAG IMEI ... Done
Reading Device Configuration ... Done
Wiping IMEI ... Done
Writing New Security ... Done.
Writing IMEI ... Done
New IMEI 1: 351279771054843
Writing New Security ... Done.
Writing UTAG IMEI ... Done
Erasing Factory Mode ... Done
Rebooting to Fastboot ... Done
Elapsed Time: 0:50.55
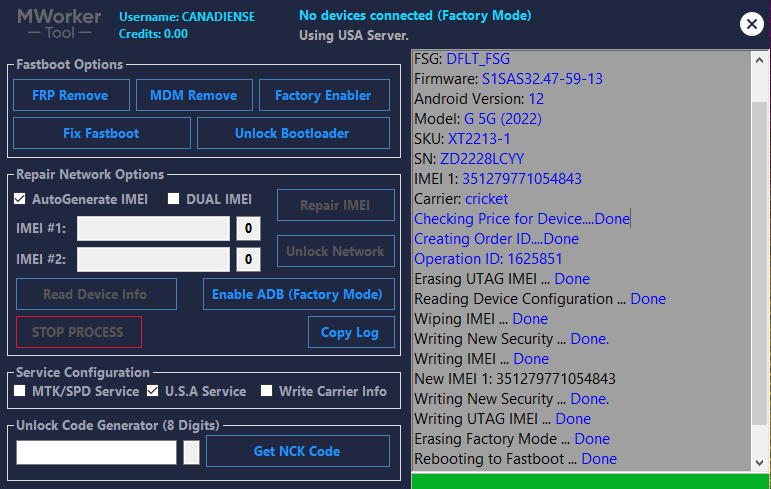
FRP Motorola Moto C MT6737M by NCK BOX
Exe version: NCKBox AndroidMTK 2.9.7
Selected model: Motorola Moto C
[auto]Action: Reset FRP
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(161) : MediaTek PreLoader USB VCOM (Android) (COM161)
[161] \\?\usb#vid_0e8d&pid_2000#6&1bf12d6f&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Preloader
BBCHIP: 335 0 ca00
Using Algo 2.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6737M
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 1 GB DRAM
----------------------------------------------------
EMMC: (58Gb+8192Mb) SAMSUNG 0x464e36324d42
EMMC FW VERSION: 03:00:00:00:00:00:00:00
EMMC CID: 150100464E36324D42 : 00000000000000
EMMC UA SIZE: 0x1d2000000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x1d2880000 [7.290 GB]
Checking data, wait...
Writing FRP, wait...
FRP Reset Done.
Wait untill phone will start charging.
[0]All done.
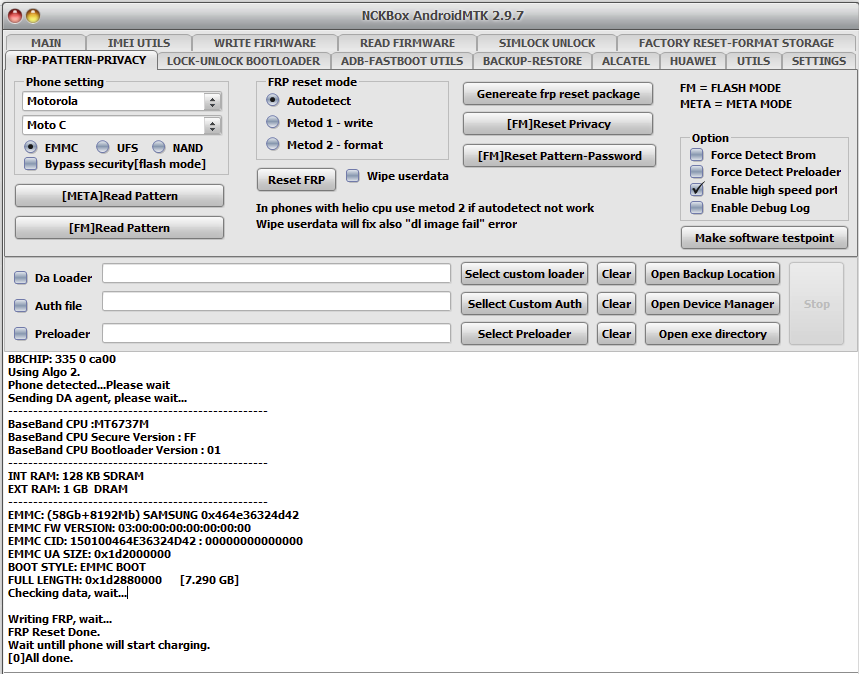
FRP Samsung A02 SM-A022M by UnlockTool
[COM] REMOVE FRP [2023]
Method :
[1]
Scanning for device...
COM22
Enabling
ADB
...
OK
Waiting for device...
Model :
SM-A022M
Manufacturer :
samsung
Platform :
mt6739
CPU Arch :
armeabi-v7a
Android Serial :
R58RA3YVH9K
Manufacturing Date :
20211028
Security Patch :
2021-09-01
Connection :
mtp,adb
Timezone :
America/Mexico_City
Android Version :
11
Android SDK :
30
Build :
RP1A.200720.012.A022MUBU2BUI2
Build Date :
Sat Sep 18 04:51:55 KST 2021
Product Code :
SM-A022MZKLMXO
Device Name :
a02
Product Name :
a02ub
Code Name :
SM-A022MZKLMXO
BL :
A022MUBU2BUI2
PDA :
A022MUBU2BUI2
CP :
A022MUBU2BUI2
CSC :
A022MOWO2BUI2
Sales Code :
MXO
Removing
FRP
...
OK
UNLOCKTOOL
2023.07.04.1
Elapsed time :
28 seconds
FRP Oppo Reno7 4G CPH2363 by UnlockTool
[EDL] FACTORY RESET Selected Model : Oppo Reno7 4G
Code Name : CPH2363
Operation : Factory Reset [4]
Authenticating... OK
Retrieving data... OK [276.42 KiB]
Initializing data... OK
Waiting for HS-USB QDLoader 9008... COM20
Connecting to device... OK
Handshaking... OK
Reading bootloader info... OK
Serial : 1342983630 SoC : [Snapdragon 680 4G] [SM6250] [0x001B80E1]
OEM : Oppo/Oneplus [0x0051] Model : Unknown [0x0000]
PK_HASH[0] : D53F19D28ED8CA4A5D9C5BD7DDB365DB
PK_HASH[1] : C9268CBDE3DFC8A151E70C8B0A0DFFC2
Writing flash programmer... OK
Connecting to flash programmer... OK
Configuring device... OK
Firehose config : UFS [Sector:4096] [Target:0] [Host:1048576]
Erasing FRP... OK
Erasing USERDATA... OK
Rebooting... OK
UNLOCKTOOL 2023.07.04.1
Elapsed time : 13 minutes 34 seconds
Revivir Samsung MTK dead boot Brickeado con pantalla Negra BROM mode
Bajar SamKEY MTK Edition ultima version
comprar Creditos para poder hacer Login
despues solo presionar boton RepairBROM
y en segundos enciende SAMSUNG
https://www.mediafire.com/file/h8lz92zdetia8hw/SamKEYMTK1096.zip/file
Password for ZIP = samkey
FRP Alcatel 4065F (Alcatel 1L Pro) cuenta google by Pandora Box
Alcatel 4065F (Alcatel 1L Pro) cuenta google
Pandora Box by Z3X
cpu SC9863A_64 con vol - y + sostenido
Selected model: Alcatel 4065F (Alcatel 1L Pro)
Operation: Erase FRP
Software version: 5.3
Work ID: 4047228
Connect phone in BROM mode. Use volume key buttons or testpoint.
Waiting for device... OK
Device found at COM14
Port: USB\VID_1782&PID_4D00\5&14A7B65B&0&1
Driver: [UNISOC Communications Inc.,sprdvcom,SPRD U2S Diag,sprdvcom.sys,4.19.38.134]
Port type: BROM
Connecting to device... OK
Selected processor: SC9863A_64
Load files... (universal) OK
Connect preloader 1... OK
Connect preloader 2... OK
Connect loader 1... OK
Connect loader 2... OK
Serial Number: JZNA06CGILE025X
Read partitions info... OK
Checking A/B state... OK [A]
Read product info... [EXT4] ... OK
Product Brand : Alcatel
Product Manufacturer : TCL
Product Model : 4065F
Product Name : Alcatel 4065F
Product Device : Jakarta_Mini
Product Board : s9863a1h10_go_32b
Board Platform : sp9863a
Build ID : RP1A.201005.001
Build Date : Thu Jul 22 22:05:27 EDT 2021
Display ID : 4065F_TGMX_1SIM_V2.2_20210723
Security Patch : 2021-07-05
Version SDK : 30
Version Release : 11
Version Codename : REL
Firmware Version : 4065F_TGMX_1SIM_V2.2
Userdata FS Type : F2FS
Backup partitions... OK
Formatting "persist" partition... OK
Done!
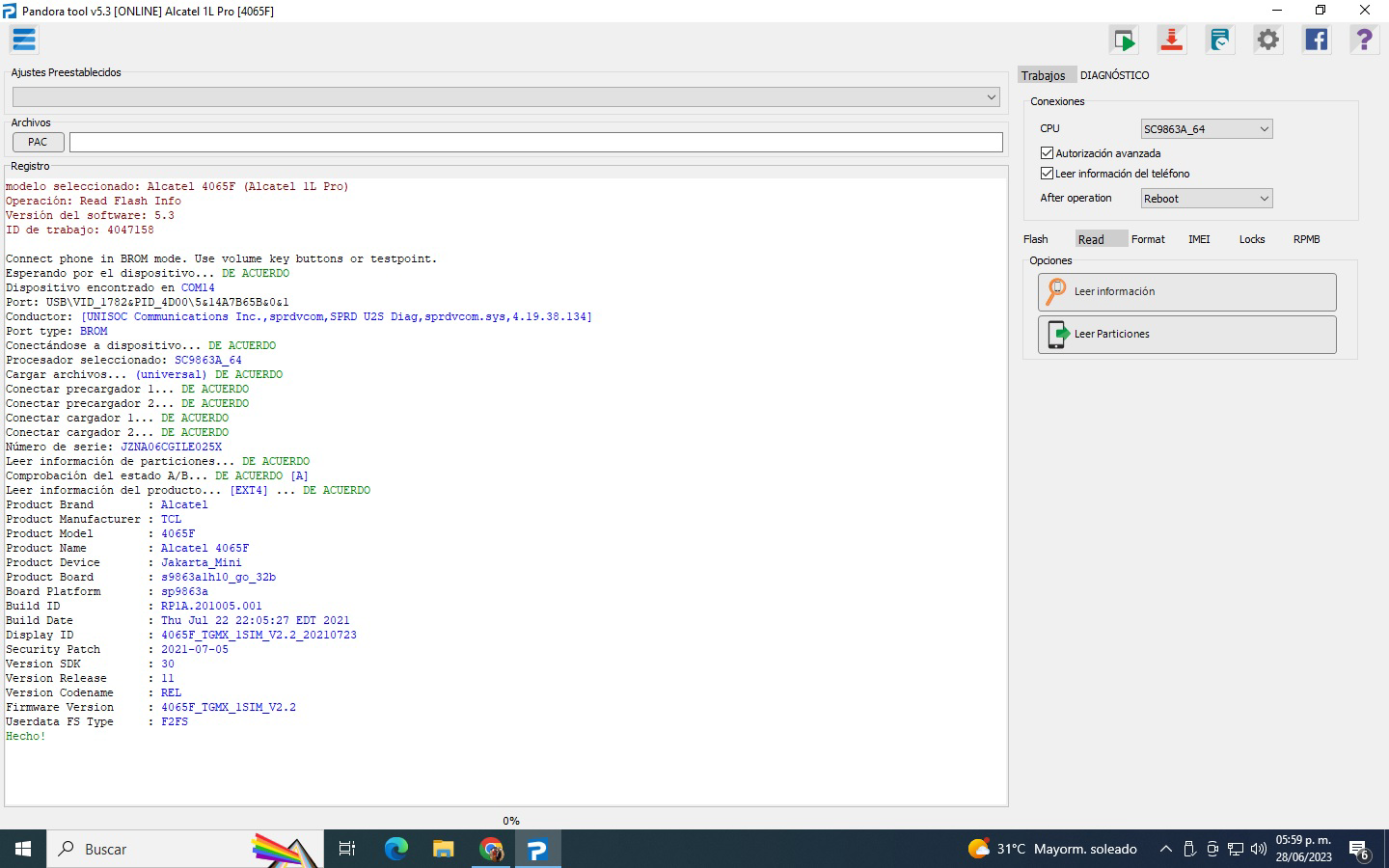
FRP Motorola Moto G20 XT2128-1 Pandora Box
Selected model: Motorola XT2128-1 (Motorola Moto G20)
Operation: Erase FRP
Software version: 5.3
Work ID: 4043978
Connect phone in BROM mode. Use volume key buttons or testpoint.
Waiting for device... OK
Device found at COM7
Port: USB\VID_1782&PID_4D00\5&390FD7C2&0&4
Driver: [UNISOC Communications Inc.,sprdvcom,SPRD U2S Diag,sprdvcom.sys,4.19.38.134]
Port type: BROM
Connecting to device... OK
Selected processor: Tiger_T700_64
Load files... (universal) OK
Connect preloader 1... OK
Connect preloader 2... OK
Connect loader 1... OK
Connect loader 2... OK
Serial Number: ZY32C5HLXP
Read partitions info... OK
Checking A/B state... OK [A]
Read product info... [EXT4] ... OK
Product Brand : motorola
Product Manufacturer : motorola
Product Model : moto g(20)
Product Name : java_retail
Product Device : java
Product Board : p352
Board Platform : ums512
Build ID : RTAS31.68-66-3
Build Date : Tue Feb 21 13:40:32 CST 2023
Display ID : RTAS31.68-66-3
Security Patch : 2023-03-01
Version SDK : 30
Version Release : 11
Version Codename : REL
Firmware Version : 66-3
Userdata FS Type : F2FS
Backup partitions... OK
Formatting "persist" partition... OK
Done!
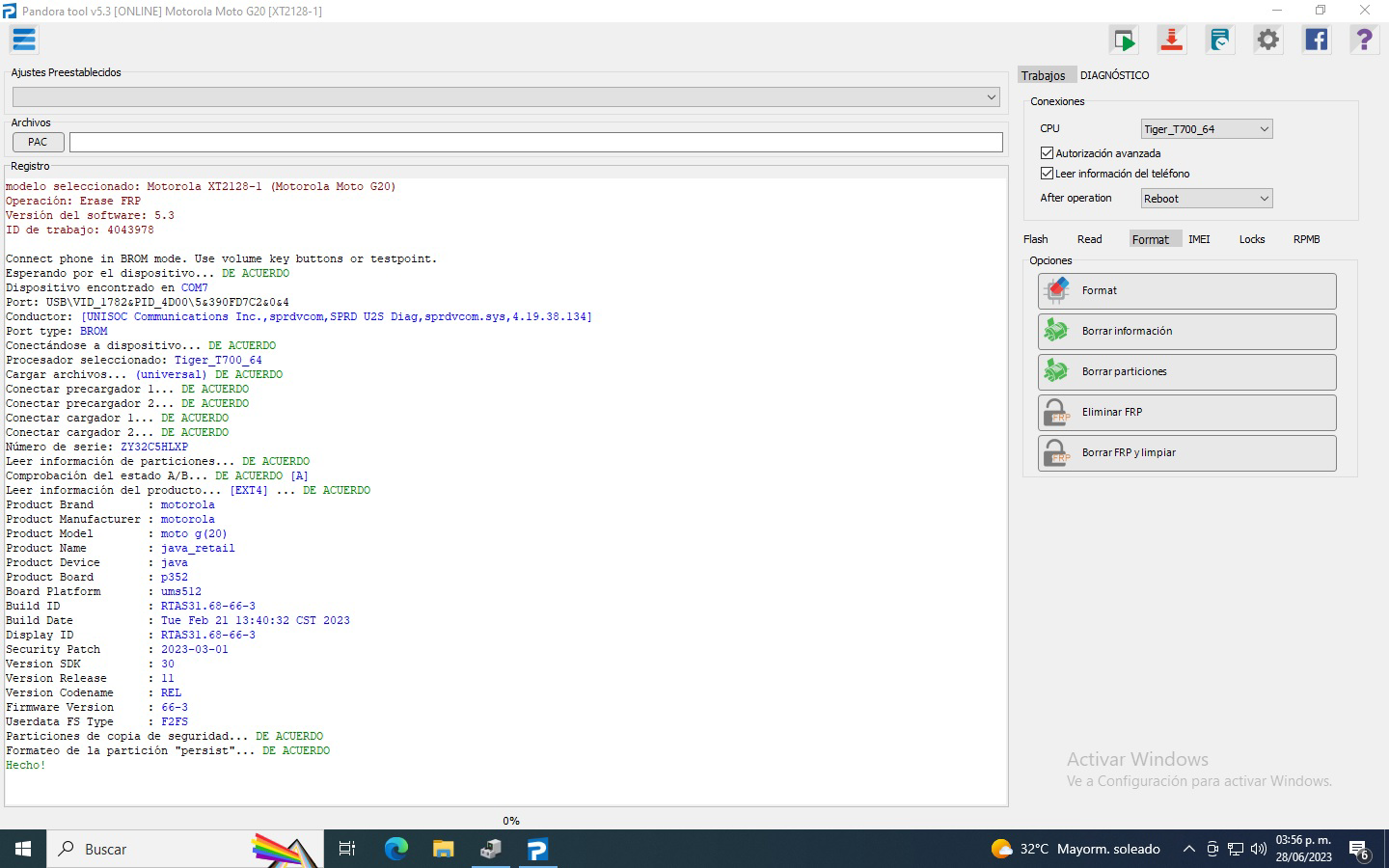
Instalacion libusb win32 driver from Zadig
https://zadig.akeo.ie/#google_vignette
https://github.com/pbatard/libwdi/releases/download/v1.5.0/zadig-2.8.exe
https://github.com/pbatard/libwdi/wiki/Zadig
FRP Motorola E7 XT2095-1
FRP Motorola E7 XT2095-1
FRP Motorola XT2117-3 Moto G Power 2021 Verizon
FRP Motorola XT2117-3 Moto G Power 2021 Verizon
Presionar Volumen abajo + Insertar cable USB
Starting FRP Remove process...
Waiting for device in Fastboot Mode....Done.
Reading Data....Done
UNLOCK.MX ..... Done
Firmware: RZBS31.Q2-143-27-4
Android: 11
CPU: SM_KAMORTA_H 1.0
Model: XT2117-3
SN: ZY22D3NP6Z
IMEI: 356898111296981
Channel ID: 0x83
CID: 0x0002
Carrier: vzw
Reading Data ... Done
Creating Order ID....Done
Operation ID: 1602505
Setting Device Config ... Done
Unlocking Bootloader...Done
Reboot Bootloader ... Done.
Wait for Bootloader Reboot ... Done
Wait for Fastboot Mode ... Done
Verify Factory CID ... Done.
Erase FRP ... Done.
Wait 3 Seconds for FRP ... Done
Erase User Data ... Done.
Erase Cache ... Done.
Wait for erase cache ... Done
Configuring Bootloader...Done
Wait for CID ... Done
Erase Modem1 ... Done.
Erase Modem2 ... Done.
Clear Mode ... Done.
Fastboot Reboot ... Done.
Elapsed Time: 0:49.19
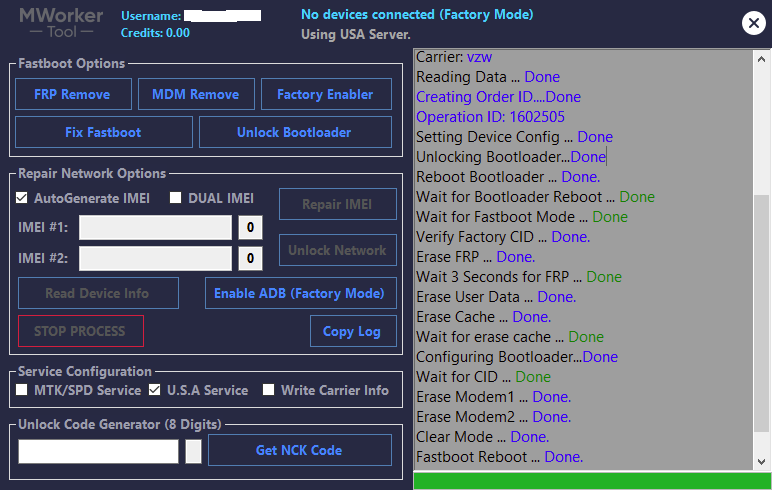
Direct Unlock SM-J260T1 J260T1UVS4ATA1 Samsung Metro Pcs
Poner en Modo desarrollador
marcar *#0808# y seleccionar DM+ACM+ADB
Searching for SAMSUNG Mobile USB Modem...OK
UNLOCK.MX ..... OK
SAMSUNG USB Modem detected on [COM48]
Looking for DEVICE...OK
Reading USB MODEM information...OK
MODEL : SM-J260T1
VER : J260T1UVS4ATA1/J260T1TMK4ATA1/J260T1UVS4ATA1/J260T1UVS4ATA1
VER : J260T1UVS5ATD1
IMEI : 352436112732490
S/N : RF8N214K13
U/N : CQE001E620729B6
Loading ADB module............OK
Loading ADB module.OK
Searching for SAMSUNG ADB device...OK
Checking device authorization...OK
Reading ADB device information...
ADB Serial Number : 42001E620729B6CB
SIM State : OK
AP Version : J260T1UVS4ATA1
CP Version : J260T1UVS4ATA1
Debug Level : OK
Android Version : 8.1.0
Warranty VOID : 0
Setting USB Settings to [dm,acm,adb] automatically...OK
Searching for SAMSUNG Diagnostic Port...[COM47]...OK
Connecting to phone via DIAG port...OK
Reading CP registers.....OK
Executing exploit...[CPRAM:OK]...[BUFF:OK]...OK
Loading RIL applet...OK
Starting RIL applet...OK
Reading RADIO information...
IMEI : 352436112732490
MSL address : RF8N214K13
Initializing RIL applet...OK
Starting exploit...[SHL:OK]...OK
Reading HW signature...OK
Signature status : VALID
Sending data to SERVER...OK
Waiting for SERVER response...OK
Loading RIL applet...[SHL:OK]...OK
Unlocking phone...[OEM:OK]...OK
Operation successful.
PLEASE REBOOT PHONE MANUALLY TO FINISH UNLOCK!
SamKEY Team (2017)
UNLOCK.MX & MULTI-UNLOCK.COM
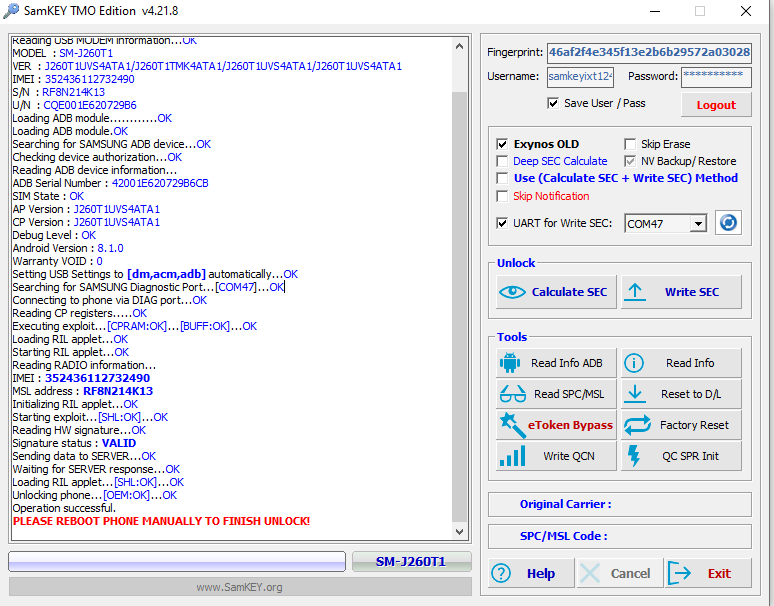
Lanix X860 flash phone write firmware freeze logo start up
Me llego este Lanix X860 se quedaba atorado en el logo
Lanix X860 Mexico Telcel Movistar at&t
https://www.needrom.com/download/lanix-x860/
baja este ROM LANIX X860 - Update SW_03
Open PAC File
Firmware Settings y dejar seleccionadas solo las casillas que tienen palomitas todas las demas desmarquelas
Despues presionar FLASH PHONE en segundos queda prendido y jalando al 100 %
ACTION: Flash Firmware.
Selected firmware: X860_OPEN_SW_03.pac
NV: Default Mode (protect calibration)
Device Storage: EMMC
Start Detect phone...
Unlock.mx ... Done
Phone must be off with battery inside.
Long press "VOL -" key and insert usb cable.
For some phones need to
Long press "VOL -"+ "VOL +" key and insert usb cable.
Detected: SPRD U2S Diag (COM38)
[00:00:00] Sending loader.
BOOT: SPRD3
Sending loader, keep boot key untill loader start.
[00:00:05] Loader ok
[00:00:05] Wait for loader....
Loader OK: ~"Spreadtrum Boot Block version 1.1
Changing bautrate OK.
[00:00:06] [1]First boot done.
[00:00:06] Sending second loader.
[00:00:13] Second loader sent ok.
New flash protocol detected.
[00:00:13] Reading: system
Error while read flash(1).
[00:00:34] Reading: super
System name: super
Phone and firmware have same android
[00:00:34] Reading: miscdata
[00:00:34] Reading: w_fixnv1_a
NVRAM saved to: C:\Users\Montreal\Documents\spreadtrum_module\flashmode_nvram_backup\_352171890429486\_352171890429486_nvram_backup.tar
Phone have super partition.
[00:00:46] Making flash ic repartition.
NV_COMM disabled by user, skip
[uboot_a]Format disabled, skip.
[uboot_log]Format disabled, skip.
[00:00:46] Start write: cache
[00:00:46] Start write: userdata
[w_runtimenv1]Format disabled, skip.
[misc]Format disabled, skip.
[sysdumpdb]Format disabled, skip.
[00:01:02] Start write: persist
[00:01:04] Format: metadata
[00:01:04] [metadata]Format OK.
Flashing done.
[can take 0-10 sec]Wait untill phone restart.
Exe version: NckBox Spreadtrum Module 2.1.8_bugfix
Log saved:
C:\Users\Montreal\Documents\spreadtrum_module\Saved_Logs\_writepac__1.txt
Total Time: 00:01:15
Done.
UNLOCK.MX & MULTI-UNLOCK.COM
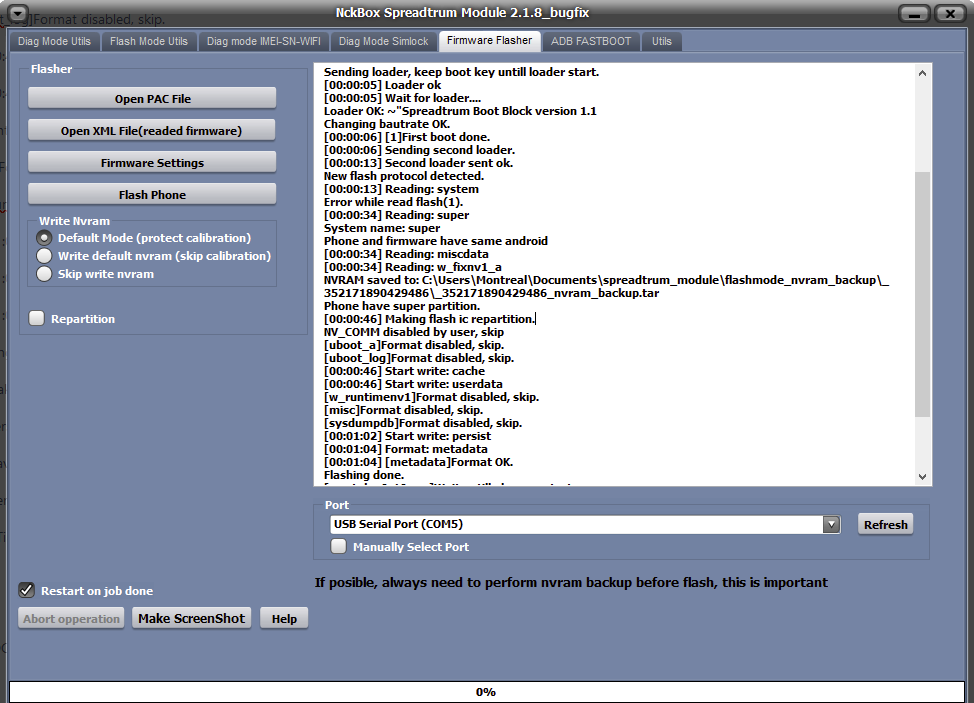
FRP Hot Pepper HPP-L55B Serrano MT6739
Aqui le dejo como quitar cuenta FRP
Waiting for mtk usb device... ok
BootMode : Preloader[COM13]
DriverDesc : MediaTek PreLoader USB VCOM_V1633 (Android)
DriverPath : usb\vid_0e8d&pid_2000\6&1a9a519a&0&1
DriverSRV : wdm_usb
DriverVersion : 3.0.1504.0
DriverDate : 1-22-2015
DriverCFG : oem43.inf
DriverOEM : MediaTek Inc.
Start handshake with Preloader...
PreloaderCmd::CMD_BootAsMETA(): Receive READY succeed!
Send BootMode Switch Request...
reboot to meta mode success!
Wait for meta mode usb device...
Init meta mode api...
Connect to SP_META mode...
connect to meta mode success!
Reading device information...
RNID 9c2c80e918a22bac5f7b8e28be708c5100000000
Bluetooth C4:74:F8:21:7C:A5
WIFIMac C4:74:F8:21:4D:4D
Chip ID MT6739
SW Ver alps-mp-q0.mp1-V9.196.1_xthink.q0mp1.k61v1.64.bsp_P10
● Manufacturer Hot Pepper Inc
● Brand HotPepper
● Model HPP-L55B
● DevName HPP-L55B
● Name Serrano
● Board HotPepper
● Build ID HPP-L55B-M-1.0.7
● Android Ver 10 (Quince Tart)
● EMI ID Serrano-user
● Sec Patch 2022-04-05
● UsbConf mtp
● Branch ID alps-mp-q0.mp1
● Build Type user
● Hardware mt6739
● Device State locked
● VerifiedBootState green
● Flash_locked 1
● Veritymode enforcing
● Base android-chinoe
● CryptState encrypted
● CryptType File Based Encryption (FBE) is present.
● SDKVer 29
● FRP Pst /dev/block/platform/bootdevice/by-name/frp
Format frp success
Rebooting from meta mode...success!
UNLOCK.MX & MULTI-UNLOCK.COM
Read PreLoader mt6739 BROM Mode HotPepper HPP-L55B-M-1.0.7 Serrano
Waiting for mtk usb device... ok
BootMode : Preloader[COM13]
DriverDesc : MediaTek PreLoader USB VCOM_V1633 (Android)
DriverPath : usb\vid_0e8d&pid_2000\6&1a9a519a&0&1
DriverSRV : wdm_usb
DriverVersion : 3.0.1504.0
DriverDate : 1-22-2015
DriverCFG : oem43.inf
DriverOEM : MediaTek Inc.
Start handshake with Preloader...
PreloaderCmd::CMD_BootAsMETA(): Receive READY succeed!
Send BootMode Switch Request...
reboot to meta mode success!
Wait for meta mode usb device...
Init meta mode api...
Connect to SP_META mode...
connect to meta mode success!
Reading device information...
RNID 9c2c80e918a22bac5f7b8e28be708c5100000000
Bluetooth C4:74:F8:21:7C:A5
WIFIMac C4:74:F8:21:4D:4D
Chip ID MT6739
SW Ver alps-mp-q0.mp1-V9.196.1_xthink.q0mp1.k61v1.64.bsp_P10
● Manufacturer Hot Pepper Inc
● Brand HotPepper
● Model HPP-L55B
● DevName HPP-L55B
● Name Serrano
● Board HotPepper
● Build ID HPP-L55B-M-1.0.7
● Android Ver 10 (Quince Tart)
● EMI ID Serrano-user
● Sec Patch 2022-04-05
● UsbConf mtp
● Branch ID alps-mp-q0.mp1
● Build Type user
● Hardware mt6739
● Device State locked
● VerifiedBootState green
● Flash_locked 1
● Veritymode enforcing
● Base android-chinoe
● CryptState encrypted
● CryptType File Based Encryption (FBE) is present.
● SDKVer 29
● FRP Pst /dev/block/platform/bootdevice/by-name/frp
Rebooting from meta mode...success!
●●● Log file saved to => C:/Users/UNLOCK.MX/Downloads/Android_Utility_v106/AndroidUtility.v106/Logs/2023_05_27_18_36_41.log
Waiting for mtk usb device... ok
BootMode : Preloader[COM13]
DriverDesc : MediaTek PreLoader USB VCOM_V1633 (Android)
DriverPath : usb\vid_0e8d&pid_2000\6&1a9a519a&0&1
DriverSRV : wdm_usb
DriverVersion : 3.0.1504.0
DriverDate : 1-22-2015
DriverCFG : oem43.inf
DriverOEM : MediaTek Inc.
Connecting to BootROM......
● Chipset MT6739
● Info 8A00_CB00_0002_zion
Force preloader to BootROM(0)...crash succeed!
Waiting for mtk brom usb device... ok
BootMode : BootRom[COM13]
DriverDesc : MediaTek USB Port_V1633
DriverPath : usb\vid_0e8d&pid_0003\6&1a9a519a&0&1
DriverSRV : wdm_usb
DriverVersion : 3.0.1504.0
DriverDate : 1-22-2015
DriverCFG : oem43.inf
DriverOEM : MediaTek Inc.
Connecting to BootROM......
● Chipset MT6739
● Info 8A00_CB00_0002_zion
● MEID:959ECB9F12C47D1D5B4B71E514B95F6F
● SecCFG SBC+SDA
Dumping preloader from memory...
BootROM::UsbSendDevCtrl:Begin(Dym)!
Preloader file saved to
C:/Users/ UNLOCK.MX/Downloads/Android_Utility_v106/AndroidUtility.v106//2023_05_27_18_38_20_preloader_x038_k39tv1_bsp.bin
Bloader Info Version = (MTK_BLOADER_INFO_v32)●●● Log file saved to => C:/Users/UNLOCK.MX/Downloads/Android_Utility_v106/AndroidUtility.v106/Logs/2023_05_27_18_38_22.log
Moto G60 XT2135-2 Remove FRP Payjoy MDM Remove DONE
The Magic Tool
Start MDM Unlock Task on 5/27/2023 11:55:33 AM -07:00
Waiting for device arrival.... OK
UNLOCK.MX.... OK
Model SKU: XT2135-2
Carrier: RETEU
Serial: ZY22DWP5BK
Authorizing MDM Access...OK
Reboot bootloader...OK
Waiting for device arrival.... OK
Erasing MDM...OK
Erasing FRP...OK
Erasing UserData...OK
Erasing Cache...OK
Final Step...OK
Rebooting...OK
MDM Unlock Task Successful!
UNLOCK.MX
FRP Motorola XT1772 E4 PLUS Done
Se conecta apagado con volumen + / volumen -
Exe version: NCKBox AndroidMTK 2.9.7
Selected model: Motorola XT1773
[auto]Action: Reset FRP
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(26) : MediaTek PreLoader USB VCOM (Android) (COM26)
[26] \\?\usb#vid_0e8d&pid_2000#6&3492803a&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Preloader
BBCHIP: 335 0 ca00
Using Algo 2.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6737M
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 2 GB DRAM
----------------------------------------------------
EMMC: (117Gb+16384Mb) HYNIX 0x484147346132
EMMC FW VERSION: a5:00:00:00:00:00:00:00
EMMC CID: 90014A484147346132 : 00000000000000
EMMC UA SIZE: 0x3ab400000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x3ac000000 [14.688 GB]
Resetting userdata.
Checking data, wait...
Writing FRP, wait...
FRP Reset Done.
Wait untill phone will start charging.
[0]All done.
UNLOCK.MX & MULTI-UNLOCK.COM
ANDROID UTILITY V106:22.05.2023
ANDROID UTILITY V106:22.05.2023
Link descarga
https://mega.nz/file/h5QVRCpY#VQFVejVWHecQSRvhlh7xOaARQeGpsypDB3HUbT_QnxA
UNLOCK.MX
Necesitas ayuda puedes contactarnos
adb device info
Device connected
Brand: HotPepper
Model: HPP-L55B
Android: 10
Serial NO: MA95M2208005964
Extended information
Searching device ...
Device connected
[Build.BRAND]: [MTK]
[camera.disable_zsl_mode]: [1]
[dalvik.vm.appimageformat]: [lz4]
[dalvik.vm.dex2oat-Xms]: [64m]
[dalvik.vm.dex2oat-Xmx]: [512m]
[dalvik.vm.dex2oat-max-image-block-size]: [524288]
[dalvik.vm.dex2oat-minidebuginfo]: [true]
[dalvik.vm.dex2oat-resolve-startup-strings]: [true]
[dalvik.vm.dexopt.secondary]: [true]
[dalvik.vm.heapgrowthlimit]: [256m]
[dalvik.vm.heapsize]: [512m]
[dalvik.vm.image-dex2oat-Xms]: [64m]
[dalvik.vm.image-dex2oat-Xmx]: [64m]
[dalvik.vm.isa.arm.features]: [default]
[dalvik.vm.isa.arm.variant]: [cortex-a53]
[dalvik.vm.minidebuginfo]: [true]
[dalvik.vm.mtk-stack-trace-file]: [/data/anr/mtk_traces.txt]
[dalvik.vm.usejit]: [true]
[dalvik.vm.usejitprofiles]: [true]
[debug.atrace.tags.enableflags]: [0]
[debug.force_rtl]: [false]
[debug.sf.disable_backpressure]: [1]
[dev.bootcomplete]: [1]
[dev.mnt.blk.product]: [dm-5]
[dev.mnt.blk.root]: [dm-3]
[dev.mnt.blk.vendor]: [dm-4]
[drm.service.enabled]: [true]
[gsm.current.phone-type]: [1]
[gsm.network.type]: [Unknown]
[gsm.operator.alpha]: []
[gsm.operator.iso-country]: [mx]
[gsm.operator.isroaming]: [false]
[gsm.operator.numeric]: []
[gsm.sim.num.pin]: [3]
[gsm.sim.num.pin2]: [3]
[gsm.sim.num.puk]: [10]
[gsm.sim.num.puk2]: [10]
[gsm.sim.operator.alpha]: [U.S. Cellular]
[gsm.sim.operator.iso-country]: [us]
[gsm.sim.operator.numeric]: [20404]
[gsm.sim.preiccid_0]: [8901580]
[gsm.sim.state]: [LOADED]
[gsm.sim1.type]: [-1]
[gsm.version.baseband]: [MOLY.LR12A.R3.MP.V140.8.P7]
[gsm.version.ril-impl]: [android reference-ril 1.0]
[hwservicemanager.ready]: [true]
[init.svc.adbd]: [running]
[init.svc.agpsd]: [running]
[init.svc.apexd]: [running]
[init.svc.apexd-bootstrap]: [stopped]
[init.svc.ashmemd]: [running]
[init.svc.audioserver]: [running]
[init.svc.batterywarning]: [running]
[init.svc.bluetooth-1-0]: [running]
[init.svc.bootanim]: [stopped]
[init.svc.bootlogoupdater]: [stopped]
[init.svc.bpfloader]: [stopped]
[init.svc.camerahalserver]: [running]
[init.svc.cameraserver]: [running]
[init.svc.ccci3_mdinit]: [stopped]
[init.svc.ccci_mdinit]: [running]
[init.svc.drm]: [running]
[init.svc.flash_recovery]: [stopped]
[init.svc.fuelgauged]: [running]
[init.svc.fuelgauged_nvram]: [stopped]
[init.svc.gatekeeperd]: [running]
[init.svc.gnss_service]: [running]
[init.svc.gpu]: [running]
[init.svc.gpu-1-0]: [running]
[init.svc.gsid]: [stopped]
[init.svc.health-hal-2-0]: [running]
[init.svc.hidl_memory]: [running]
[init.svc.hwservicemanager]: [running]
[init.svc.idmap2d]: [stopped]
[init.svc.incidentd]: [running]
[init.svc.installd]: [running]
[init.svc.iorapd]: [stopped]
[init.svc.ipsec_mon]: [running]
[init.svc.keystore]: [running]
[init.svc.lbs_dbg]: [running]
[init.svc.lbs_hidl_service]: [running]
[init.svc.light-hal-2-0]: [running]
[init.svc.lmkd]: [running]
[init.svc.logd]: [running]
[init.svc.logd-auditctl]: [stopped]
[init.svc.logd-reinit]: [stopped]
[init.svc.media]: [running]
[init.svc.media.swcodec]: [running]
[init.svc.mediacodec]: [running]
[init.svc.mediadrm]: [running]
[init.svc.mediaextractor]: [running]
[init.svc.mediametrics]: [running]
[init.svc.mnld]: [running]
[init.svc.mobile_log_d]: [running]
[init.svc.mtk_secure_element_hal_service]: [running]
[init.svc.mtkcodecservice-1-1]: [stopped]
[init.svc.netd]: [running]
[init.svc.netdagent]: [running]
[init.svc.netdiag]: [running]
[init.svc.nvram-hidl-1-1]: [running]
[init.svc.nvram_daemon]: [stopped]
[init.svc.power-hal-1-0]: [running]
[init.svc.pq-2-2]: [running]
[init.svc.rcs_volte_stack]: [running]
[init.svc.servicemanager]: [running]
[init.svc.statsd]: [running]
[init.svc.storaged]: [running]
[init.svc.surfaceflinger]: [running]
[init.svc.system_suspend]: [running]
[init.svc.tee_check_keybox]: [stopped]
[init.svc.teed]: [running]
[init.svc.terservice]: [stopped]
[init.svc.thermal]: [running]
[init.svc.thermal_manager]: [stopped]
[init.svc.thermald]: [running]
[init.svc.thermalloadalgod]: [running]
[init.svc.tombstoned]: [running]
[init.svc.ueventd]: [running]
[init.svc.usbd]: [stopped]
[init.svc.vendor.audio-hal-2-0]: [running]
[init.svc.vendor.bip]: [running]
[init.svc.vendor.cas-hal-1-1]: [running]
[init.svc.vendor.ccci3_fsd]: [stopped]
[init.svc.vendor.ccci_fsd]: [running]
[init.svc.vendor.ccci_rpcd]: [running]
[init.svc.vendor.configstore-hal]: [running]
[init.svc.vendor.drm-clearkey-hal-1-2]: [running]
[init.svc.vendor.drm-hal-1-0]: [running]
[init.svc.vendor.drm-widevine-hal-1-2]: [running]
[init.svc.vendor.epdg_wod]: [running]
[init.svc.vendor.gatekeeper-1-0]: [running]
[init.svc.vendor.gralloc-2-0]: [running]
[init.svc.vendor.gsm0710muxd]: [running]
[init.svc.vendor.hwcomposer-2-1]: [running]
[init.svc.vendor.keymaster-4-0-trustkernel]: [running]
[init.svc.vendor.memtrack-hal-1-0]: [running]
[init.svc.vendor.ril-daemon-mtk]: [running]
[init.svc.vendor.sensors-hal-2-0]: [running]
[init.svc.vendor.thermal-hal-1-0]: [running]
[init.svc.vendor.usb-hal-1-1]: [running]
[init.svc.vendor.vibrator-1-0]: [running]
[init.svc.vendor.volte_imcb]: [running]
[init.svc.vendor.volte_stack]: [running]
[init.svc.vendor.volte_ua]: [running]
[init.svc.vendor.wifi_hal_legacy]: [running]
[init.svc.vndservicemanager]: [running]
[init.svc.vold]: [running]
[init.svc.volte_imsm_93]: [running]
[init.svc.volte_md_status]: [running]
[init.svc.volte_rcs_ua]: [running]
[init.svc.vtservice]: [running]
[init.svc.vtservice_hidl]: [running]
[init.svc.wfca]: [running]
[init.svc.wificond]: [running]
[init.svc.wlan_assistant]: [running]
[init.svc.wmt_launcher]: [running]
[init.svc.wmt_loader]: [stopped]
[init.svc.wpa_supplicant]: [running]
[init.svc.xthink_factory]: [stopped]
[init.svc.zygote]: [running]
[log.tag]: [M]
[log.tag.APM_AudioPolicyManager]: [D]
[log.tag.stats_log]: [I]
[media.stagefright.thumbnail.prefer_hw_codecs]: [true]
[mediatek.wlan.ctia]: [0]
[net.bt.name]: [Android]
[net.lte.data.roaming.setting1]: [true]
[net.qtaguid_enabled]: [1]
[net.tcp.default_init_rwnd]: [60]
[persist.adb.nonblocking_ffs]: [0]
[persist.log.tag.APM-KpiMonitor]: [I]
[persist.log.tag.APM-ServiceJ]: [I]
[persist.log.tag.APM-SessionJ]: [I]
[persist.log.tag.APM-SessionN]: [I]
[persist.log.tag.APM-Subscriber]: [I]
[persist.log.tag.AT]: [I]
[persist.log.tag.AdnRecord]: [I]
[persist.log.tag.AdnRecordCache]: [I]
[persist.log.tag.AdnRecordLoader]: [I]
[persist.log.tag.AirplaneHandler]: [I]
[persist.log.tag.AutoRegSmsFwk]: [I]
[persist.log.tag.C2K_RIL-DATA]: [I]
[persist.log.tag.CapaSwitch]: [I]
[persist.log.tag.CarrierExpressServiceImpl]: [I]
[persist.log.tag.CarrierExpressServiceImplExt]: [I]
[persist.log.tag.CdmaMoSms]: [I]
[persist.log.tag.CdmaMtSms]: [I]
[persist.log.tag.ConSmsFwkExt]: [I]
[persist.log.tag.CountryDetector]: [I]
[persist.log.tag.DC-C-1]: [I]
[persist.log.tag.DC-C-2]: [I]
[persist.log.tag.DCT-C-0]: [I]
[persist.log.tag.DCT-C-1]: [I]
[persist.log.tag.DCT-I-0]: [I]
[persist.log.tag.DCT-I-1]: [I]
[persist.log.tag.DMC-ApmService]: [I]
[persist.log.tag.DMC-Core]: [I]
[persist.log.tag.DMC-DmcService]: [I]
[persist.log.tag.DMC-EventsSubscriber]: [I]
[persist.log.tag.DMC-ReqQManager]: [I]
[persist.log.tag.DMC-SessionManager]: [I]
[persist.log.tag.DMC-TranslatorLoader]: [I]
[persist.log.tag.DMC-TranslatorUtils]: [I]
[persist.log.tag.DSSelector]: [I]
[persist.log.tag.DSSelectorOP01]: [I]
[persist.log.tag.DSSelectorOP02]: [I]
[persist.log.tag.DSSelectorOP09]: [I]
[persist.log.tag.DSSelectorOP18]: [I]
[persist.log.tag.DSSelectorOm]: [I]
[persist.log.tag.DSSelectorUtil]: [I]
[persist.log.tag.DataDispatcher]: [I]
[persist.log.tag.DataOnlySmsFwk]: [I]
[persist.log.tag.DcFcMgr]: [I]
[persist.log.tag.DupSmsFilterExt]: [I]
[persist.log.tag.ExternalSimMgr]: [I]
[persist.log.tag.GsmCallTkrHlpr]: [I]
[persist.log.tag.GsmCdmaConn]: [I]
[persist.log.tag.GsmCdmaPhone]: [I]
[persist.log.tag.IMSRILRequest]: [I]
[persist.log.tag.IMS_RILA]: [I]
[persist.log.tag.IccCardProxy]: [I]
[persist.log.tag.IccPhoneBookIM]: [I]
[persist.log.tag.IccProvider]: [I]
[persist.log.tag.ImsApp]: [I]
[persist.log.tag.ImsBaseCommands]: [I]
[persist.log.tag.ImsCall]: [I]
[persist.log.tag.ImsCallProfile]: [I]
[persist.log.tag.ImsCallSession]: [I]
[persist.log.tag.ImsEcbm]: [I]
[persist.log.tag.ImsEcbmProxy]: [I]
[persist.log.tag.ImsManager]: [I]
[persist.log.tag.ImsPhone]: [I]
[persist.log.tag.ImsPhoneBase]: [I]
[persist.log.tag.ImsPhoneCall]: [I]
[persist.log.tag.ImsService]: [I]
[persist.log.tag.ImsVTProvider]: [I]
[persist.log.tag.IsimFileHandler]: [I]
[persist.log.tag.IsimRecords]: [I]
[persist.log.tag.LCM-Subscriber]: [I]
[persist.log.tag.MAPI-CommandProcessor]: [I]
[persist.log.tag.MAPI-MdiRedirector]: [I]
[persist.log.tag.MAPI-MdiRedirectorCtrl]: [I]
[persist.log.tag.MAPI-NetworkSocketConnection]: [I]
[persist.log.tag.MAPI-SocketConnection]: [I]
[persist.log.tag.MAPI-SocketListener]: [I]
[persist.log.tag.MAPI-TranslatorManager]: [I]
[persist.log.tag.MDM-Subscriber]: [I]
[persist.log.tag.MDMI-CommandProcessor]: [I]
[persist.log.tag.MDMI-CoreSession]: [I]
[persist.log.tag.MDMI-MdmiRedirector]: [I]
[persist.log.tag.MDMI-MdmiRedirectorCtrl]: [I]
[persist.log.tag.MDMI-NetworkSocketConnection]: [I]
[persist.log.tag.MDMI-Permission]: [I]
[persist.log.tag.MDMI-Provider]: [I]
[persist.log.tag.MDMI-SocketConnection]: [I]
[persist.log.tag.MDMI-SocketListener]: [I]
[persist.log.tag.MDMI-TranslatorManager]: [I]
[persist.log.tag.MGsmSMSDisp]: [I]
[persist.log.tag.MSimSmsIStatus]: [I]
[persist.log.tag.MSmsStorageMtr]: [I]
[persist.log.tag.MSmsUsageMtr]: [I]
[persist.log.tag.MTKSST]: [D]
[persist.log.tag.MtkAdnRecord]: [I]
[persist.log.tag.MtkConSmsFwk]: [I]
[persist.log.tag.MtkCsimFH]: [I]
[persist.log.tag.MtkDupSmsFilter]: [I]
[persist.log.tag.MtkEmbmsAdaptor]: [I]
[persist.log.tag.MtkFactory]: [I]
[persist.log.tag.MtkGsmCdmaConn]: [I]
[persist.log.tag.MtkIccCardProxy]: [I]
[persist.log.tag.MtkIccPHBIM]: [I]
[persist.log.tag.MtkIccProvider]: [I]
[persist.log.tag.MtkIccSmsIntMgr]: [I]
[persist.log.tag.MtkImsManager]: [I]
[persist.log.tag.MtkImsService]: [I]
[persist.log.tag.MtkIsimFH]: [I]
[persist.log.tag.MtkPhoneNotifr]: [I]
[persist.log.tag.MtkPhoneNumberUtils]: [I]
[persist.log.tag.MtkPhoneSwitcher]: [D]
[persist.log.tag.MtkRecordLoader]: [I]
[persist.log.tag.MtkRetryManager]: [I]
[persist.log.tag.MtkRuimFH]: [I]
[persist.log.tag.MtkSIMFH]: [I]
[persist.log.tag.MtkSIMRecords]: [I]
[persist.log.tag.MtkSmsCbHeader]: [I]
[persist.log.tag.MtkSmsManager]: [I]
[persist.log.tag.MtkSmsMessage]: [I]
[persist.log.tag.MtkSpnOverride]: [I]
[persist.log.tag.MtkSubCtrl]: [I]
[persist.log.tag.MtkUiccCard]: [I]
[persist.log.tag.MtkUiccCardApp]: [I]
[persist.log.tag.MtkUiccCtrl]: [I]
[persist.log.tag.MtkUsimFH]: [I]
[persist.log.tag.Mtk_RIL_ImsSms]: [I]
[persist.log.tag.MwiRIL]: [I]
[persist.log.tag.NetAgentService]: [I]
[persist.log.tag.NetAgent_IO]: [I]
[persist.log.tag.NetLnkEventHdlr]: [I]
[persist.log.tag.NetworkPolicy]: [I]
[persist.log.tag.NetworkStats]: [I]
[persist.log.tag.OperatorUtils]: [I]
[persist.log.tag.PKM-Lib]: [I]
[persist.log.tag.PKM-MDM]: [I]
[persist.log.tag.PKM-Monitor]: [I]
[persist.log.tag.PKM-SA]: [I]
[persist.log.tag.PKM-Service]: [I]
[persist.log.tag.Phone]: [I]
[persist.log.tag.PhoneConfigurationSettings]: [I]
[persist.log.tag.PhoneFactory]: [I]
[persist.log.tag.PowerHalAddressUitls]: [I]
[persist.log.tag.PowerHalMgrImpl]: [I]
[persist.log.tag.PowerHalMgrServiceImpl]: [I]
[persist.log.tag.PowerHalWifiMonitor]: [I]
[persist.log.tag.PowerWrap]: [I]
[persist.log.tag.ProxyController]: [I]
[persist.log.tag.RFX]: [I]
[persist.log.tag.RIL]: [I]
[persist.log.tag.RIL-CC]: [I]
[persist.log.tag.RIL-DATA]: [I]
[persist.log.tag.RIL-Fusion]: [I]
[persist.log.tag.RIL-Netlink]: [I]
[persist.log.tag.RIL-OEM]: [I]
[persist.log.tag.RIL-PHB]: [I]
[persist.log.tag.RIL-Parcel]: [I]
[persist.log.tag.RIL-RP]: [I]
[persist.log.tag.RIL-SIM]: [I]
[persist.log.tag.RIL-SMS]: [I]
[persist.log.tag.RIL-SocListen]: [I]
[persist.log.tag.RIL-Socket]: [I]
[persist.log.tag.RILC]: [I]
[persist.log.tag.RILC-MTK]: [I]
[persist.log.tag.RILC-OP]: [I]
[persist.log.tag.RILC-RP]: [I]
[persist.log.tag.RILD]: [I]
[persist.log.tag.RILMD2-SS]: [I]
[persist.log.tag.RILMUXD]: [I]
[persist.log.tag.RIL_Mux]: [I]
[persist.log.tag.RIL_UIM_SOCKET]: [I]
[persist.log.tag.RP_DAC]: [I]
[persist.log.tag.RP_DC]: [I]
[persist.log.tag.RP_IMS]: [I]
[persist.log.tag.RTC_DAC]: [I]
[persist.log.tag.RadioManager]: [I]
[persist.log.tag.RetryManager]: [I]
[persist.log.tag.RfxAction]: [I]
[persist.log.tag.RfxChannelMgr]: [I]
[persist.log.tag.RfxCloneMgr]: [I]
[persist.log.tag.RfxContFactory]: [I]
[persist.log.tag.RfxController]: [I]
[persist.log.tag.RfxDT]: [I]
[persist.log.tag.RfxDebugInfo]: [I]
[persist.log.tag.RfxDefDestUtils]: [I]
[persist.log.tag.RfxDisThread]: [I]
[persist.log.tag.RfxFragEnc]: [I]
[persist.log.tag.RfxHandlerMgr]: [I]
[persist.log.tag.RfxIdToMsgId]: [I]
[persist.log.tag.RfxIdToStr]: [I]
[persist.log.tag.RfxMainThread]: [I]
[persist.log.tag.RfxMclDisThread]: [I]
[persist.log.tag.RfxMclMessenger]: [I]
[persist.log.tag.RfxMclStatusMgr]: [I]
[persist.log.tag.RfxMessage]: [I]
[persist.log.tag.RfxObject]: [I]
[persist.log.tag.RfxOpUtils]: [I]
[persist.log.tag.RfxRilAdapter]: [I]
[persist.log.tag.RfxRilUtils]: [I]
[persist.log.tag.RfxRoot]: [I]
[persist.log.tag.RfxSM]: [I]
[persist.log.tag.RfxSocketSM]: [I]
[persist.log.tag.RfxStatusMgr]: [I]
[persist.log.tag.RfxTimer]: [I]
[persist.log.tag.RfxTransUtils]: [I]
[persist.log.tag.RilClient]: [I]
[persist.log.tag.RilMalClient]: [I]
[persist.log.tag.RilOemClient]: [I]
[persist.log.tag.RilOpProxy]: [I]
[persist.log.tag.RmcCapa]: [I]
[persist.log.tag.RmcCdmaSimRequest]: [I]
[persist.log.tag.RmcCdmaSimUrc]: [I]
[persist.log.tag.RmcCommSimOpReq]: [I]
[persist.log.tag.RmcCommSimReq]: [I]
[persist.log.tag.RmcCommSimUrc]: [I]
[persist.log.tag.RmcDcCommon]: [I]
[persist.log.tag.RmcDcDefault]: [I]
[persist.log.tag.RmcDcPdnManager]: [I]
[persist.log.tag.RmcDcReqHandler]: [I]
[persist.log.tag.RmcDcUtility]: [I]
[persist.log.tag.RmcEccNumberUrcHandler]: [D]
[persist.log.tag.RmcEmbmsReq]: [I]
[persist.log.tag.RmcEmbmsUrc]: [I]
[persist.log.tag.RmcGsmSimRequest]: [I]
[persist.log.tag.RmcGsmSimUrc]: [I]
[persist.log.tag.RmcImsCtlReqHdl]: [I]
[persist.log.tag.RmcImsCtlUrcHdl]: [I]
[persist.log.tag.RmcNwHdlr]: [D]
[persist.log.tag.RmcNwRTReqHdlr]: [D]
[persist.log.tag.RmcNwReqHdlr]: [D]
[persist.log.tag.RmcOemHandler]: [I]
[persist.log.tag.RmcOpRadioReq]: [I]
[persist.log.tag.RmcPhbReq]: [I]
[persist.log.tag.RmcPhbUrc]: [I]
[persist.log.tag.RmcRadioReq]: [I]
[persist.log.tag.RmcRatSwHdlr]: [D]
[persist.log.tag.RmcWp]: [I]
[persist.log.tag.RpAudioControl]: [I]
[persist.log.tag.RpCallControl]: [I]
[persist.log.tag.RpCdmaOemCtrl]: [I]
[persist.log.tag.RpCdmaRadioCtrl]: [I]
[persist.log.tag.RpFOUtils]: [I]
[persist.log.tag.RpMDCtrl]: [I]
[persist.log.tag.RpMalController]: [I]
[persist.log.tag.RpModemMessage]: [I]
[persist.log.tag.RpPhbController]: [I]
[persist.log.tag.RpPhoneNumberController]: [D]
[persist.log.tag.RpRadioCtrl]: [I]
[persist.log.tag.RpRadioMessage]: [I]
[persist.log.tag.RpRilClientCtrl]: [I]
[persist.log.tag.RpSimController]: [I]
[persist.log.tag.RtcCapa]: [I]
[persist.log.tag.RtcCommSimCtrl]: [I]
[persist.log.tag.RtcDC]: [I]
[persist.log.tag.RtcEccNumberController]: [D]
[persist.log.tag.RtcEmbmsAt]: [I]
[persist.log.tag.RtcEmbmsUtil]: [I]
[persist.log.tag.RtcIms]: [I]
[persist.log.tag.RtcImsConference]: [I]
[persist.log.tag.RtcImsDialog]: [I]
[persist.log.tag.RtcModeCont]: [I]
[persist.log.tag.RtcNwCtrl]: [I]
[persist.log.tag.RtcPhb]: [I]
[persist.log.tag.RtcRadioCont]: [I]
[persist.log.tag.RtcRatSwCtrl]: [D]
[persist.log.tag.RtcWp]: [I]
[persist.log.tag.SIMRecords]: [I]
[persist.log.tag.SimSwitchOP01]: [I]
[persist.log.tag.SimSwitchOP02]: [I]
[persist.log.tag.SimSwitchOP18]: [I]
[persist.log.tag.SlotQueueEntry]: [I]
[persist.log.tag.SmsPlusCode]: [I]
[persist.log.tag.SpnOverride]: [I]
[persist.log.tag.Telecom]: [I]
[persist.log.tag.UiccCard]: [I]
[persist.log.tag.UiccController]: [I]
[persist.log.tag.UxUtility]: [I]
[persist.log.tag.VT]: [I]
[persist.log.tag.VsimAdaptor]: [I]
[persist.log.tag.WORLDMODE]: [I]
[persist.log.tag.WfoApp]: [I]
[persist.log.tag.legacy_power@2.1-impl]: [I]
[persist.log.tag.libPowerHal]: [I]
[persist.log.tag.mtkperf_client]: [I]
[persist.log.tag.mtkpower@1.0-impl]: [I]
[persist.log.tag.power@1.3-impl]: [I]
[persist.log.tag.powerd]: [I]
[persist.qiku.operators.isabroad]: [1]
[persist.radio.multisim.config]: [ss]
[persist.radio.voice.domain.prefer]: [3]
[persist.sys.alarm.test]: [true]
[persist.sys.boot.reason]: []
[persist.sys.boot.reason.history]: [cold,powerkey,1262304008
reboot,mtk,1651291951
cold,powerkey,1262304068
reboot,1262304147]
[persist.sys.dalvik.vm.lib.2]: [libart.so]
[persist.sys.device_provisioned]: [1]
[persist.sys.displayinset.top]: [0]
[persist.sys.gps.lpp]: [0]
[persist.sys.isolated_storage]: [true]
[persist.sys.locale]: [en-US]
[persist.sys.timezone]: [America/New_York]
[persist.sys.usb.config]: [adb]
[persist.vendor.audiohal.besloudness_state]: [1]
[persist.vendor.audiohal.firstboot]: [0]
[persist.vendor.camera3.pipeline.bufnum.base.imgo]: [5]
[persist.vendor.camera3.pipeline.bufnum.base.lcso]: [5]
[persist.vendor.camera3.pipeline.bufnum.base.rrzo]: [5]
[persist.vendor.camera3.pipeline.bufnum.base.rsso]: [5]
[persist.vendor.camera3.pipeline.bufnum.min.high_ram.fdyuv]: [8]
[persist.vendor.camera3.pipeline.bufnum.min.high_ram.imgo]: [8]
[persist.vendor.camera3.pipeline.bufnum.min.high_ram.lcso]: [8]
[persist.vendor.camera3.pipeline.bufnum.min.high_ram.rrzo]: [8]
[persist.vendor.camera3.pipeline.bufnum.min.high_ram.rsso]: [8]
[persist.vendor.camera3.pipeline.bufnum.min.low_ram.fdyuv]: [6]
[persist.vendor.camera3.pipeline.bufnum.min.low_ram.imgo]: [6]
[persist.vendor.camera3.pipeline.bufnum.min.low_ram.lcso]: [6]
[persist.vendor.camera3.pipeline.bufnum.min.low_ram.rrzo]: [6]
[persist.vendor.camera3.pipeline.bufnum.min.low_ram.rsso]: [6]
[persist.vendor.connsys.chipid]: [0x6739]
[persist.vendor.connsys.dynamic.dump]: [0]
[persist.vendor.connsys.fm_chipid]: [mt6627]
[persist.vendor.connsys.patch.version]: [20200629194517a]
[persist.vendor.duraspeed.app.on]: [1]
[persist.vendor.duraspeed.support]: [1]
[persist.vendor.ims_support]: [1]
[persist.vendor.log.tel_log_ctrl]: [1]
[persist.vendor.mims_support]: [2]
[persist.vendor.mtk.provision.int.01]: [26,0;27,1;66,0;]
[persist.vendor.mtk.vilte.enable]: [0]
[persist.vendor.mtk.viwifi.enable]: [0]
[persist.vendor.mtk.volte.enable]: [1]
[persist.vendor.mtk.wfc.enable]: [0]
[persist.vendor.mtk_ct_volte_support]: [1]
[persist.vendor.mtk_dynamic_ims_switch]: [1]
[persist.vendor.mtk_rcs_ua_support]: [1]
[persist.vendor.mtk_sim_switch_policy]: [2]
[persist.vendor.mtk_wfc_support]: [1]
[persist.vendor.radio.airplane.mode.on]: [false]
[persist.vendor.radio.c_capability_slot]: [0]
[persist.vendor.radio.fd.counter]: [150]
[persist.vendor.radio.fd.off.counter]: [50]
[persist.vendor.radio.fd.off.r8.counter]: [50]
[persist.vendor.radio.fd.r8.counter]: [150]
[persist.vendor.radio.msimmode]: [ss]
[persist.vendor.radio.mtk_dsbp_support]: [1]
[persist.vendor.radio.mtk_ps2_rat]: [L/W/G]
[persist.vendor.radio.mtk_ps3_rat]: [G]
[persist.vendor.radio.pendcapswt]: [0]
[persist.vendor.radio.raf1]: [81930]
[persist.vendor.radio.rilj_nw_type1]: [20]
[persist.vendor.radio.signal_band]: [2]
[persist.vendor.radio.sim.mode]: [1]
[persist.vendor.radio.simswitch]: [1]
[persist.vendor.radio.smart.data.switch]: [1]
[persist.vendor.radio.terminal-based.clir_m]: [4]
[persist.vendor.radio.terminal-based.clir_n]: [0]
[persist.vendor.radio.terminal-based.cw]: [disabled_tbcw]
[persist.vendor.radio.volte_state]: [1]
[persist.vendor.radio.wfc_state]: [0]
[persist.vendor.ss.modem_version]: [0]
[persist.vendor.sys.pq.adl.idx]: [0]
[persist.vendor.sys.pq.bluelight.default]: [128]
[persist.vendor.sys.pq.hdr.en]: [1]
[persist.vendor.sys.pq.hfg.en]: [2]
[persist.vendor.sys.pq.iso.shp.en]: [2]
[persist.vendor.sys.pq.mdp.ccorr.en]: [0]
[persist.vendor.sys.pq.mdp.color.dbg]: [1]
[persist.vendor.sys.pq.mdp.color.idx]: [0]
[persist.vendor.sys.pq.mdp.dre.en]: [2]
[persist.vendor.sys.pq.mdp.hdrvp.dre.en]: [2]
[persist.vendor.sys.pq.mdp.vp.dre.en]: [1]
[persist.vendor.sys.pq.shp.idx]: [2]
[persist.vendor.sys.pq.ultrares.en]: [2]
[persist.vendor.vilte_support]: [1]
[persist.vendor.viwifi_support]: [1]
[persist.vendor.volte_support]: [1]
[persist.vendor.vt.RTPInfo]: [1]
[pm.boot.disable_package_cache]: [true]
[pm.dexopt.ab-ota]: [speed-profile]
[pm.dexopt.bg-dexopt]: [speed-profile]
[pm.dexopt.boot]: [verify]
[pm.dexopt.first-boot]: [quicken]
[pm.dexopt.inactive]: [verify]
[pm.dexopt.install]: [speed-profile]
[pm.dexopt.shared]: [speed]
[qemu.hw.mainkeys]: [0]
[ril.ecclist]: [911,112,*911,#911,*272911]
[ro.actionable_compatible_property.enabled]: [false]
[ro.adb.secure]: [1]
[ro.allow.mock.location]: [0]
[ro.apex.updatable]: [true]
[ro.audio.silent]: [0]
[ro.audio.usb.period_us]: [16000]
[ro.base_build]: [noah]
[ro.baseband]: [unknown]
[ro.bionic.2nd_arch]: []
[ro.bionic.2nd_cpu_variant]: [cortex-a53]
[ro.bionic.arch]: [arm]
[ro.bionic.cpu_variant]: [cortex-a53]
[ro.board.platform]: [mt6739]
[ro.boot.atm]: [disabled]
[ro.boot.avb_version]: [1.1]
[ro.boot.boot_devices]: [bootdevice,11230000.mmc]
[ro.boot.bootlogo_number]: [A95M]
[ro.boot.bootreason]: [PowerKey]
[ro.boot.dtb_idx]: [0]
[ro.boot.dtbo_idx]: [0]
[ro.boot.dynamic_partitions]: [true]
[ro.boot.efuse_status]: [1]
[ro.boot.flash.locked]: [1]
[ro.boot.hardware]: [mt6739]
[ro.boot.hardware.revision]: [A95_P0]
[ro.boot.meta_log_disable]: [0]
[ro.boot.mode]: [normal]
[ro.boot.serialno]: [MA95M2208005964]
[ro.boot.vbmeta.avb_version]: [1.1]
[ro.boot.vbmeta.device_state]: [locked]
[ro.boot.vbmeta.digest]: [02215227ffd4a9fee5636e9241682f57c2b62955d9a5a12d8f1a904bb3bed8ac]
[ro.boot.vbmeta.hash_alg]: [sha256]
[ro.boot.vbmeta.size]: [10176]
[ro.boot.verifiedbootstate]: [green]
[ro.boot.veritymode]: [enforcing]
[ro.boot.veritymode.managed]: [yes]
[ro.bootimage.build.date]: [Sat Apr 30 11:59:13 CST 2022]
[ro.bootimage.build.date.utc]: [1651291153]
[ro.bootimage.build.fingerprint]: [HotPepper/Serrano/HPP-L55B:10/QP1A.190711.020/581:user/release-keys]
[ro.bootloader]: [unknown]
[ro.bootmode]: [normal]
[ro.build.branch.name]: []
[ro.build.characteristics]: [default]
[ro.build.date]: [Sat Apr 30 11:59:13 CST 2022]
[ro.build.date.utc]: [1651291153]
[ro.build.description]: [Serrano-user 10 QP1A.190711.020 581 release-keys]
[ro.build.display.id]: [HPP-L55B-M-1.0.7]
[ro.build.fingerprint]: [HotPepper/Serrano/HPP-L55B:10/QP1A.190711.020/581:user/release-keys]
[ro.build.flavor]: [Serrano-user]
[ro.build.host]: [xx]
[ro.build.id]: [QP1A.190711.020]
[ro.build.product]: [Serrano]
[ro.build.system_root_image]: [false]
[ro.build.tags]: [release-keys]
[ro.build.type]: [user]
[ro.build.user]: [xx]
[ro.build.version.all_codenames]: [REL]
[ro.build.version.base_os]: [HotPepper/Serrano/HPP-L55B:10/QP1A.190711.020/566:user/release-keys]
[ro.build.version.codename]: [REL]
[ro.build.version.incremental]: [581]
[ro.build.version.min_supported_target_sdk]: [23]
[ro.build.version.preview_sdk]: [0]
[ro.build.version.preview_sdk_fingerprint]: [REL]
[ro.build.version.release]: [10]
[ro.build.version.sdk]: [29]
[ro.build.version.security_patch]: [2022-04-05]
[ro.build.x.display.id]: [HPP-L55B-M-1.0.7.2022043012]
[ro.camera.sound.forced]: [0]
[ro.carrier]: [unknown]
[ro.com.android.dataroaming]: [true]
[ro.com.android.mobiledata]: [true]
[ro.com.google.acsa]: [true]
[ro.com.google.clientidbase]: [android-chinoe]
[ro.com.google.clientidbase.am]: [android-uscellular-us]
[ro.com.google.clientidbase.ms]: [android-uscellular-us-revc]
[ro.com.google.gmsversion]: [10_202102]
[ro.config.alarm_alert]: [Alarm_Classic.ogg]
[ro.config.max_starting_bg]: [4]
[ro.config.notification_sound]: [OnTheHunt.ogg]
[ro.config.per_app_memcg]: [false]
[ro.config.ringtone]: [Ring_Synth_04.ogg]
[ro.control_privapp_permissions]: [enforce]
[ro.crypto.state]: [encrypted]
[ro.crypto.type]: [file]
[ro.crypto.volume.filenames_mode]: [aes-256-cts]
[ro.dalvik.vm.native.bridge]: [0]
[ro.debuggable]: [0]
[ro.device_owner]: [false]
[ro.frp.pst]: [/dev/block/platform/bootdevice/by-name/frp]
[ro.hardware]: [mt6739]
[ro.hardware.egl]: [mtk]
[ro.hwui.use_vulkan]: []
[ro.iorapd.enable]: [false]
[ro.kernel.zio]: [38,108,105,16]
[ro.lmk.downgrade_pressure]: [60]
[ro.lmk.kill_heaviest_task]: [true]
[ro.lmk.kill_timeout_ms]: [100]
[ro.lmk.upgrade_pressure]: [30]
[ro.lmk.use_minfree_levels]: [true]
[ro.logd.kernel]: [false]
[ro.logd.size.stats]: [64K]
[ro.mediatek.rsc_name]: [default]
[ro.mediatek.version.branch]: [alps-mp-q0.mp1]
[ro.mediatek.version.release]: [alps-mp-q0.mp1-V9.196.1_xthink.q0mp1.k61v1.64.bsp_P10]
[ro.mediatek.wlan.p2p]: [1]
[ro.mediatek.wlan.wsc]: [1]
[ro.mtk_modem_monitor_support]: [1]
[ro.mtk_perf_fast_start_win]: [1]
[ro.mtk_perf_response_time]: [1]
[ro.mtk_perf_simple_start_win]: [1]
[ro.odm.build.date]: [Sat Apr 30 11:59:13 CST 2022]
[ro.odm.build.date.utc]: [1651291153]
[ro.odm.build.fingerprint]: [HotPepper/Serrano/HPP-L55B:10/QP1A.190711.020/581:user/release-keys]
[ro.odm.build.id]: [QP1A.190711.020]
[ro.odm.build.tags]: [release-keys]
[ro.odm.build.type]: [user]
[ro.odm.build.version.incremental]: [581]
[ro.odm.build.version.release]: [10]
[ro.odm.build.version.sdk]: [29]
[ro.odm.product.cpu.abilist]: [armeabi-v7a,armeabi]
[ro.odm.product.cpu.abilist32]: [armeabi-v7a,armeabi]
[ro.odm.product.cpu.abilist64]: []
[ro.oem_unlock_supported]: [1]
[ro.opa.eligible_device]: [true]
[ro.opengles.version]: [196610]
[ro.postinstall.fstab.prefix]: [/system]
[ro.product.board]: [HotPepper]
[ro.product.brand]: [HotPepper]
[ro.product.build.date]: [Sat Apr 30 11:59:13 CST 2022]
[ro.product.build.date.utc]: [1651291153]
[ro.product.build.fingerprint]: [HotPepper/Serrano/HPP-L55B:10/QP1A.190711.020/581:user/release-keys]
[ro.product.build.id]: [QP1A.190711.020]
[ro.product.build.tags]: [release-keys]
[ro.product.build.type]: [user]
[ro.product.build.version.incremental]: [581]
[ro.product.build.version.release]: [10]
[ro.product.build.version.sdk]: [29]
[ro.product.cpu.abi]: [armeabi-v7a]
[ro.product.cpu.abi2]: [armeabi]
[ro.product.cpu.abilist]: [armeabi-v7a,armeabi]
[ro.product.cpu.abilist32]: [armeabi-v7a,armeabi]
[ro.product.cpu.abilist64]: []
[ro.product.device]: [HPP-L55B]
[ro.product.first_api_level]: [28]
[ro.product.locale]: [en-US]
[ro.product.manufacturer]: [Hot Pepper Inc]
[ro.product.model]: [HPP-L55B]
[ro.product.name]: [Serrano]
[ro.product.odm.brand]: [HotPepper]
[ro.product.odm.device]: [HPP-L55B]
[ro.product.odm.manufacturer]: [Hot Pepper Inc]
[ro.product.odm.model]: [HPP-L55B]
[ro.product.odm.name]: [Serrano]
[ro.product.product.brand]: [HotPepper]
[ro.product.product.device]: [HPP-L55B]
[ro.product.product.manufacturer]: [Hot Pepper Inc]
[ro.product.product.model]: [HPP-L55B]
[ro.product.product.name]: [Serrano]
[ro.product.property_source_order]: [odm,vendor,product,system]
[ro.product.system.brand]: [HotPepper]
[ro.product.system.device]: [HPP-L55B]
[ro.product.system.manufacturer]: [Hot Pepper Inc]
[ro.product.system.model]: [HPP-L55B]
[ro.product.system.name]: [Serrano]
[ro.product.vendor.brand]: [HotPepper]
[ro.product.vendor.device]: [HPP-L55B]
[ro.product.vendor.manufacturer]: [Hot Pepper Inc]
[ro.product.vendor.model]: [HPP-L55B]
[ro.product.vendor.name]: [Serrano]
[ro.product.xdev_model]: [x038_k39tv1_bsp]
[ro.property_service.version]: [2]
[ro.revision]: [0]
[ro.secure]: [1]
[ro.serialno]: [MA95M2208005964]
[ro.setupwizard.rotation_locked]: [true]
[ro.sf.lcd_density]: [240]
[ro.surface_flinger.primary_display_orientation]: [0]
[ro.sys.usb.bicr]: [no]
[ro.sys.usb.charging.only]: [yes]
[ro.sys.usb.mtp.whql.enable]: [0]
[ro.sys.usb.storage.type]: [mtp]
[ro.system.build.date]: [Sat Apr 30 11:59:13 CST 2022]
[ro.system.build.date.utc]: [1651291153]
[ro.system.build.fingerprint]: [HotPepper/Serrano/HPP-L55B:10/QP1A.190711.020/581:user/release-keys]
[ro.system.build.id]: [QP1A.190711.020]
[ro.system.build.tags]: [release-keys]
[ro.system.build.type]: [user]
[ro.system.build.version.incremental]: [581]
[ro.system.build.version.release]: [10]
[ro.system.build.version.sdk]: [29]
[ro.telephony.default_network]: [9,9,9,9]
[ro.telephony.iwlan_operation_mode]: [default]
[ro.telephony.sim.count]: [1]
[ro.treble.enabled]: [true]
[ro.vendor.ap_info_monitor]: [0]
[ro.vendor.build.date]: [Sat Apr 30 11:59:13 CST 2022]
[ro.vendor.build.date.utc]: [1651291153]
[ro.vendor.build.fingerprint]: [HotPepper/Serrano/HPP-L55B:10/QP1A.190711.020/581:user/release-keys]
[ro.vendor.build.id]: [QP1A.190711.020]
[ro.vendor.build.security_patch]: [2022-04-05]
[ro.vendor.build.tags]: [release-keys]
[ro.vendor.build.type]: [user]
[ro.vendor.build.version.incremental]: [581]
[ro.vendor.build.version.release]: [10]
[ro.vendor.build.version.sdk]: [29]
[ro.vendor.camera.isp-version.major]: [3]
[ro.vendor.camera3.zsl.default]: [150]
[ro.vendor.enable.geo.fencing]: [1]
[ro.vendor.md_apps.load_date]: [2022/04/30 11:51:12 GMT +08:00]
[ro.vendor.md_apps.load_gencfg]: [GEN93_USER]
[ro.vendor.md_apps.load_type]: [user]
[ro.vendor.md_apps.load_verno]: [MOLY.LR12A.R3.MP.V140.8.P7]
[ro.vendor.md_apps.support]: [1]
[ro.vendor.md_auto_setup_ims]: [1]
[ro.vendor.md_mims_support]: [2]
[ro.vendor.md_prop_ver]: [1]
[ro.vendor.mediatek.rsc_name]: [default]
[ro.vendor.mediatek.version.branch]: [alps-mp-q0.mp1]
[ro.vendor.mediatek.version.release]: [alps-mp-q0.mp1-V9.196.1_xthink.q0mp1.k61v1.64.bsp_P10]
[ro.vendor.mtk.bt_sap_enable]: [true]
[ro.vendor.mtk_aal_support]: [1]
[ro.vendor.mtk_agps_app]: [1]
[ro.vendor.mtk_audio_alac_support]: [1]
[ro.vendor.mtk_audio_ape_support]: [1]
[ro.vendor.mtk_audio_tuning_tool_ver]: [V2.2]
[ro.vendor.mtk_besloudness_support]: [1]
[ro.vendor.mtk_blulight_def_support]: [1]
[ro.vendor.mtk_c2k_lte_mode]: [0]
[ro.vendor.mtk_camera_app_version]: [2]
[ro.vendor.mtk_config_max_dram_size]: [0x80000000]
[ro.vendor.mtk_data_config]: [1]
[ro.vendor.mtk_eccci_c2k]: [1]
[ro.vendor.mtk_embms_support]: [1]
[ro.vendor.mtk_emmc_support]: [1]
[ro.vendor.mtk_exchange_support]: [1]
[ro.vendor.mtk_external_sim_only_slots]: [0]
[ro.vendor.mtk_f2fs_enable]: [1]
[ro.vendor.mtk_fd_support]: [1]
[ro.vendor.mtk_flv_playback_support]: [1]
[ro.vendor.mtk_gps_support]: [1]
[ro.vendor.mtk_log_hide_gps]: [1]
[ro.vendor.mtk_lte_support]: [1]
[ro.vendor.mtk_md1_support]: [9]
[ro.vendor.mtk_md_world_mode_support]: [1]
[ro.vendor.mtk_mdmi_support]: [1]
[ro.vendor.mtk_omacp_support]: [1]
[ro.vendor.mtk_pq_color_mode]: [1]
[ro.vendor.mtk_pq_support]: [2]
[ro.vendor.mtk_protocol1_rat_config]: [Lf/Lt/W/G]
[ro.vendor.mtk_ps1_rat]: [Lf/Lt/W/G]
[ro.vendor.mtk_ril_mode]: [c6m_1rild]
[ro.vendor.mtk_rild_read_imsi]: [1]
[ro.vendor.mtk_telephony_add_on_policy]: [0]
[ro.vendor.mtk_wappush_support]: [1]
[ro.vendor.mtk_wfd_support]: [1]
[ro.vendor.mtk_widevine_drm_l3_support]: [1]
[ro.vendor.mtk_world_phone_policy]: [0]
[ro.vendor.net.upload.benchmark.default]: [blocking]
[ro.vendor.num_md_protocol]: [2]
[ro.vendor.product.cpu.abilist]: [armeabi-v7a,armeabi]
[ro.vendor.product.cpu.abilist32]: [armeabi-v7a,armeabi]
[ro.vendor.product.cpu.abilist64]: []
[ro.vendor.radio.max.multisim]: [ss]
[ro.vendor.rc]: [/vendor/etc/init/hw/]
[ro.vendor.sim_me_lock_mode]: [0]
[ro.vendor.sim_refresh_reset_by_modem]: [1]
[ro.vendor.sys.current_rsc_path]: [/system/etc/rsc/default]
[ro.vendor.system.mtk_dmc_support]: [1]
[ro.vendor.system.mtk_mapi_support]: [1]
[ro.vendor.system.mtk_mdmi_support]: [1]
[ro.vendor.vnd.current_rsc_path]: [/vendor/etc/rsc/default]
[ro.vendor.wfd.dummy.enable]: [1]
[ro.vendor.wfd.iframesize.level]: [0]
[ro.vendor.wifi.sap.interface]: [ap0]
[ro.vendor.wlan.gen]: [gen2]
[ro.vndk.version]: [29]
[ro.wifi.channels]: []
[ro.x.code.branch]: [cellular]
[ro.x.config.dev_pro]: [5,4,5,4,5,48,12.0,#,#,#,2]
[ro.x.product.model]: [A95M]
[ro.zygote]: [zygote32]
[ro.zygote.preload.enable]: [0]
[security.perf_harden]: [1]
[selinux.restorecon_recursive]: [/data/misc_ce/0]
[service.bootanim.exit]: [1]
[service.sf.present_timestamp]: [1]
[setupwizard.theme]: [glif_v3_light]
[sys.boot.reason]: [cold,powerkey]
[sys.boot.reason.last]: [bootloader]
[sys.boot_completed]: [1]
[sys.factory.hardware.info]: [true]
[sys.ipo.disable]: [1]
[sys.ipo.pwrdncap]: [2]
[sys.isolated_storage_snapshot]: [true]
[sys.logbootcomplete]: [1]
[sys.oem_unlock_allowed]: [1]
[sys.rescue_boot_count]: [1]
[sys.retaildemo.enabled]: [0]
[sys.sysctl.extra_free_kbytes]: [5400]
[sys.system_server.start_count]: [1]
[sys.system_server.start_elapsed]: [12462]
[sys.system_server.start_uptime]: [12462]
[sys.usb.config]: [adb]
[sys.usb.configfs]: [1]
[sys.usb.controller]: [musb-hdrc]
[sys.usb.ffs.aio_compat]: [1]
[sys.usb.ffs.ready]: [1]
[sys.usb.state]: [adb]
[sys.use_memfd]: [false]
[sys.user.0.ce_available]: [true]
[sys.wifitracing.started]: [1]
[sys.x.screenoff.timeout]: [1]
[vendor.MB.running]: [0]
[vendor.audiohal.speech.shm_init]: [1]
[vendor.camera.mdp.cz.enable]: [0]
[vendor.camera.mdp.dre.enable]: [0]
[vendor.connsys.driver.ready]: [yes]
[vendor.connsys.formeta.ready]: [yes]
[vendor.debug.pq.acaltm.dbg]: [0]
[vendor.debug.pq.adl.dbg]: [0]
[vendor.debug.pq.cz.isp.tuning]: [0]
[vendor.debug.pq.dre.dbg]: [0]
[vendor.debug.pq.dre.demowin.x]: [536805376]
[vendor.debug.pq.dre.isp.tuning]: [0]
[vendor.debug.pq.dredriver.blk]: [0]
[vendor.debug.pq.dredriver.dbg]: [0]
[vendor.debug.pq.dshp.en]: [2]
[vendor.debug.pq.hdr.dbg]: [0]
[vendor.debug.pq.hdrdriver.dbg]: [0]
[vendor.debug.pq.hfg.isp.tuning]: [0]
[vendor.debug.pq.shp.en]: [2]
[vendor.gsm.gcf.testmode]: [0]
[vendor.gsm.project.baseband]: [TK_MD_BASIC(LWCTG_R3_6739)]
[vendor.gsm.ril.ct3g]: [0]
[vendor.gsm.ril.eboot]: [0]
[vendor.gsm.ril.fulluicctype]: [USIM]
[vendor.gsm.ril.uicc.mccmnc]: [20404]
[vendor.gsm.ril.uicctype]: [USIM]
[vendor.gsm.serial]: [MQXXA95M220810186E MA95M2208005964 PPP10P]
[vendor.gsm.sim.extended.format1]: [0]
[vendor.gsm.sim.retry.pin1]: [3]
[vendor.gsm.sim.retry.pin2]: [3]
[vendor.gsm.sim.retry.puk1]: [10]
[vendor.gsm.sim.retry.puk2]: [10]
[vendor.gsm.sim.ril.phbready]: [true]
[vendor.gsm.sim.ril.testsim]: [0]
[vendor.gsm.sim.slot.lock.card.valid]: [0]
[vendor.gsm.sim.slot.lock.policy]: [0]
[vendor.gsm.sim.slot.lock.service.capability]: [0]
[vendor.gsm.sim.slot.lock.state]: [1]
[vendor.ims.eims.pdn.info]: []
[vendor.mtk.atci.boot_completed]: [1]
[vendor.mtk.md1.status]: [ready]
[vendor.mtk.nvram.ready]: [1]
[vendor.mtk.vdec.waitkeyframeforplay]: [9]
[vendor.mtk_thumbnail_optimization]: [true]
[vendor.mtkcamapp.cshot.platform]: [-1]
[vendor.net.ims.ipsec.version]: [2.0]
[vendor.ril.active.md]: [9]
[vendor.ril.apc.support]: [1]
[vendor.ril.call.emci_support]: [0]
[vendor.ril.cdma.3g.dualact]: [0]
[vendor.ril.cdma.card.type.1]: [2]
[vendor.ril.data.allow_data_slot]: [0]
[vendor.ril.data.gsm_mcc_mnc0]: [20404]
[vendor.ril.data.gsm_spn0]: [00552E532E2043656C6C756C6172FFFFFF]
[vendor.ril.data.legacy_allow_mode]: [-1]
[vendor.ril.data.pdn_info0]: []
[vendor.ril.data.pnn0]: [430D8555D7D4051A96D9EC3A3B2C07]
[vendor.ril.data.preferred_data_mode]: [1]
[vendor.ril.data.ssc.mode]: [3]
[vendor.ril.disable.eboot]: [0]
[vendor.ril.ecc.service.category.list]: []
[vendor.ril.fd.mode]: [1]
[vendor.ril.ipo.radiooff]: [0]
[vendor.ril.mtk]: [1]
[vendor.ril.mux.ee.md1]: [0]
[vendor.ril.mux.report.case]: [0]
[vendor.ril.mux.start]: [0]
[vendor.ril.muxreport.run]: [0]
[vendor.ril.nw.signalstrength.lte.1]: [2147483647,214748364]
[vendor.ril.nw.worldmode.activemode]: [1]
[vendor.ril.nw.worldmode.keep_3g_mode]: [0]
[vendor.ril.rc.session.id1]: [-1]
[vendor.ril.sim.onoff.state1]: [11]
[vendor.ril.sim.onoff.support]: [1]
[vendor.ril.simswitch.no_reset_support]: [1]
[vendor.ril.simswitch.tpluswsupport]: [1]
[vendor.ril.special.ecclist]: []
[vendor.rild.libargs]: [-d /dev/ttyC0]
[vendor.rild.libpath]: [mtk-ril.so]
[vendor.service.nvram_init]: [Ready]
[vendor.trustkernel.fs.mode]: [3]
[vendor.trustkernel.fs.state]: [ready]
[vendor.trustkernel.keybox.deployed]: [true]
[vendor.trustkernel.log.state]: [enable]
[vendor.trustkernel.productionline.state]: [ready]
[vendor.trustkernel.ready]: [true]
[vold.has_adoptable]: [1]
[vold.has_quota]: [1]
[vold.has_reserved]: [1]
[vold.post_fs_data_done]: [1]
[wifi.direct.interface]: [p2p0]
[wifi.interface]: [wlan0]
[wifi.tethering.interface]: [ap0]
[xthink.factorytest.camera_main2_info]: [
]
[xthink.factorytest.camera_main_info]: [
]
[xthink.factorytest.camera_sub2_info]: [
]
[xthink.factorytest.camera_sub_info]: [
]
[xthink.factorytest.chip]: [FT6336d003
]
[xthink.factorytest.emmcvendor]: [1501005145363342420]
[xthink.factorytest.firmware]: [0x05
]
[xthink.factorytest.mtk_fb_panel_name]: [GC9503_CMI
]
Current Battery Service state:
AC powered: false
USB powered: true
Wireless powered: false
Max charging current: 500000
Max charging voltage: 5000000
Charge counter: 998200
status: 2
health: 2
present: true
level: 46
scale: 100
voltage: 4108
temperature: 351
technology: Li-ion
UNLOCK.MX
comando adb # ls - la
Comandos adb
Serrano
C:\adb
λ adb shell
1|HPP-L55B:/ $ ls -la
ls: ./init.rc: Permission denied
ls: ./init.usb.rc: Permission denied
ls: ./ueventd.rc: Permission denied
ls: ./init.zygote32.rc: Permission denied
ls: ./init: Permission denied
ls: ./init.environ.rc: Permission denied
ls: ./init.usb.configfs.rc: Permission denied
ls: ./metadata: Permission denied
total 68
drwxr-xr-x 21 root root 4096 2008-12-31 19:00 .
drwxr-xr-x 21 root root 4096 2008-12-31 19:00 ..
dr-xr-xr-x 80 root root 0 2009-12-31 19:01 acct
drwxr-xr-x 16 root root 320 2009-12-31 19:01 apex
lrw-r--r-- 1 root root 11 2008-12-31 19:00 bin -> /system/bin
lrw-r--r-- 1 root root 50 2008-12-31 19:00 bugreports -> /data/user_de/0/com.android.shell/files/bugreports
drwxrwx--- 6 system cache 4096 2022-04-30 00:16 cache
lrw-r--r-- 1 root root 19 2008-12-31 19:00 charger -> /system/bin/charger
drwxr-xr-x 4 root root 0 1969-12-31 19:00 config
lrw-r--r-- 1 root root 17 2008-12-31 19:00 d -> /sys/kernel/debug
drwxrwx--x 52 system system 4096 2022-04-29 23:59 data
drwxr-xr-x 2 root root 4096 2008-12-31 19:00 debug_ramdisk
lrw------- 1 root root 23 2008-12-31 19:00 default.prop -> system/etc/prop.default
drwxr-xr-x 21 root root 4360 2009-12-31 19:01 dev
lrw-r--r-- 1 root root 11 2008-12-31 19:00 etc -> /system/etc
drwx------ 2 root root 16384 2008-12-31 19:00 lost+found
drwxr-xr-x 13 root system 280 2009-12-31 19:01 mnt
drwxr-xr-x 2 root root 4096 2008-12-31 19:00 odm
drwxr-xr-x 2 root root 4096 2008-12-31 19:00 oem
dr-xr-xr-x 467 root root 0 1969-12-31 19:00 proc
drwxr-xr-x 11 root root 4096 2008-12-31 19:00 product
lrw-r--r-- 1 root root 24 2008-12-31 19:00 product_services -> /system/product_services
drwxr-x--- 2 root shell 4096 2008-12-31 19:00 sbin
lrw-r--r-- 1 root root 21 2008-12-31 19:00 sdcard -> /storage/self/primary
drwxr-xr-x 4 root root 100 2022-04-29 23:59 storage
dr-xr-xr-x 15 root root 0 2009-12-31 19:01 sys
drwxr-xr-x 13 root root 4096 2008-12-31 19:00 system
drwxr-xr-x 12 root shell 4096 2008-12-31 19:00 vendor
Best Regard
UNLOCK.MX
MWORKER Tool Motorola G POWER 2021 XT2117-1 Cricket Unlock Done
Unlock Done
35 Creditos - MWORKER TOOL
Motorola G POWER 2021 XT2117-1 Cricket
Starting Factory Enabler process...
Waiting for device in Fastboot Mode....Done.
Reading Data....Done
UNLOCK.MX....Done
Firmware: RZBS31.Q2-143-27-4
Android: 11
CPU: SM_KAMORTA_H 1.0
Model: XT2117-1
SN: ZD2223P8JP
IMEI: 3510165622XXXXX
Channel ID: 0x89
Carrier: cricket
Factory Mode: disabled
Reading Data ... Done
Creating Order ID....Done
Operation ID: 1591488
Sending Data to Server ... Done
Setting Factory Mode ... Done
Rebooting Phone ... Done
Elapsed Time: 0:15.08
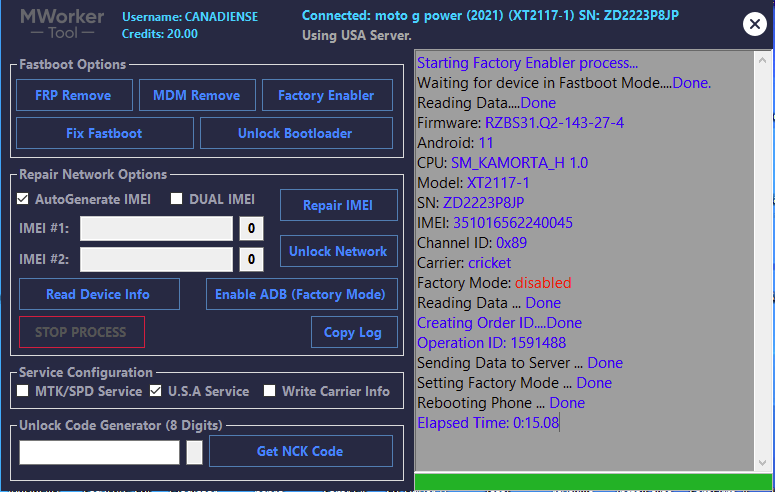
Waiting for Device in Factory Mode.....Found!
Reading Data...Done
UNLOCK.MX....Done
FSG: BORNEO_NA_CUST
Firmware: RZBS31.Q2-143-27-4
Android Version: 11
Model: G POWER (2021)
SKU: XT2117-1
SN: ZD2223P8JP
IMEI 1: 3510165622XXXXX
Carrier: cricket
Creating Order ID....Done
Operation ID: 1591492
Erasing UTAG IMEI ... Done
Reading Device Configuration ... Done
Wiping IMEI ... Done
Writing New Security ... Done.
Writing IMEI ... Done
New IMEI 1: 3510165622XXXXX
Writing New Security ... Done.
Writing UTAG IMEI ... Done
Erasing Factory Mode ... Done
Rebooting to Fastboot ... Done
Elapsed Time: 0:38.88
UNLOCK.MX & MULTI-UNLOCK.COM
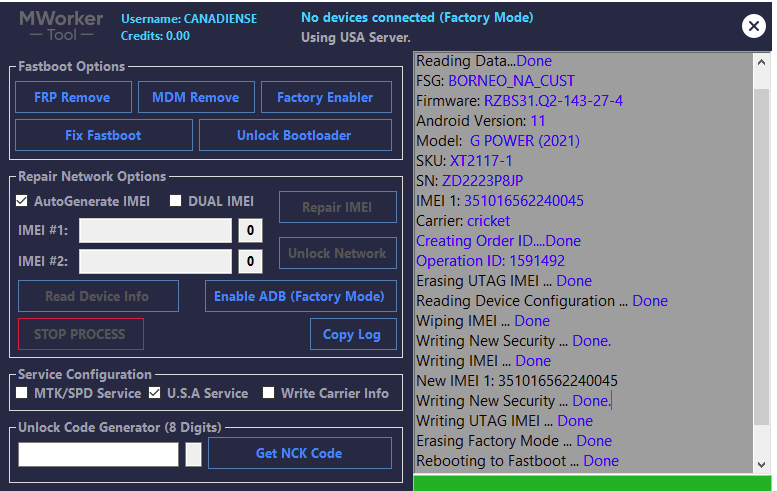
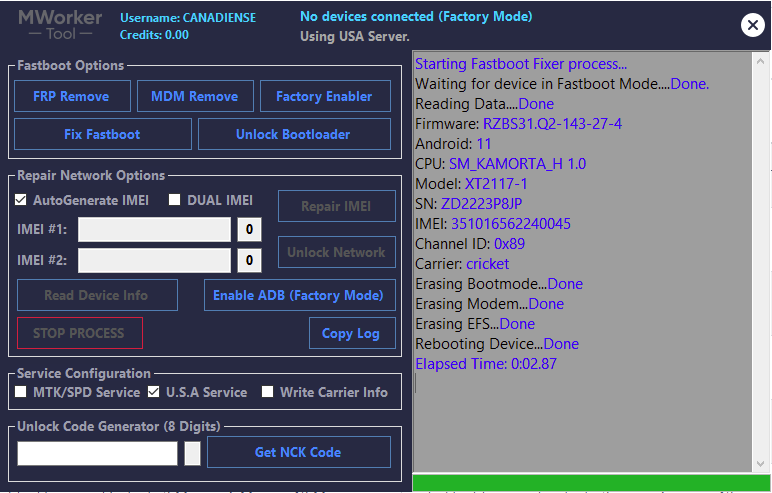
Motorola E32 XT2227-1 FRP al Instante by Unlocktool
FORMAT DATA Selected Platform : Tiger T606_64_Bypass
Waiting for device... COM14 (SPRD U2S Diag)
USB : USB\VID_1782&PID_4D00\5&14A7B65B&0&1
Initializing loader... OK
Protocol : SPRD3
Unlock.Mx .... OK
Sending payload... OK
Sending auth data... OK
Sending preloader1... OK
Sending preloader2... OK
Booting loader, please wait... OK
Boot ver: Spreadtrum Boot Block version 1.1
Sending FDL1... OK
Sending FDL2... OK
Reading partitions info... OK
Reading device info... OK
Model Name : moto e32
Product Name : hawaii
Manufacturer : motorola
Android Version : 11
Security Patch : 2023-01-05
Build ID : RORS31.335-20-2 release-keys
Build Date : Tue Jan 3 15:58:16 CST 2023
Erasing FRP... OK
Erasing USERDATA... OK
UNLOCKTOOL 2023.05.25.0
Elapsed time : 22 seconds
Venta de creditos y Activaciones
UNLOCK.MX & MULTI-UNLOCK.COM
Desde 2006
Whatsapp: +523781040103
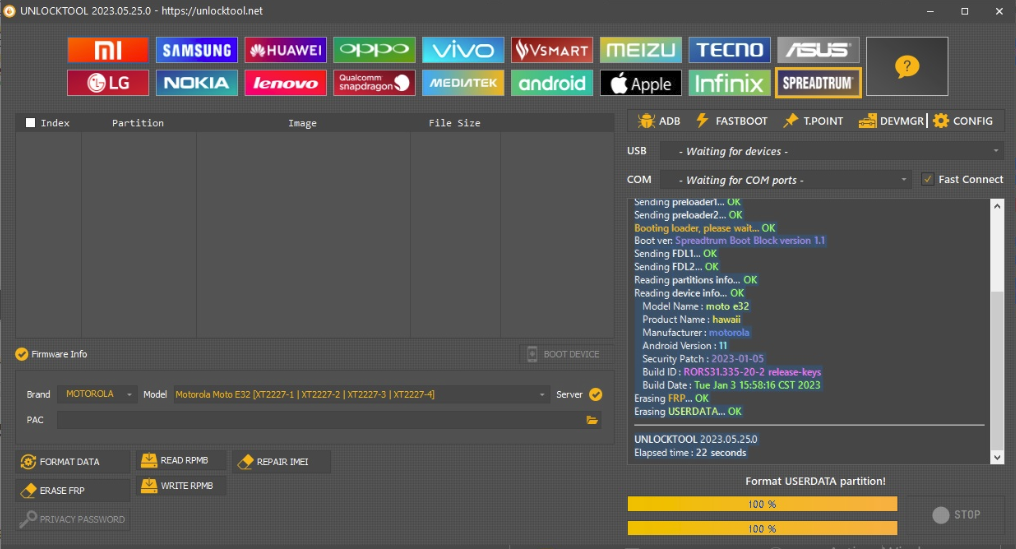
FRP Motorola MOTO G PLAY 2023 XT2271-5 al instante
Aqui les dejo como quitar cuenta google en segundos
Presionar volumen abajo + Insertar cable USB para ponerlo en fastboot
Start FRP Unlock Task on 25/05/2023 3:47:41 PM -07:00
Waiting for device arrival.... OK
Model SKU: XT2271-5
Carrier: RETUS
Serial: ZY22GJSLVX
Authorizing FRP Access...OK
Reboot bootloader...OK
Waiting for device arrival.... OK
Erasing FRP...OK
Erasing UserData...OK
Erasing Cache...OK
Final Step...OK
Rebooting...OK
FRP Unlock Task Successful!
Venta de creditos en WWW.UNLOCK.MX para quitar cuenta google
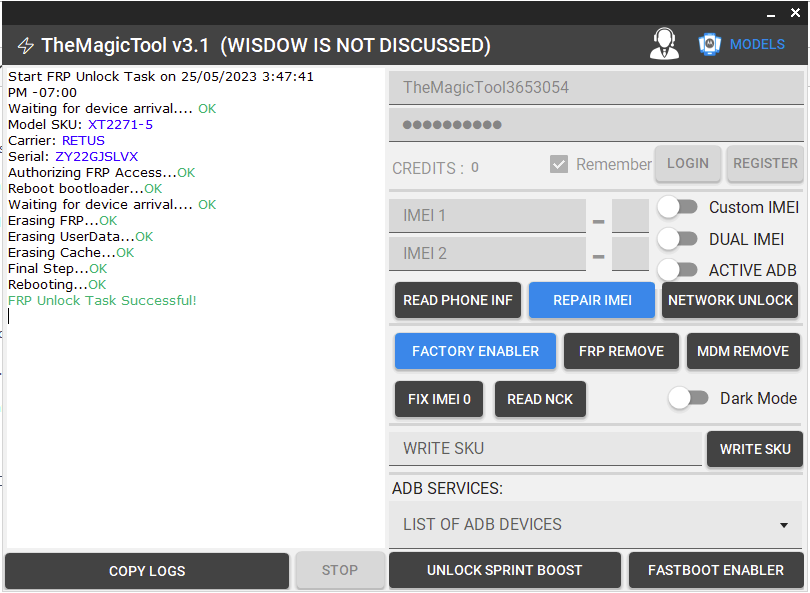
Samsung SM-G950U S8 Read Unlock Code by Samkey al Instante
Venta de Codigos para Sameky en Unlock.mx
Searching for SAMSUNG Mobile USB Modem...OK
SAMSUNG USB Modem detected on [COM17]
Looking for DEVICE.....OK
Reading USB MODEM information...OK
MODEL : SM-G950U
VER : G950USQS8DTJ1/G950UOYN8DTJ1/G950USQS8DTJ1/G950USQS8DTJ1
IMEI : 35772308000XXXX
S/N : R38J307AX7
U/N : 988829344639364
Algorithm : MSM Crypto Engine
Loading ADB module.OK
Starting ADB module...OK
Searching for SAMSUNG ADB device...OK
Checking device authorization...OK
Reading ADB device information...
Device Model : SM-G950U
ADB Serial Number : 988829344639364538
AP Ver : G950USQS8DTJ1
CP Ver : G950USQS8DTJ1
CSC Ver : G950UOYN8DTJ1
Carrier : ATT
Android Ver : 9
RIL Type : Android 9 New SDK
Country : USA
Shipping : ATT
IMEI : 35772308000XXXX
Debug Level : HIGH [0X4948]
CP Debug Level : OK [0X5500]
Setting USB Settings to [diag,acm,adb] automatically...OK
Searching for SAMSUNG Diagnostic Port...[COM19]...OK
QC SW Rev : MPSS.AT.2.0.c5-00769-8998_GEN_PACK-1.327187.1
Release : Oct 7 202010:07:26Aug 25 202007:00:008998
Checking DIAG security...[COM19]...OK
Waiting for UPLOAD MODE...[COM21]...OK
Preparing to read data...OK
Reading RAM data...[S1:OK]..[N3:OK]....[N4:OK]...OK
Rebooting device to NORMAL mode...OK
Searching HASH signature...[HSU:NA]...SKIP
Searching security HMAC...[CRT:NA]...OK
Calculating...[IDX0:OK]...[HASH:OK]...[PLN:NA]...OK
Validating security data...OK
Sending data to SERVER...OK
Waiting for SERVER response (May take few minutes)...OK
SamKEY Team (2017-2022)
MULTI-UNLOCK.COM & UNLOCK.MX
FRP Samsung *#0*#
Bajar Software desde este links de cualquiera de los dos pueden
https://www.mediafire.com/file/552rnm5hzqrw2lw/SamFwToolSetup_v4.4.zip/file
Despues de instalar el software ocupan ir a esta url
C:\SamFwTool\data
buscar el archivo adb.exe lo seleccionan copiar y pegar lo van a renombrar la copia en adbsl.exe para que pueda abrir el software SamFwTool
SamFw Tool 4.4
[XIAOMI]
[EDL 9008] - Add support Blackshark 3, Mi Max 2, Mi Max 3, Mi 6, Mi 6X, Mi 8, Mi Mix 2, Mi Pad 4, Redmi Note 5/6/7, Redmi S2
- Add support Factory reset/Reset FRP/Reset Micloud
- Fix Windows 7 error
- Optimize execute size
- Update new C++ download links
- Fix some bugs
No device selected
Using port SAMSUNG Mobile USB Modem #6 (COM16)
Reading info mode MTP ... OK
Model : SM-J327T1
CSC : TMK
AP version : J327T1UVS4ASH2
BL version : J327T1UVS4ASH2
CP version : J327T1UVS4ASH2
CSC version : J327T1TMK4ASH2
IMEI : 3556030888XXXXX
SN : R28J527RSPT
Lock status : NONE
MCC : 334
MNC : 020
USB mode : AT,MTP
Unique number : CQ300934BE0BE44
Android version : 7.0
FRP status : LOCKED
Firmware : https://samfw.com/firmware/SM-J327T1/TMK
Using port SAMSUNG Mobile USB Modem #6 (COM16)
Sending ADB exploit (normal)... OK
Sending ADB exploit (normal)... OK
Sending ADB exploit (normal)... OK
Sending ADB exploit (normal)... The port 'COM16' does not exist.
OK
Please click to the allow USB Debugging on the screen. If not apprear, unplug and replug the cable
Waiting for device
Removing... OK
MULTI-UNLOCK.COM & UNLOCK.MX
UnlockTool Licencia al Instante 3 Meses - 6 Meses - 12 Meses
Activacion de UnlockTool al Instante
Licencia
- 3 Meses $ 422.08 MXN
- 6 Meses $ 609.08 MXN
- 12 Meses $ 938.81 MXN
El Mejor precio lo encontraras con nosotros

UNLOCK.MX & MULTI-UNLOCK.COM
IMSI CODE FULL LIST
IMSI CODE
MAIN COUNTRIES CARRIER IMSI CODE LIST
| Spectrum 2040438 or 3115803 or 3134500 Viaero 3104500 Sprint(CDMA) 3160101 3160100 Gci 3113700 Cable&Wireless Lime 3461401 GSM/vzw 3101500 Sprint 3101200 Cricket 3101500 Virgin 3160101 Straight Talk 2040400 T-Mobile iPhone5 3102605 Wireless Alaska 3113700 T-Mobile 3102620 Tracfone 3114801 MetroPCS 3102600 Total Wireless 3114803 Consumer Celullar 3115804 Straight Talk 3114801 Boost Mobile 3160101 3160100 Xfinity2040438 US Cellular 3115801 TracFone/Straight talk 3114801 At&t USA 3104101 Cricket 3101508 T-Mobile 3102605 Sprint 3101200 Verizon/Xfinity 2040400,2040438 GCI 3113700 Claro puerto rico 3301104 | |||||
| COUNTRY | NETWORK | IMSI 1 | IMSI 2 | IMSI 3 | IMSI 4 |
| Albania | Albanian Mobile | 2760111 | |||
| Albania | Eagle Mobile | 2760311 | |||
| Albania | Vodafone | 2760211 | |||
| Albania | Plus Al | 2760411 | |||
| Algeria | AlgeTel | 6030111 | |||
| Algeria | Nedjma | 6030311 | |||
| Algeria | Orascom | 6030211 | |||
| Andorra | mobiland | 2130311 | |||
| Angola | Unitel | 6310211 | |||
| Anguilla | Cabl&wi | 3654011 | |||
| Anguilla | Mossel | 3650511 | |||
| Anguilla | Weblink | 3651011 | |||
| Argentina | Claro | 7161003 | |||
| Argentina | compala | 7161003 | |||
| Argentina | CTI | 7223101 | |||
| Argentina | Movistar | 7220104 | |||
| Argentina | Nextel | 7220211 | |||
| Argentina | Nextel2 | 7222011 | |||
| Argentina | Telecom | 7223411 | |||
| Argentina | Telefoni | 7220711 | |||
| Argentina | Telfonic | 7227011 | |||
| Armenia | Armentel | 2830134 | |||
| Armenia | Karabakh | 2830434 | |||
| Armenia | Orange | 2831034 | |||
| Armenia | Vivacell | 2830534 | |||
| Australia | 3 | 5050610 | |||
| Australia | Optus | 5050210 | |||
| Australia | Vodafone | 5050390 | |||
| Australia | 3GIS | 5051570 | |||
| Australia | AAPT | 5051470 | |||
| Australia | Advan | 5052470 | |||
| Australia | Localstar | 5058870 | |||
| Australia | One | 5050870 | |||
| Australia | OZITEL | 5050534 | |||
| Australia | Telstra71 | 5057170 | |||
| Australia | Telstra72 | 5057270 | |||
| Australia | Telstra11 | 5051170 | |||
| Australia | Telstra | 5050134 | |||
| Austria | 3Hutch | 2321070 | |||
| Austria | A1 Telekom | 2320170 | 2320100 | 2320186 | |
| Austria | Barabl | 2321570 | |||
| Austria | BobA1 | 2321170 | |||
| Austria | OneOra | 2320570 | |||
| Austria | Teleri | 2320770 | |||
| Austria | T-mobi le | 2320370 | 2320328 | ||
| Austria | yesOra | 2321270 | |||
| Austria | Orange | 2320588 | |||
| Austria | Three | 2321069 | |||
| Aux-Airnet | Airnet | 5050970 | |||
| Aux-Depart | Depart | 5050434 | |||
| Belarus | Best | 2570434 | |||
| Belarus | MDC | 2570134 | |||
| Belarus | MTS | 2270234 | |||
| Belgium | Base | 2061034 | |||
| Belgium | Globul | 2060534 | |||
| Belgium | mobistar | 2061034 | |||
| Belgium | Proximus | 2060134 | 2060122 | ||
| Belgium | Ortel | 2062050 | |||
| Bulgaria | MTel | 2840179 | 2840189 | ||
| Bulgaria | Vivacom | 2840310 | |||
| Bulgaria | Globul | 2840510 | 2840500 | ||
| Canada | BELL610 | 3026104 | |||
| Canada | Bellpacific | 3101703 | 3026103 | ||
| Canada | Fido | 3023704 | 3023703 | ||
| Canada | Rogers | 3027204 | 3027203 | ||
| Canada | Telus220 | 3022204 | 3022203 | ||
| Canada | MTS | 3026600 | |||
| Canada | Virgin | 3026102 | |||
| CGI | USA | 3113700 | |||
| Chile | Claro | 7300304 | |||
| Chile | Entel | 7300104 | |||
| Chile | Entel10 | 7301004 | |||
| Chile | Movistar | 7300204 | |||
| China | Mobile | 4600202 | |||
| China | Unicom | 4600158 | |||
| China | Telecom China | 2040438 | |||
| Colombia | ColomTel | 7320014 | |||
| Colombia | Comcel | 7321014 | |||
| Colombia | Edatel | 7320024 | |||
| Colombia | Movista3 | 7321234 | |||
| Colombia | Movistar | 7321024 | |||
| Colombia | Tigo1 | 7321114 | |||
| Colombia | Tigo3 | 7321034 | |||
| Croatia | T-Mobile | 2190199 | |||
| Croatia | VIP | 2191065 | |||
| Czech | Mobikom | 2300434 | |||
| Czech | O2telefh | 2300234 | |||
| Czech | Sprava | 2309834 | |||
| Czech | Tmobi | 2300134 | |||
| Czech | Vodafone | 2300334 | |||
| Czech | Vodaf2 | 2309934 | |||
| Denmark | TM | 2620125 | |||
| Denmark | Demark | 2382010 | |||
| Denmark | APS | 2380534 | |||
| Denmark | Barablu | 2380734 | 2380734 | ||
| Denmark | H3G | 2380634 | |||
| Denmark | 3 | 2380632 | |||
| Denmark | Telen | 2380241 | |||
| Denmark | MiGway | 2380334 | |||
| Denmark | TDC | 2380134 | |||
| Denmark | TDC2 | 2381034 | |||
| Denmark | Telenor | 2387734 | 2380234 | ||
| Denmark | Telia | 2382034 | |||
| Denmark | Telia30 | 2383034 | |||
| Dominican | Movil | 7321234 | |||
| Ecuador | Alegro | 7400234 | |||
| Ecuador | Movista | 7400034 | |||
| Ecuador | Porta | 7400134 | |||
| Egypt | Mobinil | 6020111 | 8920016 | ||
| Egypt | Vodafone | 6020211 | |||
| Egypt | Etisalat | 6020311 | |||
| El Salvador | Claro/CTE | 7061034 | |||
| El Salvador | CTE/Claro | 7060134 | |||
| El Salvador | Digice | 7060234 | |||
| El Salvador | Movita | 7060434 | |||
| El Salvador | Telemo | 7060334 | |||
| Estonia | EMT | 2480134 | |||
| Finland | NDA | 2440311 | 2441211 | 2440367 | |
| Finland | Sonera | 2449111 | |||
| France | Bouygues | 2082136 | 2082015 | ||
| France | BT | 2082031 | |||
| France | Orange | 2080189 | 2080131 | ||
| France | Bouygues20 | 2082011 | |||
| France | Bouygues21 | 2082111 | |||
| France | Bouygues88 | 2088811 | |||
| France | Orange01 | 2080111 | |||
| France | Orange02 | 2080211 | |||
| France | SFR10 | 2081011 | |||
| France | SFR11 | 2081111 | |||
| France | SFR | 2081031 | |||
| France | SFR | 2081003 | |||
| France | Virgin | 2080191 | |||
| Germany | T-mobile | 2620111 | 2620125 | 2620155 | 2620166 |
| Germany | Vodafone | 2620208 | |||
| Greece | Cosmote | 2020134 | |||
| Greece | QTelecom | 2020934 | |||
| Greece | Vodafone | 2020534 | |||
| Greece | Wind | 2021034 | |||
| Honduras | Claro | 7080111 | |||
| Hungary | T-mobile | 2163011 | 2163000 | ||
| Hungary | Vodafone | 2167000 | |||
| India | Airtel02 | 4040211 | |||
| India | Vodaf01 | 4040111 | |||
| India | Vodaf05 | 4040511 | |||
| India | Vodaf46 | 4044611 | |||
| Ireland | Vodafone | 2720110 | 2720172 | ||
| Ireland | O2 | 2720211 | 2720231 | ||
| Ireland | E-Mobile | 2720320 | |||
| Ireland | Meteor | 2720303 | |||
| Ireland | 3 | 2720500 | 272536 | ||
| Italy | Blu | 2229834 | |||
| Italy | Elsacom | 2220234 | |||
| Italy | H3G | 2229934 | |||
| Italy | IPSE | 2227734 | |||
| Italy | Telecom | 2220134 | |||
| Italy | TIM | 2220134 | 2220195 | ||
| Italy | Vodafone | 2221034 | |||
| Italy | Wind | 2228834 | |||
| Japan | AU Kiddi 4s | 4540492 | |||
| Japan | AU Kiddi 5g | 4405000 | |||
| Japan | Softbank 4s/5g | 4402081 | |||
| JAPAN | AU KDDI iPhone5 | 4405014 | 4405000 | ||
| Jordan | Orange | 4167711 | |||
| Korea | Telecome | 4500826 | |||
| Liechtenstein | Orange | 2950211 | |||
| Liechtenstein | Swisco | 2950111 | |||
| Lithuania | OMNITEL | 2460165 | |||
| Lithuania | OMNITEL | 2460165 | |||
| Luxembourg | Luxgsm | 2700101 | |||
| Luxembourg | Tango | 2707701 | |||
| Luxembourg | Voxmobi | 2709901 | |||
| Macao | China | 4550234 | |||
| Macao | CMT | 4550134 | |||
| Macao | Hutchis | 4550534 | |||
| Macao | SmartT | 4550034 | |||
| Macedonia | Vip | 2940387 | |||
| Macedonia | One(Ex-Cosmofon) | 2940200 | |||
| Macedonia | T-Mobile | 2940102 | |||
| Mexico | Telcel | 3340202 | 3340200 | 3340300 | |
| Mexico | Nextel | 3340100 | |||
| Mexico | Lusacell | 3340500 | |||
| Mexico | Movistar | 3340300 | |||
| Mexico | America Movil | 3340202 | |||
| Moldova | Orange | 2590101 | |||
| Montenegro | T-Mobile | 2970200 | |||
| Netherland | T-Mobile | 2041611 | |||
| Netherland | Reserve | 5300134 | |||
| Netherland | Vodafone | 2040438 | |||
| New Zeland | Econet | 5302834 | |||
| New Zeland | Nzcomunic | 5302434 | |||
| New Zeland | Telecom | 5300534 | |||
| New Zeland | Teltracle | 5300434 | |||
| New Zeland | Vodafone | 5300134 | 5300166 | ||
| New Zeland | Woosh | 5300334 | |||
| Norway | Netcom | 2420211 | |||
| Norway | Telenor | 2420111 | |||
| Norway | Tele2 | 2400768 | |||
| Peru | Claro | 7161011 | |||
| Peru | TIM | 7161011 | |||
| Philipine | GB | 5150220 | |||
| Philipine | SM | 5150303 | |||
| Philipine | Sun | 5150509 | |||
| Philipine | Globe | 5150211 | |||
| Poland | Era | 2600211 | |||
| Poland | Orange | 2600311 | 2600300 | ||
| Poland | T-Mobile | 2600200 | |||
| Portugal | Optimus | 2680311 | |||
| Portugal | Vodafone | 2680111 | |||
| Portugal | TMN | 2680611 | |||
| Romania | Vodafone | 2260107 | |||
| Romania | Orange | 2261007 | |||
| Romania | Cosmote | 2260307 | |||
| Romania | ZAPP | 2260407 | |||
| Russian | Beeline28 | 2502834 | |||
| Russian | Beeline99 | 2509934 | |||
| Russian | Megafon | 2500234 | |||
| Russian | MTS10 | 2501034 | |||
| Russian | Telecom | 2509334 | |||
| SaudiArabia | EAE | 4200734 | |||
| SaudiArabia | Mobily | 4200334 | |||
| SaudiArabia | STC | 4200134 | |||
| SaudiArabia | ZainSA | 4200434 | |||
| Slovakia | T-Mobile 2 | 2310411 | |||
| Slovakia | Eurotel 2 | 2310234 | |||
| Slovakia | Orange | 2310134 | |||
| Slovakia | Orange UMT | 2310534 | |||
| Slovakia | Orange UMT2 | 2311534 | |||
| Slovakia | TeleficO2 | 2310634 | |||
| Slovakia | Vodacom | 6550134 | |||
| Slovenia | Si-Mobile | 2934001 | |||
| Spain | Movistar | 2140711 | 2140785 | ||
| Spain | Orange | 2140333 | |||
| Spain | Vodafone | 2140198 | 2140130 | ||
| Spain | Yoigo | 2140401 | |||
| Sweden | 3 | 2400200 | 2400232 | ||
| Sweden | Telia | 2400111 | |||
| Sweden | Tele2 | 2400700 | 2400782 | ||
| Sweden | Telia | 2400100 | 2400111 | ||
| Sweden | Telenor | 2400885 | |||
| Switzerland | Swisscom | 2280167 | |||
| Switzerland | Orange | 2280311 | 2280300 | ||
| Switzerland | Sunrise | 2280200 | |||
| Switzerland | Swiscom | 2280111 | |||
| Switzerland | Sunrise | 2280211 | 2280167 | 2280203 | |
| Switzerland | Swiscom (unoffical) | 2280121 | |||
| Taiwan | Chungwa | 4669234 | |||
| Turkey | Turcell | 2860134 | |||
| Turkey | Vodafone | 2860211 | |||
| Turkey | Vodafone | 2862034 | |||
| UAE | DU | 4240334 | |||
| UAE | ETisal | 4240234 | |||
| UK | 3 | 2342091 | 2342073 | ||
| UK | O2 | 2341091 | |||
| UK | Orange/T-Mobile | 2343320 | 2343091 | 2343302 | |
| UK | Vodafone 2 | 2341590 | |||
| UK | O2 – 2 | 2340211 | |||
| UK | Orange33 | 2343334 | |||
| UK | T-Mobile | 2343091 | 2343302 | ||
| UK | Orange | 2343091 | 2343302 | ||
| UK | EE | 2343091 | 2343302 | ||
| UK | Vectone | 2340100 | |||
| Uruguay | CTimov | 7481011 | |||
| Uruguay | Movistar | 7480711 | |||
| Uruguay | Antel | 7480111 | |||
| USA | AT&T | 3104101 | |||
| USA | Verizon | 2040400 | |||
| USA | Sprint(CDMA) | 3160101 | 3160100 | ||
| USA | Cable&Wireless Lime | 3461401 | |||
| USA | Sprint iPhone5 | 3101200 | |||
| USA | Cricket | 2040400 | |||
| USA | Virgin iPhone5 | 3101200 | 3160101 | ||
| USA | Straight Talk | 2040400 | |||
| USA | T-Mobile iPhone5 | 3102605 | |||
| USA | Wireless Alaska | 3113700 | |||
| USA | T-Mobile | 3102620 | |||
| USA | Tracfone | 3114801 | |||
| USA | MetroPCS | 3102600 | |||
| USA | Total Wireless | 3114801 | |||
| USA | Consumer Celullar | 3104101 | 3102620 | ||
| USA | Straight Talk | 3114801 | |||
| USA | Boost Mobile | 3160101 | 3160100 | ||
| USA | Xfinity | 2040400 | |||
| Venezuela | Movistar | 7340486 | |||
| Venezuela | Digitel | 7340100 | 7340200 | 7340300 | |
| Venezuela | Movilnet | 7340600 | |||
| Venezuela | Telefonica | 7340400 |
KEY Tool creditos al instante
Venta de creditos para Key Tool Samsung
KEY-TOOL [ Samsung ] Direct UnLock / Change CSC
MULTI-UNLOCK.COM & UNLOCK.MX
Z3X Box Server Creditos al instante
Venta de creditos para liberar via SERVER
- Refill credits
- 30 Credits Packs
- 50 Credits Packs
Z3X BOX Server Credits Powered by Z3X [30,50 Credits Packs]
MULTI-UNLOCK.COM & UNLOCK.MX
General Unlocker Creditos al Intante
General Unlocker Venta de creditos al instate
GENERAL UNLOCKER PRO
MULTI-UNLOCK.COM & UNLOCK.MX
NCK BOX DONGLE Activation al Instante
Venta de activation 12 Meses NCK BOX & DONGLE
NCK BOX/DONGLE 1 YEAR ACTIVATION
MULTI-UNLOCK.COM & UNLOCK.MX
UMT ULTIMATE MULTI TOOL Activation al Instante
Venta de Activacion 12 Meses
UMT [ULTIMATE MULTI TOOL 1 YEAR ACTIVATION]
MULTI-UNLOCK.COM & UNLOCK.MX
MAGICTOOL Creditos al Instante
Magic Tool Creditos
TOOL PRICES
- REPAIR IMEI 15 CRD
- NETWORK UNLOCK 15 CRD
- FACTORY ENABLE FREE
- FRP PHONE 5 CRD
- MDM PHONE 5 CRD
- READ NCK 1 CRD
- FIX IMEI 0 FREE
- WRITE SKU FREE
MAGICTOOL CREDITS - [ Repair IMEI, Factory Enable, MDM ,FRP , UNLOCK]
MULTI-UNLOCK.COM & UNLOCK.MX
GuerraTool Creditos al Instante
Necesitas creditos en unlock.mx te los entregamos al instante
Guerra Tool
Motorola MTK/SPD
- Repair IMEI
- Frp Phone
- Network Unlock
- Read Nck
- MDM Phone
MULTI-UNLOCK.COM & UNLOCK.MX
EVTOOL Activation al Instante
Activación Software EVTOOL al instante
- Licencia 3 Meses
- Licencia 6 Meses
- Licencia 12 Meses
EVTOOL ACTIVATION - XIAMOI,OPPO,REALME,VIVO [ERASE FRP,UNLOCK BOOTLOADER,FACTORY RESET,REAPIR NETWORK]
MULTI-UNLOCK.COM & UNLOCK.MX
Global Unlocker Pro Creditos al Instante
Venta de creditos Global Unlocker Pro entregamos al instante
- Samsung
- LG
- Motorola
- Alcatel
- TINNO
- Google Pixel
- 1+ ONEPLUS
- ZTE
- CooldPad
- Wiko
- MEDIATEK
- FIH
- DISH
- XIAOMI
- T-MOBILE
- NOKIA
Unlock , Repair , Bypass
Just One Click
professional skills Not needed.
MULTI-UNLOCK.COM & UNLOCK.MX
T-Unlock Creditos al Instante
Venta de Creditos al instante T-Unlock Software
- TINNO
- LG
- MOTOROLA
- SAMSUNG
- ZTE
- 1+ ONE PLUS
★★★★★Direct UnLock★★★★★
MULTI-UNLOCK.COM & UNLOCK.MX
Lista de Herramientas JTAG ★★★★★
- EASY JTAG PLUS
- RIFF BOX V2 BY LEGIJA
- Octoplus Pro Jtag
- Medusa Pro Jtag
- ORT JTAG Pro Edition
- UFI UFS ToolBox
eMMC, Jtag, ISP, SPI, NAND protocols, UFS Chip, forensic tools.
MULTI-UNLOCK.COM & UNLOCK.MX
Contactanos
Ing. Francisco Morales
Celular/WhatsApp: 3781040103
Location: Jalisco
Ventas Unlock.mx : 3781040103
+ 15,000 Clientes atendidos desde 2006 en todo México - América del Sur - USA - Canadá - Europa - Asia
MULTI-UNLOCK.COM desde 2006
UNLOCK.MX desde 2009
SamKEY MTK Direct Unlock and Repair Dead Phones by one click
Venta de Creditos en www.unlock.mx registrate para poder comprar
SamKEY MTK Does NOT Require TestPoint Anymore
ALL SUPPORTED MODELS WITHOUT TESTPOINT
SAFE & UP TO DATE
What's New v1.08.5
- Added definition for NEW UNSUPPORTED DEVICES/FIRMWARES:
- S127DL : S127DLUDU6CVG4, S127DLUDS7CVI1 and newer...
- S326DL : S326DLUDU7BVI1 and newer...
- A037U : A037USQS3BVI2 and newer (XAU, APP, AIO Only)
- A136U : A136USQS3BVI1 and newer (XAU, APP, AIO Only)
- A215U : A215USQS8CVI6 and newer (XAU, APP, AIO Only)
What's New v1.07.5
- Added support for A326U, A326U1, S326DL WITHOUT TESTPOINT
What's New v1.06.5
- Added support for S326DL (Galaxy A32 5G) FULL PERMANENT UNLOCK
- Added support for A326U, A326U1 (Galaxy A32 5G) ATT, CHA, CCT FULL PERMANENT UNLOCK
- Added support for A326U, A326U1 (Galaxy A32 5G) TMB, TMK, APP, VZW, AIO, BST, SPR, DSH (MUST ENTER 16 ZERO's AT EVERY POWER UP)
- Added support for A037F, A037M (Galaxy A03s) FULL PERMANENT UNLOCK
- Added support for A136U, A136U1 (Galaxy A13 5G) TMB, TMK, APP, VZW, AIO (MUST ENTER 0000000000000000 CODE AT EVERY POWER UP)
- Added support for A215U, A215U1 (Galaxy A21) TMB, TMK, APP, VZW, AIO (MUST ENTER 0000000000000000 CODE AT EVERY POWER UP)
- Added support for A037U, A037U1 (Galaxy A03s) TMB, TMK, APP, VZW, DSH, AIO (MUST ENTER 0000000000000000 CODE AT EVERY POWER UP)
- Added support for T227U (Galaxy Tab A7 Lite) XAU, TMB, TMK, AIO, DSH, VZW (MUST ENTER 0000000000000000 CODE AT EVERY POWER UP!
History:
- Added support for A136U (Galaxy A13) CCT, ATT, CHA FULL PERMANENT UNLOCK
- Added support for T227U (Galaxy Tab A7 Lite) CCT, ATT, CHA FULL PERMANENT UNLOCK
- Added support for A037U (Galaxy A03s) CCT, ATT, CHA FULL PERMANENT UNLOCK
- Added support for A037U1 (Galaxy A03s) CCT, ATT, CHA, BAA FULL PERMANENT UNLOCK
- Added support for A125U (Galaxy A12) ALL CARRIERS FULL PERMANENT UNLOCK
- Added support for A125U1 (Galaxy A12) ALL CARRIERS FULL PERMANENT UNLOCK
- Added support for A215U (Galaxy A21) CCT, ATT, CHA FULL PERMANENT UNLOCK
- Added support for A215U1 (Galaxy A21) CCT, ATT, CHA, BAA FULL PERMANENT UNLOCK
- Added support for S127DL (Galaxy A12) FULL PERMANENT UNLOCK
- Added support for S215DL (Galaxy A21) FULL PERMANENT UNLOCK
Attention : NEVER DELETE BACKUP FOLDER! SamKEY Team take no responsibility if BACKUP folder delete!
Attention :
It is obligatory to keep minimum of 5 credits in your account in order to use Restore and Repair functions, But they consume 0 credit.
WARNING : IF YOU TRY UN-SUPPORTED MODEL BY SAMKEY MTK, WE WILL NEVER REFUND!
DOWNLOAD TUTORIAL (How to Fix MTK Drivers)
(LibUsb - Automatic Installation)
(INF Files - Manual Installation or Repair Drivers)
Password for ZIP = samkey
MULTI-UNLOCK.COM & UNLOCK.MX
Que necesito para reparar un celular
- Cautin con punta delgada
- Pistola de Calor que regule el aire y temperatura
- Soldadura muy delgada
- Flux
- Alcohol Isopropilico
- Cepillo antiestatico
- Juego de desarmadores
- Malla para desoldar
- Extractor de Soldadura
- Multimetro
- Cinta termica para soldar
- Fuente de poder
- Microscopio con luz
- Tapete antiestatico
MULTI-UNLOCK.COM & UNLOCK.MX
Como Instalar DC Unlocker ★★★★★
Link para descargar software
Distribuidor Oficial en Mexico = MULTI-UNLOCK
Liberar Modem y Celulares
Costos https://www.dc-unlocker.com/buy/user_prices
MULTI-UNLOCK.COM & UNLOCK.MX
Como instalar Hcu Client ★★★★★
Link para bajar software
Distribuidor Oficial en Mexico = MULTI-UNLOCK
venta de creditos al instante
Features
Supported models list
- Supported 500+ Huawei models and modifications
- Supported Hisilicon, Quallcom, MTK CPU’s
- Repair IMEI, IMEI2
- Repair CDMA MEID, SUB IMEI
- Repair WIFI, Bluetooth
- Repair SN
- Repair Vendor, Country
- Read unlock codes,Unlock
- Read bootloader code, Lock bootloader
- Unlock FRP
- Repair/Flash by DC Phoenix with HCU license
- Full supported models list
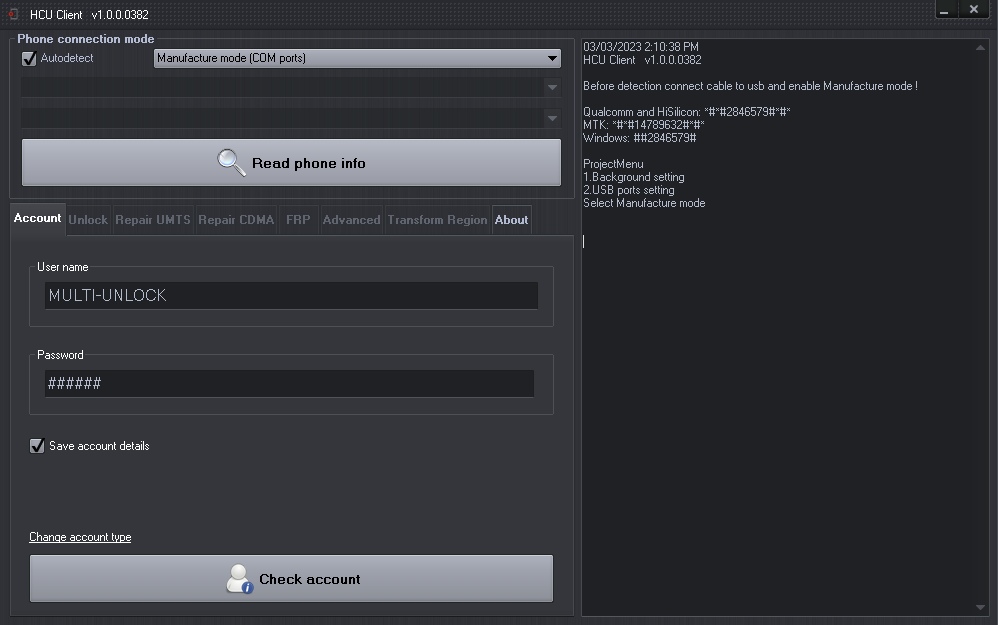
MULTI-UNLOCK.COM & UNLOCK.MX
Liberar Samsung SamKEY MTK SPR TMO CodeReader
Link para bajar los software
Creditos disponibles para entrega al instante
SamKEY MTK
SamKEY SPR
SamKEY TMO
SamKEY CodeReader
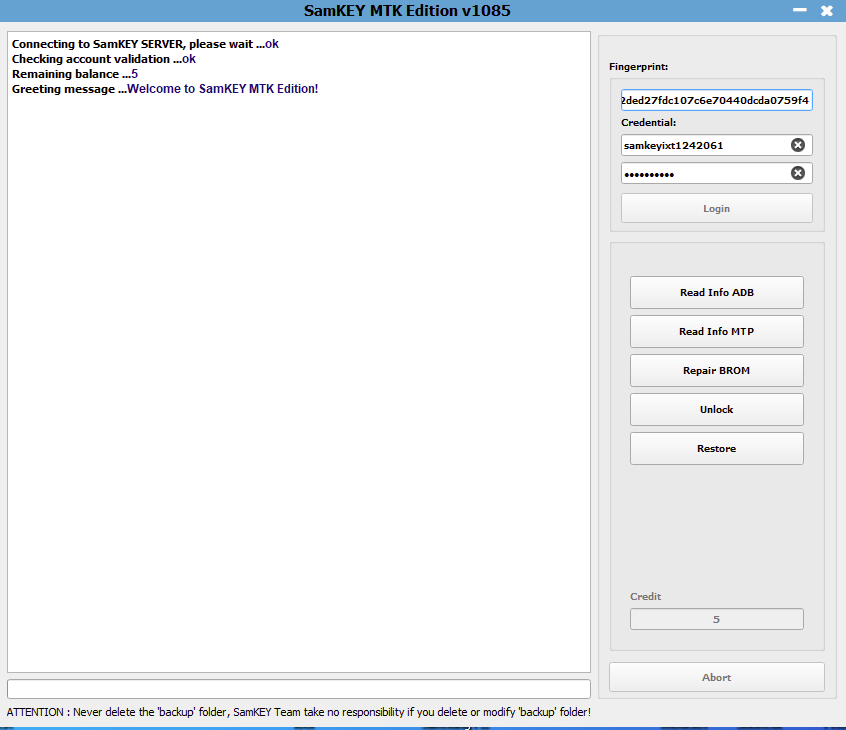
MULTI-UNLOCK.COM & UNLOCK.MX
Sim Unlocker Pro
Link para descargar Software y Drivers
https://mega.nz/folder/PXARXYgT#yd6wqbEAn88WaFsdPhvrCw
venta de creditos y crear cuenta para empezar a liberar celulares en Unlock.Mx
Buscar Servicio - Sim-Unlocker Pro Credit Create New Account
si ya tienes cuenta y solo requieres mas creditos
Buscar Servicio - Sim-Unlocker Pro Credit Refill / ReCharge Old Account
Venta desde = 1 Credito
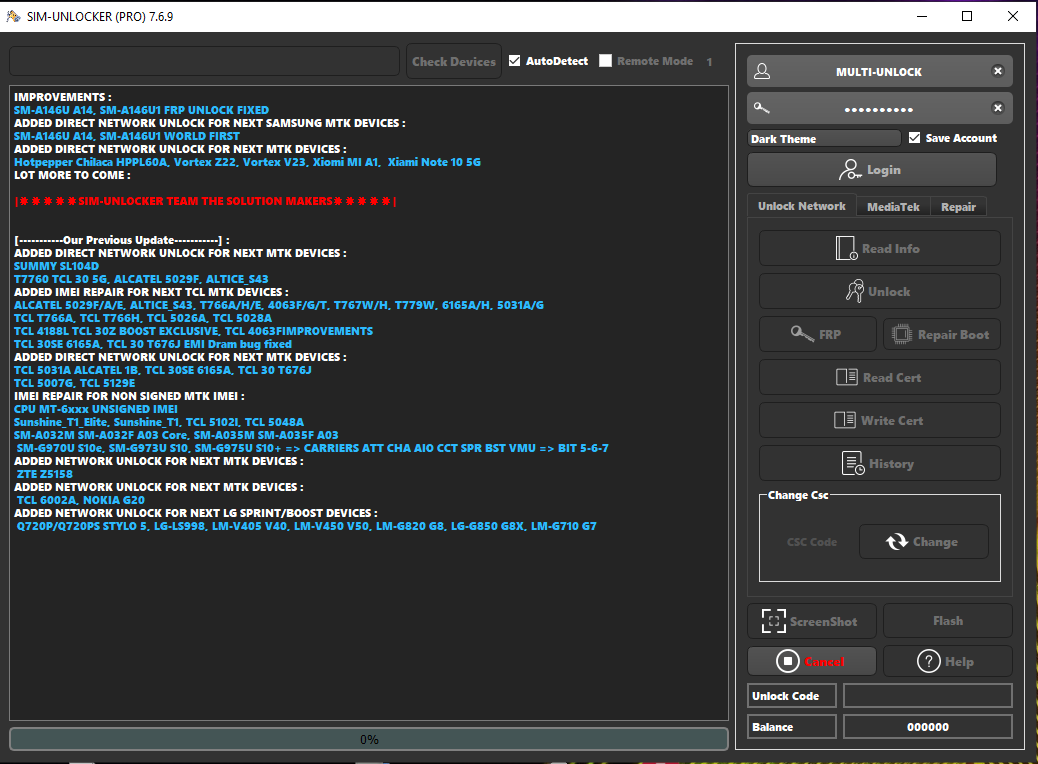
MULTI-UNLOCK.COM & UNLOCK.MX
2004-2023
Bruteforce Nokia SL3 by GPU and Hashcat
Link descarga Hashcat
C:\hashcat-6.2.6>hashcat -w3 -m110 -O --status --hex-salt --hex-charset DCDE46BD98086DEBA61254DB538A9B8447EFBE80:003570050475173200 -a3 -1 00010203040506070809 ?1?1?1?1?1?1?1?1?1?1?1?1?1?1?1 --force --outfile=357005047517329\357005047517329_COD.txt --session=SL3
Session..........: SL3 by Unlock.Mx
Status...........: Running
Hash.Mode........: 110 (sha1($pass.$salt))
Hash.Target......: dcde46bd98086deba61254db538a9b8447efbe80:003570050475173200
Time.Started.....: Sun Feb 19 14:09:19 2023, (10 secs)
Time.Estimated...: Tue May 30 14:55:45 2023, (99 days, 23 hours)
Kernel.Feature...: Optimized Kernel
Guess.Mask.......: ?1?1?1?1?1?1?1?1?1?1?1?1?1?1?1 [15]
Guess.Charset....: -1 00010203040506070809, -2 Undefined, -3 Undefined, -4 Undefined
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 115.8 MH/s (65.51ms) @ Accel:32 Loops:500 Thr:256 Vec:1
Recovered........: 0/1 (0.00%) Digests (total), 0/1 (0.00%) Digests (new)
Progress.........: 1179648000/1000000000000000 (0.00%)
Rejected.........: 0/1179648000 (0.00%)
Restore.Point....: 1179648/1000000000000 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-500 Iteration:0-500
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[080200010406090701010000000000] -> $HEX[010904080300060901010000000000]
[s]tatus [p]ause [b]ypass [c]heckpoint [f]inish [q]uit =>
Una vez que sale el código se tiene que calcular este fue el .cod obtenido por fuerza bruta 000109080905030306040306000209 este es el hash SHA1 ea928d1bd4eba4fe50b99f40605878f48183cd21
356945030661793,ea928d1bd4eba4fe50b99f40605878f48183cd21:003569450306617900:000109080905030306040306000209
#pw+001975189427989+1#
#pw+768347019273132+2#
#pw+698234671637288+3#
#pw+218261635481666+4#
#pw+762990465607815+5#
#pw+727942383108765+6#
#pw+221653143073865+7#
Requieres ayuda o soporte contactanos
MULTI-UNLOCK.COM & UNLOCK.MX
Nokia SL3 Modelos
2690 (RM-635) - Cable 2690 2700 Classic (RM-561) 2730 Classic (RM-578/579) 3600 Slide (RM-352) 3720 Classic (RM-518) 5130 XpressMusic (RM-495) - Cable 5130 5310 XpressMusic (RM-303) - Cable 5310 6300 (RM-217) 6303 Classic (RM-443) 6500 Slide (RM-240) 6500 Classic (RM-265) C6 (RM-612) label= - Cable C6 E63 (RM-437) - Cable E66 (RM-343) - Cable E71-1 (RM-346) - Cable E71 5250 (RM-684) - Cable 5230-1b (RM-593) - Cable 5800d 5230-1b (RM-594) - Cable 5800d 5230 (RM-588) - Cable 5800d 5530 (RM-504) - Cable 5530 5730s XpressMusic (RM-465) - Cable 5800d-1 (RM-356) - Cable 5800d 6120C (RM-243) 6760s (RM-573) 6790s (RM-492) N97-1 (RM-505) - Cable N97 N97-3 (RM-506) - Cable N97 N97-4 (RM-507) - Cable N97 N86 (RM-484/485/486) N97mini (RM-555) - Cable N97mini X6 (RM-551/559) C3-01 (RM-640) - Cable C3-01 C5 (RM-645) - Cable C5 C5-03 (RM-697) - Cable C5 C6-01 (RM-601) - Cable C6 C7-00 (RM-675) - Cable C7 E52 (RM-469) E55 (RM-482) E5-00 (RM-632) E72 (RM-529) E72 (RM-530) E73 mode E7-00 (RM-626) 5630d (RM-431) 5730s XpressMusic (RM-465) - Cable E75 or 5730s 6700s (RM-576) 6720 Classic(RM-424) 6730 Classic (RM-547) 6730 Classic (RM-566) 6710 Navigator (RM-491) 6700 Classic (RM-470) 6750 Classic (RM-381) N8 (RM-596) - Cable N8 X3-02 (RM-639) - Cable X3-02 X5-01 (RM-627) - Cable X5 X7-00 (RM-707) - Cable X7 C2-01 (RM-721) - Cable C2-01 3710a-1 (RM-509) 3710a-1b (RM-510) 3711a-1 (RM-511) 5330 (RM-479/478) 6303ci (RM-638) 7230 (RM-604) X3-00 (RM-540) - Cable X3-00
Mayoreo TCL 20 XE Nuevo Liberado de fabrica $ 1699
Se requiere mínimo de piezas
Incluye caja y accesorios
hasta agotar existencias

FRP Lanix Ilium M9V by NckBox Spreadtrum
Como quitar cuenta google FRP Lanix Ilium M9V
Bajar Software desde este link se tiene que pagar para bajarlo
https://www.needrom.com/download/lanix-ilium-m9v/
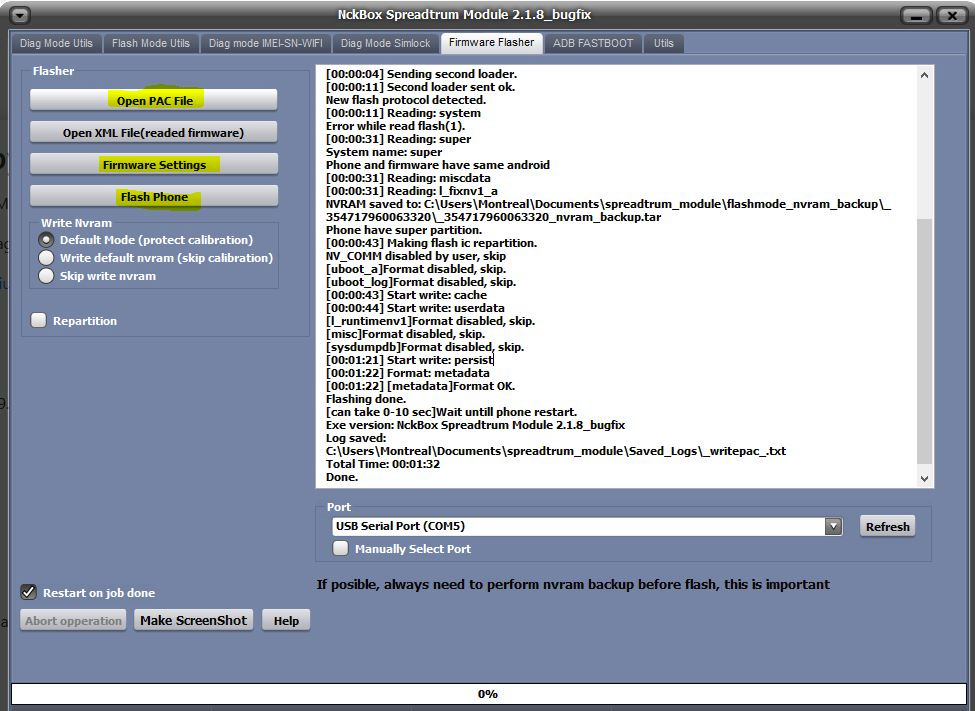
Pestaña Firmware Flasher
Open Pac File
seleccionar archivo - Ilium_M9V_OPEN_SW_09.pac
Dar click Firmware Settings
Seleccionar solamente estos archivos
- FDL
- FDL2
- Cache
- UserData
- Persist = esta es la area donde se guarda el FRP en los Spreadtrum
- EraseMetadata
Dar Boton OK
Dar Click Flash Phone
Presiionar Volumen + mas Volumen - conectar el cable no soltar los botones hasta que termine de hacer el boot
esperan un momento a que termine el proceso aqui dejo el log
ACTION: Flash Firmware.
Selected firmware: Ilium_M9V_OPEN_SW_09.pac
NV: Default Mode (protect calibration)
Device Storage: EMMC
Start Detect phone...
Phone must be off with battery inside.
Long press "VOL -" key and insert usb cable.
For some phones need to
Long press "VOL -"+ "VOL +" key and insert usb cable.
Detected: SPRD U2S Diag (COM6)
[00:00:00] Sending loader.
BOOT: SPRD3
Sending loader, keep boot key untill loader start.
[00:00:03] Loader ok
[00:00:03] Wait for loader....
Loader OK: ~"Spreadtrum Boot Block version 1.1
Changing bautrate OK.
[00:00:04] [1]First boot done.
[00:00:04] Sending second loader.
[00:00:11] Second loader sent ok.
New flash protocol detected.
[00:00:11] Reading: system
Error while read flash(1).
[00:00:31] Reading: super
System name: super
Phone and firmware have same android
[00:00:31] Reading: miscdata
[00:00:31] Reading: l_fixnv1_a
NVRAM saved to: C:\Users\Montreal\Documents\spreadtrum_module\flashmode_nvram_backup\_354717960063320\_354717960063320_nvram_backup.tar
Phone have super partition.
[00:00:43] Making flash ic repartition.
NV_COMM disabled by user, skip
[uboot_a]Format disabled, skip.
[uboot_log]Format disabled, skip.
[00:00:43] Start write: cache
[00:00:44] Start write: userdata
[l_runtimenv1]Format disabled, skip.
[misc]Format disabled, skip.
[sysdumpdb]Format disabled, skip.
[00:01:21] Start write: persist
[00:01:22] Format: metadata
[00:01:22] [metadata]Format OK.
Flashing done.
[can take 0-10 sec]Wait untill phone restart.
Exe version: NckBox Spreadtrum Module 2.1.8_bugfix
Log saved:
C:\Users\Montreal\Documents\spreadtrum_module\Saved_Logs\_writepac_.txt
Total Time: 00:01:32
Done.
MULTI-UNLOCK & UNLOCK.MX
Best Regard