Blog
-> FRP
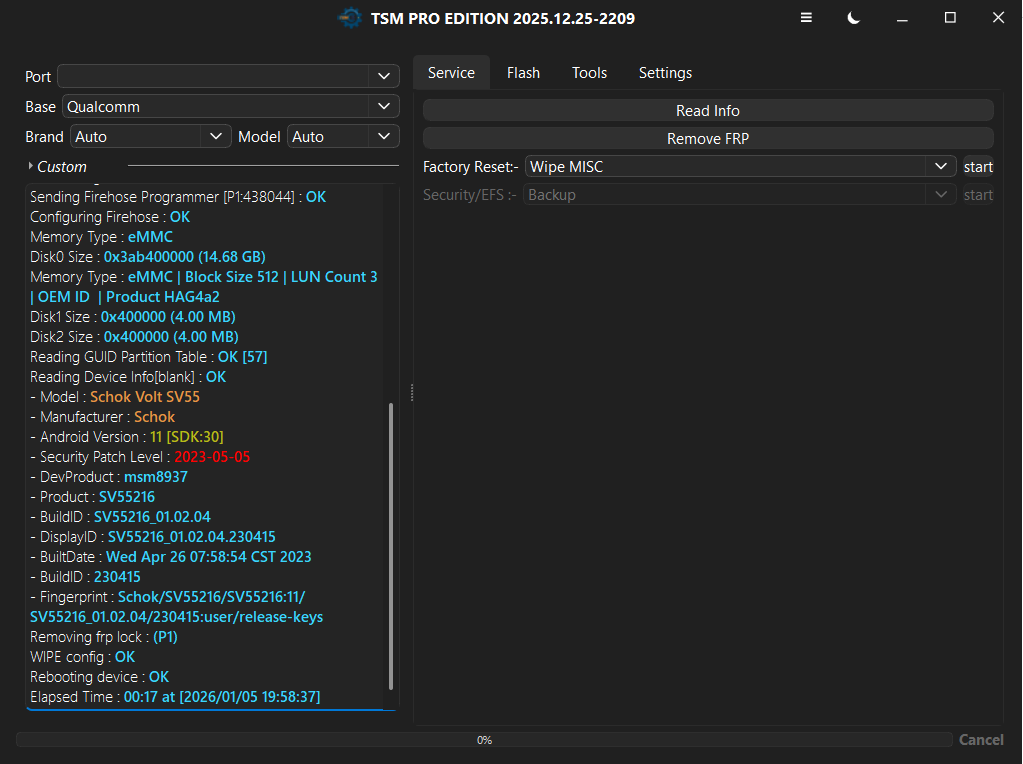
Remove FRP Schok Volt SV55 SV55216 By TSM PRO EDITION
Apagado Presionar Volumen arriba + Abajo y conectar el cable para entrar en modo qualcomm
Seleccionar Base: Qualcomm y presionar Boton Remove FRP
Operation : Remove FRP
Waiting for QCOM EDL usb device : OK
USB Port : Qualcomm HS-USB QDLoader 9008 (COM96)
USB Device : oem223.inf v2.1.3.5 12-17-2018 [0x5C6-0x9008]
Connecting device : OK
Reading Chip Info : OK
- Sahara version : 2
- Chip Serial Number : 09b1ede3
- MSM HWID : 0x1060e1 | model_id:0x0004 | oem_id:0019
- OEM PKHASH : f76a42e0f7bd4bc90ec4d925a8ba9f62aaa8cdc45be5d65387bf892de9a854ec
- HW_ID : 001060e100190004
- CHIP : Qualcomm Snapdragon 215 [QM215]
Connecting to Server : OK
Sending Firehose Programmer [P1:438044] : OK
Configuring Firehose : OK
Memory Type : eMMC
Disk0 Size : 0x3ab400000 (14.68 GB)
Memory Type : eMMC | Block Size 512 | LUN Count 3 | OEM ID | Product HAG4a2
Disk1 Size : 0x400000 (4.00 MB)
Disk2 Size : 0x400000 (4.00 MB)
Reading GUID Partition Table : OK [57]
Reading Device Info[blank] : OK
- Model : Schok Volt SV55
- Manufacturer : Schok
- Android Version : 11 [SDK:30]
- Security Patch Level : 2023-05-05
- DevProduct : msm8937
- Product : SV55216
- BuildID : SV55216_01.02.04
- DisplayID : SV55216_01.02.04.230415
- BuiltDate : Wed Apr 26 07:58:54 CST 2023
- BuildID : 230415
- Fingerprint : Schok/SV55216/SV55216:11/SV55216_01.02.04/230415:user/release-keys
Removing frp lock : (P1)
WIPE config : OK
Rebooting device : OK
Elapsed Time : 00:17 at [2026/01/05 19:58:37]
Reading bootloader info... OK
Serial : 162655715 SoC : [Snapdragon 215] [QM215] [0x001060E1]
OEM : [0x0019] Model : Unknown [0x0000]
PK_HASH[0] : F76A42E0F7BD4BC90EC4D925A8BA9F62
PK_HASH[1] : AAA8CDC45BE5D65387BF892DE9A854EC
FRP One Plus N200 5G by Chimera Tool
Primero Desconectar pantalla para poder hacer el Test Point
Chimera Mobile Phone Utility version: 44.46.0957 @ 2025-10-07
Delete FRP partition
Clearing FRP lock
Rebooting the phone...
Finished at local time: [10.07.25 10:07:10]
WorkID: 402293195

onn 8 Tablet Azul FRP Factory Reset by Chimera Tool file= preloader_t302aa.bin
Tablet ONN Azul
Presionar Apagar y presionar Volumen Abajo para que la detecte en BROM
..Port - Device detected :)
Preloader - CPU: MT6768/MT6769(Helio P65/G85 k68v1)
Preloader - HW version: 0x0
Preloader - WDT: 0x10007000
Preloader - Uart: 0x11002000
Preloader - Brom payload addr: 0x100a00
Preloader - DA payload addr: 0x201000
Preloader - CQ_DMA addr: 0x10212000
Preloader - Var1: 0x25
Preloader - Disabling Watchdog...
Preloader - HW code: 0x707
Preloader - Target config: 0xe1
Preloader - SBC enabled: True
Preloader - SLA enabled: False
Preloader - DAA enabled: False
Preloader - SWJTAG enabled: False
Preloader - EPP_PARAM at 0x600 after EMMC_BOOT/SDMMC_BOOT: False
Preloader - Root cert required: False
Preloader - Mem read auth: True
Preloader - Mem write auth: True
Preloader - Cmd 0xC8 blocked: True
Preloader - Get Target info
Preloader - BROM mode detected.
Preloader - HW subcode: 0x8a00
Preloader - HW Ver: 0xca00
Preloader - SW Ver: 0x0
Preloader - ME_ID: 5D0460E07ACDF00530423239DB7186E9
Preloader - SOC_ID: B9282535F434E79783F7EA2C7249FB5179C5D19282784E7B38A85085FF666236
DaHandler - Device is protected.
DaHandler - Device is in BROM-Mode. Bypassing security.
PLTools - Loading payload from mt6768_payload.bin, 0x264 bytes
Exploitation - Kamakiri Run
Exploitation - Done sending payload...
PLTools - Successfully sent payload: \payloads\mt6768_payload.bin
Port - Device detected :)
DaHandler
DaHandler - [LIB]: Device is in BROM mode. No preloader given, trying to dump preloader from ram.
Successfully extracted preloader for this device to: preloader_t302aa.bin
DAXFlash - Uploading xflash stage 1 from MTK_DA_V5.bin
XFlashExt - Patching da1 ...
Mtk - Patched "Patched loader msg" in preloader
Mtk - Patched "hash_check" in preloader
Mtk - Patched "Patched loader msg" in preloader
Mtk - Patched "get_vfy_policy" in preloader
XFlashExt - Patching da2 ...
XFlashExt - Security check patched
XFlashExt - DA version anti-rollback patched
XFlashExt - SBC patched to be disabled
XFlashExt - Register read/write not allowed patched
DAXFlash - Successfully uploaded stage 1, jumping ..
Preloader - Jumping to 0x200000
Preloader - Jumping to 0x200000: ok.
DAXFlash - Successfully received DA sync
DAXFlash - Sending emi data ...
DAXFlash - DRAM setup passed.
DAXFlash - Sending emi data succeeded.
DAXFlash - Uploading stage 2...
DAXFlash - Upload data was accepted. Jumping to stage 2...
DAXFlash - Boot to succeeded.
DAXFlash - Successfully uploaded stage 2
DAXFlash - DA SLA is disabled
DAXFlash - EMMC FWVer: 0x0
DAXFlash - EMMC ID: AT3SFB
DAXFlash - EMMC CID: ec2900415433534642300d2fd384baf9
DAXFlash - EMMC Boot1 Size: 0x400000
DAXFlash - EMMC Boot2 Size: 0x400000
DAXFlash - EMMC GP1 Size: 0x0
DAXFlash - EMMC GP2 Size: 0x0
DAXFlash - EMMC GP3 Size: 0x0
DAXFlash - EMMC GP4 Size: 0x0
DAXFlash - EMMC RPMB Size: 0x400000
DAXFlash - EMMC USER Size: 0x748000000
DAXFlash - HW-CODE : 0x707
DAXFlash - HWSUB-CODE : 0x8A00
DAXFlash - HW-VERSION : 0xCA00
DAXFlash - SW-VERSION : 0x0
DAXFlash - CHIP-EVOLUTION : 0x1
DAXFlash - DA-VERSION : 1.0
DAXFlash - Extensions were accepted. Jumping to extensions...
DAXFlash - Boot to succeeded.
DAXFlash - DA Extensions successfully added
DeviceClass - [Errno 19] No such device (it may have been disconnected)
Reset command was sent. Disconnect usb cable to power off.
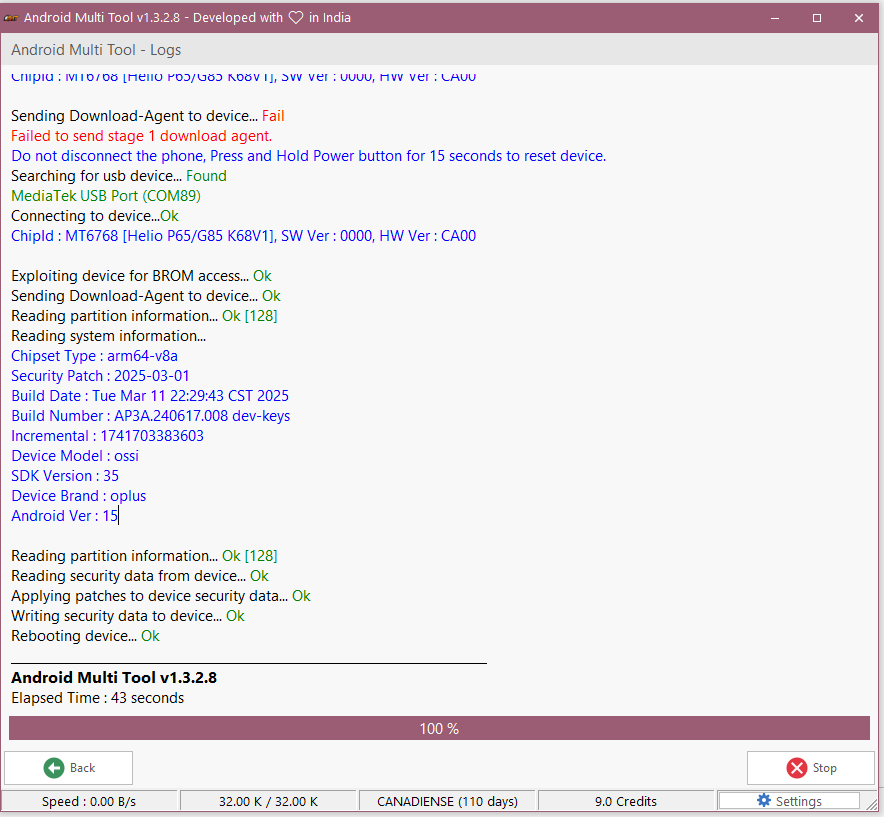
FRP Oppo A58 CPH2577 by AMT
Presionar Volumen + - Insertar cable USB para entrar en modo Preloader
Instalar Drivers QcomMtk_Driver_Setup_4.0.1.6_.exe
Brand : OPPO
Model : A58
Operation : Reset FRP
Searching for usb device... Found
MediaTek PreLoader USB VCOM (Android) (COM87)
Connecting to device...Ok
ChipId : MT6768 [Helio P65/G85 K68V1], SW Ver : 0000, HW Ver : CA00
Sending Download-Agent to device... Fail
Failed to send stage 1 download agent.
Do not disconnect the phone, Press and Hold Power button for 15 seconds to reset device.
Searching for usb device... Found
MediaTek USB Port (COM89)
Connecting to device...Ok
ChipId : MT6768 [Helio P65/G85 K68V1], SW Ver : 0000, HW Ver : CA00
Exploiting device for BROM access... Ok
Sending Download-Agent to device... Ok
Reading partition information... Ok [128]
Reading system information...
Chipset Type : arm64-v8a
Security Patch : 2025-03-01
Build Date : Tue Mar 11 22:29:43 CST 2025
Build Number : AP3A.240617.008 dev-keys
Incremental : 1741703383603
Device Model : ossi
SDK Version : 35
Device Brand : oplus
Android Ver : 15
Reading partition information... Ok [128]
Formatting desired partition... Ok
Reading partition information... Ok [128]
Reading security data from device... Ok
Applying patches to device security data... Ok
Writing security data to device... Ok
Rebooting device... Ok
Android Multi Tool v1.3.2.8
Elapsed Time : 43 seconds
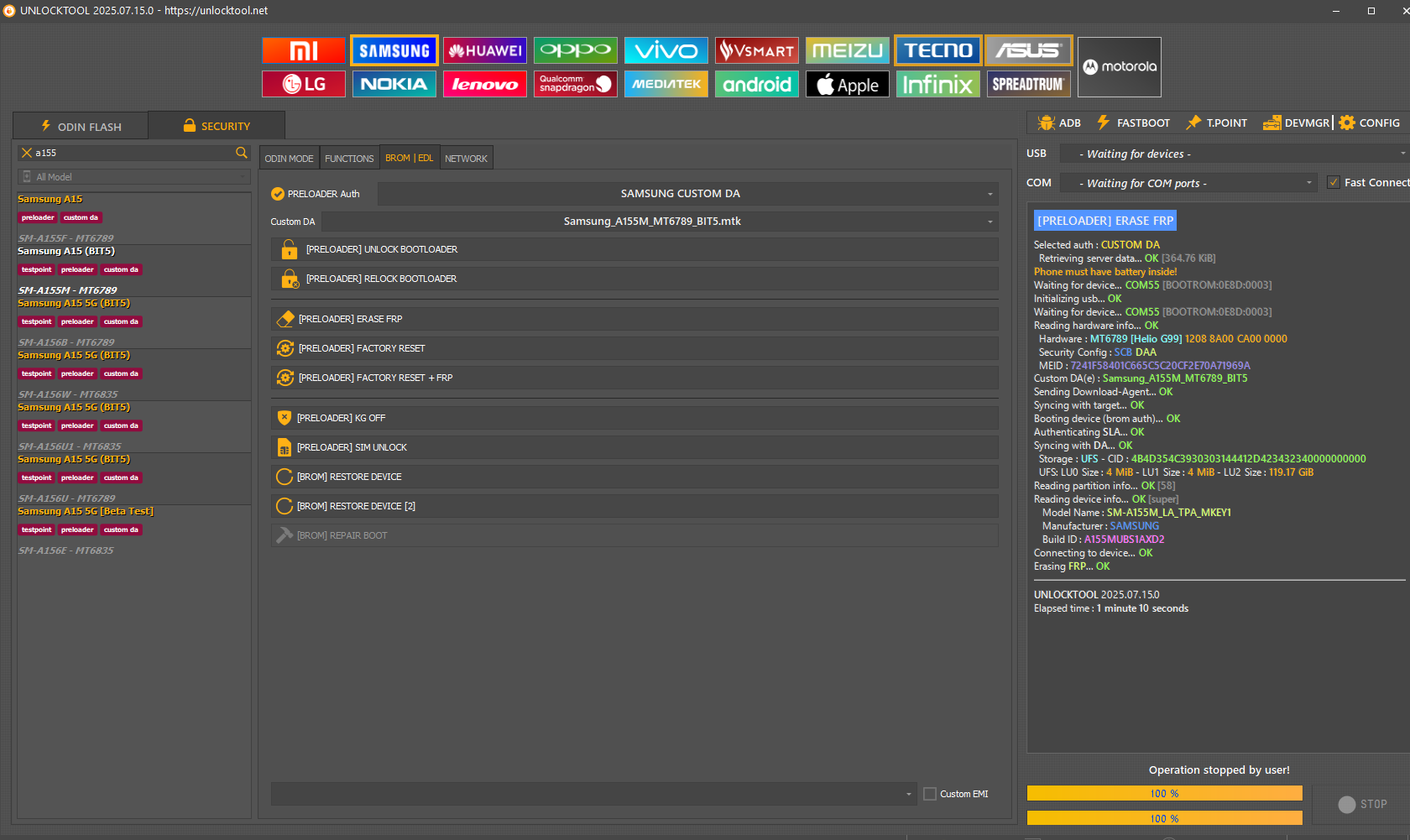
FRP Samsung A155M A15 by Unlocktool
[PRELOADER] ERASE FRP
Selected auth :
CUSTOM DA
Retrieving server data...
OK
[364.76 KiB]
Phone must have battery inside!
Waiting for device...
COM55
[BOOTROM:0E8D:0003]
Initializing usb...
OK
Waiting for device...
COM55
[BOOTROM:0E8D:0003]
Reading hardware info...
OK
Hardware :
MT6789 [Helio G99]
1208
8A00
CA00
0000
Security Config :
SCB DAA
MEID :
7241F58401C665C5C20CF2E70A71969A
Custom DA(e) :
Samsung_A155M_MT6789_BIT5
Sending Download-Agent...
OK
Syncing with target...
OK
Booting device (brom auth)...
OK
Authenticating
SLA
...
OK
Syncing with
DA
...
OK
Storage :
UFS
- CID :
4B4D354C3930303144412D423432340000000000
UFS: LU0 Size :
4 MiB
- LU1 Size :
4 MiB
- LU2 Size :
119.17 GiB
Reading partition info...
OK
[58]
Reading device info...
OK
[super]
Model Name :
SM-A155M_LA_TPA_MKEY1
Manufacturer :
SAMSUNG
Build ID :
A155MUBS1AXD2
Connecting to device...
OK
Erasing
FRP
...
OK
UNLOCKTOOL
2025.07.15.0
Elapsed time :
1 minute 10 seconds
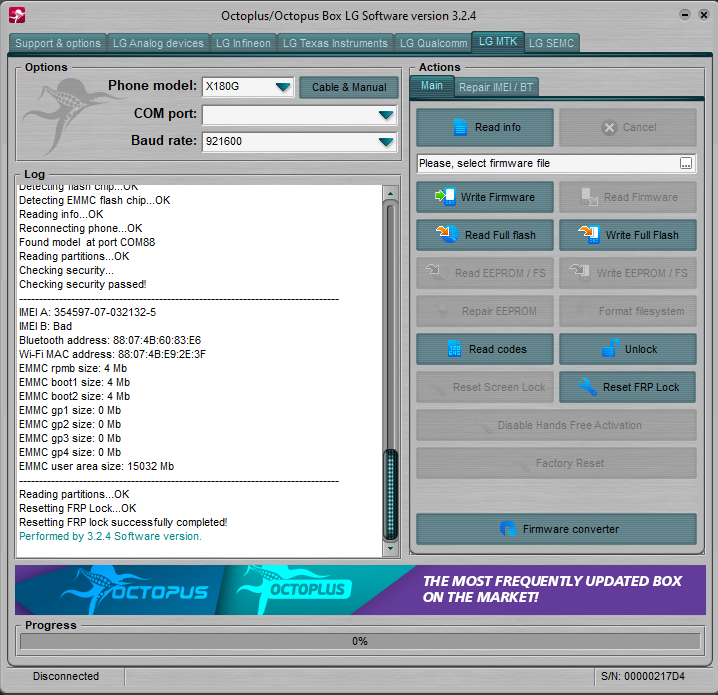
FRP LG X180g MTK MT6592 by Octopus Box LG
Welcome to Octoplus/Octopus Box LG Software version 3.2.4
Plesionar volumen abajo + cable usb
Selected USB connection type
Work ID: 00000000021E2DC7
Checking data...OK
Platform: LG MTK
Selected port:
Selected baudrate: 0
Selected model: X180G
Press and hold "Vol-" and connect cable.OK
Phone found.
CPU name: MT6592
CPU revision: 8A00.CA00.0000.0000
Prepairing loader...OK
Sending loader...OK
Synchronizing with loader...
Detecting flash chip...OK
Detecting EMMC flash chip...OK
Reading info...OK
Reconnecting phone...OK
Found model at port COM88
Reading partitions...OK
Checking security...
Checking security passed!
--------------------------------------------------------------------------------
IMEI A: 354597-07-032132-5
IMEI B: Bad
Bluetooth address: 88:07:4B:60:83:E6
Wi-Fi MAC address: 88:07:4B:E9:2E:3F
EMMC rpmb size: 4 Mb
EMMC boot1 size: 4 Mb
EMMC boot2 size: 4 Mb
EMMC gp1 size: 0 Mb
EMMC gp2 size: 0 Mb
EMMC gp3 size: 0 Mb
EMMC gp4 size: 0 Mb
EMMC user area size: 15032 Mb
--------------------------------------------------------------------------------
Reading partitions...OK
Resetting FRP Lock...OK
Resetting FRP lock successfully completed!
Performed by 3.2.4 Software version.
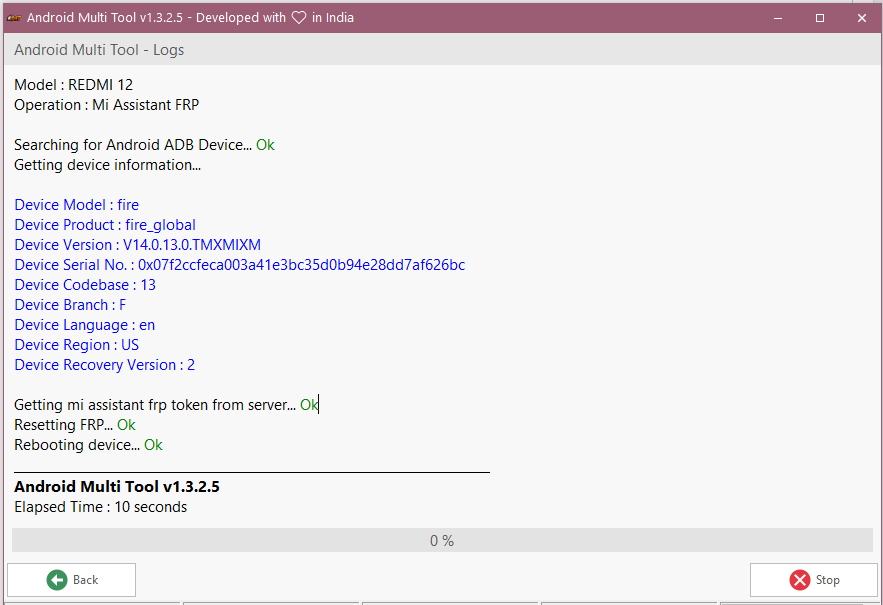
FRP REDMI 12 by AMT Android Multi Tool
Consume 1 credito
presionar volumen arriba + encendido (conectar cable usb)
Brand : XIAOMI
Model : REDMI 12
Operation : Mi Assistant FRP
Searching for Android ADB Device... Ok
Getting device information...
Device Model : fire
Device Product : fire_global
Device Version : V14.0.13.0.TMXMIXM
Device Serial No. : 0x07f2ccfeca003a41e3bc35d0b94e28dd7af626bc
Device Codebase : 13
Device Branch : F
Device Language : en
Device Region : US
Device Recovery Version : 2
Getting mi assistant frp token from server... Ok
Resetting FRP... Ok
Rebooting device... Ok
Android Multi Tool v1.3.2.5
Elapsed Time : 10 seconds
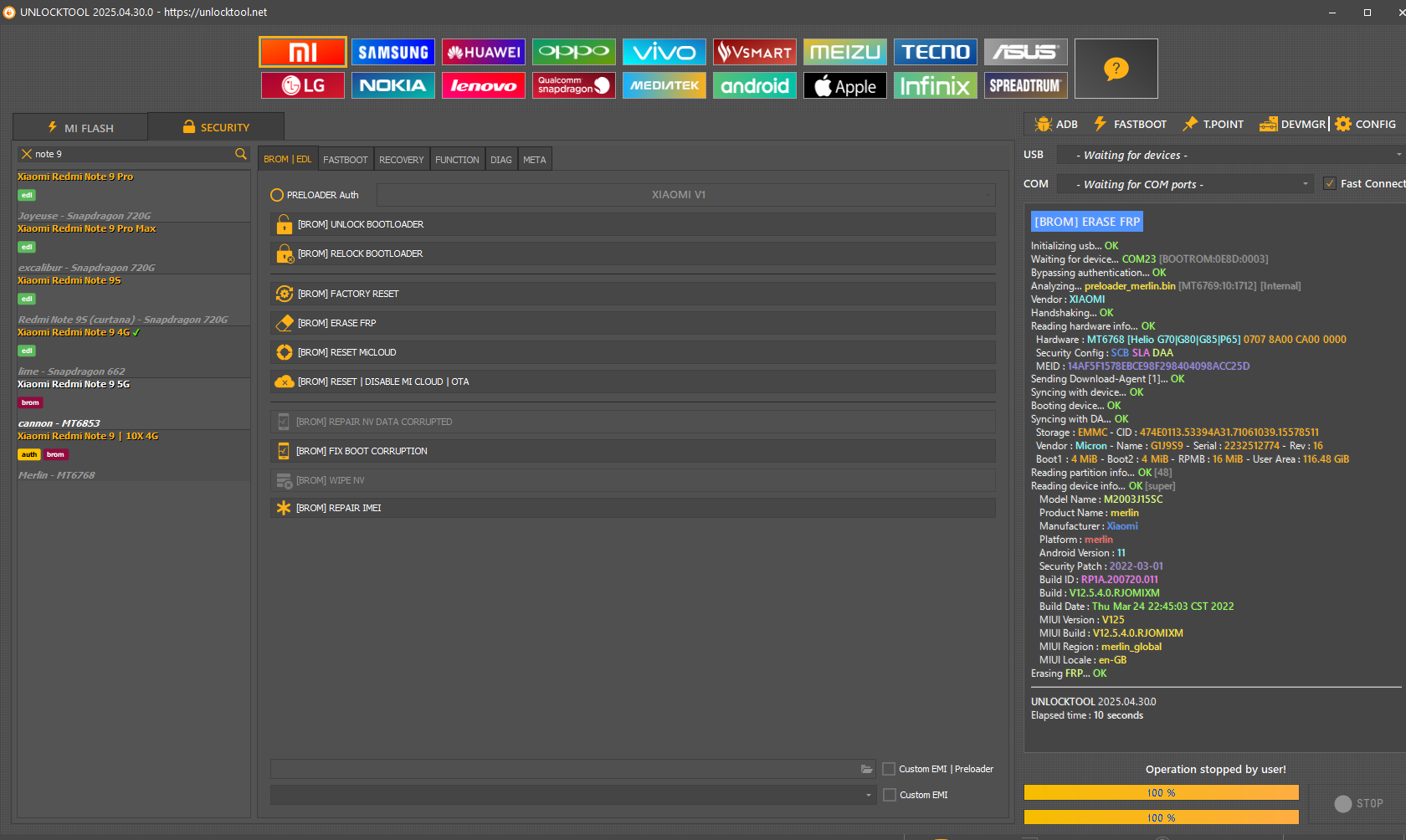
FRP Xiaomi Note 9 5G By Unlocktool
[BROM] ERASE FRP
Initializing usb...
OK
Waiting for device...
COM23
[BOOTROM:0E8D:0003]
Bypassing authentication...
OK
Analyzing...
preloader_merlin.bin [MT6769:10:1712] [Internal]
Vendor :
XIAOMI
Handshaking...
OK
Reading hardware info...
OK
Hardware :
MT6768 [Helio G70|G80|G85|P65]
0707
8A00
CA00
0000
Security Config :
SCB SLA DAA
MEID :
14AF5F1578EBCE98F298404098ACC25D
Sending Download-Agent [1]...
OK
Syncing with device...
OK
Booting device...
OK
Syncing with DA...
OK
Storage :
EMMC
- CID :
474E0113.53394A31.71061039.15578511
Vendor :
Micron
- Name :
G1J9S9
- Serial :
2232512774
- Rev :
16
Boot1 :
4 MiB
- Boot2 :
4 MiB
- RPMB :
16 MiB
- User Area :
116.48 GiB
Reading partition info...
OK
[48]
Reading device info...
OK
[super]
Model Name :
M2003J15SC
Product Name :
merlin
Manufacturer :
Xiaomi
Platform :
merlin
Android Version :
11
Security Patch :
2022-03-01
Build ID :
RP1A.200720.011
Build :
V12.5.4.0.RJOMIXM
Build Date :
Thu Mar 24 22:45:03 CST 2022
MIUI Version :
V125
MIUI Build :
V12.5.4.0.RJOMIXM
MIUI Region :
merlin_global
MIUI Locale :
en-GB
Erasing
FRP
...
OK
UNLOCKTOOL
2025.04.30.0
Elapsed time :
10 seconds
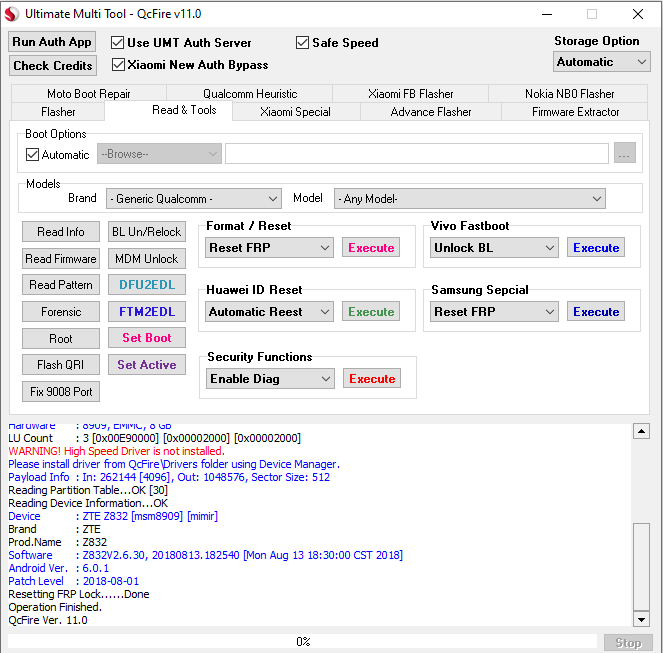
FRP ZTE Z832 By UMT Box
Enter FTM = Volumen Abajo + Encendido
$ adb reboot edl
# Qualcomm mode detected
Operation : Reset FRP
Checking for existing devices...Found
Port : Qualcomm HS-USB QDLoader 9008 (COM243)
Driver Info : Qualcomm Incorporated, qcusbser.sys, 2.1.4.1
Opening Port...OK
Init Handshake Sequence...OK
Hardware ID : E1009600 [8909] 00000400
OPK_DATA : 39B5FF24D131CBE6DFF161CD237FD1087FBC923F2174267E93C62FDF1ED5F076
Initializing Protocol...OK
Using Auto Loader Selection [1]
Preparing Loader...Done
Sending Loader [8909_040]...Done
Executing Loader...OK
Detecting Storage Type...OK
Hardware : 8909, EMMC, 8 GB
LU Count : 3 [0x00E90000] [0x00002000] [0x00002000]
WARNING! High Speed Driver is not installed.
Please install driver from QcFire\Drivers folder using Device Manager.
Payload Info : In: 262144 [4096], Out: 1048576, Sector Size: 512
Reading Partition Table...OK [30]
Reading Device Information...OK
Device : ZTE Z832 [msm8909] [mimir]
Brand : ZTE
Prod.Name : Z832
Software : Z832V2.6.30, 20180813.182540 [Mon Aug 13 18:30:00 CST 2018]
Android Ver. : 6.0.1
Patch Level : 2018-08-01
Resetting FRP Lock......Done
Operation Finished.
QcFire Ver. 11.0
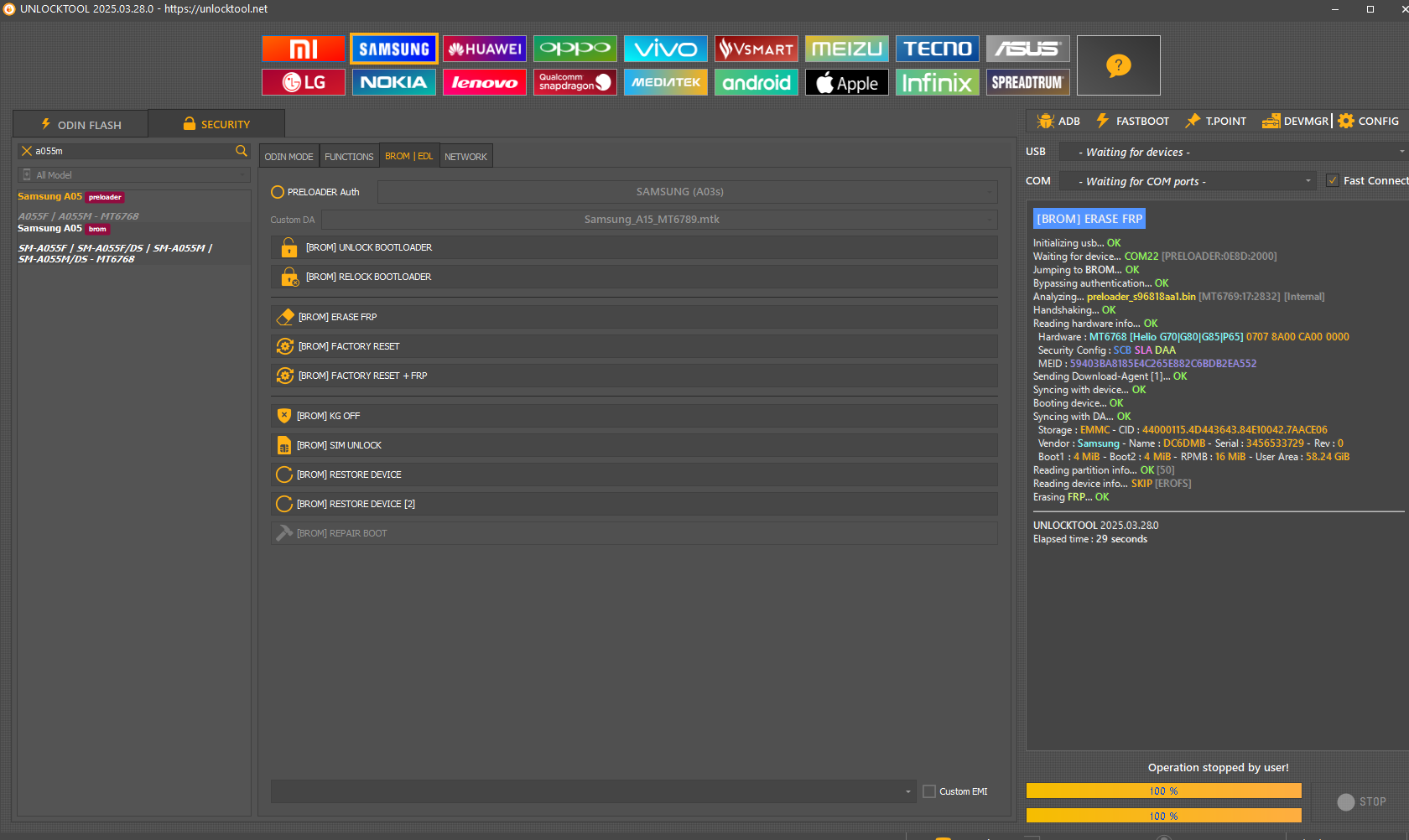
FRP Samsung SM-A055M by Unlocktool

[BROM] ERASE FRP
Initializing usb...
OK
Waiting for device...
COM22
[PRELOADER:0E8D:2000]
Jumping to
BROM
...
OK
Bypassing authentication...
OK
Analyzing...
preloader_s96818aa1.bin [MT6769:17:2832] [Internal]
Handshaking...
OK
Reading hardware info...
OK
Hardware :
MT6768 [Helio G70|G80|G85|P65]
0707
8A00
CA00
0000
Security Config :
SCB SLA DAA
MEID :
59403BA8185E4C265E882C6BDB2EA552
Sending Download-Agent [1]...
OK
Syncing with device...
OK
Booting device...
OK
Syncing with DA...
OK
Storage :
EMMC
- CID :
44000115.4D443643.84E10042.7AACE06
Vendor :
Samsung
- Name :
DC6DMB
- Serial :
3456533729
- Rev :
0
Boot1 :
4 MiB
- Boot2 :
4 MiB
- RPMB :
16 MiB
- User Area :
58.24 GiB
Reading partition info...
OK
[50]
Reading device info...
SKIP
[EROFS]
Erasing
FRP
...
OK
UNLOCKTOOL
2025.03.28.0
Elapsed time :
29 seconds
FRP Samsung SM-A032F
Realisar Test Point
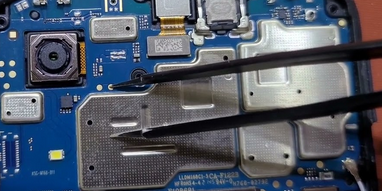
[SPRD] FACTORY RESET
Selected Platform :
SC9863A_32_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM9 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\6&182A12DA&0&8
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading Serial Number...
N.A
Reading
partitions info
...
OK
[56] [1024]
Reading
device info
...
OK
[super]
Model Name :
SM-A032F
Product Name :
a3corexx
Manufacturer :
samsung
Android Version :
12
Security Patch :
2023-08-01
Build ID :
SP1A.210812.016.A032FXXS4BWH5
Build Date :
Wed Aug 30 10:58:36 KST 2023
Code Name :
SM-A032F
PDA :
A032FXXS4BWH5
Erasing
FRP (persist)
...
OK
Erasing
FRP (persistent)
...
OK
Erasing
metadata
...
OK
Erasing
cache
...
OK
Erasing
userdata
...
OK
UNLOCKTOOL
2025.03.10.0
Elapsed time :
31 seconds
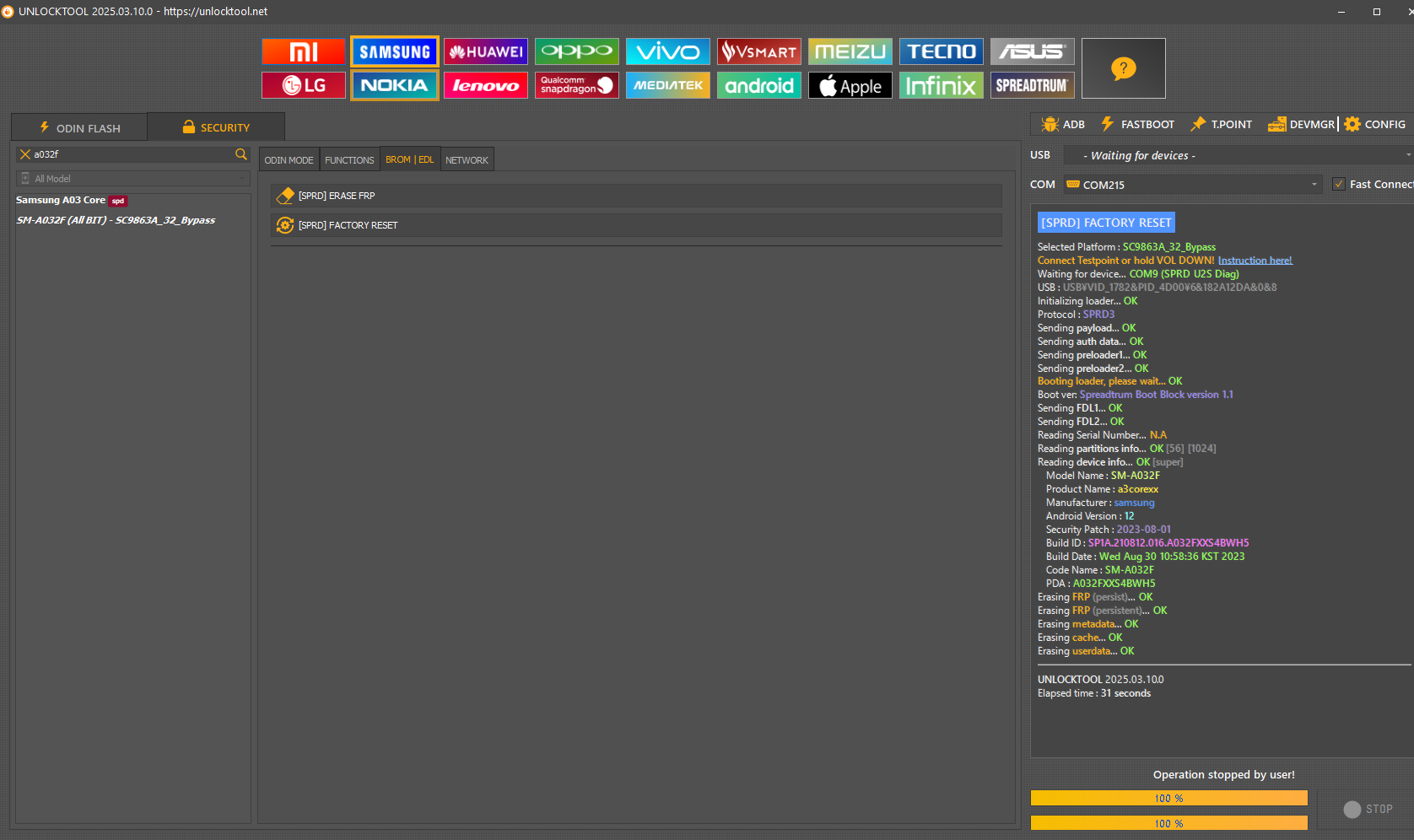
FRP Motorola E6 Play
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:003214 SourceURL:file%3a%2f%2f
ERASE FRP
Initializing usb...
OK
Waiting for device...
COM23
[BOOTROM:0E8D:0003]
Bypassing authentication...
OK
Analyzing...
preloader_bali.bin [MT6739:10:1992] [Internal]
Handshaking...
OK
Reading hardware info...
OK
Hardware :
MT6739
0699
8A00
CB00
0002
Security Config :
SCB SLA DAA
MEID :
A7EC8488F547E925C9A57C10C0F1EECB
Sending Download-Agent [1]...
OK
Syncing with device...
OK
Booting device...
OK
Syncing with DA...
OK
Storage :
EMMC
- CID :
51000115.4D333644.8D050142.1D777207
Vendor :
Samsung
- Name :
QD63MB
- Serial :
1913097477
- Rev :
1
Boot1 :
4 MiB
- Boot2 :
4 MiB
- RPMB :
16 MiB
- User Area :
29.12 GiB
Reading partition info...
OK
[40]
Reading device info...
OK
[system vendor]
Model Name :
moto e6 play
Product Name :
bali
Manufacturer :
motorola
Platform :
bali
Android Version :
9
Security Patch :
2021-11-06
Build ID :
POAS29.550-132-25
Build Date :
Mon Nov 8 09:24:12 CST 2021
Erasing
FRP
...
OK
UNLOCKTOOL
2025.02.19.0
Elapsed time :
10 seconds
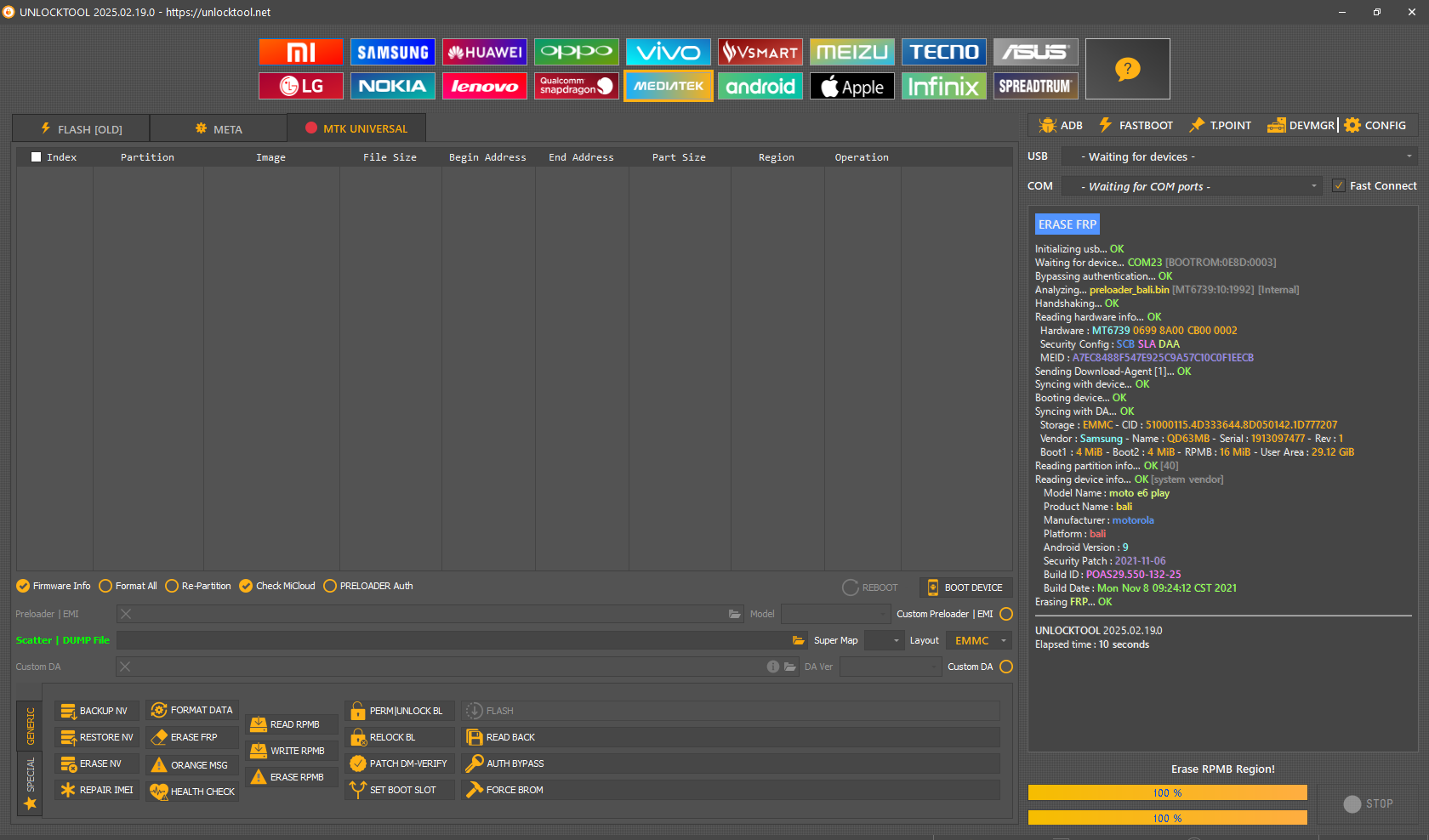
FRP Samsung SM-A115AZ Cricket by UMT BOX
Test Point

Device : Samsung Galaxy A11 (SM-A115AZ)
Operation : Reset FRP
Checking for existing devices...Found
Port : Qualcomm HS-USB QDLoader 9008 (COM93)
Driver Info : Qualcomm Incorporated, qcusbser.sys, 2.1.4.1
Opening Port...OK
Init Handshake Sequence...OK
Hardware ID : E1A00900 [8953] 00002000
OPK_DATA : CCC81D1E9F542D37EF3BBF0FBDB5DEC36A8EEBB41F832FEDE2292294DCB94B0A
Initializing Protocol...OK
Using Auto Loader Selection [1]
Preparing Loader...Done
Sending Loader [8953_052]...Done
Executing Loader...OK
Detecting Storage Type...OK
Hardware : 8953, EMMC, 32 GB
LU Count : 3 [0x03A3E000] [0x00002000] [0x00002000]
WARNING! High Speed Driver is not installed.
Please install driver from QcFire\Drivers folder using Device Manager.
Payload Info : In: 262144 [4096], Out: 1048576, Sector Size: 512
Reading Partition Table...OK [78]
Reading Device Information...OK
Software : QP1A.190711.020.A115AZTUU1ATF3, A115AZTUU1ATF3 [Tue Jun 9 14:03:14 KST 2020]
Android Ver. : 10
Patch Level : 2020-05-01
Resetting FRP Lock......Done
Operation Finished.
QcFire Ver. 11.0
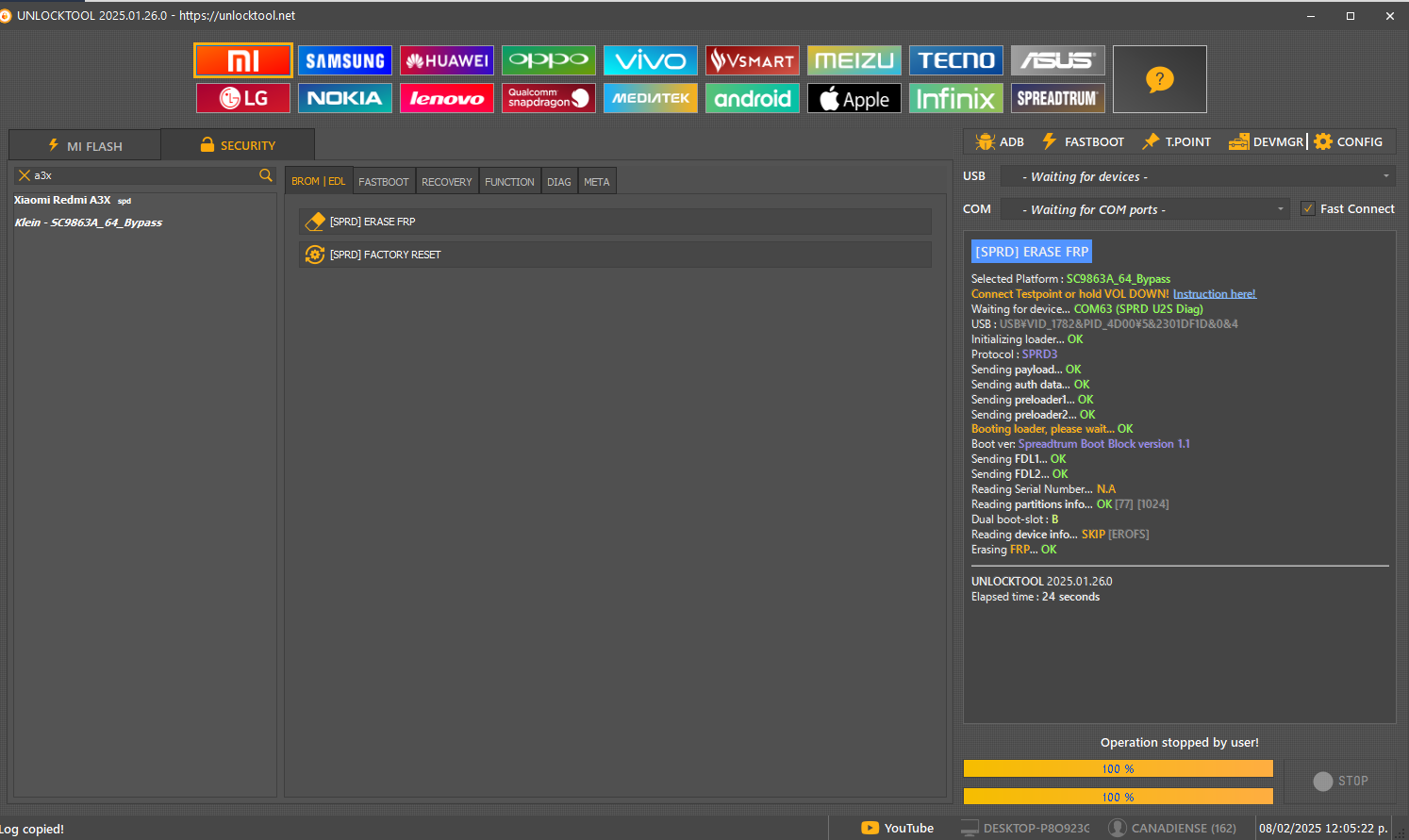
FRP Redmi A3X By Unlock Tool
Connect Test Point
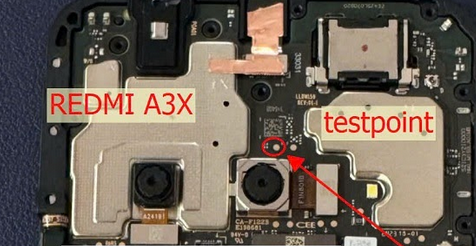
[SPRD] ERASE FRP
Selected Platform :
SC9863A_64_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM63 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\5&2301DF1D&0&4
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading Serial Number...
N.A
Reading
partitions info
...
OK
[77] [1024]
Dual boot-slot :
B
Reading
device info
...
SKIP
[EROFS]
Erasing
FRP
...
OK
UNLOCKTOOL
2025.01.26.0
Elapsed time :
24 seconds
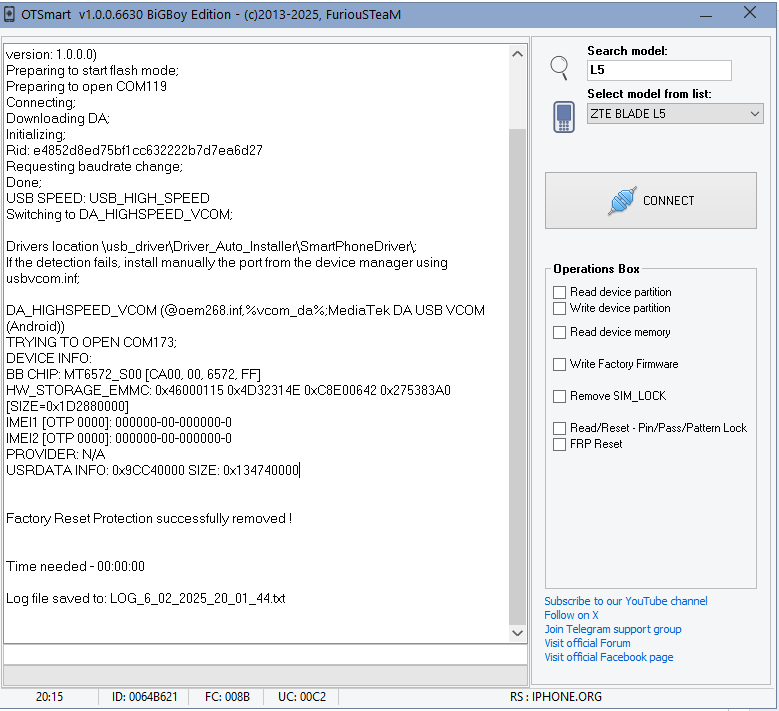
FRP ZTE BLADE L5 by Furious Gold
Using library Brom_DLL_v7.1522.2
Engine version 1.0.0.6630
Searching phone in normal mode;
[connect the phone powered off to the usb cable]
Phone detected (MediaTek PreLoader USB VCOM (Android) (COM119)) (Driver version: 1.0.0.0)
Preparing to start flash mode;
Preparing to open COM119
Connecting;
Downloading DA;
Initializing;
Rid: e4852d8ed75bf1cc632222b7d7ea6d27
Requesting baudrate change;
Done;
USB SPEED: USB_HIGH_SPEED
Switching to DA_HIGHSPEED_VCOM;
Drivers location \usb_driver\Driver_Auto_Installer\SmartPhoneDriver\;
If the detection fails, install manually the port from the device manager using usbvcom.inf;
DA_HIGHSPEED_VCOM (@oem268.inf,%vcom_da%;MediaTek DA USB VCOM (Android))
TRYING TO OPEN COM173;
DEVICE INFO:
BB CHIP: MT6572_S00 [CA00, 00, 6572, FF]
HW_STORAGE_EMMC: 0x46000115 0x4D32314E 0xC8E00642 0x275383A0 [SIZE=0x1D2880000]
IMEI1 [OTP 0000]: 000000-00-000000-0
IMEI2 [OTP 0000]: 000000-00-000000-0
PROVIDER: N/A
USRDATA INFO: 0x9CC40000 SIZE: 0x134740000
Factory Reset Protection successfully removed !
Time needed - 00:00:00
Log file saved to: LOG_6_02_2025_20_01_44.txt
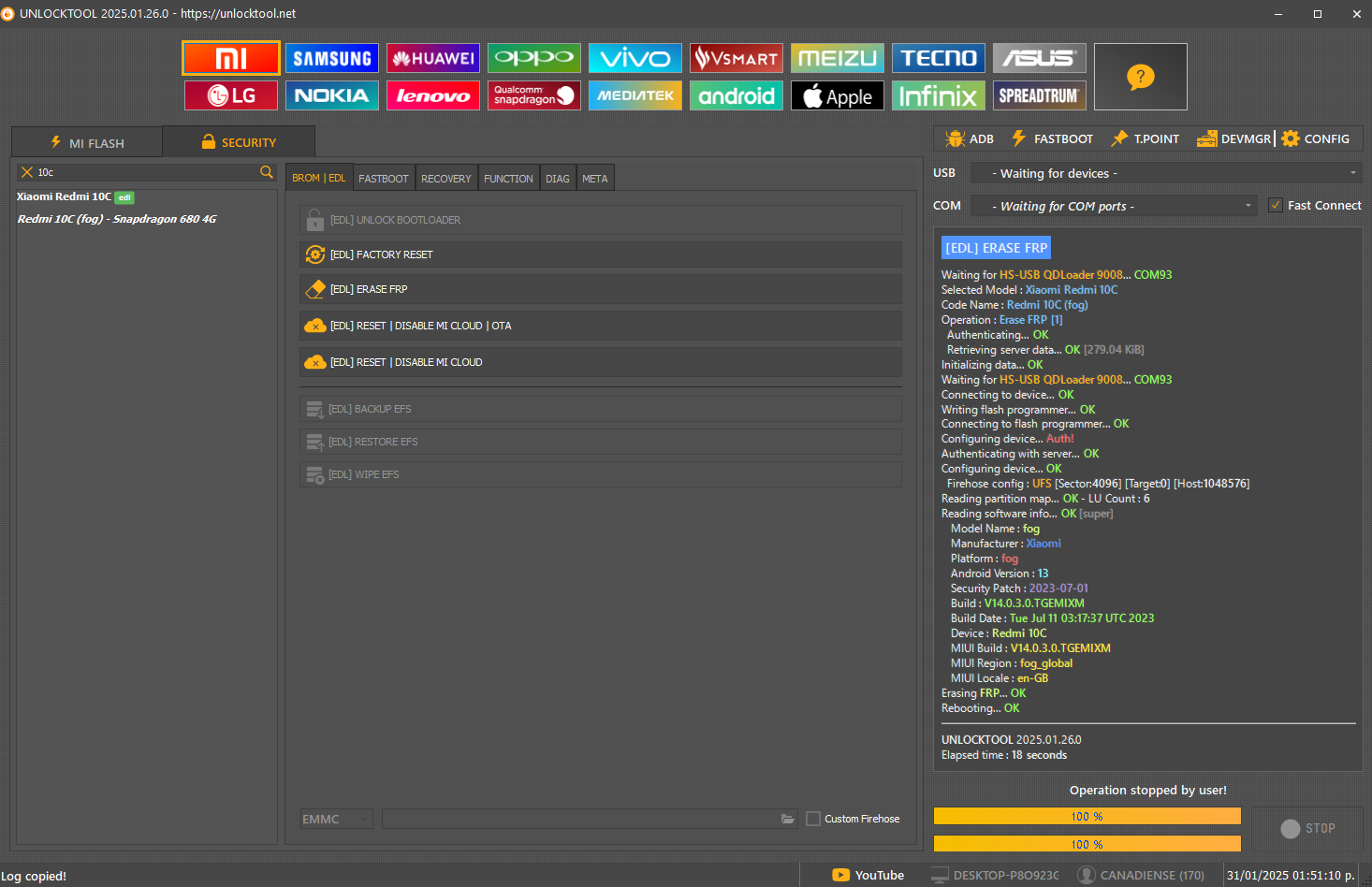
FRP Xiaomi Redmi 10C by Unlocktool
Conectar Test Point primero
[EDL] ERASE FRP
Waiting for
HS-USB QDLoader 9008
...
COM93
Selected Model :
Xiaomi Redmi 10C
Code Name :
Redmi 10C (fog)
Operation :
Erase FRP [1]
Authenticating...
OK
Retrieving server data...
OK
[279.04 KiB]
Initializing data...
OK
Waiting for
HS-USB QDLoader 9008
...
COM93
Connecting to device...
OK
Writing flash programmer...
OK
Connecting to flash programmer...
OK
Configuring device...
Auth!
Authenticating with server...
OK
Configuring device...
OK
Firehose config :
UFS
[Sector:
4096
] [Target:
0
] [Host:
1048576
]
Reading partition map...
OK
- LU Count :
6
Reading software info...
OK
[super]
Model Name :
fog
Manufacturer :
Xiaomi
Platform :
fog
Android Version :
13
Security Patch :
2023-07-01
Build :
V14.0.3.0.TGEMIXM
Build Date :
Tue Jul 11 03:17:37 UTC 2023
Device :
Redmi 10C
MIUI Build :
V14.0.3.0.TGEMIXM
MIUI Region :
fog_global
MIUI Locale :
en-GB
Erasing
FRP
...
OK
Rebooting...
OK
UNLOCKTOOL
2025.01.26.0
Elapsed time :
18 seconds
FRP Huawei P30 Lite HiSilicon Kirin 710
[USB 1.0] ERASE FRP Scanning port... COM4
Connecting to port... OK
Connection : USB 1.0 Full-Speed
USB Driver : [HUAWEI Incorporated] HSPL_usbvcom - Version : 2.0.7.1
Selected Model : HiSilicon Kirin 710 Emmc [Erase FRP]
Code Name : Hi710
Operation : Erase FRP [1]
Authenticating... OK
Retrieving server data... OK [110.72 KiB]
Writing unlocktool1... OK 1.503s
Writing unlocktool2... OK 0.232s
Writing unlocktool3... OK 0.450s
Reading partition map... OK [71]
Searching FRP Lock... OK [0:524288:524288]
Erasing FRP... OK
UNLOCKTOOL 2025.01.17.0
Elapsed time : 20 seconds
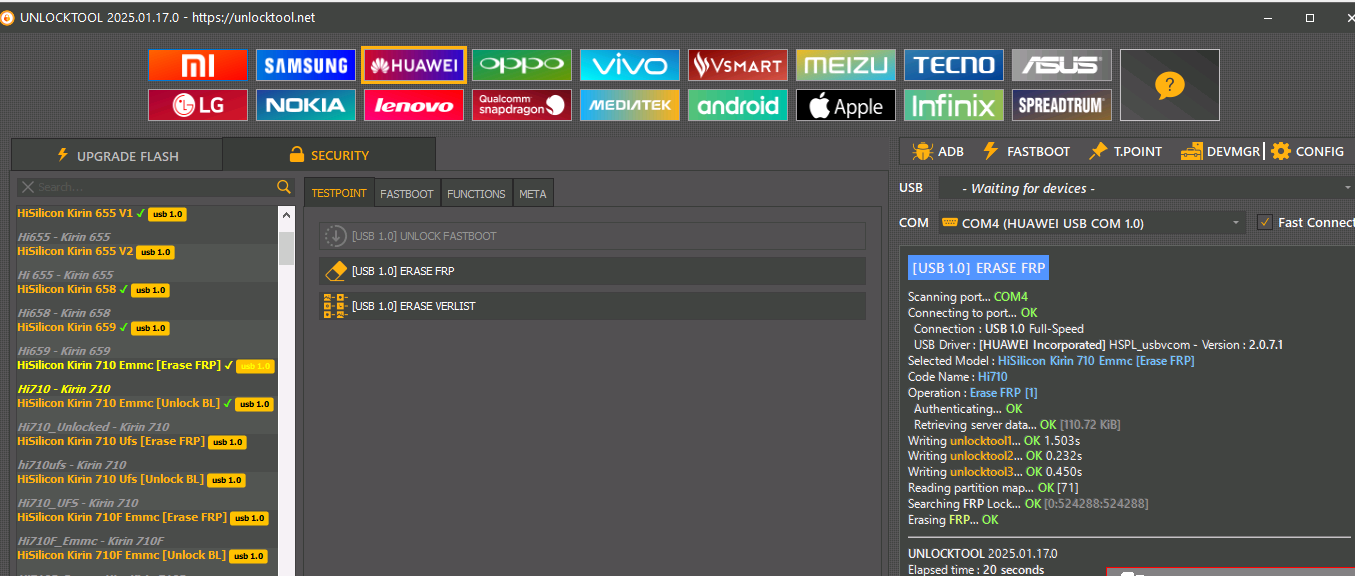
FRP Tablet Samsung SM-P610 Android 11
Primero seleccionar Android MTP y seleccionar open youtube url y abrir Chrome
Url para abrir menu
https://frpbypass.romstage.com/
Seleccionar Open dial pad

Marcar: asterisco # 0 # asterisco y seleccionar REMOVE FRP 2023 ALL METHODS
[COM] REMOVE FRP [2023] Scanning for device... COM9
Reading Info... FAIL
Connecting to device... OK
Trying method [1]... FAIL
Trying method [2]... FAIL
Trying method [3]... OK
Waiting for device...
Please accept USB Debugging on your phone!
Model : SM-P610
Manufacturer : samsung
Platform : universal9611
CPU Arch : arm64-v8a
Android Serial : R52R40FGZGW
Security Patch : 2021-05-01
Connection : mtp,adb
Timezone : America/Mexico_City
Android Version : 11
Android SDK : 30
Build : RP1A.200720.012.P610XXU2CUE1
Build Date : Wed May 5 15:49:46 +07 2021
Product Code : SM-P610NZAAITV
Device Name : gta4xlwifi
Product Name : gta4xlwifixx
Code Name : SM-P610NZAAITV
BL : P610XXU2CUE1
PDA : P610XXU2CUE1
CSC : P610OXM2CUE2
Sales Code : ITV
Removing FRP... OK
UNLOCKTOOL 2025.01.06.0
Elapsed time : 1 minute 6 seconds
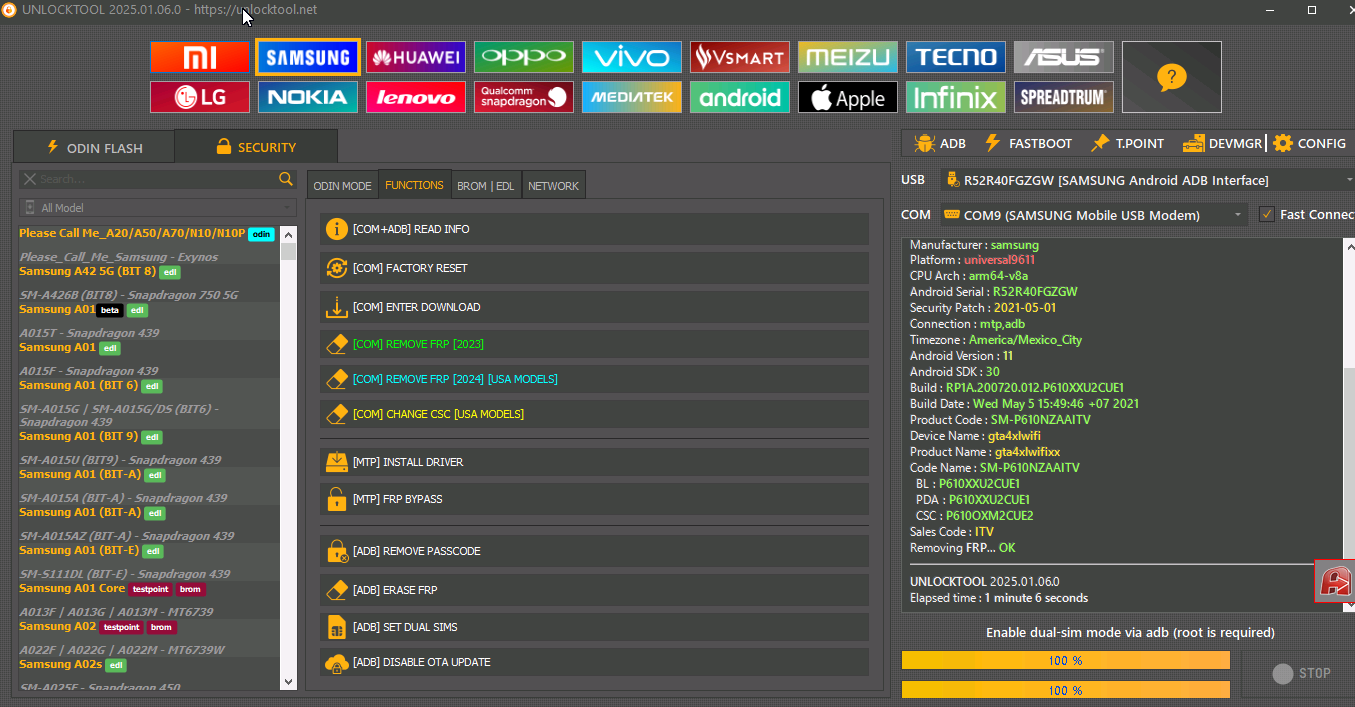
FRP Motorola one XT1941-5 by Chimera
Presiona volumen abajo + cable + encendido para entrar en Fastboot
despues seleccionar Factory Mode
seleccionar FRP
Chimera Mobile Phone Utility version: 41.58.0808 @ 2024-12-31
Preparation
Making changes
Restart
Rebooting phone to fastboot mode
Phone detected
Cleanup
Finished at local time: [12.31.24 11:37:11]
WorkID: 334331289
FRP ZTE Blade V10 Vita Spreadtrum SC9863A_64 by Pandora Box
Selected model: Spreadtrum Spreadtrum
Select->SC9863A_64
Operation: Erase FRP And Wipe
Software version: 7.10
Work ID: 55225623
Connect phone in BROM mode. Use volume key buttons or testpoint.
Waiting for device... OK
Device found at COM121
Port: USB\VID_1782&PID_4D00\6&38A36D0C&0&6
Driver: [UNISOC Communications Inc.,sprdvcom,SPRD U2S Diag,sprdvcom.sys,4.19.38.134]
Port type: BROM
Connecting to device... OK
Selected processor: SC9863A_64
Load files... (universal) OK
Connect preloader 1... OK
Connect preloader 2... OK
Connect loader 1... OK
Connect loader 2... OK
Serial Number: 726474003460
Read partitions info... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : ZTE
Product Manufacturer : ZTE
Product Model : ZTE Blade V10 Vita
Product Name : ZTE_Blade_V10_Vita
Product Device : P963F01
Product Board : sprout
Board Platform : sp9863a
Build ID : PPR1.180610.011
Build Date : Fri Apr 21 12:42:11 CST 2023
Display ID : TEL_MX_ZTE_Blade_V10_VitaV1.14
Security Patch : 2022-03-01
Version SDK : 28
Version Release : 9
Version Codename : REL
Firmware Version : 20230421.124235
Userdata FS Type : F2FS
Backup partitions... OK
Formatting "persist" partition... OK
Formatting "userdata" partition... OK
Formatting "cache" partition... OK
Formatting "metadata" partition... not found, skip
Creating default filesystems... [CACHE: EXT4] ... [USERDATA: F2FS] ... OK
Done!

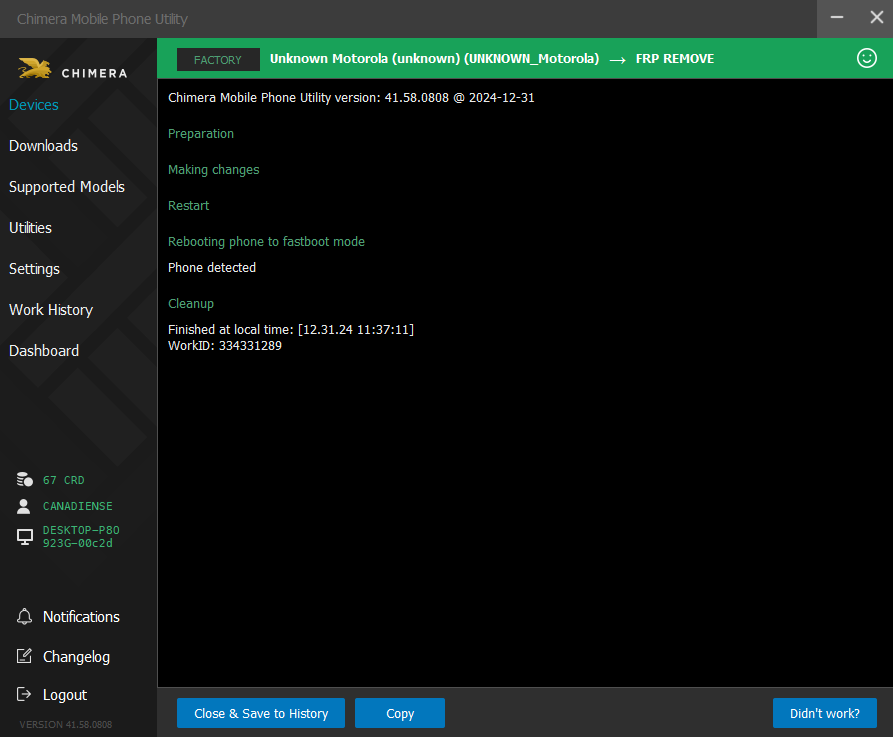
FRP Redmi Note 10 5G
Selected model: Mediatek Mediatek
Operation: Wipe Data
Software version: 7.10
There is a risk of data loss.
This procedure will erase all User Data
Make sure that you have a backup created. Continue? YES
Work ID: 54541577
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,USBSER.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM136 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0989
Get sec config... OK [000000E7]
Active sec flags: [SBC SLA DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6833]
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,USBSER.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM136 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0989
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6833]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xF0C6391A, 0xA2A3305A, 0x99D1BA4D, 0x7F3BF8EC
Get Chip ID... [MT6833]
Get SOC ID... [35EE8E5A09EDFC02D95B196FDD96F752B3ECF20EE121900BFCF44E086995CDB5]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [14]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
UFS CID (FW VER): MT128GASAO4U21 (0605)
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
UFS INFO:
UFS_CID : MT128GASAO4U21
UFS_FWVER : 0605
BLOCK_SIZE: 0x0000001000 (4.00Kb)
UFS_LU0 : 0x0000400000 (4.00Mb)
UFS_LU1 : 0x0000400000 (4.00Mb)
UFS_LU2 : 0x1DCB000000 (119.17Gb)
RAM INFO:
INT_SRAM: 0x0000070000 (448.00Kb)
EXT_RAM : 0x0100000000 (4.00Gb)
HEALTH:
Pre EOL Info: normal
DeviceLifeTimeEstA: 40% - 50% device life time used
DeviceLifeTimeEstB: 20% - 30% device life time used
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK [A]
Read product info... [EXT4] ... OK
Product Brand : Redmi
Product Manufacturer : Xiaomi
Product Model : M2103K19C
Product Name : camellia
Product Device : camellia
Product Board : camellia
Board Platform : mt6833
Build ID : SP1A.210812.016
Build Date : Wed Jun 14 15:07:19 UTC 2023
Display ID : TP1A.220624.014
Security Patch : 2023-06-01
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : V14.0.5.0.TKSMIXM
Userdata FS Type : F2FS
Formatting "userdata" partition... OK
Formatting "metadata" partition... OK
Formatting "frp" partition... OK
Wipe data done!
FRP data done!
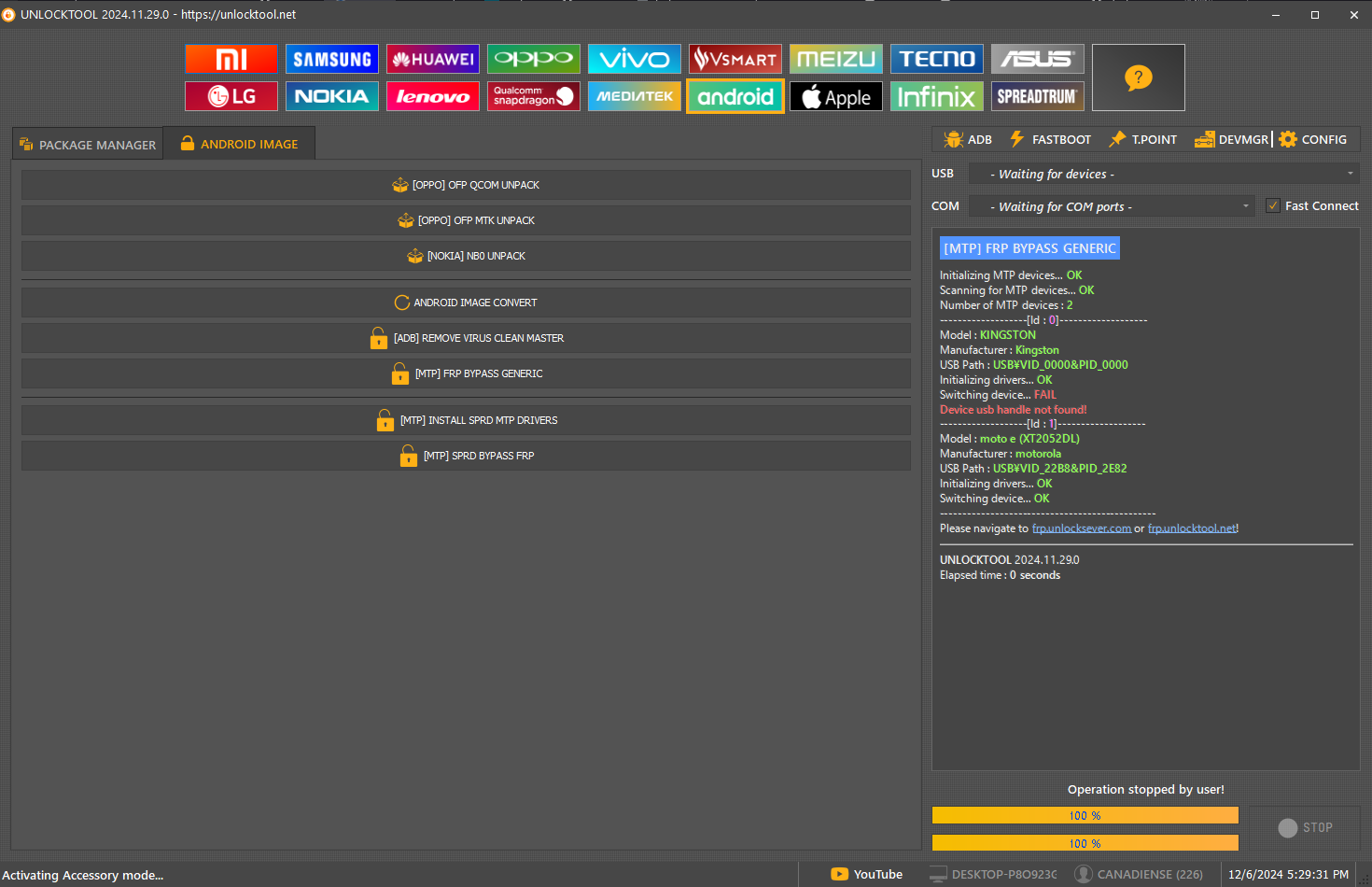
FRP Moto e (XT2052DL)
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:001724 SourceURL:file%3a%2f%2f
[MTP] FRP BYPASS GENERIC
Initializing MTP devices...
OK
Scanning for MTP devices...
OK
Number of MTP devices :
2
-------------------[Id :
0
]-------------------
Model :
KINGSTON
Manufacturer :
Kingston
USB Path :
USB\VID_0000&PID_0000
Initializing drivers...
OK
Switching device...
FAIL
Device usb handle not found!
-------------------[Id :
1
]-------------------
Model :
moto e (XT2052DL)
Manufacturer :
motorola
USB Path :
USB\VID_22B8&PID_2E82
Initializing drivers...
OK
Switching device...
OK
-----------------------------------------------
Please navigate to
or
!
UNLOCKTOOL
2024.11.29.0
Elapsed time :
0 seconds
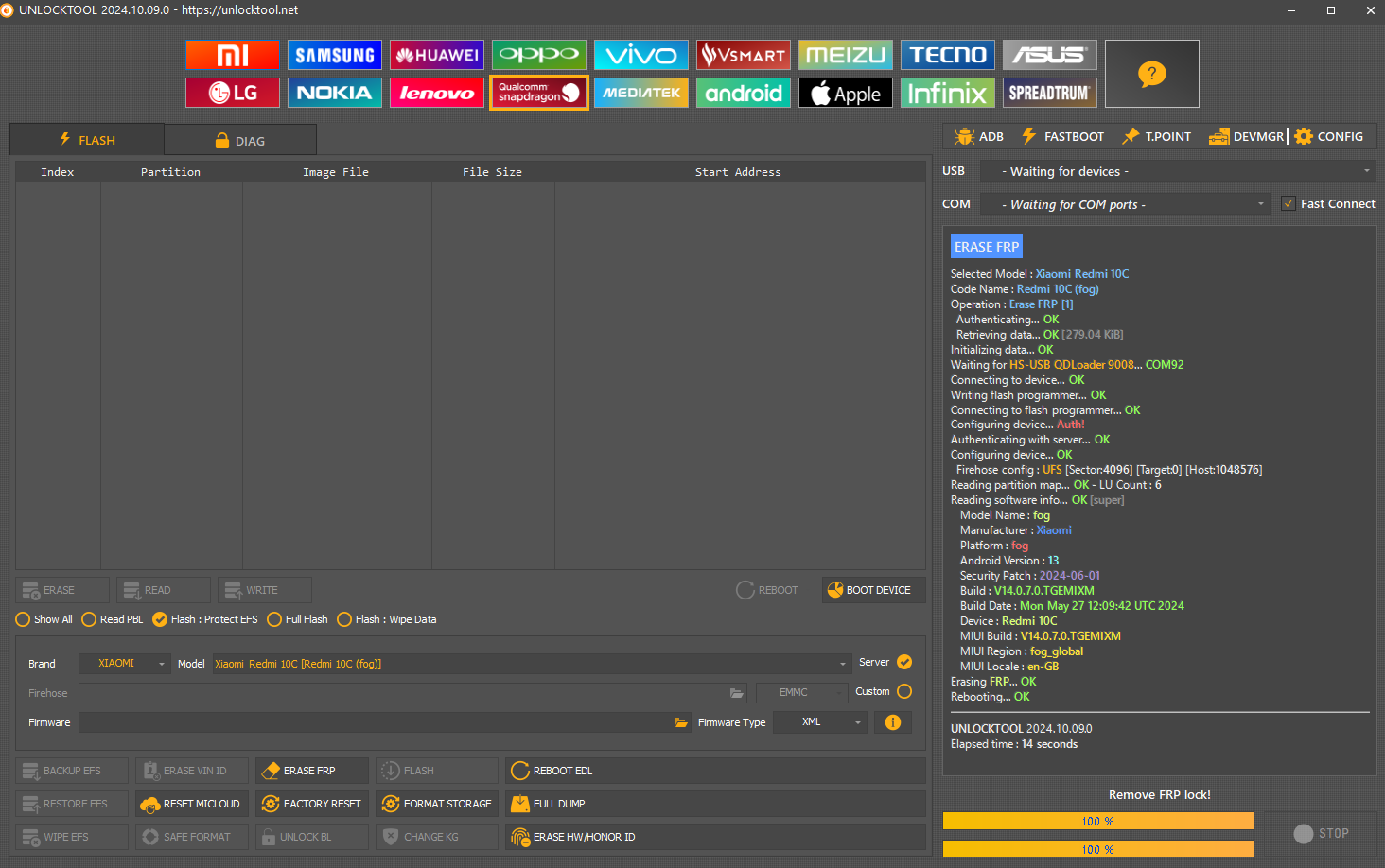
FRP Xiomi Redmi 10C By Unlocktool

ERASE FRP
Selected Model :
Xiaomi Redmi 10C
Code Name :
Redmi 10C (fog)
Operation :
Erase FRP [1]
Authenticating...
OK
Retrieving data...
OK
[279.04 KiB]
Initializing data...
OK
Waiting for
HS-USB QDLoader 9008
...
COM92
Connecting to device...
OK
Writing flash programmer...
OK
Connecting to flash programmer...
OK
Configuring device...
Auth!
Authenticating with server...
OK
Configuring device...
OK
Firehose config :
UFS
[Sector:
4096
] [Target:
0
] [Host:
1048576
]
Reading partition map...
OK
- LU Count :
6
Reading software info...
OK
[super]
Model Name :
fog
Manufacturer :
Xiaomi
Platform :
fog
Android Version :
13
Security Patch :
2024-06-01
Build :
V14.0.7.0.TGEMIXM
Build Date :
Mon May 27 12:09:42 UTC 2024
Device :
Redmi 10C
MIUI Build :
V14.0.7.0.TGEMIXM
MIUI Region :
fog_global
MIUI Locale :
en-GB
Erasing
FRP
...
OK
Rebooting...
OK
UNLOCKTOOL
2024.10.09.0
Elapsed time :
14 seconds
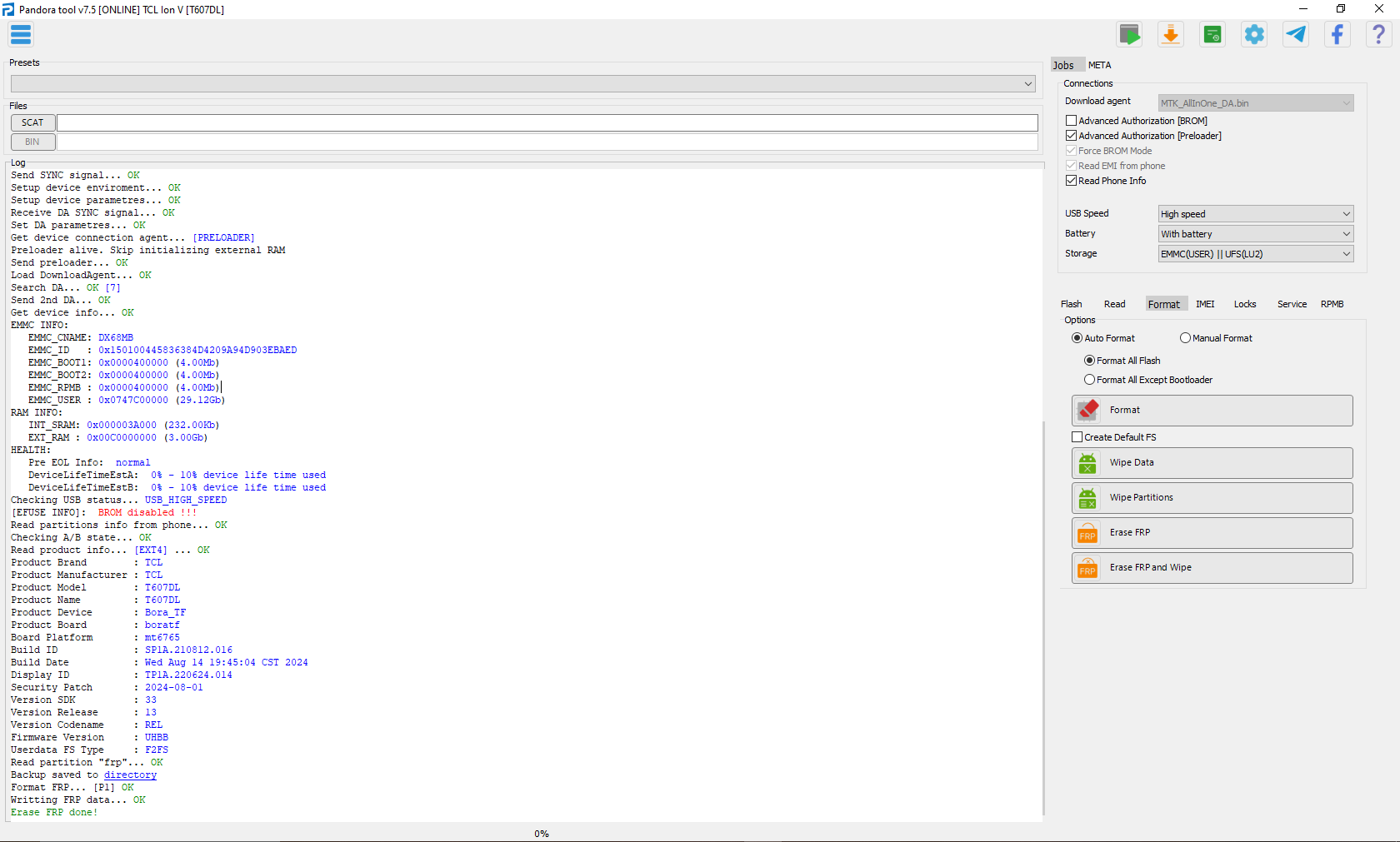
FRP TCL T607DL (TCL Ion V) By Pandora Tool
Selected model: TCL T607DL (TCL Ion V)
Operation: Erase FRP
Software version: 7.5
Work ID: 46591401
Connect phone in PRELOADER Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek PreLoader USB VCOM (Android),usb2ser.sys,3.0.1504.0]
Device found at COM45 [PRELOADER]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [00000007]
Active sec flags: [SBC SLA DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Preloader exist. Skip connection verification.
Get ME ID... OK
ME_ID = 0xD98CBD1E, 0x0CCF2849, 0x1FAA967F, 0x80D99633
Get hw mode... OK
Load DownloadAgent... OK
Search DA... OK [0]
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [PRELOADER]
Preloader alive. Skip initializing external RAM
Send preloader... OK
Load DownloadAgent... OK
Search DA... OK [7]
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: DX68MB
EMMC_ID : 0x150100445836384D4209A94D903EBAED
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0000400000 (4.00Mb)
EMMC_USER : 0x0747C00000 (29.12Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x00C0000000 (3.00Gb)
HEALTH:
Pre EOL Info: normal
DeviceLifeTimeEstA: 0% - 10% device life time used
DeviceLifeTimeEstB: 0% - 10% device life time used
Checking USB status... USB_HIGH_SPEED
[EFUSE INFO]: BROM disabled !!!
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : TCL
Product Manufacturer : TCL
Product Model : T607DL
Product Name : T607DL
Product Device : Bora_TF
Product Board : boratf
Board Platform : mt6765
Build ID : SP1A.210812.016
Build Date : Wed Aug 14 19:45:04 CST 2024
Display ID : TP1A.220624.014
Security Patch : 2024-08-01
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : UHBB
Userdata FS Type : F2FS
Read partition "frp"... OK
Backup saved to C:/Program%20Files%20(x86)/Z3X/Pandora/Backup/MTK/TCL_T607DL%20(TCL%20Ion%20V)/FRP_BACKUP_(2024-10-18_13-51-45)/
Format FRP... [P1] OK
Writting FRP data... OK
Erase FRP done!
FRP Samsung G532M TELCEL Android 6
FRP Samsung G532M Android 6
Agregar wifi poner letras y seleccionar para abrir google
despues abrir chrome y abrir vnROM
Seleccionar Test DCP configurar
Reiniciar y listo a cobrar
https://www.youtube.com/watch?v=qIcYz5elBUE
Using port SAMSUNG Mobile USB Modem #17 (COM40)
Reading info mode MTP ... OK
Model : SM-G532M
CSC : SM-G532MZKATCE
AP version : G532MUBU1ASA1
BL version : G532MUBU1ASA1
CP version : G532MUBU1ASA1
CSC version : G532MTCE1ASC1
IMEI : 358215082180748
SN : RV8J605Q6ZW
Lock status : NONE
MCC : 334
MNC : 020
USB mode : AT,MTP
Unique number : CQN0072004FBB44
Android version : 6.0.1
FRP status : TRIGGERED
Firmware : https://samfw.com/firmware/SM-G532M/SM-G532MZKATCE
Using port SAMSUNG Mobile USB Modem #17 (COM40)
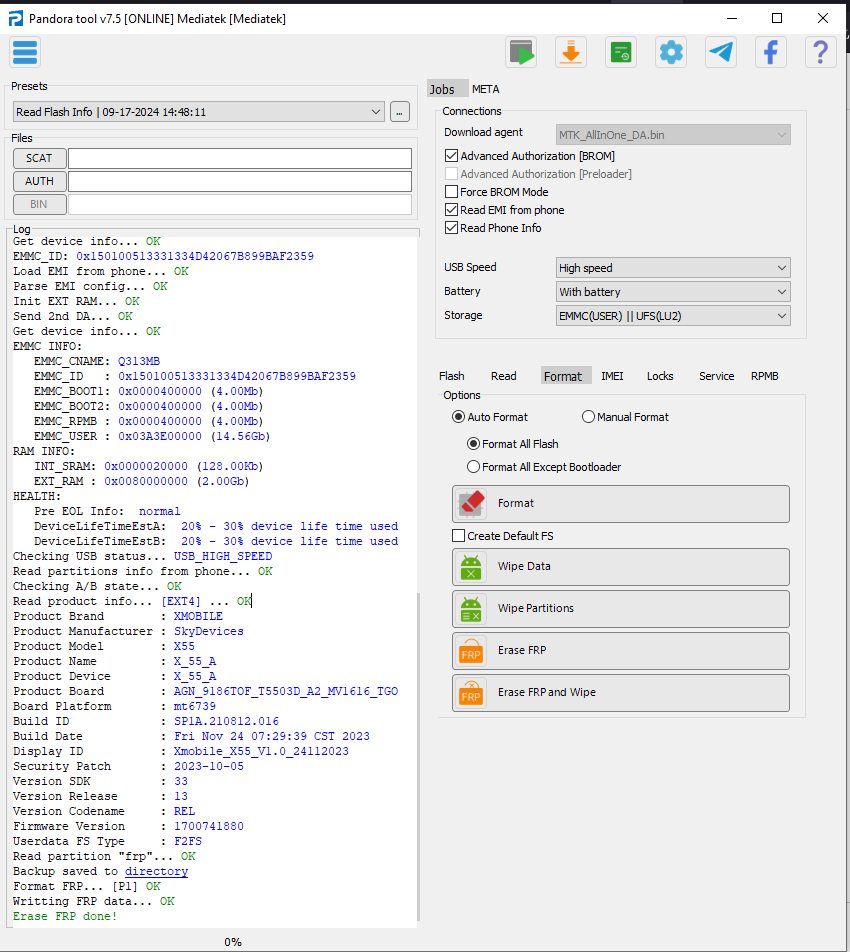
FRP XMOBILE X55 by Pandora Tool
Selected model: Mediatek Mediatek
Operation: Erase FRP
Software version: 7.5
Work ID: 44118693
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,USBSER.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM118 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0699
Get sec config... OK [00000000]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6739]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xEF5929B4, 0xD94182C0, 0x16CD59D2, 0x34927EB2
Get Chip ID... [MT6739]
Get SOC ID... [7F4F84A80646400BAA0928C1C2F952527E31D80B1B7F4857A676BDE490361AE8]
Get sec config... OK [00000000]
Load DownloadAgent... OK
Search DA... OK [1]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x150100513331334D42067B899BAF2359
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: Q313MB
EMMC_ID : 0x150100513331334D42067B899BAF2359
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0000400000 (4.00Mb)
EMMC_USER : 0x03A3E00000 (14.56Gb)
RAM INFO:
INT_SRAM: 0x0000020000 (128.00Kb)
EXT_RAM : 0x0080000000 (2.00Gb)
HEALTH:
Pre EOL Info: normal
DeviceLifeTimeEstA: 20% - 30% device life time used
DeviceLifeTimeEstB: 20% - 30% device life time used
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : XMOBILE
Product Manufacturer : SkyDevices
Product Model : X55
Product Name : X_55_A
Product Device : X_55_A
Product Board : AGN_9186TOF_T5503D_A2_MV1616_TGO
Board Platform : mt6739
Build ID : SP1A.210812.016
Build Date : Fri Nov 24 07:29:39 CST 2023
Display ID : Xmobile_X55_V1.0_24112023
Security Patch : 2023-10-05
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : 1700741880
Userdata FS Type : F2FS
Read partition "frp"... OK
Backup saved to C:/Program%20Files%20(x86)/Z3X/Pandora/Backup/MTK/Mediatek_MT6739/FRP_BACKUP_(2024-9-28_18-40-0)/
Format FRP... [P1] OK
Writting FRP data... OK
Erase FRP done!
FRP REDMI 9T
TEST POINT
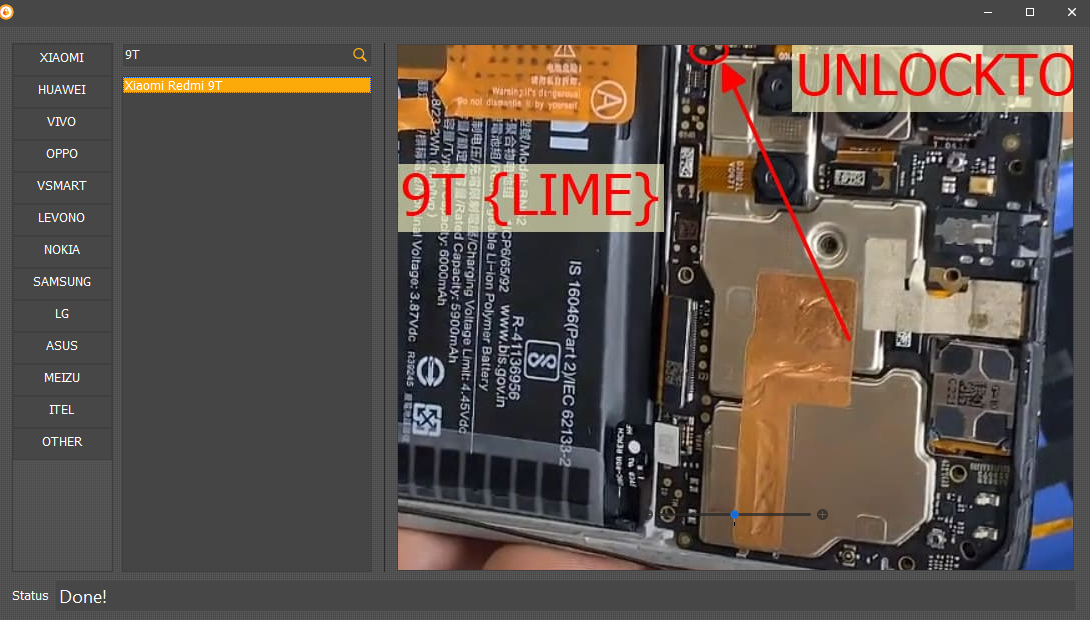
[EDL] ERASE FRP
Selected Model :
Xiaomi Redmi 9T / Redmi 9 / Redmi 9 Power
Code Name :
(lime)
Operation :
Erase FRP [1]
Authenticating...
OK
Retrieving data...
OK
[270.92 KiB]
Initializing data...
OK
Waiting for
HS-USB QDLoader 9008
...
COM80
Connecting to device...
OK
Handshaking...
OK
Reading bootloader info...
OK
Serial :
2505305946
SoC : [
Snapdragon 662
] [
SM6115
] [
0x0014D0E1
]
OEM :
Xiaomi [0x0072]
Model :
Unknown [0x0000]
PK_HASH[0] : 1BEBE3863A6781DB4B01086063007334
PK_HASH[1] : DE9E5CA14971C7C4F4358EC9D79CDA46
Writing flash programmer...
OK
Connecting to flash programmer...
OK
Configuring device...
OK
Firehose config :
UFS
[Sector:
4096
] [Target:
0
] [Host:
1048576
]
Reading partition map...
OK
- LU Count :
6
Reading software info...
OK
[super]
Model Name :
Lime for arm64
Product Name :
lime
Manufacturer :
Xiaomi
Platform :
lime
Android Version :
12
Security Patch :
2022-12-01
Build ID :
Android-Q-build-20221205011709
Build :
V13.0.2.0.SJQMIXM
Build Date :
Mon Dec 5 01:14:22 CST 2022
MIUI Version :
V130
MIUI Build :
V13.0.2.0.SJQMIXM
MIUI Region :
lime_global
MIUI Locale :
en-GB
Erasing
FRP
...
OK
Rebooting...
OK
UNLOCKTOOL
2024.09.02.0
Elapsed time :
4 minutes 27 seconds
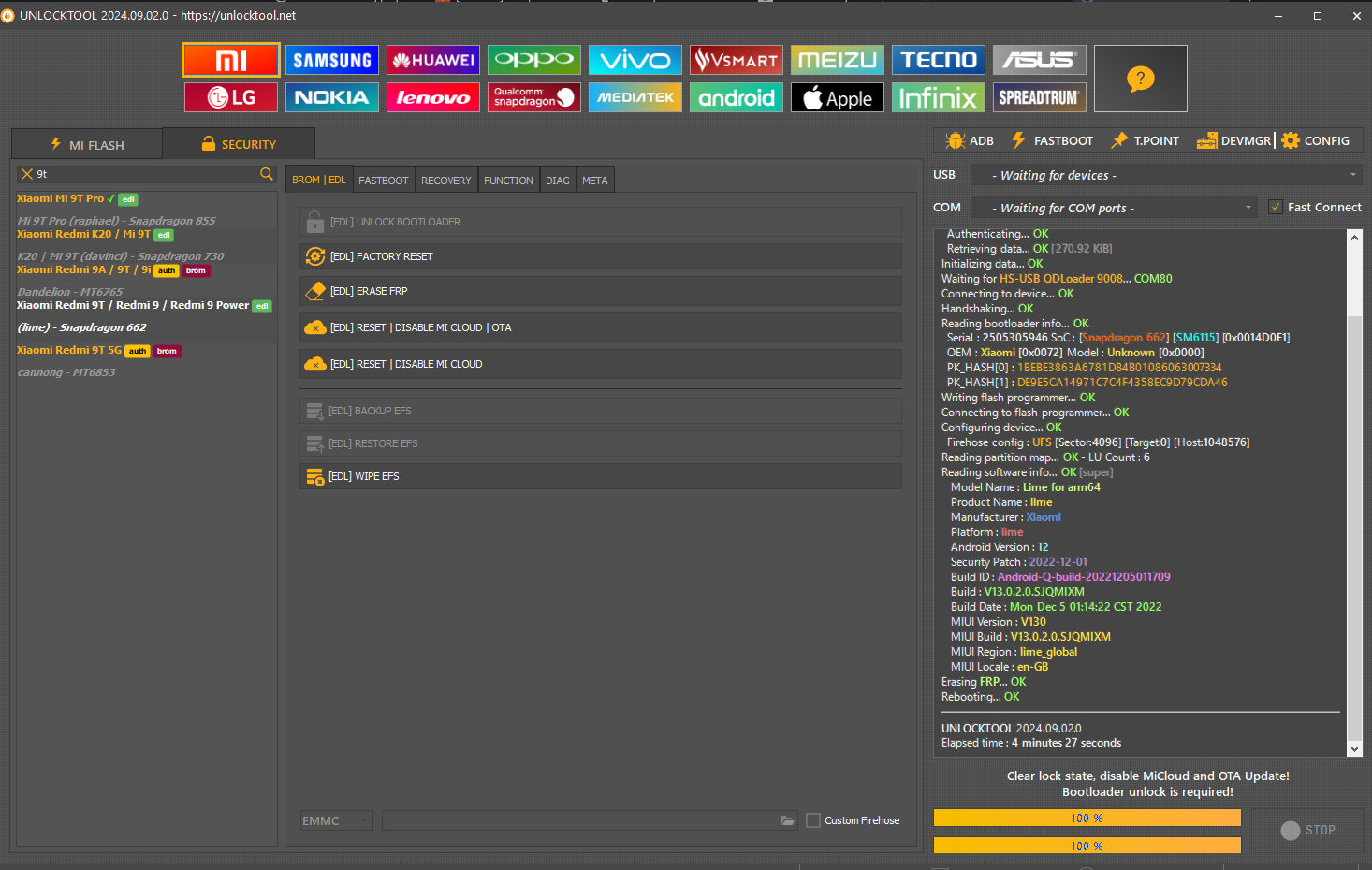
FRP Motorola XT1635-02 Moto Z Play by UMT Box
Brand : Motorola
Model : XT1635
Operation : Reset FRP
Searching for Device in FastBoot Mode...OK
Reading Phone Information...OK
Model : XT1635-02
Boot Ver. : moto-msm8953-C1.82
Baseband : M8953_10238.63.04.83.01R ADDISON_ROW_CUST
Software : Blur_Version.27.231.10.addison.retail.en.US
IMEI : 358212072705519
CPU : MSM8953
RAM : 3GB SAMSUNG LP3 DIE=6Gb M5=01 M6=05 M7=00 M8=7B
EMMC : 32GB SAMSUNG RX1BMB RV=08 PV=07 FV=0000000000000007
Setting Factory Mode...OK
Searching Network Interface...Found
Connecting to device...OK
Model : XT1635-02
Bootloader : 0xC182
Baseband : M8953_10238.63.04.83.01R ADDISON_ROW_CUST
Build : Blur_Version.27.231.10.addison.retail.en.US
Android : 8.0.0
Searching Network Interface...Found
Connecting to device...OK
Model : XT1635-02
Bootloader : 0xC182
Baseband : M8953_10238.63.04.83.01R ADDISON_ROW_CUST
Build : Blur_Version.27.231.10.addison.retail.en.US
Android : 8.0.0
Retetting FRP...OK
Searching for Device in FastBoot Mode...OK
Removing Factory Mode...OK
Operation Finished.
UltimateFRP Ver. 0.5.1
Samsung Worldwide FRP SM-A356E By IMEI Unlock INSTANT Galaxy A35 5G
Unlock.mx offer Samsung FRP by IMEI instant service
Model Name : Galaxy A35 5G Model Number : SM-A356E IMEI : 35460034XXXXXXX Status : Register successful, Enter the phone into recovery mode and choose repair apps Or factory reset It will take 3-4 minutes, then connect wifi and complete the setup. If you are late, the order will be cancelled
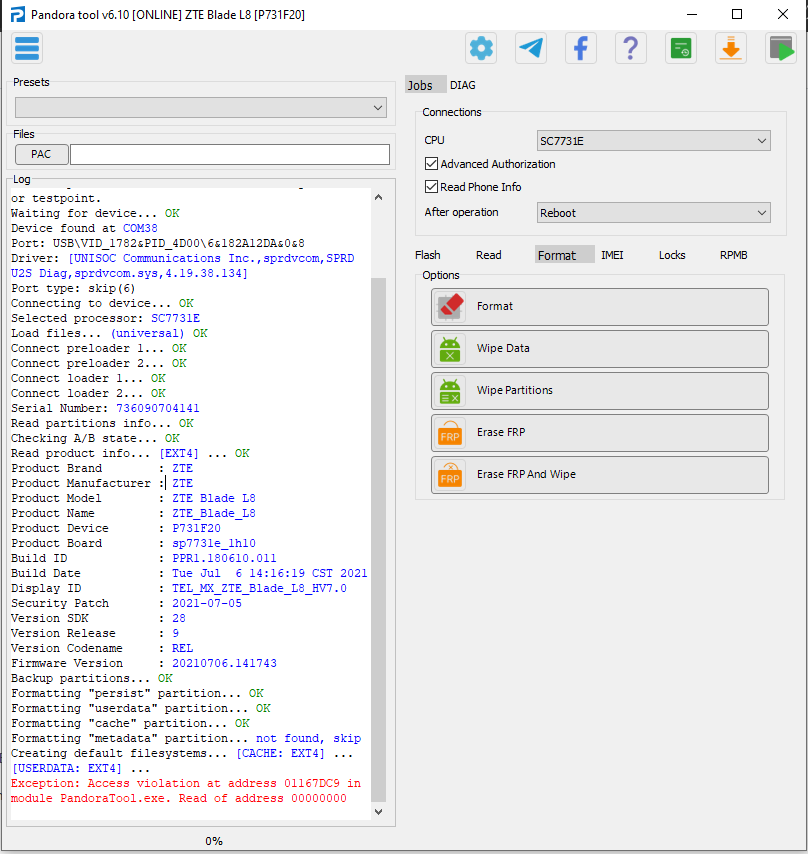
FRP ZTE Blade L8 SPD Unisoc sp7731e by Pandora Box
Apagado presionar volumen - conectar cable USB
Selected model: ZTE P731F20 (ZTE Blade L8)
Operation: Erase FRP And Wipe
Software version: 6.10
Work ID: 34580165
Connect phone in BROM mode. Use volume key buttons or testpoint.
Waiting for device... OK
Device found at COM38
Port: USB\VID_1782&PID_4D00\6&182A12DA&0&8
Driver: [UNISOC Communications Inc.,sprdvcom,SPRD U2S Diag,sprdvcom.sys,4.19.38.134]
Port type: skip(6)
Connecting to device... OK
Selected processor: SC7731E
Load files... (universal) OK
Connect preloader 1... OK
Connect preloader 2... OK
Connect loader 1... OK
Connect loader 2... OK
Serial Number: 736090704141
Read partitions info... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : ZTE
Product Manufacturer : ZTE
Product Model : ZTE Blade L8
Product Name : ZTE_Blade_L8
Product Device : P731F20
Product Board : sp7731e_1h10
Build ID : PPR1.180610.011
Build Date : Tue Jul 6 14:16:19 CST 2021
Display ID : TEL_MX_ZTE_Blade_L8_HV7.0
Security Patch : 2021-07-05
Version SDK : 28
Version Release : 9
Version Codename : REL
Firmware Version : 20210706.141743
Backup partitions... OK
Formatting "persist" partition... OK
Formatting "userdata" partition... OK
Formatting "cache" partition... OK
Formatting "metadata" partition... not found, skip
Creating default filesystems... [CACHE: EXT4] ... [USERDATA: EXT4] ...
Exception: Access violation at address 01167DC9 in module PandoraTool.exe. Read of address 00000000
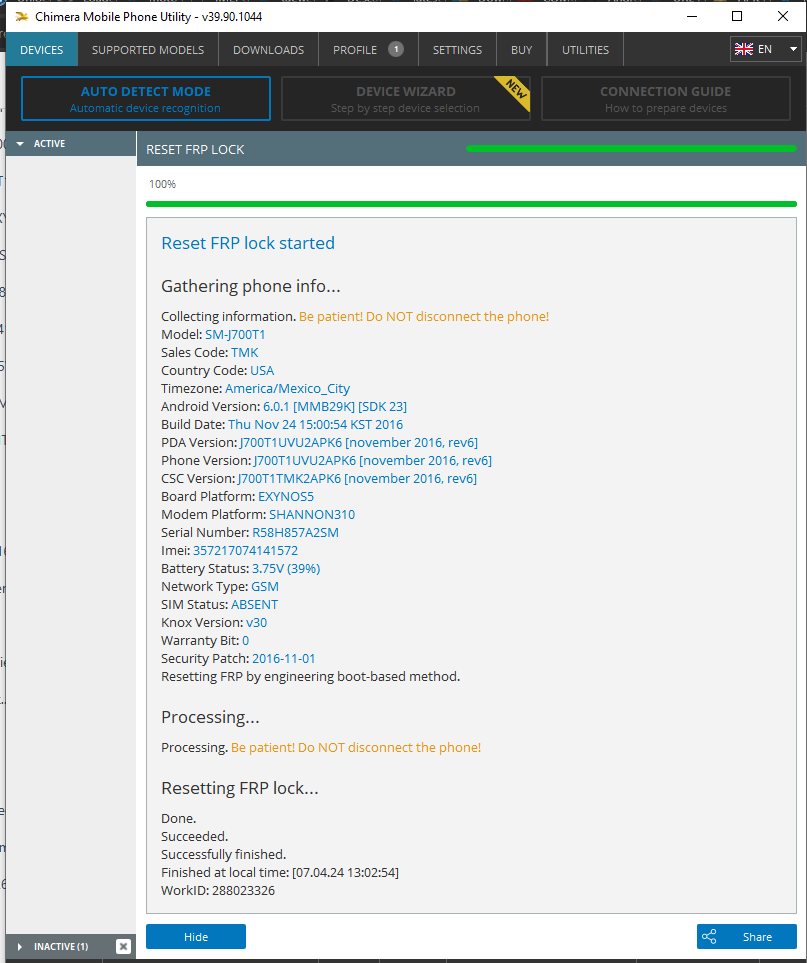
FRP Samsung SM-J700T1 by Chimera
- llamada de emergencia asterisco # 0 asterisco #
- conectar el cable usb y seleccionar FRP
Chimera Mobile Phone Utility version: 39.90.1044 @ 2024-07-04
Reset FRP lock started
Gathering phone info...
Collecting information. Be patient! Do NOT disconnect the phone!
Model: SM-J700T1
Sales Code: TMK
Country Code: USA
Timezone: America/Mexico_City
Android Version: 6.0.1 [MMB29K] [SDK 23]
Build Date: Thu Nov 24 15:00:54 KST 2016
PDA Version: J700T1UVU2APK6 [november 2016, rev6]
Phone Version: J700T1UVU2APK6 [november 2016, rev6]
CSC Version: J700T1TMK2APK6 [november 2016, rev6]
Board Platform: EXYNOS5
Modem Platform: SHANNON310
Serial Number: R58H857A2SM
Imei: 357217074141572
Battery Status: 3.75V (39%)
Network Type: GSM
SIM Status: ABSENT
Knox Version: v30
Warranty Bit: 0
Security Patch: 2016-11-01
Resetting FRP by engineering boot-based method.
Processing...
Processing. Be patient! Do NOT disconnect the phone!
Resetting FRP lock...
Done.
Succeeded.
Successfully finished.
Finished at local time: [07.04.24 13:02:54]
WorkID: 288023326
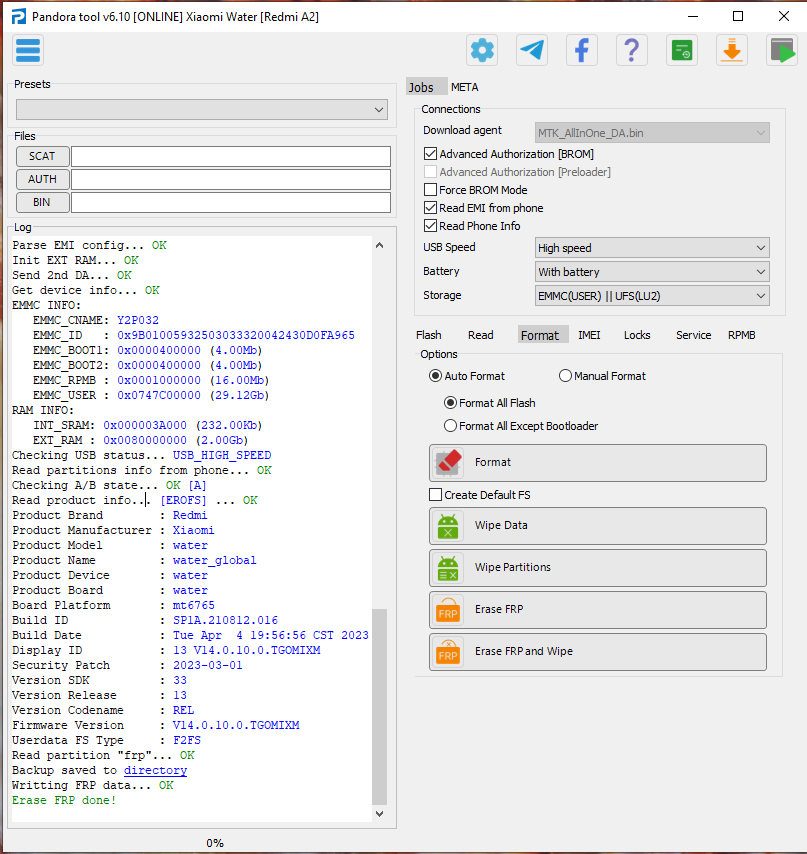
FRP Xiaomi Redmi A2 MT6765
Selected model: Xiaomi Redmi A2 (Water)
Operation: Erase FRP
Software version: 6.10
Work ID: 33909264
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM24 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E7]
Active sec flags: [SBC SLA DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Install LibUSB... OK
Waiting for device... OK
Open port... OK
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,wdm_usb,MediaTek USB Port,usb2ser.sys,3.0.1504.0]
Device found at COM24 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0xDEA08034, 0x8D71ED74, 0xCC0F1640, 0x56DA47C3
Get Chip ID... [MT6765]
Get SOC ID... [E670C7046E455F8CE0D586A36BE347B1CFB0902C86CC4CE9B18DBAECC5309667]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [7]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x9B01005932503033320042430D0FA965
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: Y2P032
EMMC_ID : 0x9B01005932503033320042430D0FA965
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0001000000 (16.00Mb)
EMMC_USER : 0x0747C00000 (29.12Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x0080000000 (2.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK [A]
Read product info... [EROFS] ... OK
Product Brand : Redmi
Product Manufacturer : Xiaomi
Product Model : water
Product Name : water_global
Product Device : water
Product Board : water
Board Platform : mt6765
Build ID : SP1A.210812.016
Build Date : Tue Apr 4 19:56:56 CST 2023
Display ID : 13 V14.0.10.0.TGOMIXM
Security Patch : 2023-03-01
Version SDK : 33
Version Release : 13
Version Codename : REL
Firmware Version : V14.0.10.0.TGOMIXM
Userdata FS Type : F2FS
Read partition "frp"... OK
Backup saved to C:/Program%20Files%20(x86)/Z3X/Pandora/Backup/MTK/Xiaomi_Redmi%20A2%20(Water)/FRP_BACKUP_(2024-7-3_15-16-21)/
Writting FRP data... OK
Erase FRP done!
Reset Protection Recovery Key Lumia 640 RM-1073
C:\iutool>iutool
(IUTool Version: 11:52:10/Feb 7 2014)
Command-Line Usage:
Command lines
-?
-p path [-s name] [-n name] [-m manufacturer] [-t model] [-a] [-v] [-V]
-l
Options
-? Show list of commands and usage
-V show VERY detailed progress messages
-a update all connected devices in parallel
-l list the connected devices
-m the phone's manufacturer
-n the phone's friendly name
-p directory path or semicolon-delimited list of package paths
-s the phone's serial number
-t the phone's type (model name)
-v show detailed progress messages
Install update files onto a device.
Command failed. (HRESULT = 0x80dd0001)

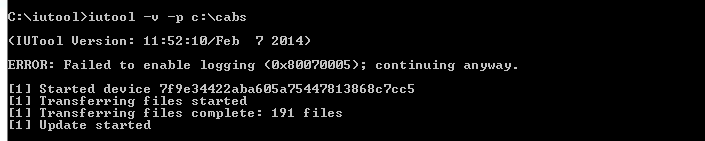
FRP Oppo A53 UFS (CPH2127) by UMT QC
- Conectar el cable USB con el telefono prendido
- Seleccionar Apagar y presionar al mismo tiempo volumen arriba + volumen abajo
- activar casilla Reset FRP y presionar Execute
Model : Oppo A53 UFS (CPH2127)
Operation : Erase Userdata
Checking for existing devices...Not Found
Turn Off phone, hold Vol UP + Vol DOWN and insert USB cable.
Some phones may need Special Boot Cable or TestPoint for EDL mode.
Found Port : Qualcomm HS-USB QDLoader 9008 (COM11)
Driver Info : Qualcomm Incorporated, qcusbser.sys, 2.1.2.0
Connecting to phone...OK
Waiting for response...OK
Init Handshake Sequence...OK
Hardware ID : E1601300 [SDM460] 00005100
OPK_DATA : 19CF99D55CA3B2E11EA19E52E3541DEDF01898FD9F8C40E62548F1C7F60ABD47
Initializing Protocol...OK
Preparing Loader...Done
Sending Loader [CPH2127]...Done
Executing Loader...OK
Initializing Storage...OK
Read : Allowed
Write : Protected
Alt. Write : Allowed
Alt. Write is allowed, using Factory Format Method...Done
Erasing FRP Data...Done
Operation Finished.
QcFire Ver. 10.2
FRP Motorola E5 XT1944-3
Searching fastboot device ...
Device found
Reading device Info ...
Modal : XT1944-3
IMEI : 355561091633265
Version : 0.5
Bootloader : moto-msm8917-BE.4F
Stroage Type : emmc
Ram : 2GB SAMSUNG LP3 DIE=8Gb M5=01 M6=06 M7=00 M8=1F
UID : BAF3BB1B00000000000000000000
Relased Date : 06-12-2018
CPU : MSM8917
Serial No. : ZY322SC6B8
Cid : 0x0032
Secure : yes
eMMC : 16GB SAMSUNG QE63MB RV=08 PV=03 FV=0000000000000003
Warranty Void : no
Kernel Version : Linux version 3.18.71-perf-gc1d4a268e3b8
Setting Factory Mode... Done
Connecting to device... OK
Android Version :
Bootloader : moto-msm8917-BE.4F
Baseband :
Connecting to device... OK
Android Version :
Bootloader : moto-msm8917-BE.4F
Baseband :
Model : moto e5
Manufucture : motorola
Android Version : 8.0.0
Android OS : Oreo
CPU : armeabi-v7a
Security Patch : 2020-05-01
Platform : msm8937
Hardware : qcom
Board : msm8937
Bootloader : 0xBE4F
USB Config : usbnet,adb
User : hudsoncm
Display ID : OPPS27.91-176-11-16
Build ID : OPPS27.91-176-11-16
Build Date : Mon Apr 27 13:12:40 CDT 2020
Build Tags : release-keys
LCD Density : 320
Data Encryption : encrypted
Resetting Frp..... DONE
All done Successfully.
UAT PRO : 170.01 | 22 - May - 2024 [ 10:47:41 AM ] MEXICO
Elapsed Time : 3 minutes 12 seconds

Samsung SM-A145M by Global Unlocker
Costo 8 Creditos
CPU EXYNOS 3830
Press button Samsung FRP / MDM seleccionar modo Samsung primera opcion
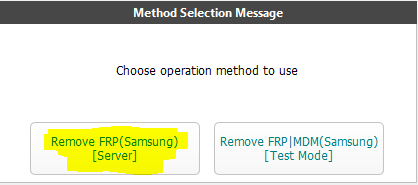
* # 0 * #
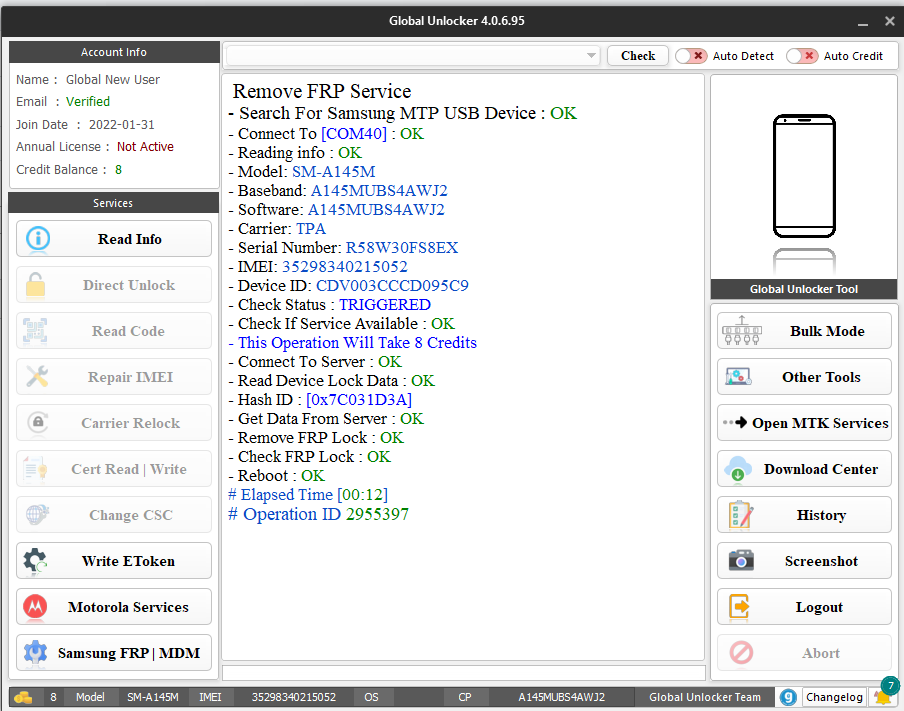
Remove FRP Service
- Search For Samsung MTP USB Device : OK
- Connect To [COM40] : OK
- Reading info : OK
- Model: SM-A145M
- Baseband: A145MUBS4AWJ2
- Software: A145MUBS4AWJ2
- Carrier: TPA
- Serial Number: R58W30FS8EX
- IMEI: 35298340215052
- Device ID: CDV003CCCD095C9
- Check Status : TRIGGERED
- Check If Service Available : OK
- This Operation Will Take 8 Credits
- Connect To Server : OK
- Read Device Lock Data : OK
- Hash ID : [0x7C031D3A]
- Get Data From Server : OK
- Remove FRP Lock : OK
- Check FRP Lock : OK
- Reboot : OK
# Elapsed Time [00:12]
# Operation ID 2955397
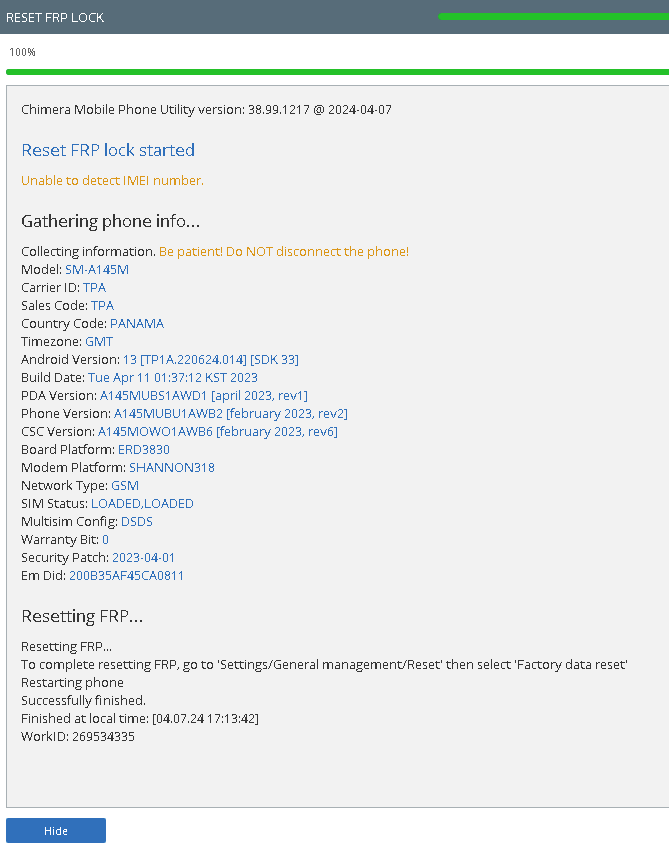
FRP Samsung SM-A145M by Chimera Tool
CPU INSIDE - EXYNOS 3830
Test Point

Chimera Mobile Phone Utility version: 38.99.1217 @ 2024-04-07
Reset FRP lock started
Unable to detect IMEI number.
Gathering phone info...
Collecting information. Be patient! Do NOT disconnect the phone!
Model: SM-A145M
Carrier ID: TPA
Sales Code: TPA
Country Code: PANAMA
Timezone: GMT
Android Version: 13 [TP1A.220624.014] [SDK 33]
Build Date: Tue Apr 11 01:37:12 KST 2023
PDA Version: A145MUBS1AWD1 [april 2023, rev1]
Phone Version: A145MUBU1AWB2 [february 2023, rev2]
CSC Version: A145MOWO1AWB6 [february 2023, rev6]
Board Platform: ERD3830
Modem Platform: SHANNON318
Network Type: GSM
SIM Status: LOADED,LOADED
Multisim Config: DSDS
Warranty Bit: 0
Security Patch: 2023-04-01
Em Did: 200B35AF45CA0811
Resetting FRP...
Resetting FRP...
To complete resetting FRP, go to 'Settings/General management/Reset' then select 'Factory data reset'
Restarting phone
Successfully finished.
Finished at local time: [04.07.24 17:13:42]
WorkID: 269534335
FRP Samsung SM-A025M
Conectar Test Point + Cable
ERASE FRP Selected Platform : SC9863A_32_Bypass
Connect Testpoint or hold VOL DOWN! Instruction here!
Waiting for device... COM68 (SPRD U2S Diag)
USB : USB\VID_1782&PID_4D00\5&1B14D878&0&3
Initializing loader... OK
Protocol : SPRD3
Sending payload... OK
Sending auth data... OK
Sending preloader1... OK
Sending preloader2... OK
Booting loader, please wait... OK
Boot ver: Spreadtrum Boot Block version 1.1
Sending FDL1... OK
Sending FDL2... OK
Reading Serial Number... N.A
Reading partitions info... OK [56] [1024]
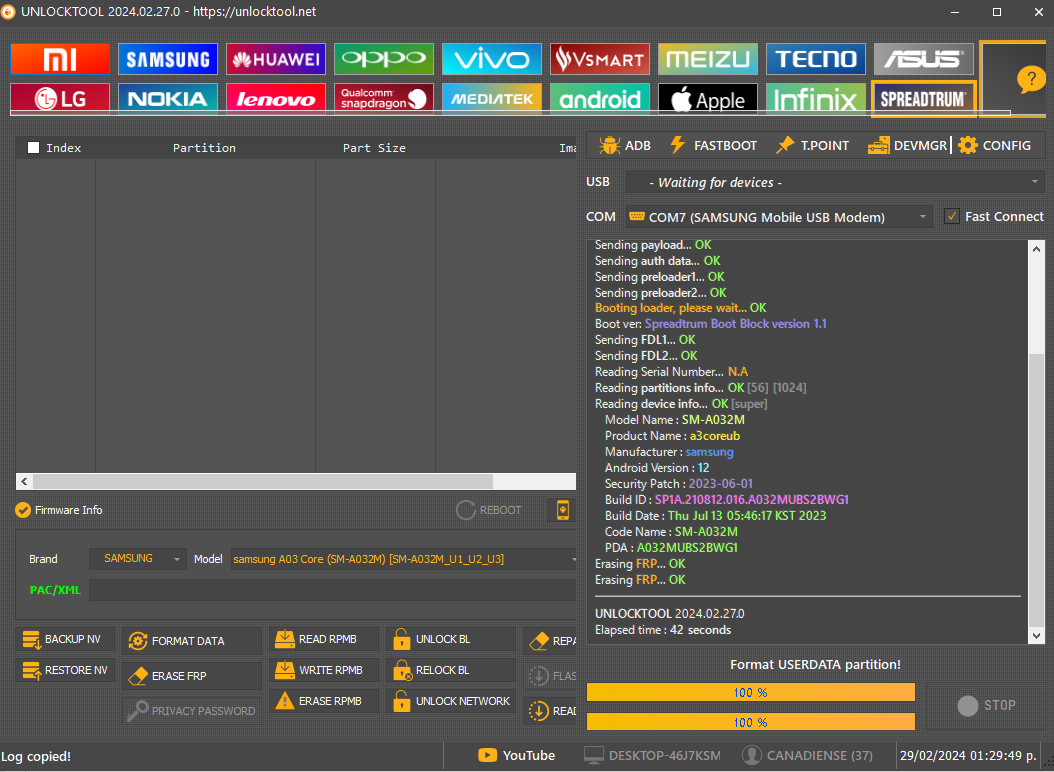
Reading device info... OK [super]
Model Name : SM-A032M
Product Name : a3coreub
Manufacturer : samsung
Android Version : 12
Security Patch : 2023-06-01
Build ID : SP1A.210812.016.A032MUBS2BWG1
Build Date : Thu Jul 13 05:46:17 KST 2023
Code Name : SM-A032M
PDA : A032MUBS2BWG1
Erasing FRP... OK
Erasing FRP... OK
UNLOCKTOOL 2024.02.27.0
Elapsed time : 42 seconds
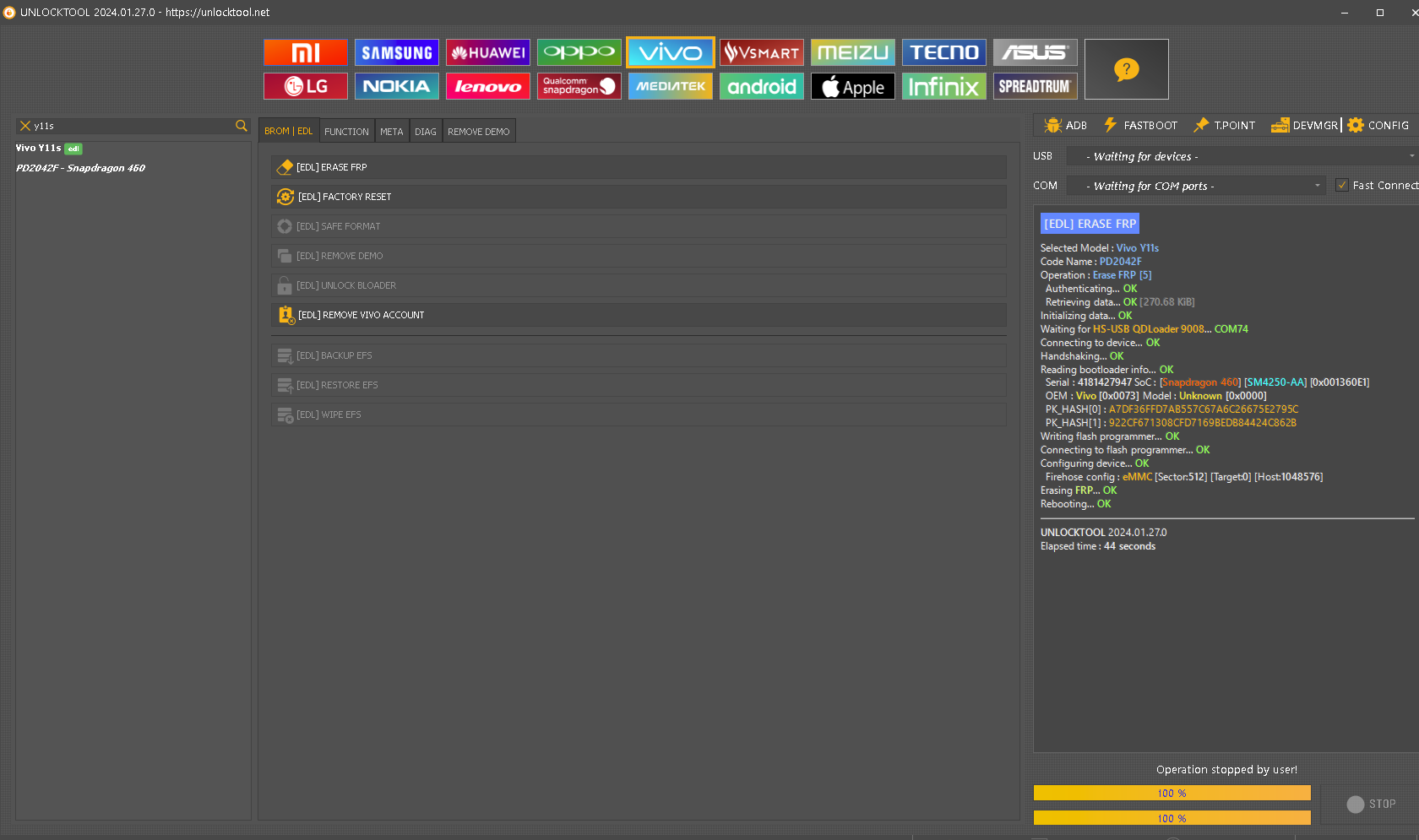
FRP Vivo Y11s
Hacer Test Point
[EDL] ERASE FRP
Selected Model :
Vivo Y11s
Code Name :
PD2042F
Operation :
Erase FRP [5]
Authenticating...
OK
Retrieving data...
OK
[270.68 KiB]
Initializing data...
OK
Waiting for
HS-USB QDLoader 9008
...
COM74
Connecting to device...
OK
Handshaking...
OK
Reading bootloader info...
OK
Serial :
4181427947
SoC : [
Snapdragon 460
] [
SM4250-AA
] [
0x001360E1
]
OEM :
Vivo [0x0073]
Model :
Unknown [0x0000]
PK_HASH[0] : A7DF36FFD7AB557C67A6C26675E2795C
PK_HASH[1] : 922CF671308CFD7169BEDB84424C862B
Writing flash programmer...
OK
Connecting to flash programmer...
OK
Configuring device...
OK
Firehose config :
eMMC
[Sector:
512
] [Target:
0
] [Host:
1048576
]
Erasing
FRP
...
OK
Rebooting...
OK
UNLOCKTOOL
2024.01.27.0
Elapsed time :
44 seconds
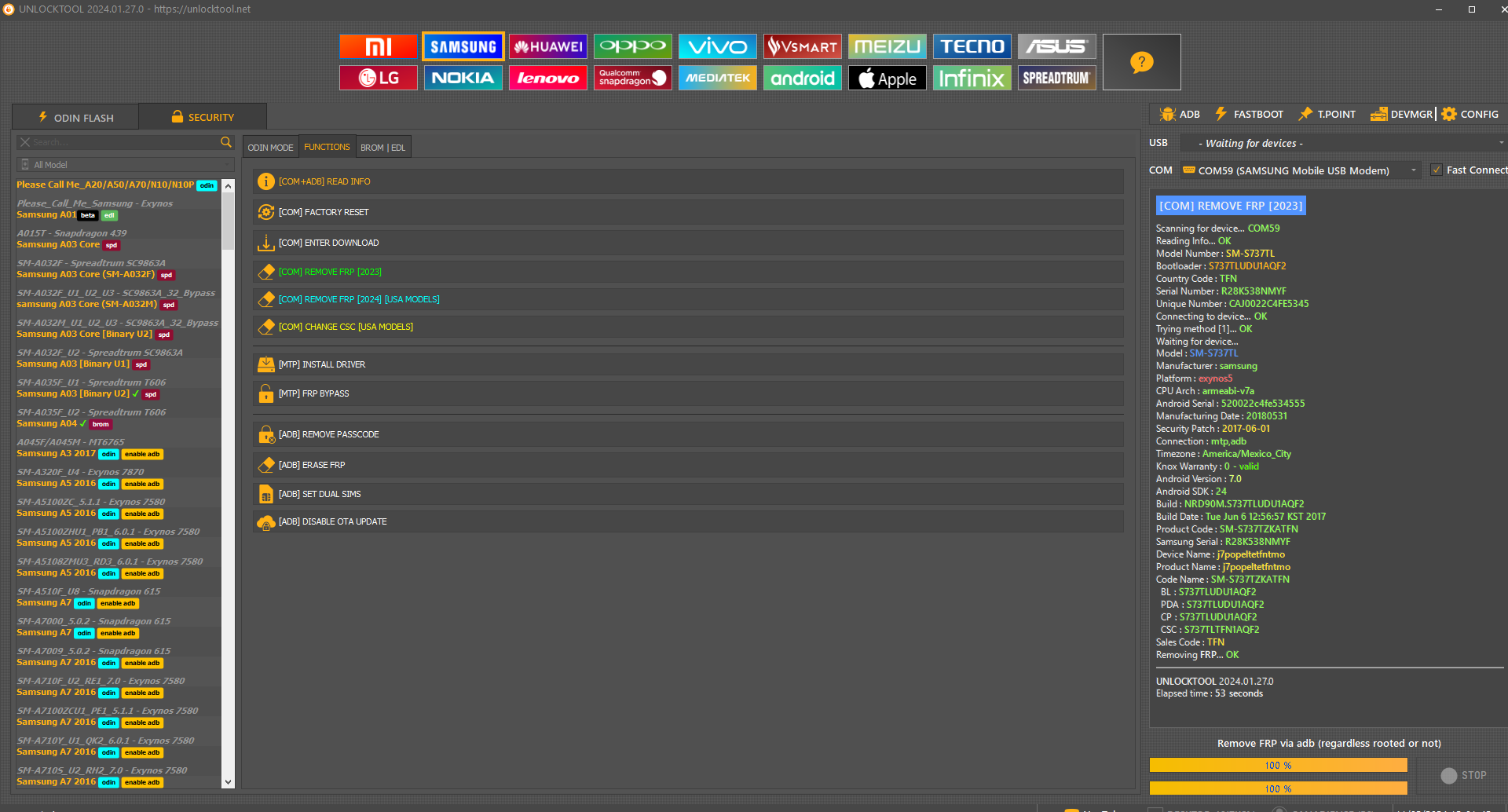
FRP Samsung SM-S737TL
[COM] REMOVE FRP [2023]
Scanning for device...
COM59
Reading Info...
OK
Model Number :
SM-S737TL
Bootloader :
S737TLUDU1AQF2
Country Code :
TFN
Serial Number :
R28K538NMYF
Unique Number :
CAJ0022C4FE5345
Connecting to device...
OK
Trying method [1]...
OK
Waiting for device...
Model :
SM-S737TL
Manufacturer :
samsung
Platform :
exynos5
CPU Arch :
armeabi-v7a
Android Serial :
520022c4fe534555
Manufacturing Date :
20180531
Security Patch :
2017-06-01
Connection :
mtp,adb
Timezone :
America/Mexico_City
Knox Warranty :
0 - valid
Android Version :
7.0
Android SDK :
24
Build :
NRD90M.S737TLUDU1AQF2
Build Date :
Tue Jun 6 12:56:57 KST 2017
Product Code :
SM-S737TZKATFN
Samsung Serial :
R28K538NMYF
Device Name :
j7popeltetfntmo
Product Name :
j7popeltetfntmo
Code Name :
SM-S737TZKATFN
BL :
S737TLUDU1AQF2
PDA :
S737TLUDU1AQF2
CP :
S737TLUDU1AQF2
CSC :
S737TLTFN1AQF2
Sales Code :
TFN
Removing
FRP
...
OK
UNLOCKTOOL
2024.01.27.0
Elapsed time :
53 seconds
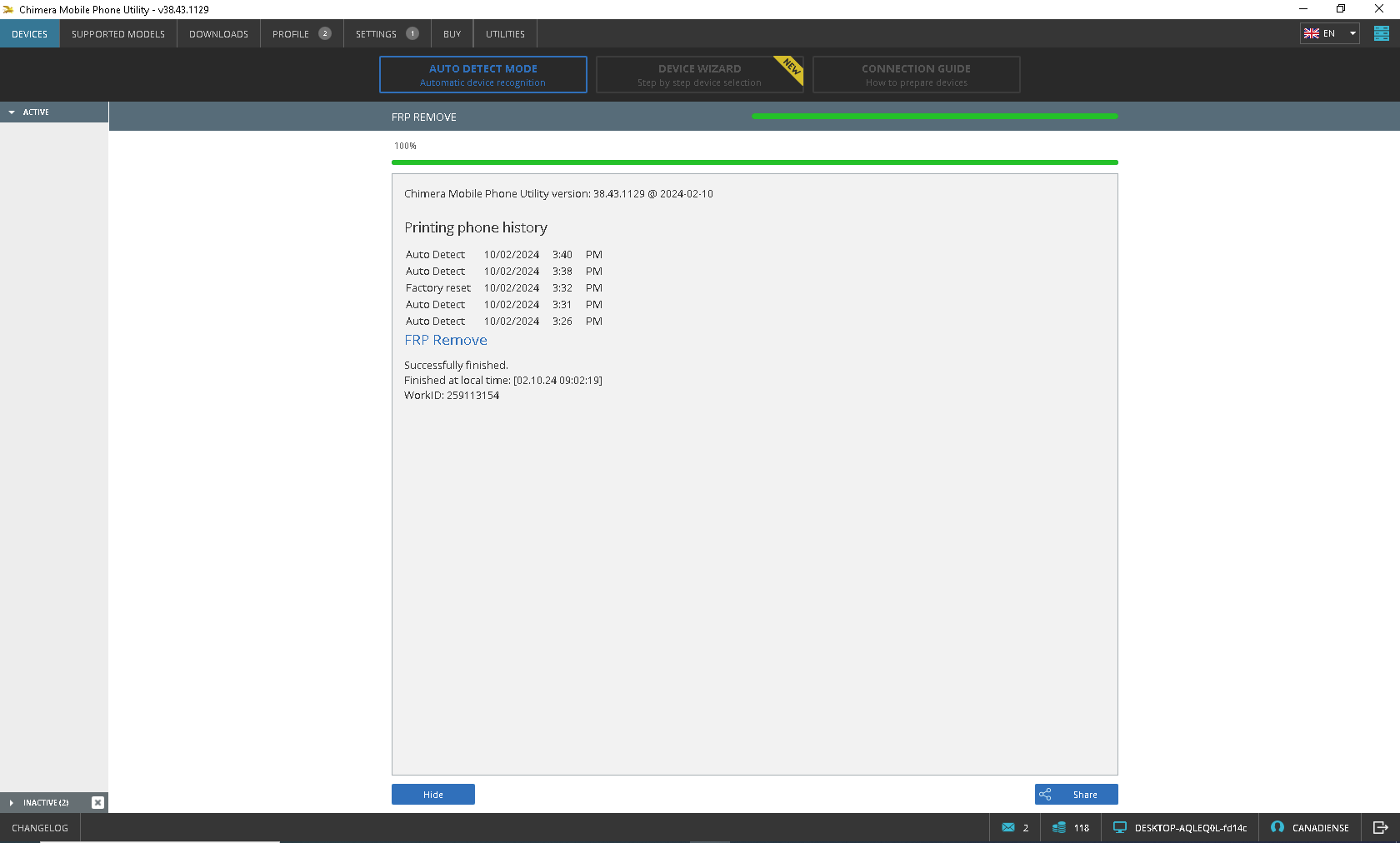
FRP Samsung SM-A146U
Test point SM-A146M

Chimera Mobile Phone Utility version: 38.43.1129 @ 2024-02-10
Printing phone history
Auto Detect
10/02/2024
3:40
PM
Auto Detect
10/02/2024
3:38
PM
Factory reset
10/02/2024
3:32
PM
Auto Detect
10/02/2024
3:31
PM
Auto Detect
10/02/2024
3:26
PM
FRP Remove
Successfully finished.
Finished at local time: [02.10.24 09:02:19]
WorkID: 259113154
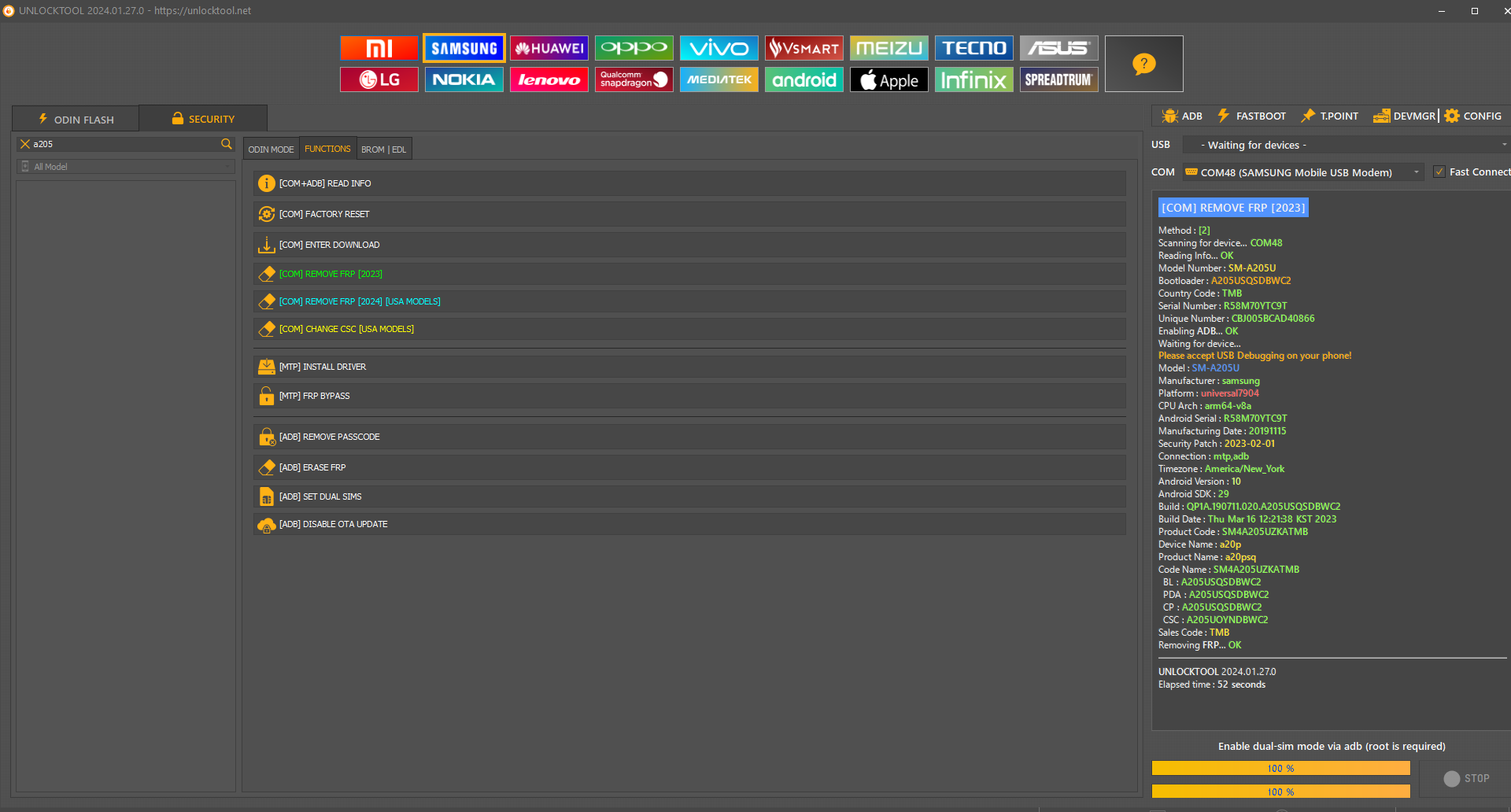
FRP Samsung A20 SM-A205U by Unlock Tool
[COM] REMOVE FRP [2023] Method : [2]
Scanning for device... COM48
Reading Info... OK
Model Number : SM-A205U
Bootloader : A205USQSDBWC2
Country Code : TMB
Serial Number : R58M70YTC9T
Unique Number : CBJ005BCAD40866
Enabling ADB... OK
Waiting for device...
Please accept USB Debugging on your phone!
Model : SM-A205U
Manufacturer : samsung
Platform : universal7904
CPU Arch : arm64-v8a
Android Serial : R58M70YTC9T
Manufacturing Date : 20191115
Security Patch : 2023-02-01
Connection : mtp,adb
Timezone : America/New_York
Android Version : 10
Android SDK : 29
Build : QP1A.190711.020.A205USQSDBWC2
Build Date : Thu Mar 16 12:21:38 KST 2023
Product Code : SM4A205UZKATMB
Device Name : a20p
Product Name : a20psq
Code Name : SM4A205UZKATMB
BL : A205USQSDBWC2
PDA : A205USQSDBWC2
CP : A205USQSDBWC2
CSC : A205UOYNDBWC2
Sales Code : TMB
Removing FRP... OK
UNLOCKTOOL 2024.01.27.0
Elapsed time : 52 seconds
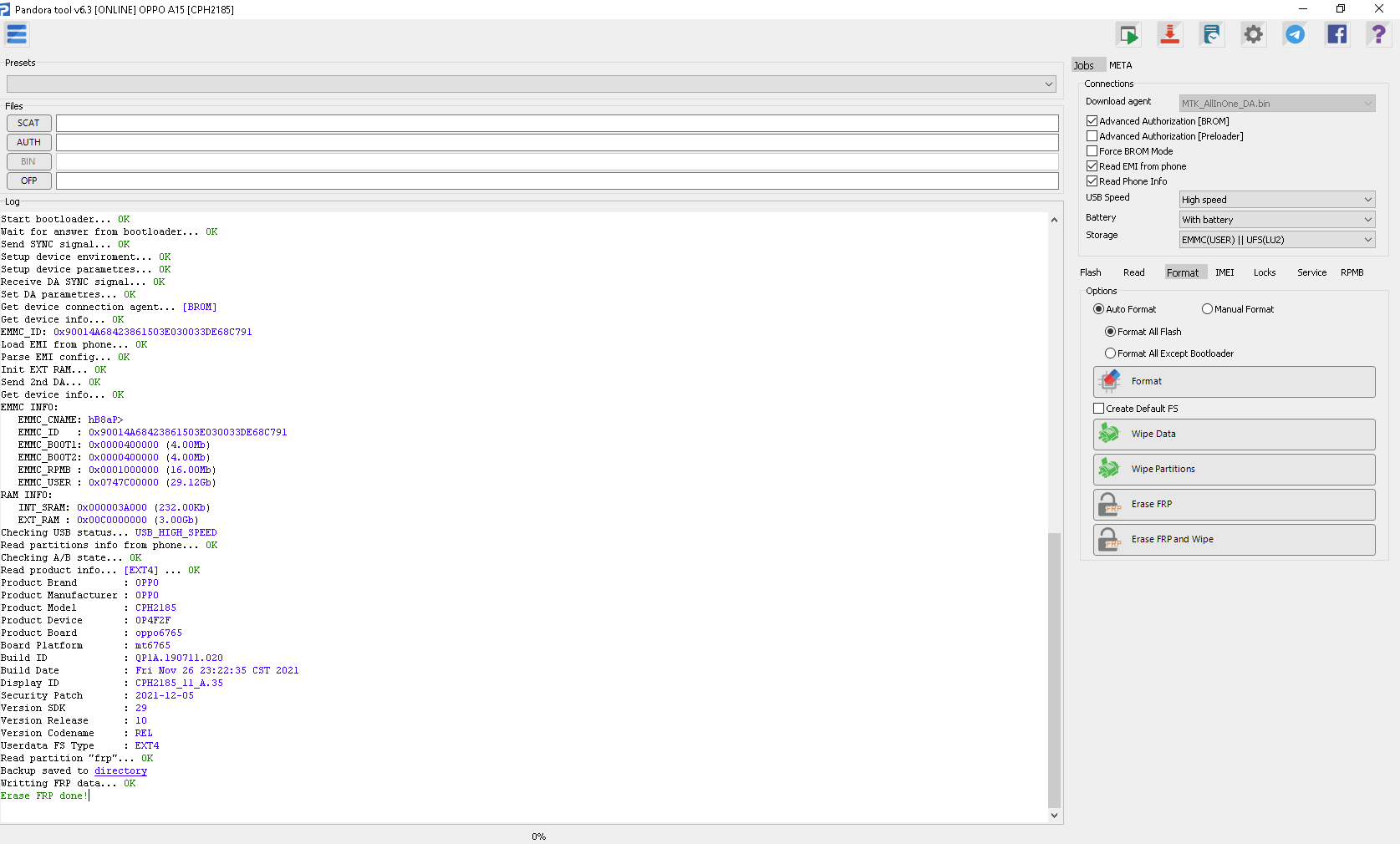
FRP OPPO A15 CPH2185
Selected model: OPPO CPH2185 (OPPO A15)
Operation: Erase FRP
Software version: 6.3
Work ID: 18084608
Connect phone in BROM Mode
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,usbser.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM188 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E5]
Active sec flags: [SBC DAA]
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
LibUSB installed
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Release testpoint, waiting 2 seconds
Advanced Bypass Security... OK
Waiting for device... OK
Driver: [MediaTek Inc.,usbser,MediaTek USB Port,usbser.sys,10.0.19041.3636]
You are using driver version 10.0.19041.3636, we recommend using version 3.0.1504.0 for proper operation. You can install the correct driver from the program directory.
Device found at COM188 [BROM]
Open port... OK
Send start cmd... OK
Get HW code from device... 0766
Get sec config... OK [000000E0]
Active sec flags: []
Get HW & SW version from device... OK
HW VER: CA00, SW VER: 0000, HW SUB CODE: 8A00
Detect chip [MT6765]
Library Version [2]
Select platform... OK
Init BROM... OK
Force Charge... OK
Disable WatchDog Timer... OK
Reopen port for libver2... OK
Get ME ID... OK
ME_ID = 0x87A55CC9, 0x07F1400C, 0xB464618D, 0xAF6325BF
Get Chip ID... [MT6765]
Get SOC ID... [5196F77473B4BA8C62204C01BC08E0FEABABCD663AE4BE520E3BCDB6AC3FFB1F]
Get sec config... OK [000000E0]
Load DownloadAgent... OK
Search DA... OK [7]
Send preloader... OK
Start preloader... OK
Checking preloader answer... OK
Send bootloader... OK
Start bootloader... OK
Wait for answer from bootloader... OK
Send SYNC signal... OK
Setup device enviroment... OK
Setup device parametres... OK
Receive DA SYNC signal... OK
Set DA parametres... OK
Get device connection agent... [BROM]
Get device info... OK
EMMC_ID: 0x90014A68423861503E030033DE68C791
Load EMI from phone... OK
Parse EMI config... OK
Init EXT RAM... OK
Send 2nd DA... OK
Get device info... OK
EMMC INFO:
EMMC_CNAME: hB8aP>
EMMC_ID : 0x90014A68423861503E030033DE68C791
EMMC_BOOT1: 0x0000400000 (4.00Mb)
EMMC_BOOT2: 0x0000400000 (4.00Mb)
EMMC_RPMB : 0x0001000000 (16.00Mb)
EMMC_USER : 0x0747C00000 (29.12Gb)
RAM INFO:
INT_SRAM: 0x000003A000 (232.00Kb)
EXT_RAM : 0x00C0000000 (3.00Gb)
Checking USB status... USB_HIGH_SPEED
Read partitions info from phone... OK
Checking A/B state... OK
Read product info... [EXT4] ... OK
Product Brand : OPPO
Product Manufacturer : OPPO
Product Model : CPH2185
Product Device : OP4F2F
Product Board : oppo6765
Board Platform : mt6765
Build ID : QP1A.190711.020
Build Date : Fri Nov 26 23:22:35 CST 2021
Display ID : CPH2185_11_A.35
Security Patch : 2021-12-05
Version SDK : 29
Version Release : 10
Version Codename : REL
Userdata FS Type : EXT4
Read partition "frp"... OK
Backup saved to C:/Program%20Files/Z3X/Pandora/Backup/MTK/OPPO_CPH2185%20(OPPO%20A15)/FRP_BACKUP_(2024-1-26_15-42-13)/
Writting FRP data... OK
Erase FRP done!
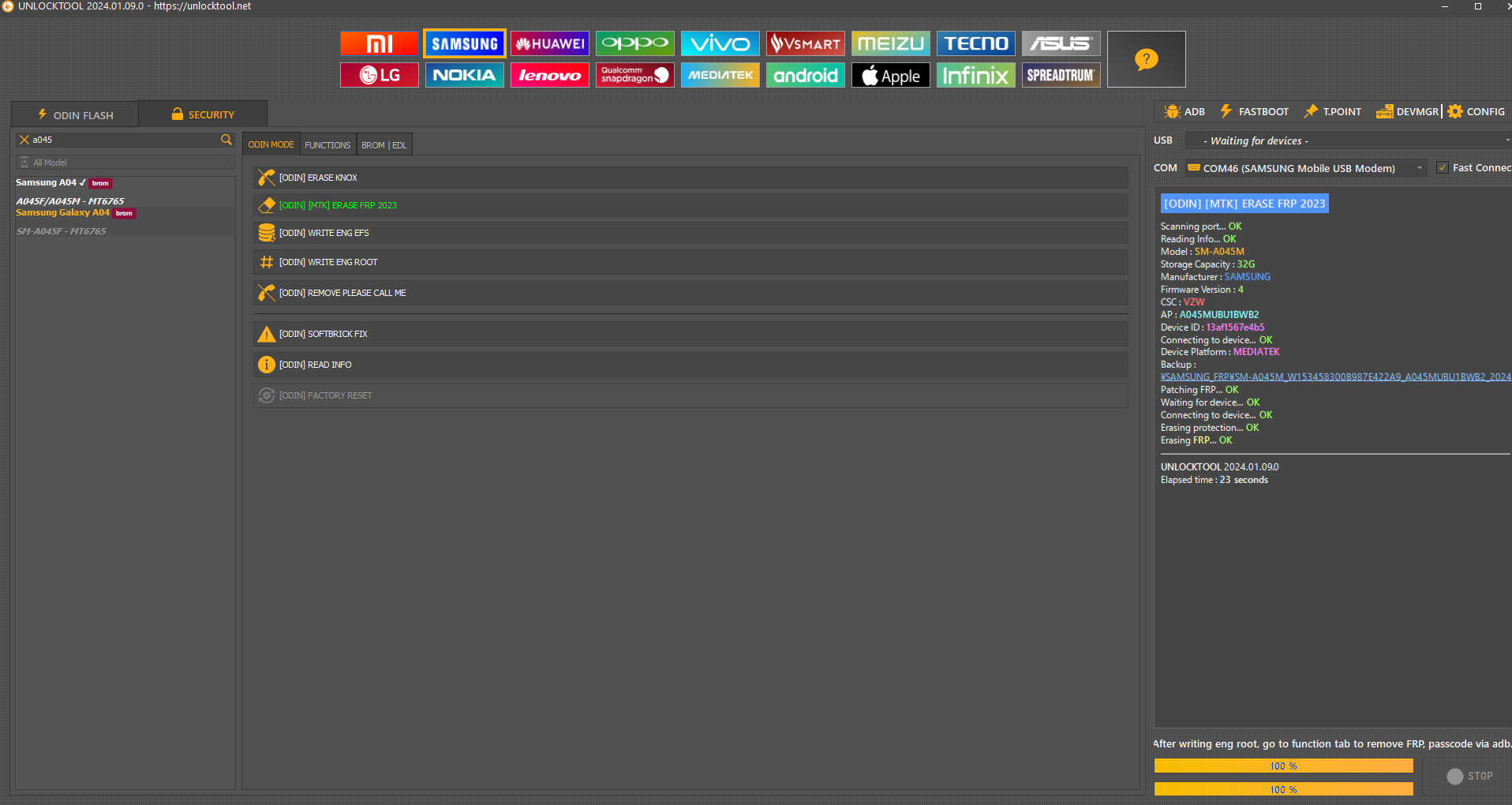
FRP Samsung SM-A045M
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:001667 SourceURL:file%3a%2f%2f
[ODIN] [MTK] ERASE FRP 2023
Scanning port...
OK
Reading Info...
OK
Model :
SM-A045M
Storage Capacity :
32G
Manufacturer :
SAMSUNG
Firmware Version :
4
CSC :
VZW
AP :
A045MUBU1BWB2
Device ID :
13af1567e4b5
Connecting to device...
OK
Device Platform :
MEDIATEK
Backup :
\SAMSUNG_FRP\SM-A045M_W153458300B987E422A9_A045MUBU1BWB2_2024-01-25_14-43-27
Patching FRP...
OK
Waiting for device...
OK
Connecting to device...
OK
Erasing protection...
OK
Erasing
FRP
...
OK
UNLOCKTOOL
2024.01.09.0
Elapsed time :
23 seconds
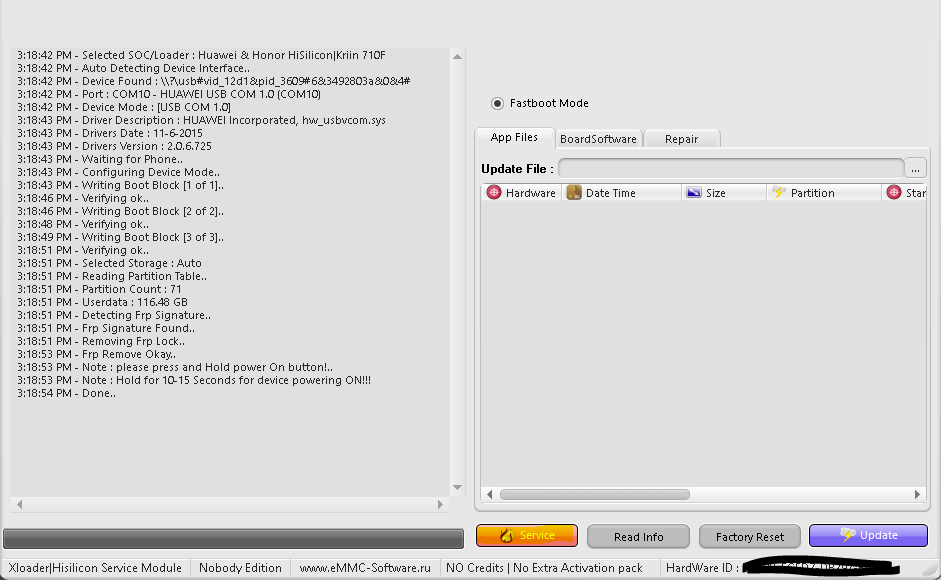
FRP Huawei Y9 Prime 2019 Done by DTPro Tool
Test Point

3:18:42 PM - Selected SOC/Loader : Huawei & Honor HiSilicon|Kriin 710F
3:18:42 PM - Auto Detecting Device Interface..
3:18:42 PM - Device Found : \\?\usb#vid_12d1&pid_3609#6&3492803a&0&4#
3:18:42 PM - Port : COM10 - HUAWEI USB COM 1.0 (COM10)
3:18:42 PM - Device Mode : [USB COM 1.0]
3:18:43 PM - Driver Description : HUAWEI Incorporated, hw_usbvcom.sys
3:18:43 PM - Drivers Date : 11-6-2015
3:18:43 PM - Drivers Version : 2.0.6.725
3:18:43 PM - Waiting for Phone..
3:18:43 PM - Configuring Device Mode..
3:18:43 PM - Writing Boot Block [1 of 1]..
3:18:46 PM - Verifying ok..
3:18:46 PM - Writing Boot Block [2 of 2]..
3:18:48 PM - Verifying ok..
3:18:49 PM - Writing Boot Block [3 of 3]..
3:18:51 PM - Verifying ok..
3:18:51 PM - Selected Storage : Auto
3:18:51 PM - Reading Partition Table..
3:18:51 PM - Partition Count : 71
3:18:51 PM - Userdata : 116.48 GB
3:18:51 PM - Detecting Frp Signature..
3:18:51 PM - Frp Signature Found..
3:18:51 PM - Removing Frp Lock..
3:18:53 PM - Frp Remove Okay..
3:18:53 PM - Note : please press and Hold power On button!..
3:18:53 PM - Note : Hold for 10-15 Seconds for device powering ON!!!
3:18:54 PM - Done..
13/01/2024 4:40:43 PM Initializing..
13/01/2024 4:40:43 PM Connected Device in Fastboot Mode Now..
13/01/2024 4:40:44 PM Model : STK-LX3
13/01/2024 4:40:44 PM Build : STK-L23B 12.0.0.225(C605E2R2P1)
13/01/2024 4:40:45 PM Bootloader : LOCKED
13/01/2024 4:40:45 PM Factory Resetting..
13/01/2024 4:40:45 PM Done!
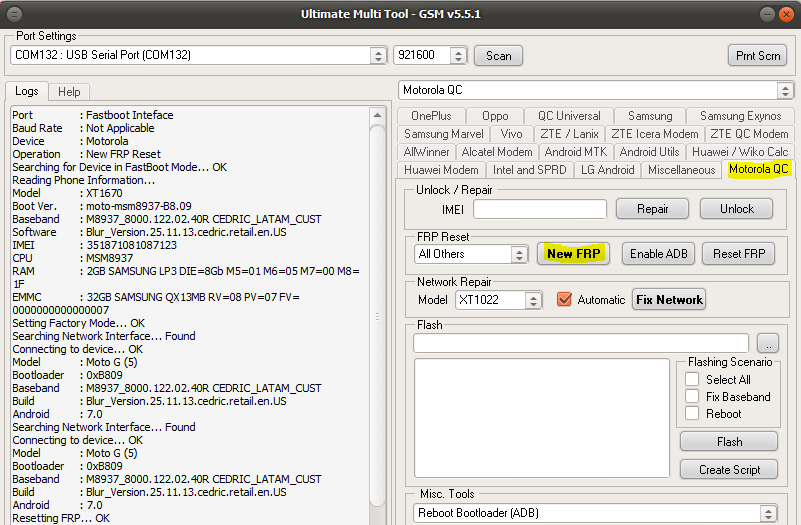
FRP Motorola XT1670 Ultimate Multi Tool UMT PRO
Volumen abajo + boton encendido para fastboot
Port : Fastboot Inteface
Baud Rate : Not Applicable
Device : Motorola
Operation : New FRP Reset
Searching for Device in FastBoot Mode... OK
Reading Phone Information...
Model : XT1670
Boot Ver. : moto-msm8937-B8.09
Baseband : M8937_8000.122.02.40R CEDRIC_LATAM_CUST
Software : Blur_Version.25.11.13.cedric.retail.en.US
IMEI : 351871081087123
CPU : MSM8937
RAM : 2GB SAMSUNG LP3 DIE=8Gb M5=01 M6=05 M7=00 M8=1F
EMMC : 32GB SAMSUNG QX13MB RV=08 PV=07 FV=0000000000000007
Setting Factory Mode... OK
Searching Network Interface... Found
Connecting to device... OK
Model : Moto G (5)
Bootloader : 0xB809
Baseband : M8937_8000.122.02.40R CEDRIC_LATAM_CUST
Build : Blur_Version.25.11.13.cedric.retail.en.US
Android : 7.0
Searching Network Interface... Found
Connecting to device... OK
Model : Moto G (5)
Bootloader : 0xB809
Baseband : M8937_8000.122.02.40R CEDRIC_LATAM_CUST
Build : Blur_Version.25.11.13.cedric.retail.en.US
Android : 7.0
Resetting FRP... OK
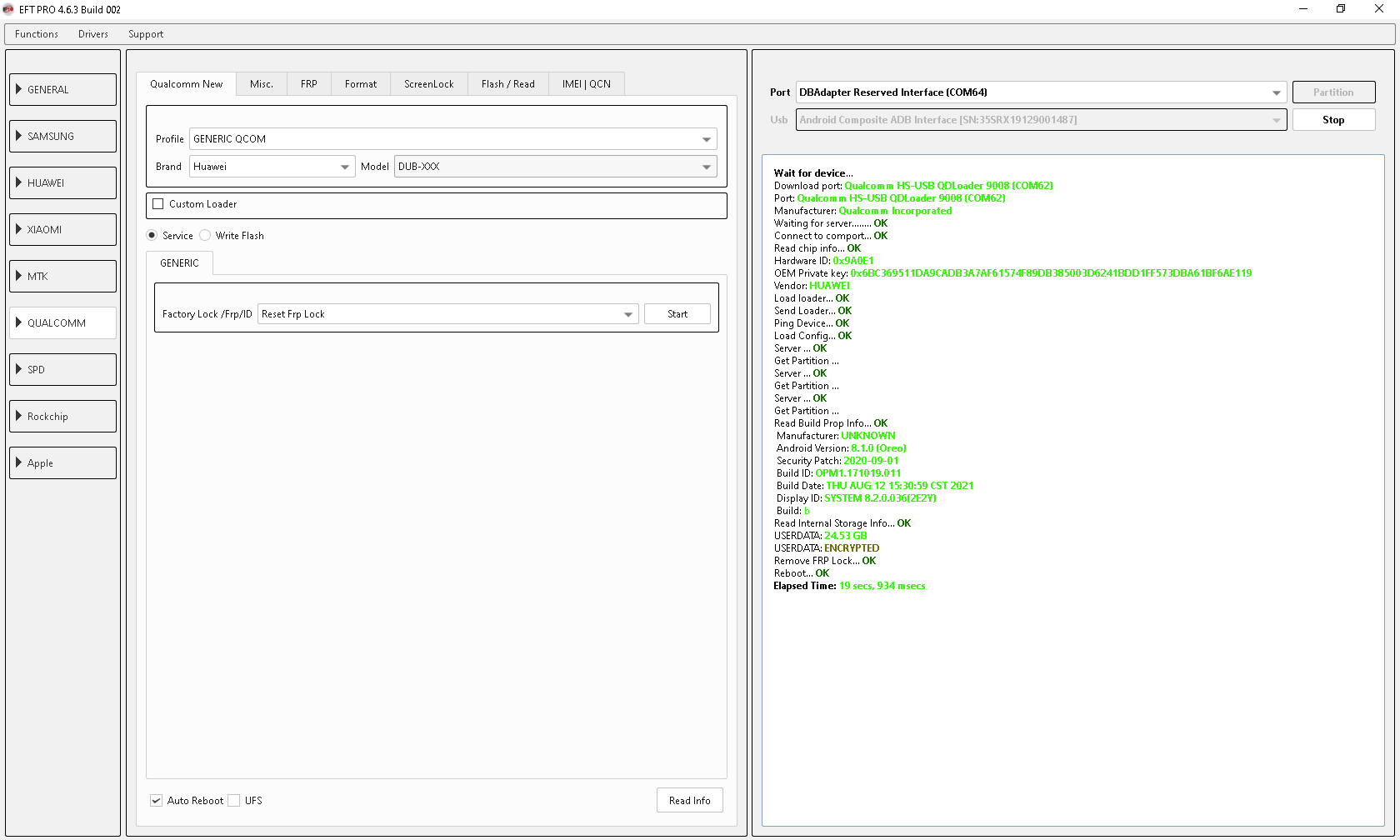
FRP Huawei Y7 2019 Done by EFT Pro
Huawei test point Y7 2019 FRP Done
Wait for device...
Download port: Qualcomm HS-USB QDLoader 9008 (COM62)
Port: Qualcomm HS-USB QDLoader 9008 (COM62)
Manufacturer: Qualcomm Incorporated
Waiting for server........ OK
Connect to comport... OK
Read chip info... OK
Hardware ID: 0x9A0E1
OEM Private key: 0x6BC369511DA9CADB3A7AF61574F89DB385003D6241BDD1FF573DBA61BF6AE119
Vendor: HUAWEI
Load loader... OK
Send Loader... OK
Ping Device... OK
Load Config... OK
Server ... OK
Get Partition ...
Server ... OK
Get Partition ...
Server ... OK
Get Partition ...
Read Build Prop Info... OK
Manufacturer: UNKNOWN
Android Version: 8.1.0 (Oreo)
Security Patch: 2020-09-01
Build ID: OPM1.171019.011
Build Date: THU AUG 12 15:30:59 CST 2021
Display ID: SYSTEM 8.2.0.036(2E2Y)
Build: b
Read Internal Storage Info... OK
USERDATA: 24.53 GB
USERDATA: ENCRYPTED
Remove FRP Lock... OK
Reboot... OK
Elapsed Time: 19 secs, 934 msecs
FRP and full Format Sky Unisoc SPRD
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM4]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&4
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Sync with node for I2C communication...
Handshake with BootROM... Done
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM7]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\skyn552202015113
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Connecting to MODEM...
● Reading Device Information...
Platform Version: MOCORTM_20A_W21.15.3_Debug
Project Version: sharklp
BASE Version: 4G_MODEM_20A_W21.15.3
HW Version: sc9832e_modem
04-14-2021 17: 43
BuildDesc: Elite_N55-user 11 R01005 1662364826 release-keys
Resetting to factory default settings... Done
●●● Log file saved to => C:/Users/Celulares Montreal/Downloads/AndroidUtilityPRO.v122.00.2022/Logs/2023_11_30_12_30_26.log
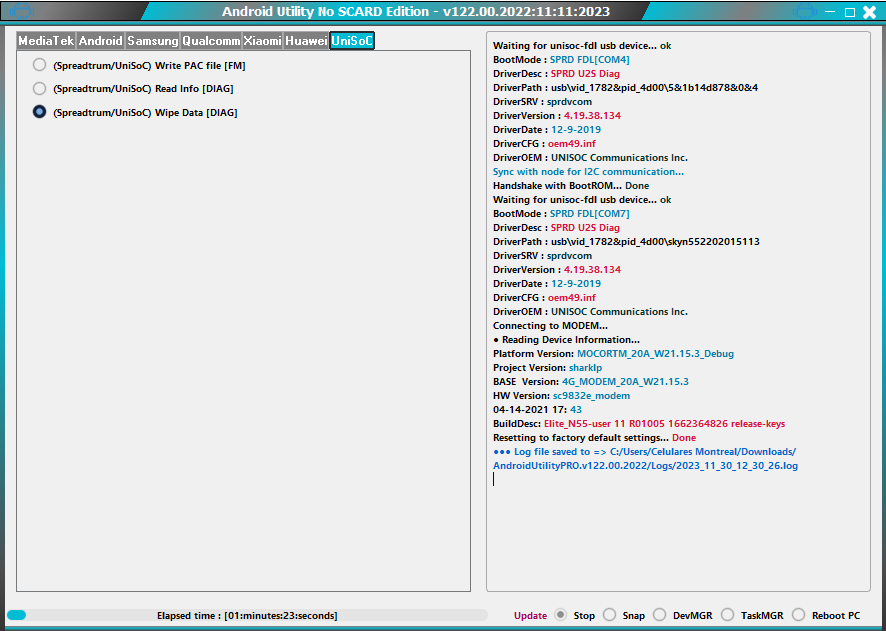
FRP Tablet PRITOM M10 sp7731e s8631e cuenta google
FRP Tablet PRITOM M10 sp7731e s8631e
Google Account Tablet PRITOM M10 sp7731e s8631e
Cuenta Google Tablet PRITOM M10 sp7731e s8631e
Volumen abajo + cable USB
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM68]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&3
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Sync with node for I2C communication...
Handshake with BootROM... Done
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM68]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&3
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Connecting to MODEM...
● Reading Device Information...
BuildDesc: sp7731e_1h30__s8631e_2g-user 9 PPR1.180610.011 13117 release-keys~
Rebooting device... Done
●●● Log file saved to => C:/Users/Downloads/AndroidUtilityPRO.v122.00.2022/Logs/2023_11_24_13_36_35.log
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM68]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&3
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Sync with node for I2C communication...
Handshake with BootROM... Done
Waiting for unisoc-fdl usb device... ok
BootMode : SPRD FDL[COM68]
DriverDesc : SPRD U2S Diag
DriverPath : usb\vid_1782&pid_4d00\5&1b14d878&0&3
DriverSRV : sprdvcom
DriverVersion : 4.19.38.134
DriverDate : 12-9-2019
DriverCFG : oem49.inf
DriverOEM : UNISOC Communications Inc.
Connecting to MODEM...
● Reading Device Information...
BuildDesc: sp7731e_1h30__s8631e_2g-user 9 PPR1.180610.011 13117 release-keys~
Resetting to factory default settings... Done
●●● Log file saved to => C:/Users/Downloads/AndroidUtilityPRO.v122.00.2022/Logs/2023_11_24_13_39_18.log
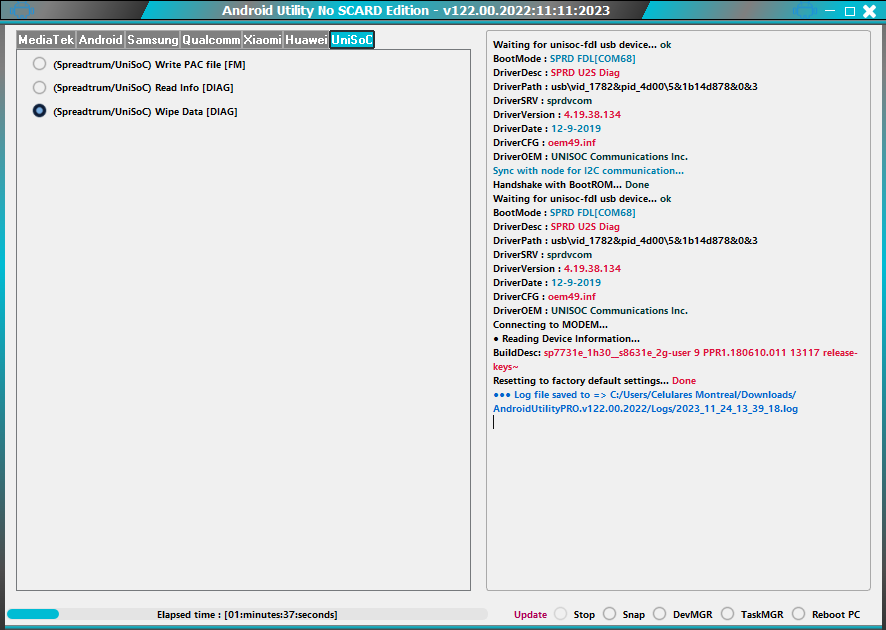
FRP Samsung SM-J106H
- Shark Tool (V0.0.0.5)
- Operation : [Remove FRP]
- Detecting Samsung modem port : SAMSUNG Mobile USB Modem
- Selected ComPort : COM52
- Connecting : OK
- Reading info : OK
- Model: SM-J106H
- Baseband: J106HDDS0ARH1
- Software: J106HDDS0ARH1
- Sales Code: SM-
- SN: RV1K106YCHX
- IMEI: 35481009193775
- UN: CFN00278AF20AB4
- Software REV: BIT[0]
- Software Build Date: 2018-08-01
- Checking device lock : TRIGGERED
- Checking server data : OK
- This operation takes 5 credits. Continue? Confirmed
- Connecting to shark server : OK
- Work id : [886315]
- Requesting device data : OK
- Generating lock hash : OK
- Calculating phone data : OK
- Removing lock state : OK
- Verifying lock state : verified
- Rebooting : OK
- FRP-Account removed successfully
- Operation finished (00:12) 2023-10-27 04:13:02 PM
FRP Motorola Moto G20 XT2128-1
FORMAT DATA
Selected Platform :
Tiger T700_64_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM68 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\5&1B14D878&0&3
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
[72]
Reading
device info
...
OK
[super]
Model Name :
moto g(20)
Product Name :
java_retail
Manufacturer :
motorola
Android Version :
11
Security Patch :
2023-03-01
Build ID :
RTAS31.68-66-3
Build Date :
Tue Feb 21 13:40:32 CST 2023
Erasing
FRP (persist)
...
OK
Erasing
USERDATA
...
OK
UNLOCKTOOL
2023.09.23.0
Elapsed time :
28 seconds
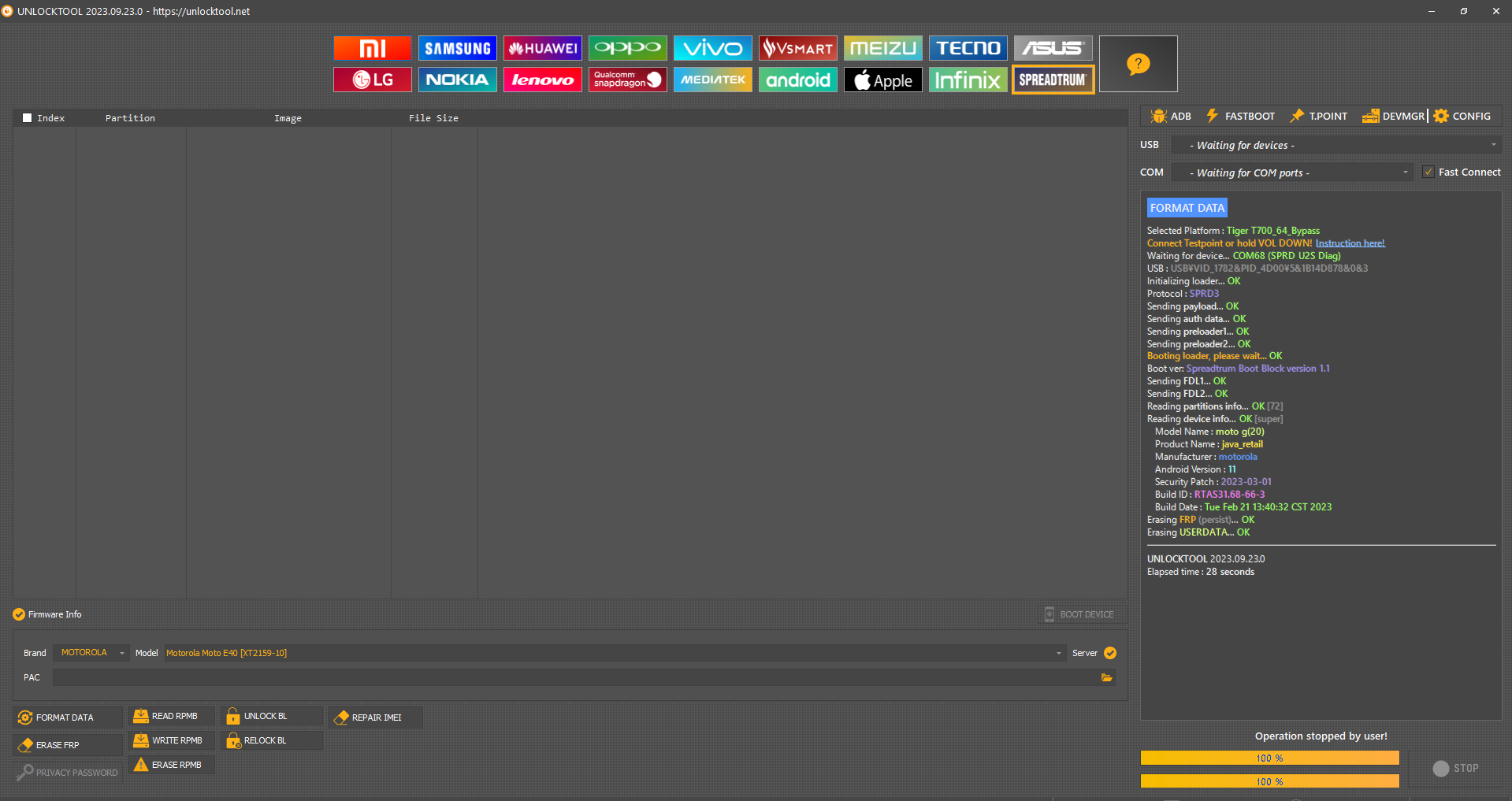
FRP Samsung SM-J337T
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:002473 SourceURL:file%3a%2f%2f
[COM] REMOVE FRP [2023]
Scanning for device...
COM59
Reading Info...
FAIL
Trying method [1]...
OK
Waiting for device...
Please accept USB Debugging on your phone!
Model :
SM-J337T
Manufacturer :
samsung
Platform :
exynos5
CPU Arch :
armeabi-v7a
Android Serial :
4200e7bb060da5ad
Manufacturing Date :
20181109
Security Patch :
2021-01-01
Connection :
mtp,adb
Timezone :
America/Mexico_City
Knox Warranty :
0 - valid
Android Version :
8.0.0
Android SDK :
26
Build :
R16NW.J337TUVSAAUB2
Build Date :
Wed Feb 10 17:05:00 KST 2021
Product Code :
SM2J337TZDATMB
Samsung Serial :
R28KB0XSW8N
Device Name :
j3topltetmo
Product Name :
j3topltetmo
Code Name :
SM2J337TZDATMB
BL :
J337TUVSAAUB2
PDA :
J337TUVSAAUB2
CP :
J337TUVSAAUB2
CSC :
J337TTMBAAUB2
Sales Code :
TMB
Removing
FRP
...
OK
UNLOCKTOOL
2023.09.23.0
Elapsed time :
37 seconds
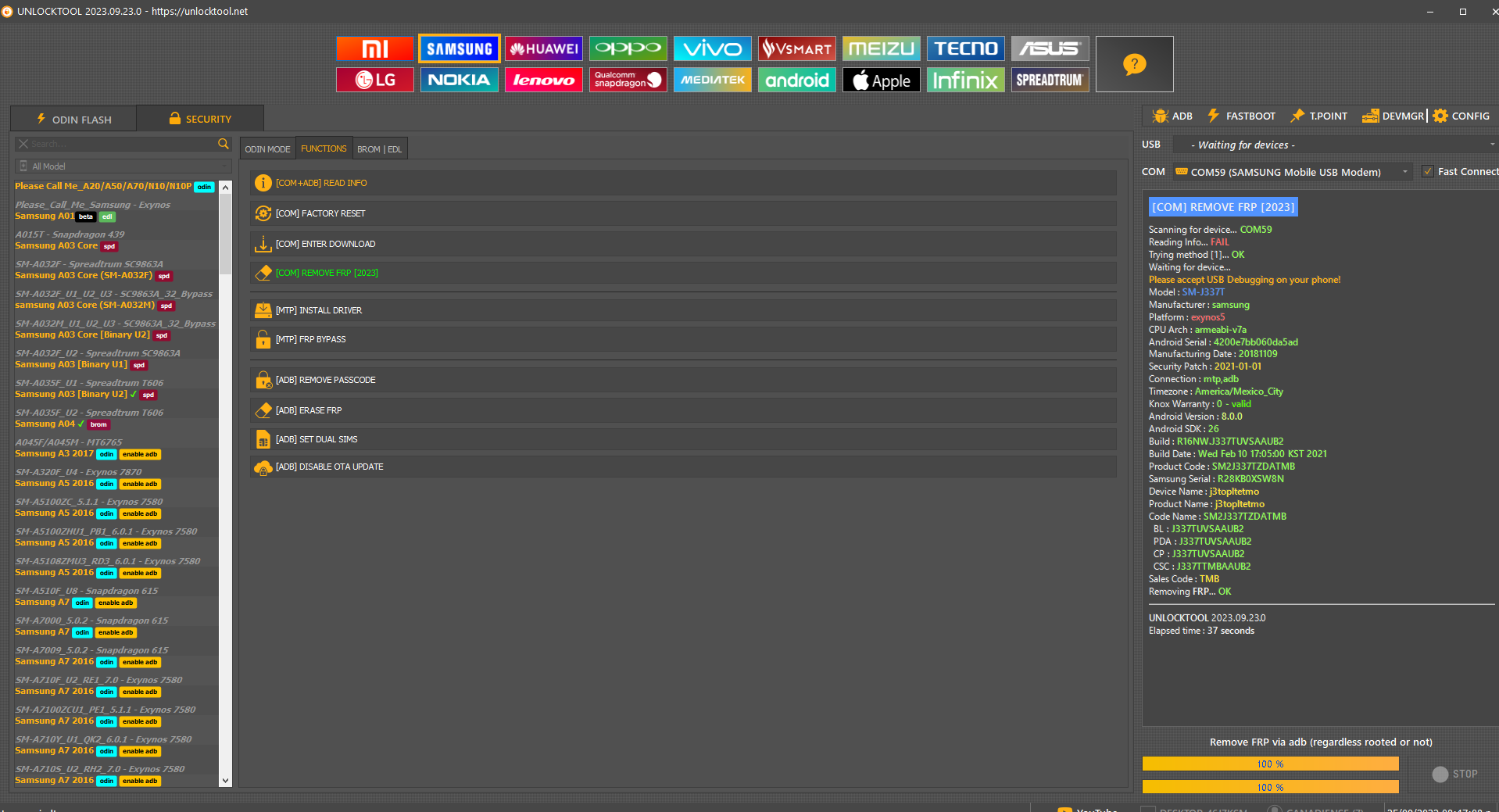
FRP Samsung Tablet SM-T580
- Shark Tool (V0.0.0.5)
- Operation : [Remove FRP]
- Detecting Samsung modem port : SAMSUNG Mobile USB Modem
- Selected ComPort : COM21
- Connecting : OK
- Reading info : OK
- Model: SM-T580
- Baseband: T580UEU4CSC1
- Software: T580UEU4CSC1
- Sales Code: XAR
- SN: R52KA02PXXP
- IMEI: NONE
- UN: CAJ033D4CEA67B4
- Software REV: BIT[4]
- Software Build Date: 2019-03-01
- Checking device lock : TRIGGERED
- Checking server data : OK
- This operation takes 5 credits. Continue? Confirmed
- Connecting to shark server : OK
- Work id : [594502]
- Requesting device data : OK
- Generating lock hash : OK
- Calculating phone data : OK
- Removing lock state : OK
- Verifying lock state : verified
- Rebooting : OK
- FRP-Account removed successfully
- Operation finished (00:07) 2023-09-22 01:04:54 PM
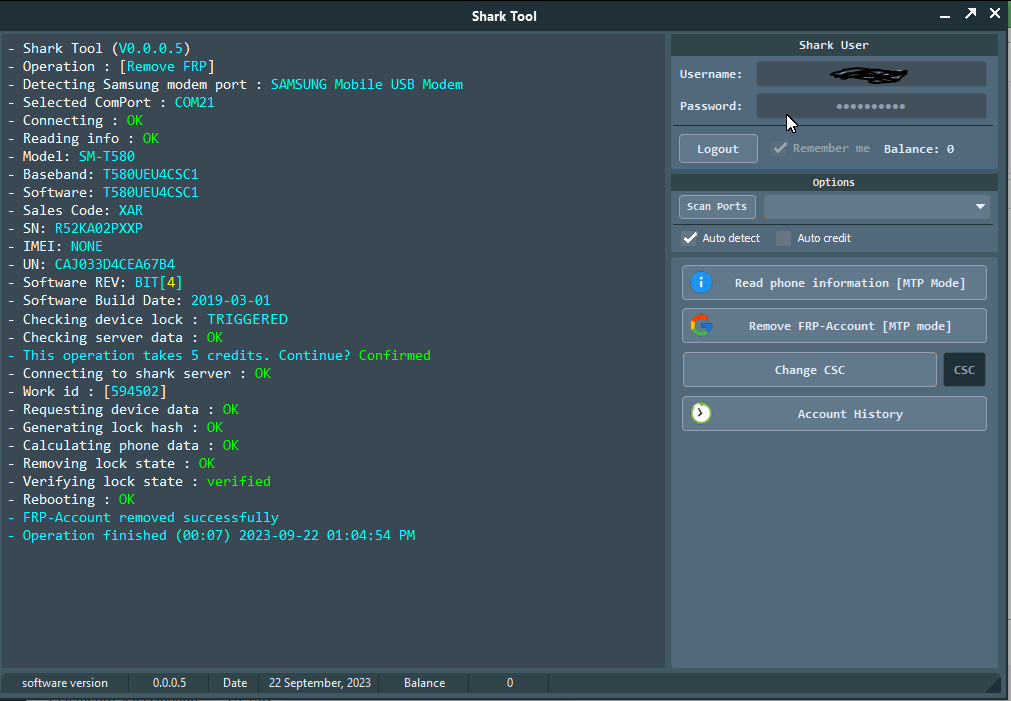
FRP Samsung SM-A205U
Chimera Mobile Phone Utility version: 36.89.1322 @ 2023-09-13
Reset FRP lock started
Resetting FRP...
Model: SM-A205U
SW Version: A205USQSDBWC2/A205UOYNDBWC2/A205USQSDBWC2/A205USQSDBWC2
Serial: R58N141HRNJ
IMEI: 352741119001934
Product Code: TMK
Unique Number: CBJ00E6159479C6
Operation in progress. Be patient! Do NOT disconnect the phone!
Please 'Allow USB debugging' in the popup window
Waiting for ADB device...
Resetting FRP...
To complete resetting FRP, go to 'Settings/General management/Reset' then select 'Factory data reset'
Restarting phone
Successfully finished.
Finished at local time: [09.13.23 16:04:31]
WorkID: 234512950
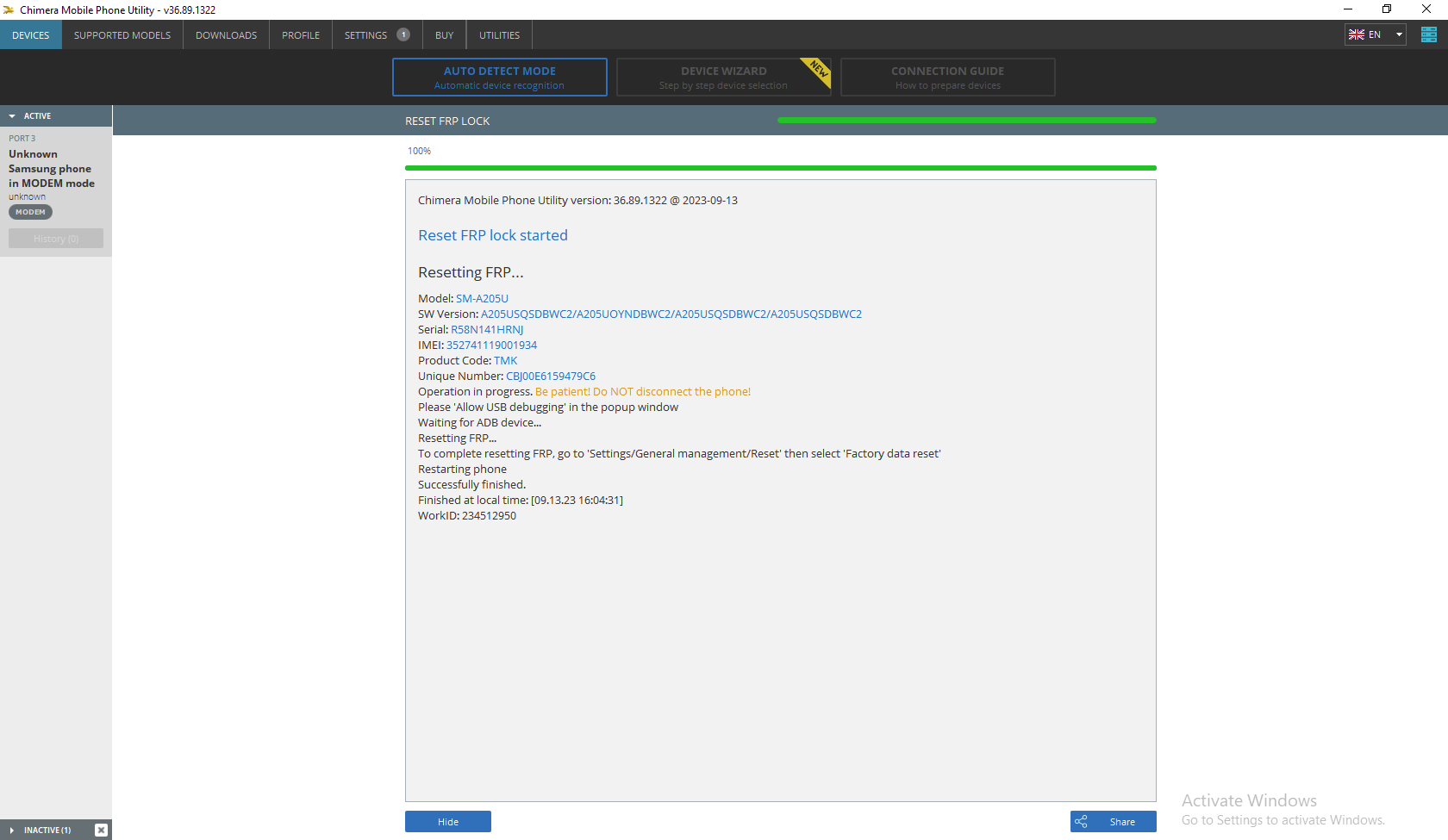
FRP Samsung Tablet T580 by Z3X Box
Escribir firmware Combination para habilitar ADB
You must activate ADB before reset FRP Yes
Goto 'Terms and conditions' press 'NEXT' and 'AGREE' EULA Yes
Waiting ADB device... OK
Reading phone info...
Model: SM-T580
Android version: 6.0.1
PDA version: FA60_T580XXU4ARJ1
CSC version:
Phone version:
Product code:
CSC country code:
CSC sales code:
Phone SN: R52KA02PXXP
IMEI:
HW version:
RF cal date:
Chip name: EXYNOS7870
Modem board:
Security patch: 2016-05-01
Boot Warranty bit: 0
Bypass FRP... OK
For complete reset FRP, goto 'Backup and reset' and make 'Factory data reset'
Done with Samsung Tool PRO v.45.14 [SM-T580,Reset FRP]
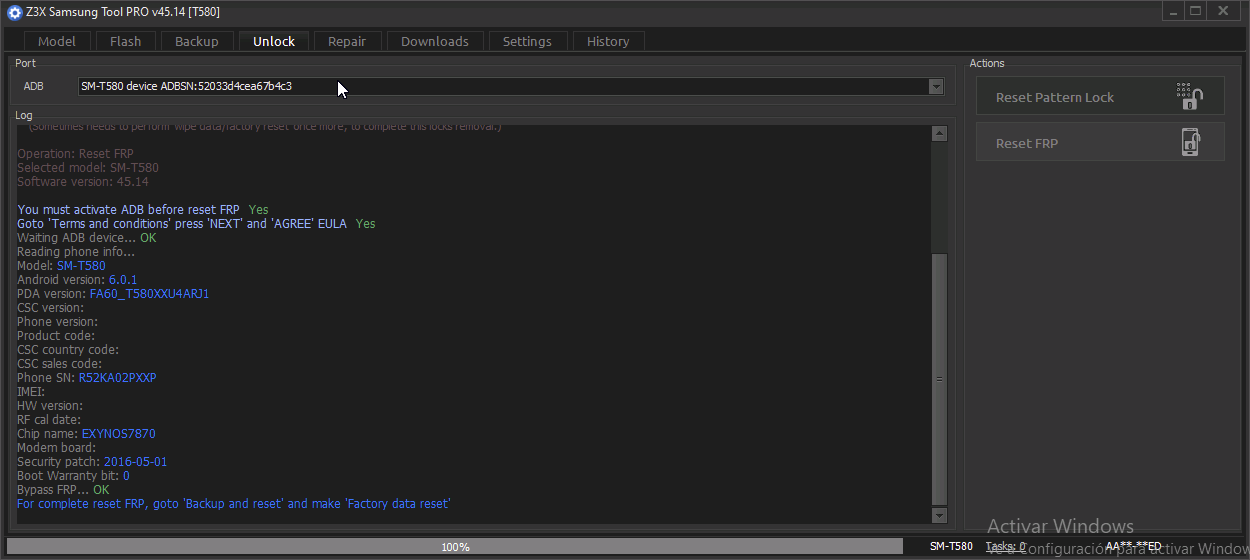
FRP Motorola E40 XT2159-3 SPD Tiger T700 64 by Unlocktool
FRP Motorola E40 SPD
Apagado Presionar volumen -
Conectar cable USB
ERASE FRP
Selected Platform :
Tiger T700_64_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM23 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
Reading
device info
...
OK
[super]
Model Name :
cyprus64
Manufacturer :
motorola
Android Version :
11
Security Patch :
2023-07-05
Build ID :
ROQS31.166-87-9 release-keys
Build Date :
Thu Jul 13 23:07:42 CST 2023
Erasing
FRP
...
OK
UNLOCKTOOL
2023.09.03.2
Elapsed time :
33 seconds
FRP Motorola G Pure XT2163-4 by Magic Tool
FRP Motorola G Pure XT2163-4
Start FRP Unlock Task on 8/19/2023 12:34:51 PM -06:00
Waiting for device arrival.... OK
Model SKU: XT2163-4
Carrier: RETUS
Serial: ZY22H8Q5T7
Authorizing FRP Access...OK
Reboot bootloader...OK
Waiting for device arrival.... OK
Erasing FRP...OK
Erasing UserData...OK
Erasing Cache...OK
Final Step...OK
Rebooting...OK
FRP Unlock Task Successful!
FRP Hisense E50 Lite by Chimera Tool
FRP Cuenta Google Hisense E50 Lite
Abrir Chimera Tool presionar volumen + - Apagado y conectar cable USB
Seleccionar -> CPU Spectrum UNISOC -> SC9863A 64Bit
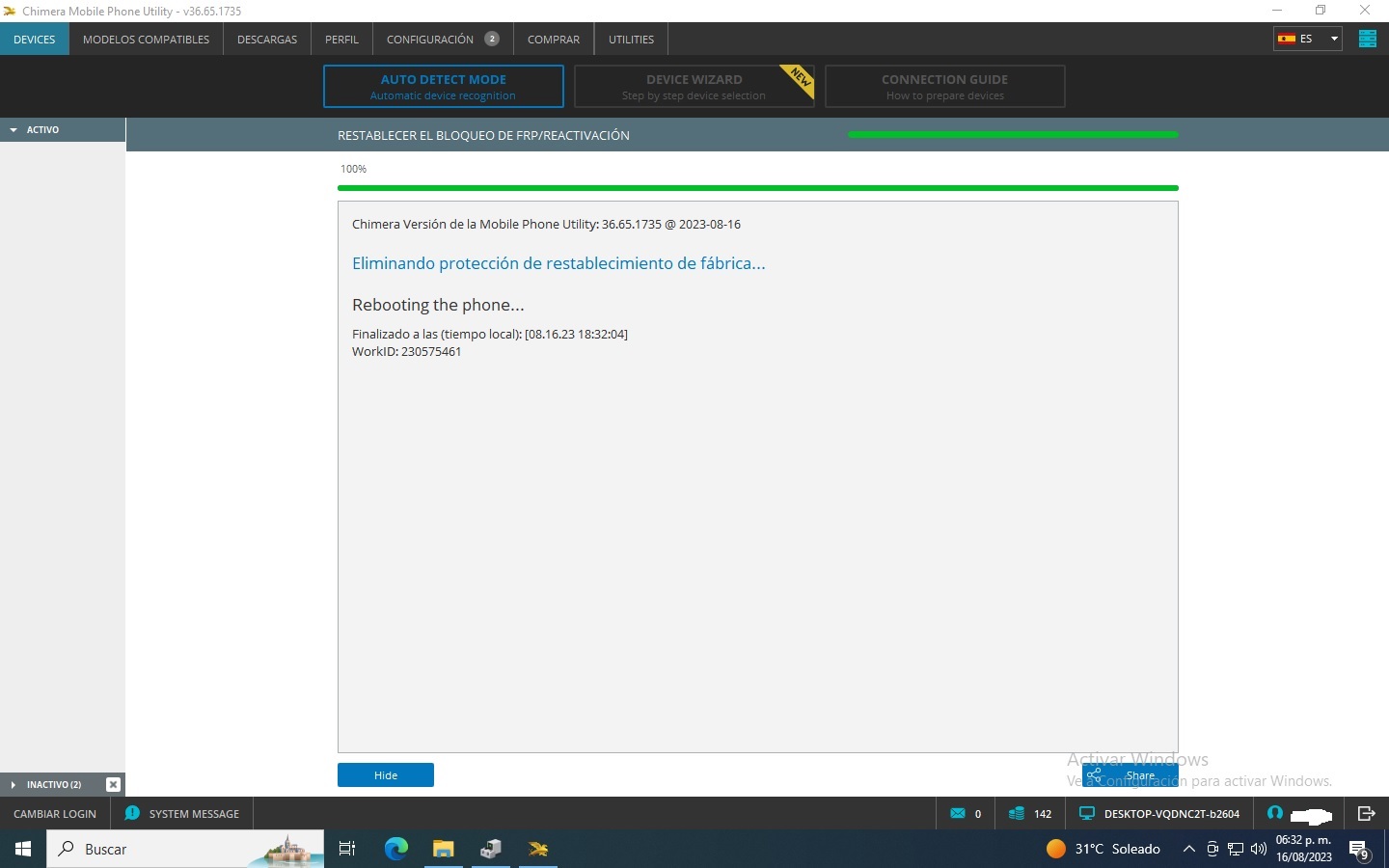
FRP ZTE V40 Smart
Select - > Tiger T606_64_Bypass
ERASE FRP Selected Platform : Tiger T606_64_Bypass
Connect Testpoint or hold VOL DOWN! Instruction here!
Waiting for device... COM7 (SPRD U2S Diag)
USB : USB\VID_1782&PID_4D00\5&390FD7C2&0&4
Initializing loader... OK
Protocol : SPRD3
Sending payload... OK
Sending auth data... OK
Sending preloader1... OK
Sending preloader2... OK
Booting loader, please wait... OK
Boot ver: Spreadtrum Boot Block version 1.1
Sending FDL1... OK
Sending FDL2... OK
Reading partitions info... OK
Reading device info... OK [super]
Model Name : ZTE A7040
Product Name : P606F01
Manufacturer : ZTE
Platform : ums9230_4h10
Android Version : 11
Security Patch : 2023-06-05
Build ID : MyOS11.0.8_A7040_TEL
Build Date : Fri Jun 16 19:38:47 CST 2023
Erasing FRP... OK
UNLOCKTOOL 2023.07.30.0
Elapsed time : 52 seconds
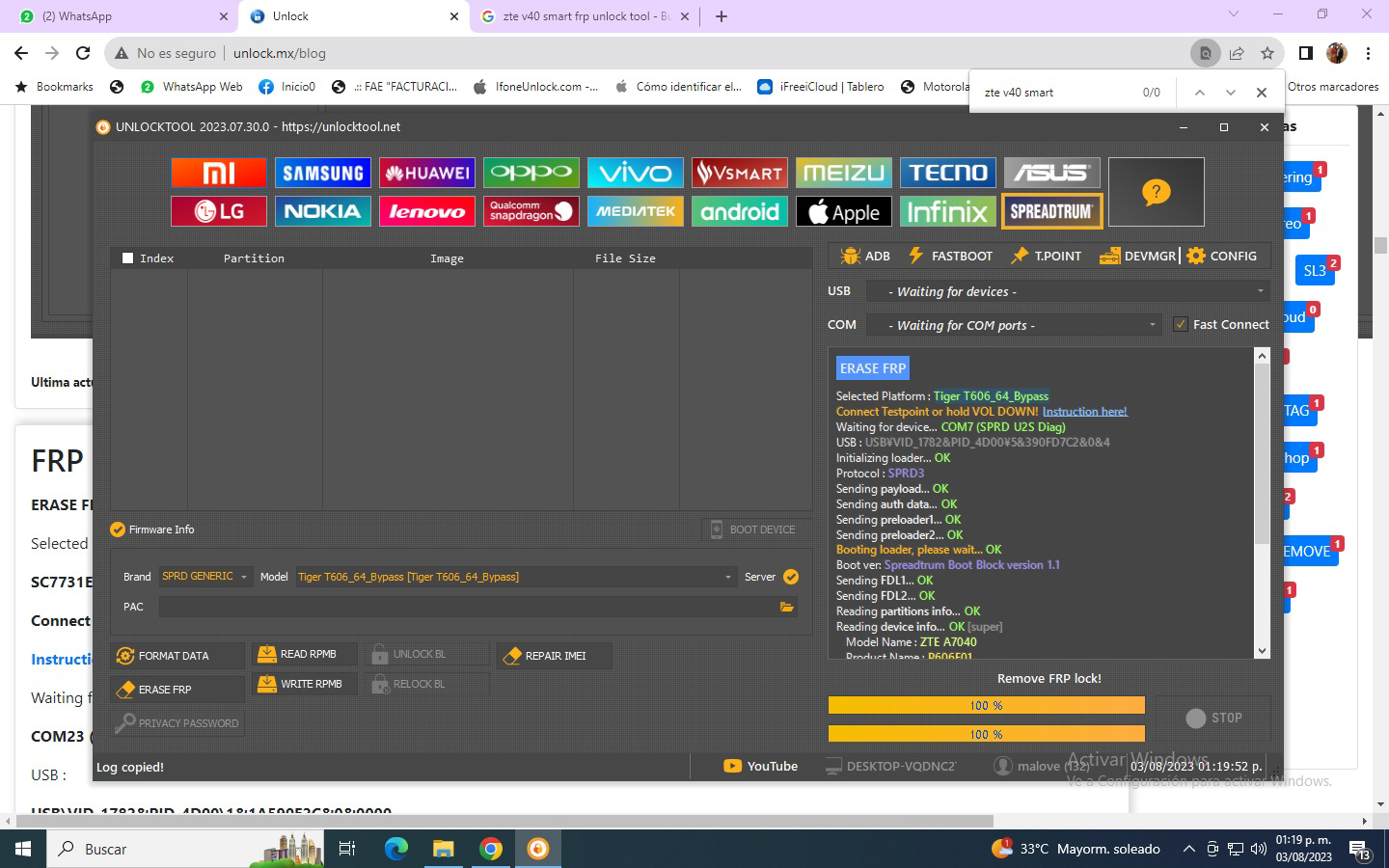
FRP Realme C21-Y RMX3263 by Unlocktool
FRP Realme C21-Y RMX3263 by Unlocktool
ERASE FRP Selected Platform : Tiger T610_64_Bypass
Connect Testpoint or hold VOL DOWN! Instruction here!
Waiting for device... COM23 (SPRD U2S Diag)
USB : USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader... OK
Unlock.mx....Done
Protocol : SPRD3
Sending payload... OK
Sending auth data... OK
Sending preloader1... OK
Sending preloader2... OK
Booting loader, please wait... OK
Boot ver: Spreadtrum Boot Block version 1.1
Sending FDL1... OK
Sending FDL2... OK
Reading partitions info... OK
Reading device info... OK [super]
Model Name : RMX3261
Manufacturer : realme
Android Version : 11
Security Patch : 2022-03-05
Build ID : RMX3261_11_A.81
Build Date : Sun Apr 3 11:44:02 CST 2022
OTA Version : RMX3261_11_A.81_20220403103755
Erasing FRP... OK
UNLOCKTOOL 2023.07.22.0
Elapsed time : 28 seconds
Version:0.9 StartHTML:-1 EndHTML:-1 StartFragment:000128 EndFragment:002518 SourceURL:file%3a%2f%2f
FORMAT DATA
Selected Platform :
Tiger T610_64_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM23 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader...
OK
Unlock.mx....OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
Reading
device info
...
OK
[super]
Model Name :
RMX3261
Manufacturer :
realme
Android Version :
11
Security Patch :
2022-03-05
Build ID :
RMX3261_11_A.81
Build Date :
Sun Apr 3 11:44:02 CST 2022
OTA Version :
RMX3261_11_A.81_20220403103755
Erasing
FRP
...
OK
Erasing
USERDATA
...
OK
UNLOCKTOOL
2023.07.22.0
Elapsed time :
27 seconds
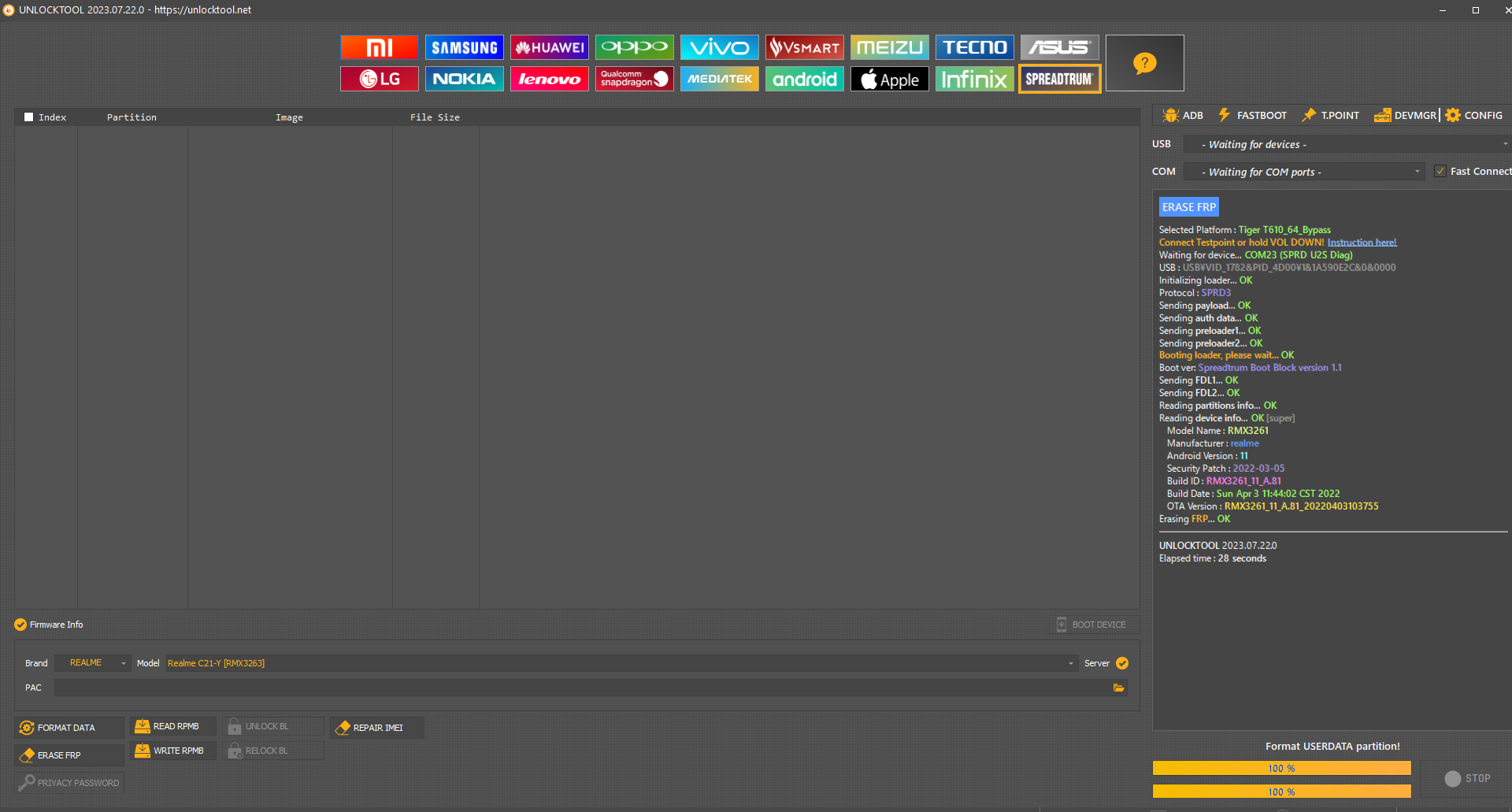
FRP Motorola Moto G GO G Pure XT2163-7
Starting Factory Enabler process...
Unlock.mx.....Done
Waiting for device in Fastboot Mode....Done.
Reading Data....Done
Firmware: RRHGS31.Q3-37-43-43-5-4-6
Android: 11
CPU: MT6762G
Model: XT2163-6
SN: ZY22G4HZ8B
IMEI: 357151881507388
Channel ID: 0x88
Carrier: attpre
Factory Mode: disabled
Reading Data ... Done
Creating Order ID....Done
Operation ID: 1630251
Sending Data to Server ... Done
Setting Factory Mode ... Done
Rebooting Phone ... Done
Elapsed Time: 6:47.07
Unlock.mx.....Done
FSG: MT6762_TC2.PR2.SP.V8.2.P89.01.66.119R
Firmware: RRHGS31.Q3-37-43-43-5-4-6
Model: G GO
SKU: XT2163-7
SN: ZY22G4HZ8B
IMEI 1: 357151881507388
Carrier: attpre
Checking Price for Device....Done
Wiping IMEI ... Done
Writing IMEI ... Done
New IMEI 1: 357151881507388
Writing New Security ... Done.
Elapsed Time: 0:38.79
FRP Samsung A32 SM-A325M by UnlockTool
[COM] REMOVE FRP [2023]
Scanning for device...
COM32
Reading Info...
FAIL
Trying method [1]...
OK
Waiting for device...
Please accept USB Debugging on your phone!
Model :
SM-A325M
Manufacturer :
samsung
Platform :
mt6768
CPU Arch :
arm64-v8a
Android Serial :
R58RB1VK5BK
Manufacturing Date :
20211109
Security Patch :
2021-09-01
Connection :
mtp,adb
Timezone :
GMT
Android Version :
11
Android SDK :
30
Build :
RP1A.200720.012.A325MUBU1AUH1
Build Date :
Sat Sep 4 05:01:13 KST 2021
Product Code :
SM-A325MZKMMXO
Device Name :
a32
Product Name :
a32ub
Code Name :
SM-A325MZKMMXO
BL :
A325MUBU1AUH1
PDA :
A325MUBU1AUH1
CP :
A325MUBU1AUH1
CSC :
A325MOWO1AUH1
Sales Code :
MXO
Removing
FRP
...
OK
UNLOCKTOOL
2023.07.12.0
Elapsed time :
42 seconds
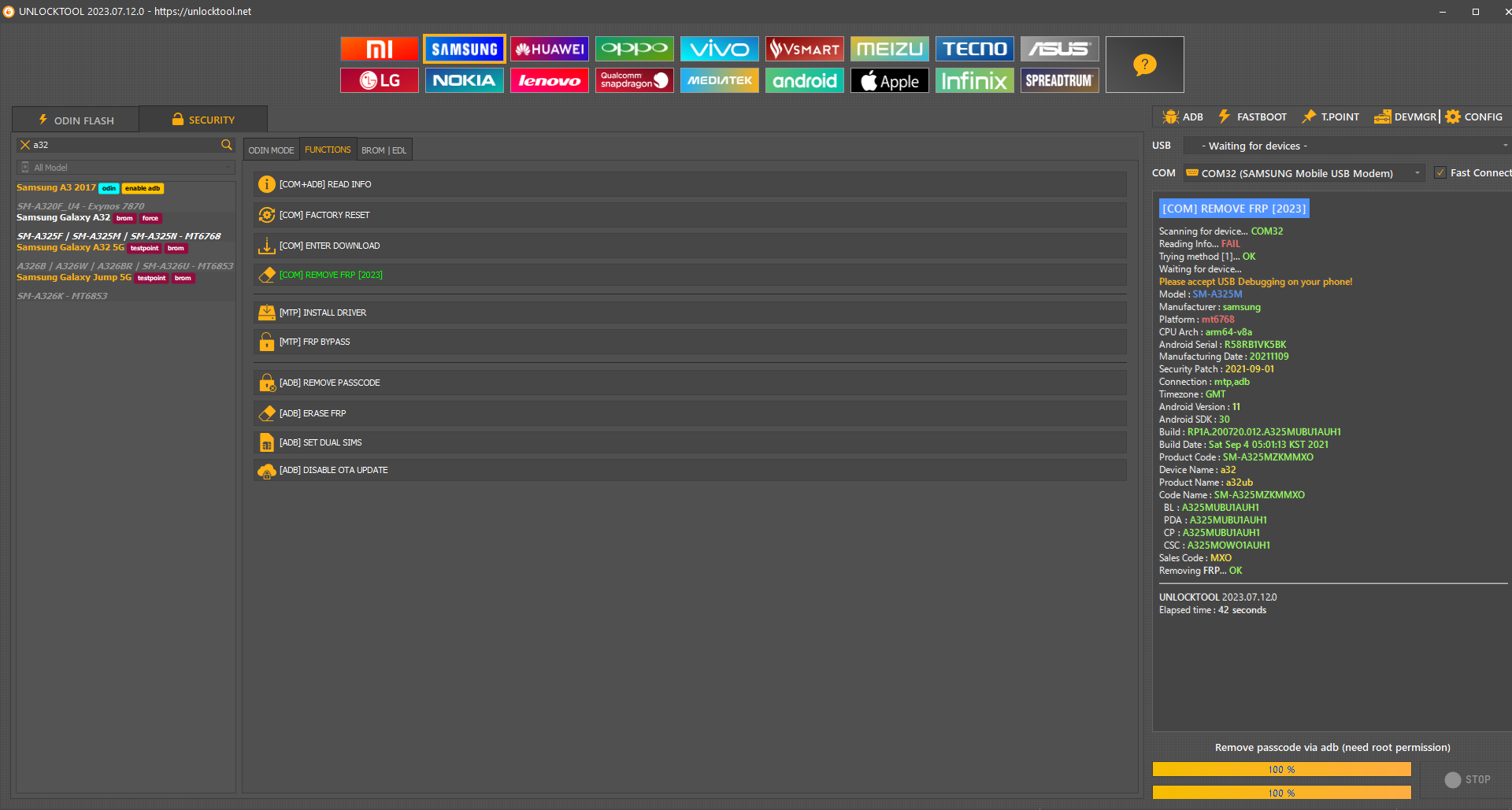
FRP Samsung A23 SM-A235M by UnlockTool
[COM] REMOVE FRP [2023]
Unlock.mx...Done
Scanning for device...
COM31
Reading Info...
FAIL
Trying method [1]...
OK
Waiting for device...
Please accept USB Debugging on your phone!
Model :
SM-A235M
Manufacturer :
samsung
Platform :
bengal
CPU Arch :
arm64-v8a
Android Serial :
R58T30AWG2L
Manufacturing Date :
2022.03.03
Security Patch :
2022-03-01
Connection :
mtp,adb
Timezone :
GMT
Android Version :
12
Android SDK :
31
Build :
SP1A.210812.016.A235MUBU1AVB8
Build Date :
Wed Feb 23 14:41:14 KST 2022
Product Code :
SM-A235MZKDTPA
Device Name :
a23
Product Name :
a23ub
Code Name :
SM-A235MZKDTPA
BL :
A235MUBU1AVB8
PDA :
A235MUBU1AVB8
CP :
A235MUBU1AVB8,A235MUBU1AVB8
CSC :
A235MOWO1AVB9
Sales Code :
TPA
Removing
FRP
...
OK
UNLOCKTOOL
2023.07.12.0
Elapsed time :
57 seconds
FRP ZTE L210 SC7731E
ERASE FRP
Selected Platform :
SC7731E_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM23 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
Reading
device info
...
OK
[super]
Model Name :
ZTE Blade L210
Product Name :
P731F50
Manufacturer :
ZTE
Platform :
sp7731e_1h10
Android Version :
10
Security Patch :
2022-04-05
Build ID :
TEL_MX_ZTE_Blade_L210V2.2
Build Date :
Fri Apr 15 12:15:46 CST 2022
Erasing
FRP
...
OK
UNLOCKTOOL
2023.07.12.0
Elapsed time :
42 seconds
FORMAT DATA
Selected Platform :
SC7731E_Bypass
Connect Testpoint or hold VOL DOWN!
Waiting for device...
COM23 (SPRD U2S Diag)
USB :
USB\VID_1782&PID_4D00\1&1A590E2C&0&0000
Initializing loader...
OK
Protocol :
SPRD3
Sending
payload
...
OK
Sending
auth data
...
OK
Sending
preloader1
...
OK
Sending
preloader2
...
OK
Booting loader, please wait...
OK
Boot ver:
Spreadtrum Boot Block version 1.1
Sending
FDL1
...
OK
Sending
FDL2
...
OK
Reading
partitions info
...
OK
Reading
device info
...
OK
[super]
Model Name :
ZTE Blade L210
Product Name :
P731F50
Manufacturer :
ZTE
Platform :
sp7731e_1h10
Android Version :
10
Security Patch :
2022-04-05
Build ID :
TEL_MX_ZTE_Blade_L210V2.2
Build Date :
Fri Apr 15 12:15:46 CST 2022
Erasing
FRP
...
OK
Erasing
USERDATA
...
OK
UNLOCKTOOL
2023.07.12.0
Elapsed time :
37 seconds
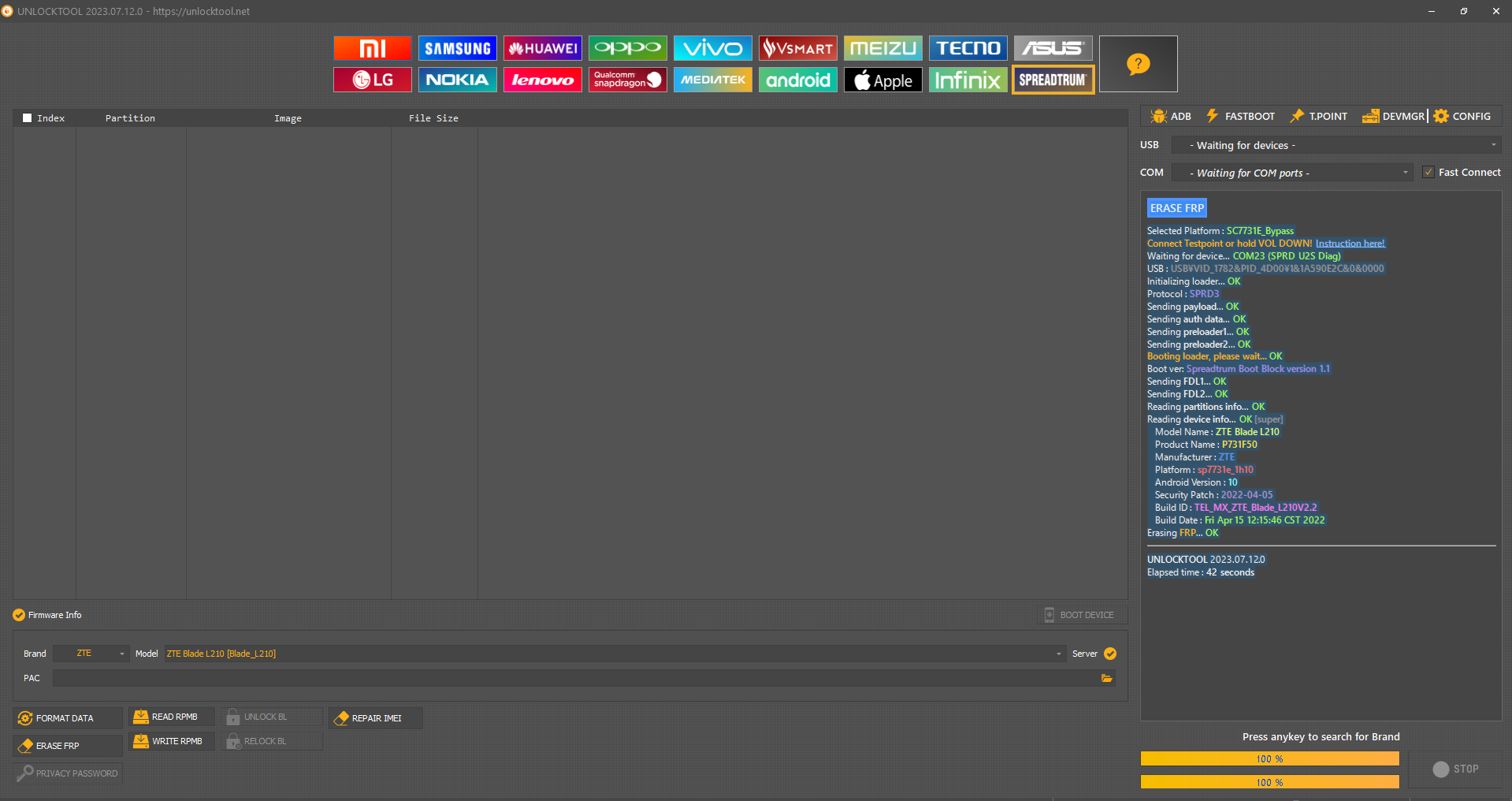
FRP Motorola moto g power (2022) XT2165-5
Starting FRP Remove process...
Waiting for device in Fastboot Mode....Done.
Reading Data....Done
Unlock.mx....Done
Firmware: S3RQS32.20-42-10-14-3
Android: 12
CPU: MT6765H
Model: XT2165-5
SN: ZY22GHDC54
IMEI: 351024744081170
Channel ID: 0x80
CID: 0x0032
Carrier: retca
Reading Data ... Done
Creating Order ID....Done
Operation ID: 1627867
Setting Device Config ... Done
Unlocking Bootloader...Done
Verify Factory CID ... Done.
Reboot Bootloader ... Done.
Wait for Bootloader Reboot ... Done
Wait for Fastboot Mode ... Done
Erase FRP ... Done.
Wait for FRP Clear ... Done
Configuring Bootloader...Done
Erase User Data ... Done.
Erase MetaData ... Done.
Erase misc ... Error.
Clear Mode ... Done.
Fastboot Reboot ... Done.
Elapsed Time: 0:44.15
FRP Motorola Moto C MT6737M by NCK BOX
Exe version: NCKBox AndroidMTK 2.9.7
Selected model: Motorola Moto C
[auto]Action: Reset FRP
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(161) : MediaTek PreLoader USB VCOM (Android) (COM161)
[161] \\?\usb#vid_0e8d&pid_2000#6&1bf12d6f&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Preloader
BBCHIP: 335 0 ca00
Using Algo 2.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6737M
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 1 GB DRAM
----------------------------------------------------
EMMC: (58Gb+8192Mb) SAMSUNG 0x464e36324d42
EMMC FW VERSION: 03:00:00:00:00:00:00:00
EMMC CID: 150100464E36324D42 : 00000000000000
EMMC UA SIZE: 0x1d2000000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x1d2880000 [7.290 GB]
Checking data, wait...
Writing FRP, wait...
FRP Reset Done.
Wait untill phone will start charging.
[0]All done.
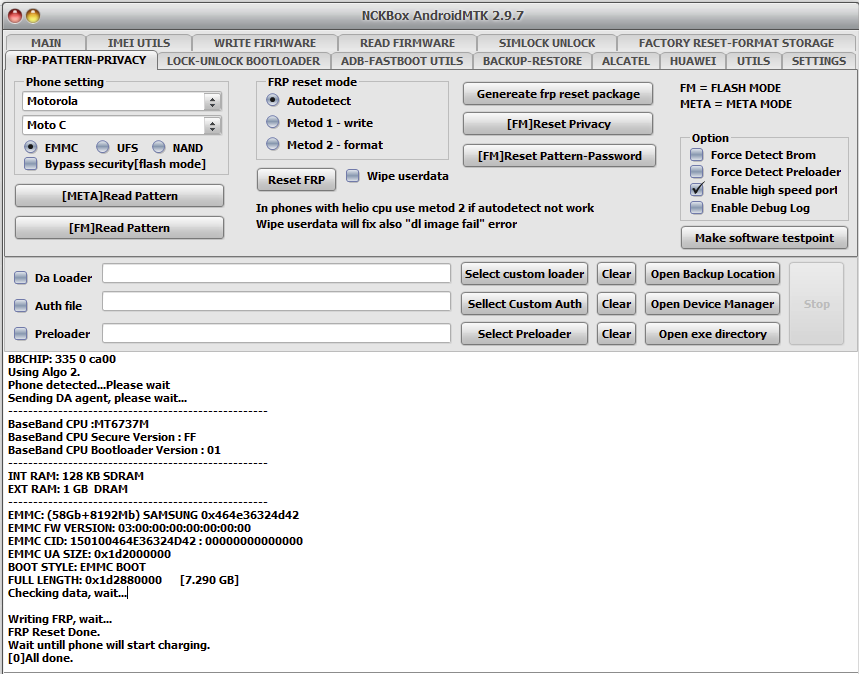
FRP Samsung A02 SM-A022M by UnlockTool
[COM] REMOVE FRP [2023]
Method :
[1]
Scanning for device...
COM22
Enabling
ADB
...
OK
Waiting for device...
Model :
SM-A022M
Manufacturer :
samsung
Platform :
mt6739
CPU Arch :
armeabi-v7a
Android Serial :
R58RA3YVH9K
Manufacturing Date :
20211028
Security Patch :
2021-09-01
Connection :
mtp,adb
Timezone :
America/Mexico_City
Android Version :
11
Android SDK :
30
Build :
RP1A.200720.012.A022MUBU2BUI2
Build Date :
Sat Sep 18 04:51:55 KST 2021
Product Code :
SM-A022MZKLMXO
Device Name :
a02
Product Name :
a02ub
Code Name :
SM-A022MZKLMXO
BL :
A022MUBU2BUI2
PDA :
A022MUBU2BUI2
CP :
A022MUBU2BUI2
CSC :
A022MOWO2BUI2
Sales Code :
MXO
Removing
FRP
...
OK
UNLOCKTOOL
2023.07.04.1
Elapsed time :
28 seconds
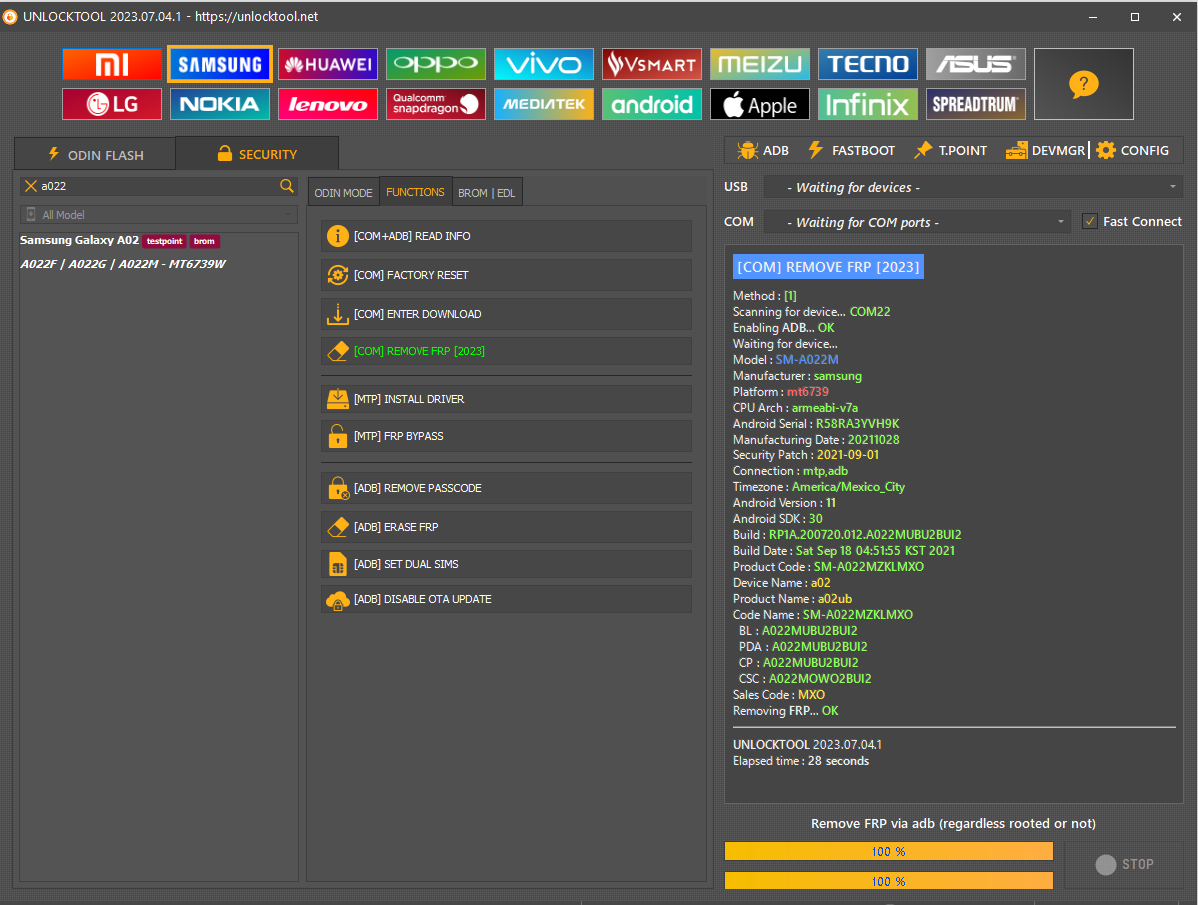
FRP Oppo Reno7 4G CPH2363 by UnlockTool
[EDL] FACTORY RESET Selected Model : Oppo Reno7 4G
Code Name : CPH2363
Operation : Factory Reset [4]
Authenticating... OK
Retrieving data... OK [276.42 KiB]
Initializing data... OK
Waiting for HS-USB QDLoader 9008... COM20
Connecting to device... OK
Handshaking... OK
Reading bootloader info... OK
Serial : 1342983630 SoC : [Snapdragon 680 4G] [SM6250] [0x001B80E1]
OEM : Oppo/Oneplus [0x0051] Model : Unknown [0x0000]
PK_HASH[0] : D53F19D28ED8CA4A5D9C5BD7DDB365DB
PK_HASH[1] : C9268CBDE3DFC8A151E70C8B0A0DFFC2
Writing flash programmer... OK
Connecting to flash programmer... OK
Configuring device... OK
Firehose config : UFS [Sector:4096] [Target:0] [Host:1048576]
Erasing FRP... OK
Erasing USERDATA... OK
Rebooting... OK
UNLOCKTOOL 2023.07.04.1
Elapsed time : 13 minutes 34 seconds
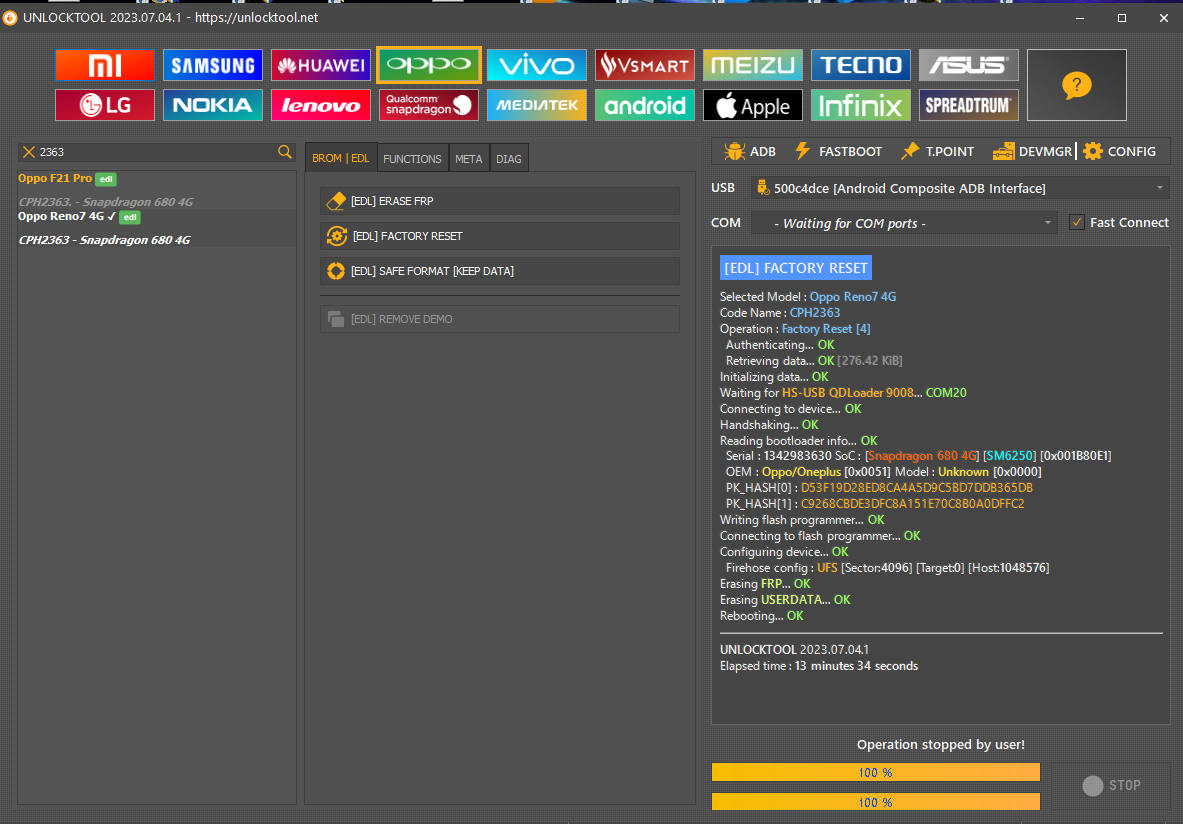
FRP Alcatel 4065F (Alcatel 1L Pro) cuenta google by Pandora Box
Alcatel 4065F (Alcatel 1L Pro) cuenta google
Pandora Box by Z3X
cpu SC9863A_64 con vol - y + sostenido
Selected model: Alcatel 4065F (Alcatel 1L Pro)
Operation: Erase FRP
Software version: 5.3
Work ID: 4047228
Connect phone in BROM mode. Use volume key buttons or testpoint.
Waiting for device... OK
Device found at COM14
Port: USB\VID_1782&PID_4D00\5&14A7B65B&0&1
Driver: [UNISOC Communications Inc.,sprdvcom,SPRD U2S Diag,sprdvcom.sys,4.19.38.134]
Port type: BROM
Connecting to device... OK
Selected processor: SC9863A_64
Load files... (universal) OK
Connect preloader 1... OK
Connect preloader 2... OK
Connect loader 1... OK
Connect loader 2... OK
Serial Number: JZNA06CGILE025X
Read partitions info... OK
Checking A/B state... OK [A]
Read product info... [EXT4] ... OK
Product Brand : Alcatel
Product Manufacturer : TCL
Product Model : 4065F
Product Name : Alcatel 4065F
Product Device : Jakarta_Mini
Product Board : s9863a1h10_go_32b
Board Platform : sp9863a
Build ID : RP1A.201005.001
Build Date : Thu Jul 22 22:05:27 EDT 2021
Display ID : 4065F_TGMX_1SIM_V2.2_20210723
Security Patch : 2021-07-05
Version SDK : 30
Version Release : 11
Version Codename : REL
Firmware Version : 4065F_TGMX_1SIM_V2.2
Userdata FS Type : F2FS
Backup partitions... OK
Formatting "persist" partition... OK
Done!
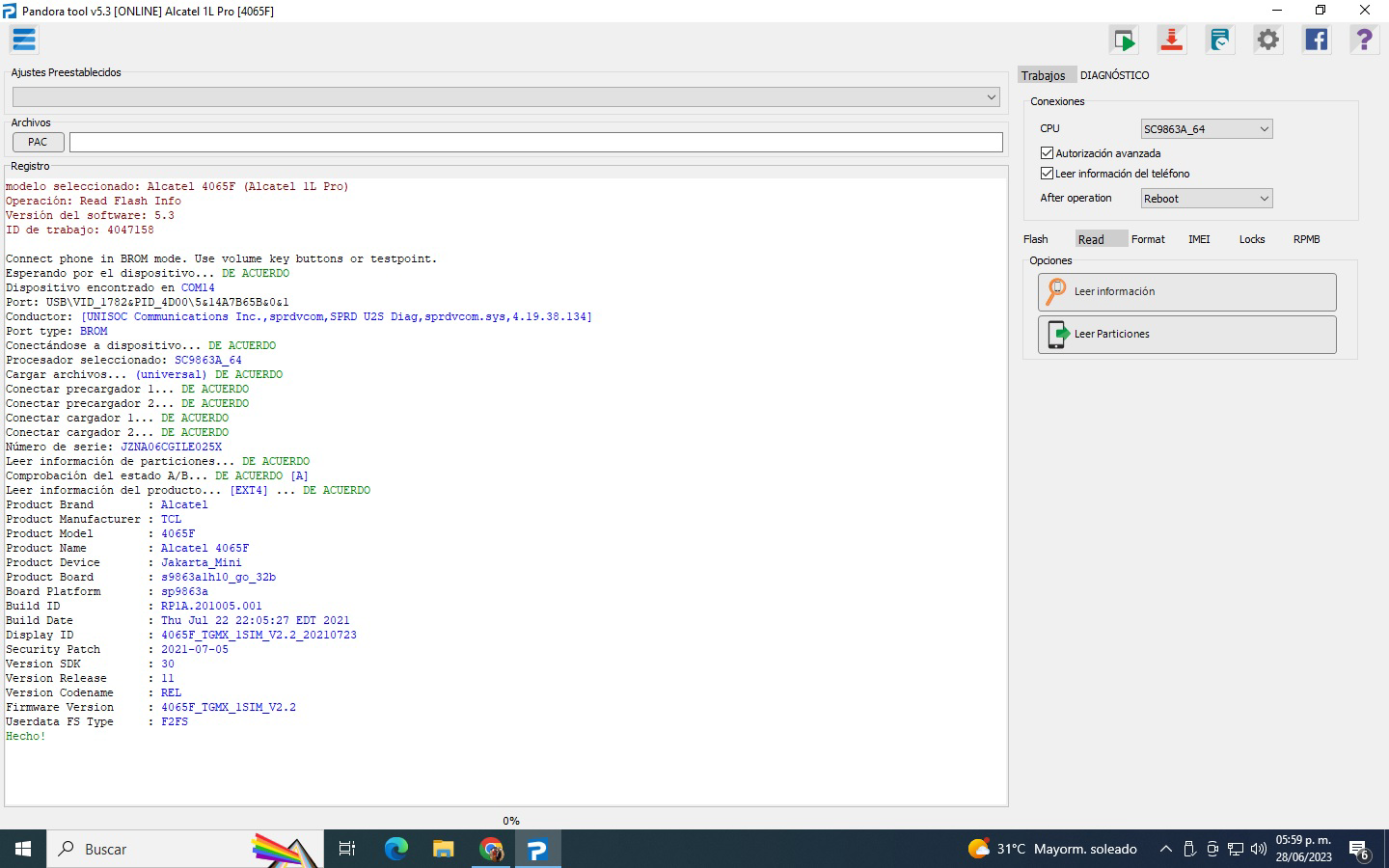
FRP Motorola Moto G20 XT2128-1 Pandora Box
Selected model: Motorola XT2128-1 (Motorola Moto G20)
Operation: Erase FRP
Software version: 5.3
Work ID: 4043978
Connect phone in BROM mode. Use volume key buttons or testpoint.
Waiting for device... OK
Device found at COM7
Port: USB\VID_1782&PID_4D00\5&390FD7C2&0&4
Driver: [UNISOC Communications Inc.,sprdvcom,SPRD U2S Diag,sprdvcom.sys,4.19.38.134]
Port type: BROM
Connecting to device... OK
Selected processor: Tiger_T700_64
Load files... (universal) OK
Connect preloader 1... OK
Connect preloader 2... OK
Connect loader 1... OK
Connect loader 2... OK
Serial Number: ZY32C5HLXP
Read partitions info... OK
Checking A/B state... OK [A]
Read product info... [EXT4] ... OK
Product Brand : motorola
Product Manufacturer : motorola
Product Model : moto g(20)
Product Name : java_retail
Product Device : java
Product Board : p352
Board Platform : ums512
Build ID : RTAS31.68-66-3
Build Date : Tue Feb 21 13:40:32 CST 2023
Display ID : RTAS31.68-66-3
Security Patch : 2023-03-01
Version SDK : 30
Version Release : 11
Version Codename : REL
Firmware Version : 66-3
Userdata FS Type : F2FS
Backup partitions... OK
Formatting "persist" partition... OK
Done!
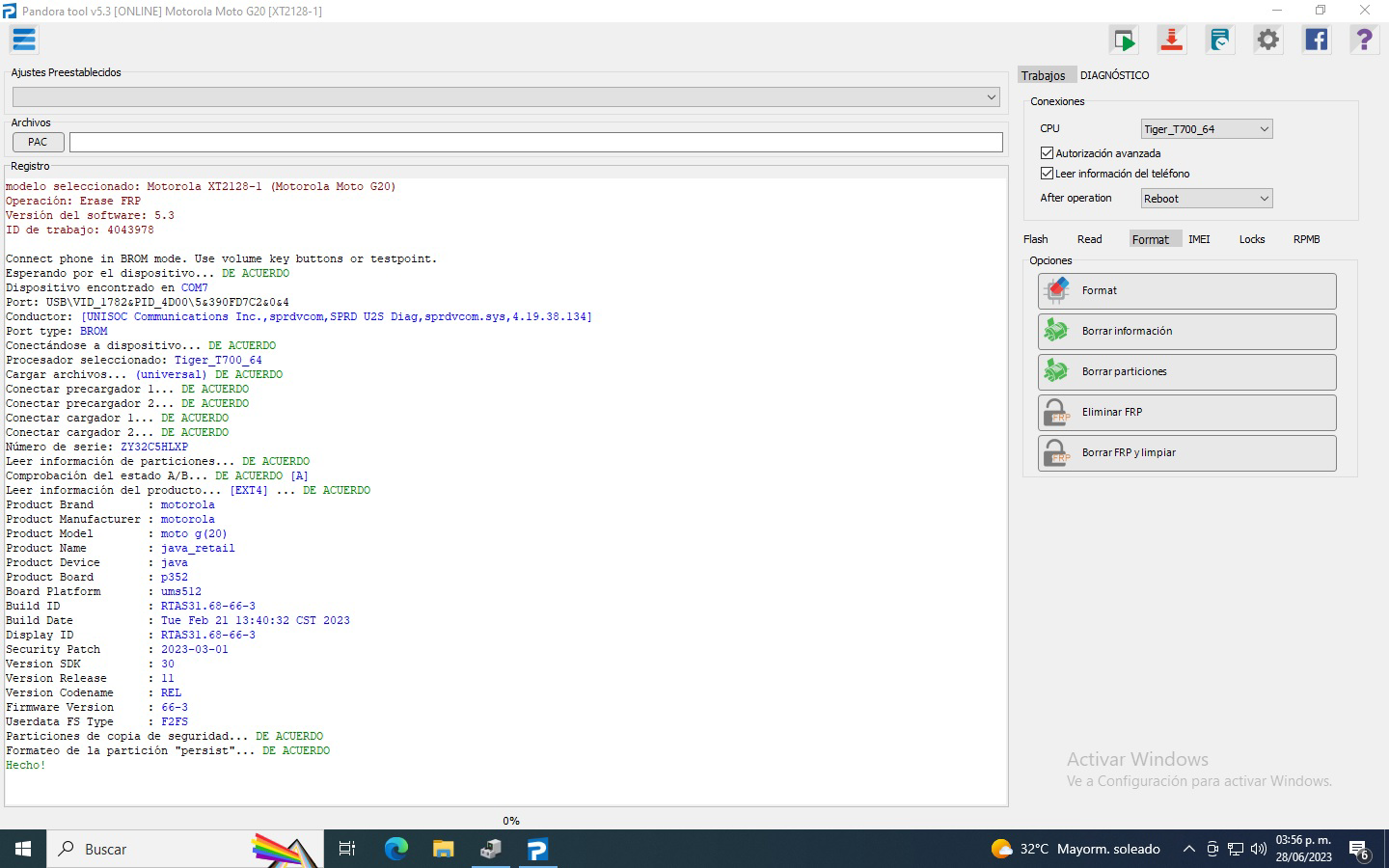
FRP Motorola E7 XT2095-1
FRP Motorola E7 XT2095-1
FRP Motorola XT2117-3 Moto G Power 2021 Verizon
FRP Motorola XT2117-3 Moto G Power 2021 Verizon
Presionar Volumen abajo + Insertar cable USB
Starting FRP Remove process...
Waiting for device in Fastboot Mode....Done.
Reading Data....Done
UNLOCK.MX ..... Done
Firmware: RZBS31.Q2-143-27-4
Android: 11
CPU: SM_KAMORTA_H 1.0
Model: XT2117-3
SN: ZY22D3NP6Z
IMEI: 356898111296981
Channel ID: 0x83
CID: 0x0002
Carrier: vzw
Reading Data ... Done
Creating Order ID....Done
Operation ID: 1602505
Setting Device Config ... Done
Unlocking Bootloader...Done
Reboot Bootloader ... Done.
Wait for Bootloader Reboot ... Done
Wait for Fastboot Mode ... Done
Verify Factory CID ... Done.
Erase FRP ... Done.
Wait 3 Seconds for FRP ... Done
Erase User Data ... Done.
Erase Cache ... Done.
Wait for erase cache ... Done
Configuring Bootloader...Done
Wait for CID ... Done
Erase Modem1 ... Done.
Erase Modem2 ... Done.
Clear Mode ... Done.
Fastboot Reboot ... Done.
Elapsed Time: 0:49.19
FRP Hot Pepper HPP-L55B Serrano MT6739
Aqui le dejo como quitar cuenta FRP
Waiting for mtk usb device... ok
BootMode : Preloader[COM13]
DriverDesc : MediaTek PreLoader USB VCOM_V1633 (Android)
DriverPath : usb\vid_0e8d&pid_2000\6&1a9a519a&0&1
DriverSRV : wdm_usb
DriverVersion : 3.0.1504.0
DriverDate : 1-22-2015
DriverCFG : oem43.inf
DriverOEM : MediaTek Inc.
Start handshake with Preloader...
PreloaderCmd::CMD_BootAsMETA(): Receive READY succeed!
Send BootMode Switch Request...
reboot to meta mode success!
Wait for meta mode usb device...
Init meta mode api...
Connect to SP_META mode...
connect to meta mode success!
Reading device information...
RNID 9c2c80e918a22bac5f7b8e28be708c5100000000
Bluetooth C4:74:F8:21:7C:A5
WIFIMac C4:74:F8:21:4D:4D
Chip ID MT6739
SW Ver alps-mp-q0.mp1-V9.196.1_xthink.q0mp1.k61v1.64.bsp_P10
● Manufacturer Hot Pepper Inc
● Brand HotPepper
● Model HPP-L55B
● DevName HPP-L55B
● Name Serrano
● Board HotPepper
● Build ID HPP-L55B-M-1.0.7
● Android Ver 10 (Quince Tart)
● EMI ID Serrano-user
● Sec Patch 2022-04-05
● UsbConf mtp
● Branch ID alps-mp-q0.mp1
● Build Type user
● Hardware mt6739
● Device State locked
● VerifiedBootState green
● Flash_locked 1
● Veritymode enforcing
● Base android-chinoe
● CryptState encrypted
● CryptType File Based Encryption (FBE) is present.
● SDKVer 29
● FRP Pst /dev/block/platform/bootdevice/by-name/frp
Format frp success
Rebooting from meta mode...success!
UNLOCK.MX & MULTI-UNLOCK.COM
FRP Motorola XT1772 E4 PLUS Done
Se conecta apagado con volumen + / volumen -
Exe version: NCKBox AndroidMTK 2.9.7
Selected model: Motorola XT1773
[auto]Action: Reset FRP
Phone must be off with battery inside.
Battery must be charged
Please insert USB cable now...
For some phones need to keep "VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+ and VOL-" button untill inserting USB cable.
For some phones need to keep "VOL+" button untill inserting USB cable.
Detected(26) : MediaTek PreLoader USB VCOM (Android) (COM26)
[26] \\?\usb#vid_0e8d&pid_2000#6&3492803a&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Boot mode: Preloader
BBCHIP: 335 0 ca00
Using Algo 2.
Phone detected...Please wait
Sending DA agent, please wait...
----------------------------------------------------
BaseBand CPU :MT6737M
BaseBand CPU Secure Version : FF
BaseBand CPU Bootloader Version : 01
----------------------------------------------------
INT RAM: 128 KB SDRAM
EXT RAM: 2 GB DRAM
----------------------------------------------------
EMMC: (117Gb+16384Mb) HYNIX 0x484147346132
EMMC FW VERSION: a5:00:00:00:00:00:00:00
EMMC CID: 90014A484147346132 : 00000000000000
EMMC UA SIZE: 0x3ab400000
BOOT STYLE: EMMC BOOT
FULL LENGTH: 0x3ac000000 [14.688 GB]
Resetting userdata.
Checking data, wait...
Writing FRP, wait...
FRP Reset Done.
Wait untill phone will start charging.
[0]All done.
UNLOCK.MX & MULTI-UNLOCK.COM
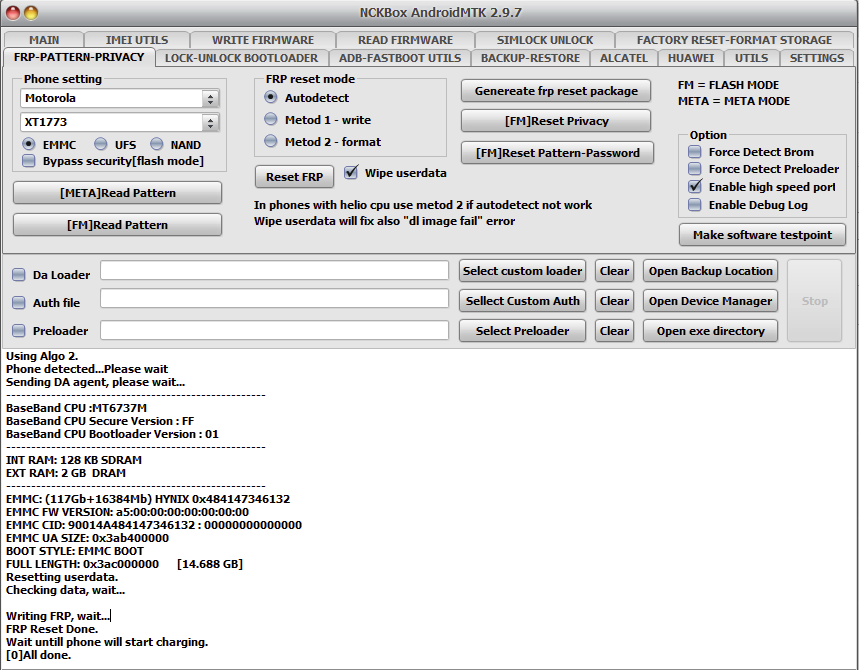
ANDROID UTILITY V106:22.05.2023
ANDROID UTILITY V106:22.05.2023
Link descarga
https://mega.nz/file/h5QVRCpY#VQFVejVWHecQSRvhlh7xOaARQeGpsypDB3HUbT_QnxA
UNLOCK.MX
Necesitas ayuda puedes contactarnos
Motorola E32 XT2227-1 FRP al Instante by Unlocktool
FORMAT DATA Selected Platform : Tiger T606_64_Bypass
Waiting for device... COM14 (SPRD U2S Diag)
USB : USB\VID_1782&PID_4D00\5&14A7B65B&0&1
Initializing loader... OK
Protocol : SPRD3
Unlock.Mx .... OK
Sending payload... OK
Sending auth data... OK
Sending preloader1... OK
Sending preloader2... OK
Booting loader, please wait... OK
Boot ver: Spreadtrum Boot Block version 1.1
Sending FDL1... OK
Sending FDL2... OK
Reading partitions info... OK
Reading device info... OK
Model Name : moto e32
Product Name : hawaii
Manufacturer : motorola
Android Version : 11
Security Patch : 2023-01-05
Build ID : RORS31.335-20-2 release-keys
Build Date : Tue Jan 3 15:58:16 CST 2023
Erasing FRP... OK
Erasing USERDATA... OK
UNLOCKTOOL 2023.05.25.0
Elapsed time : 22 seconds
Venta de creditos y Activaciones
UNLOCK.MX & MULTI-UNLOCK.COM
Desde 2006
Whatsapp: +523781040103
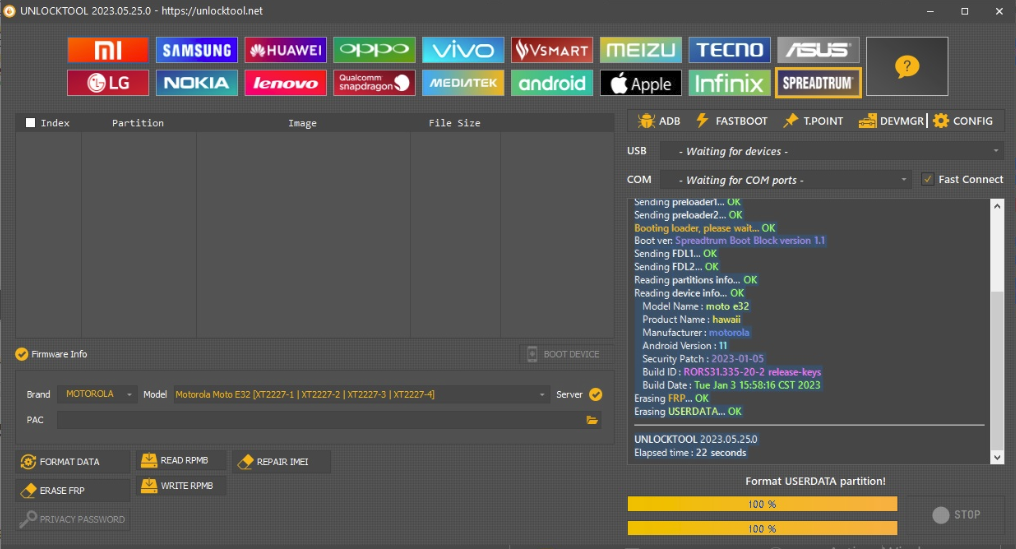
FRP Motorola MOTO G PLAY 2023 XT2271-5 al instante
Aqui les dejo como quitar cuenta google en segundos
Presionar volumen abajo + Insertar cable USB para ponerlo en fastboot
Start FRP Unlock Task on 25/05/2023 3:47:41 PM -07:00
Waiting for device arrival.... OK
Model SKU: XT2271-5
Carrier: RETUS
Serial: ZY22GJSLVX
Authorizing FRP Access...OK
Reboot bootloader...OK
Waiting for device arrival.... OK
Erasing FRP...OK
Erasing UserData...OK
Erasing Cache...OK
Final Step...OK
Rebooting...OK
FRP Unlock Task Successful!
Venta de creditos en WWW.UNLOCK.MX para quitar cuenta google
FRP Samsung *#0*#
Bajar Software desde este links de cualquiera de los dos pueden
https://www.mediafire.com/file/552rnm5hzqrw2lw/SamFwToolSetup_v4.4.zip/file
Despues de instalar el software ocupan ir a esta url
C:\SamFwTool\data
buscar el archivo adb.exe lo seleccionan copiar y pegar lo van a renombrar la copia en adbsl.exe para que pueda abrir el software SamFwTool
SamFw Tool 4.4
[XIAOMI]
[EDL 9008] - Add support Blackshark 3, Mi Max 2, Mi Max 3, Mi 6, Mi 6X, Mi 8, Mi Mix 2, Mi Pad 4, Redmi Note 5/6/7, Redmi S2
- Add support Factory reset/Reset FRP/Reset Micloud
- Fix Windows 7 error
- Optimize execute size
- Update new C++ download links
- Fix some bugs
No device selected
Using port SAMSUNG Mobile USB Modem #6 (COM16)
Reading info mode MTP ... OK
Model : SM-J327T1
CSC : TMK
AP version : J327T1UVS4ASH2
BL version : J327T1UVS4ASH2
CP version : J327T1UVS4ASH2
CSC version : J327T1TMK4ASH2
IMEI : 3556030888XXXXX
SN : R28J527RSPT
Lock status : NONE
MCC : 334
MNC : 020
USB mode : AT,MTP
Unique number : CQ300934BE0BE44
Android version : 7.0
FRP status : LOCKED
Firmware : https://samfw.com/firmware/SM-J327T1/TMK
Using port SAMSUNG Mobile USB Modem #6 (COM16)
Sending ADB exploit (normal)... OK
Sending ADB exploit (normal)... OK
Sending ADB exploit (normal)... OK
Sending ADB exploit (normal)... The port 'COM16' does not exist.
OK
Please click to the allow USB Debugging on the screen. If not apprear, unplug and replug the cable
Waiting for device
Removing... OK
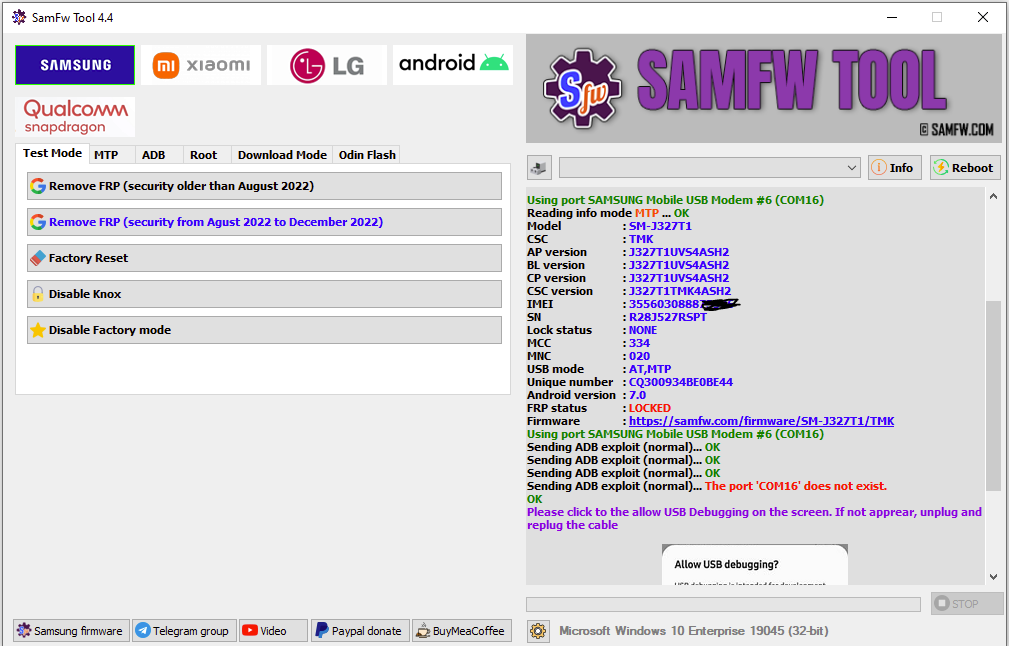
MULTI-UNLOCK.COM & UNLOCK.MX
FRP Lanix Ilium M9V by NckBox Spreadtrum
Como quitar cuenta google FRP Lanix Ilium M9V
Bajar Software desde este link se tiene que pagar para bajarlo
https://www.needrom.com/download/lanix-ilium-m9v/
Pestaña Firmware Flasher
Open Pac File
seleccionar archivo - Ilium_M9V_OPEN_SW_09.pac
Dar click Firmware Settings
Seleccionar solamente estos archivos
- FDL
- FDL2
- Cache
- UserData
- Persist = esta es la area donde se guarda el FRP en los Spreadtrum
- EraseMetadata
Dar Boton OK
Dar Click Flash Phone
Presiionar Volumen + mas Volumen - conectar el cable no soltar los botones hasta que termine de hacer el boot
esperan un momento a que termine el proceso aqui dejo el log
ACTION: Flash Firmware.
Selected firmware: Ilium_M9V_OPEN_SW_09.pac
NV: Default Mode (protect calibration)
Device Storage: EMMC
Start Detect phone...
Phone must be off with battery inside.
Long press "VOL -" key and insert usb cable.
For some phones need to
Long press "VOL -"+ "VOL +" key and insert usb cable.
Detected: SPRD U2S Diag (COM6)
[00:00:00] Sending loader.
BOOT: SPRD3
Sending loader, keep boot key untill loader start.
[00:00:03] Loader ok
[00:00:03] Wait for loader....
Loader OK: ~"Spreadtrum Boot Block version 1.1
Changing bautrate OK.
[00:00:04] [1]First boot done.
[00:00:04] Sending second loader.
[00:00:11] Second loader sent ok.
New flash protocol detected.
[00:00:11] Reading: system
Error while read flash(1).
[00:00:31] Reading: super
System name: super
Phone and firmware have same android
[00:00:31] Reading: miscdata
[00:00:31] Reading: l_fixnv1_a
NVRAM saved to: C:\Users\Montreal\Documents\spreadtrum_module\flashmode_nvram_backup\_354717960063320\_354717960063320_nvram_backup.tar
Phone have super partition.
[00:00:43] Making flash ic repartition.
NV_COMM disabled by user, skip
[uboot_a]Format disabled, skip.
[uboot_log]Format disabled, skip.
[00:00:43] Start write: cache
[00:00:44] Start write: userdata
[l_runtimenv1]Format disabled, skip.
[misc]Format disabled, skip.
[sysdumpdb]Format disabled, skip.
[00:01:21] Start write: persist
[00:01:22] Format: metadata
[00:01:22] [metadata]Format OK.
Flashing done.
[can take 0-10 sec]Wait untill phone restart.
Exe version: NckBox Spreadtrum Module 2.1.8_bugfix
Log saved:
C:\Users\Montreal\Documents\spreadtrum_module\Saved_Logs\_writepac_.txt
Total Time: 00:01:32
Done.
MULTI-UNLOCK & UNLOCK.MX
Best Regard