Blog
-> Reverse Engineering
FRP Huawei Y9s Telcel by Furious Gold Pack 7
Hacer Test Point

30/07/2025 06:21:01 p. m.
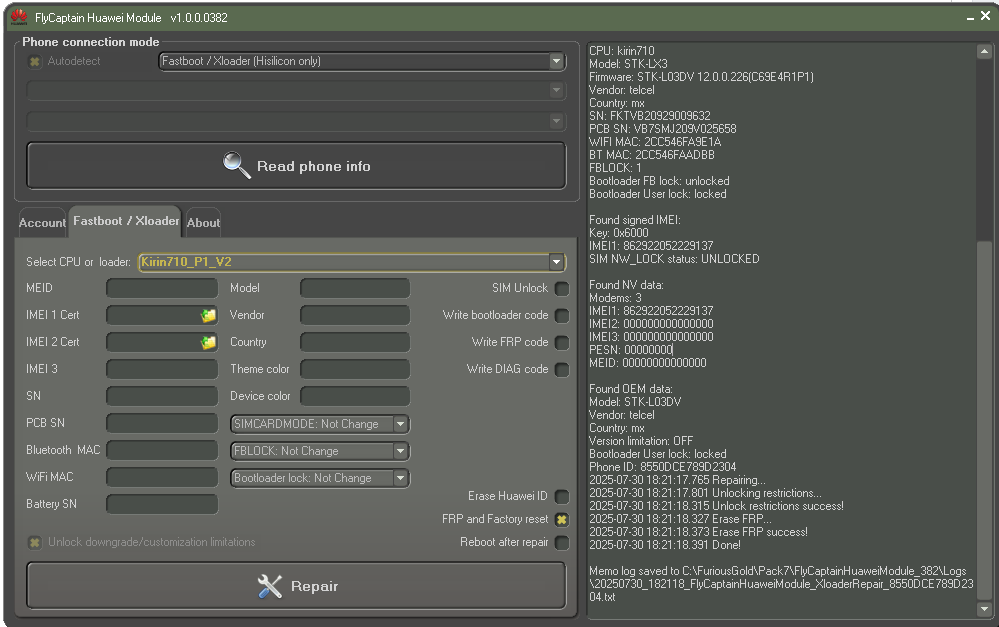
FlyCaptain Huawei Module v1.0.0.0382
Account: 0064B621
Before operation turn phone to TestPoint mode:
Turn off phone, then short TestPoint on phone pcb
and plug USB cable
Wait for device "HUAWEI USB COM 1.0" in Ports
Repair
Unlock downgrade/customization limitations
FRP and Factory reset
Selected Cpu/Bootloader - Kirin710_P1_V2
2025-07-30 18:21:03.387 Connecting to server...
2025-07-30 18:21:03.879 Connected!
2025-07-30 18:21:07.024 HUAWEI device in Test Point mode Not found!
2025-07-30 18:21:07.380 Reading info...
2025-07-30 18:21:11.900 IMEI certifiacate backup success!
2025-07-30 18:21:12.951 Done!
Fastboot provided info:
CPU: kirin710
Model: STK-LX3
Firmware: STK-L03DV 12.0.0.226(C69E4R1P1)
Vendor: telcel
Country: mx
SN: FKTVB20929009632
PCB SN: VB7SMJ209V025658
WIFI MAC: 2CC546FA9E1A
BT MAC: 2CC546FAADBB
FBLOCK: 1
Bootloader FB lock: unlocked
Bootloader User lock: locked
Found signed IMEI:
Key: 0x6000
IMEI1: 862922052229137
SIM NW_LOCK status: UNLOCKED
Found NV data:
Modems: 3
IMEI1: 862922052229137
IMEI2: 000000000000000
IMEI3: 000000000000000
PESN: 00000000
MEID: 00000000000000
Found OEM data:
Model: STK-L03DV
Vendor: telcel
Country: mx
Version limitation: OFF
Bootloader User lock: locked
Phone ID: 8550DCE789D2304
2025-07-30 18:21:17.765 Repairing...
2025-07-30 18:21:17.801 Unlocking restrictions...
2025-07-30 18:21:18.315 Unlock restrictions success!
2025-07-30 18:21:18.327 Erase FRP...
2025-07-30 18:21:18.373 Erase FRP success!
2025-07-30 18:21:18.391 Done!
Memo log saved to C:\FuriousGold\Pack7\FlyCaptainHuaweiModule_382\Logs\20250730_182118_FlyCaptainHuaweiModule_XloaderRepair_8550DCE789D2304.txt
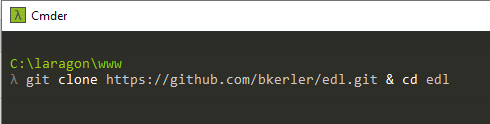
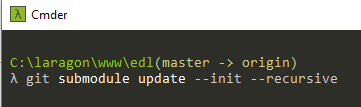
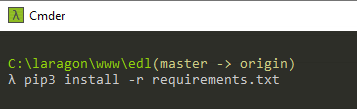
Install and Setup EDL Client
Install and Setup EDL Client
- Download and Install https://github.com/leokhoa/laragon/releases/download/6.0.0/laragon-wamp.exe
- Download and Select Custom Install with path C:\laragon\bin\python\Python312\ https://www.python.org/ftp/python/3.12.4/python-3.12.4-amd64.exe
- Download and Install https://winfsp.dev/rel/
- Download and Install https://github.com/daynix/UsbDk/releases/
- Clone Repo https://github.com/bkerler/edl.git
- git submodule update --init --recursive
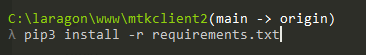
- pip3 install -r requirements.txt
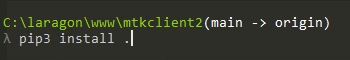
- pip3 install .
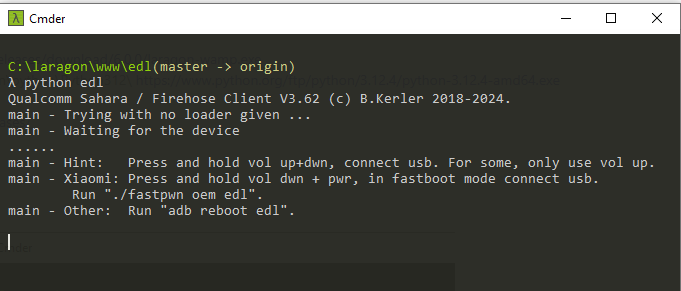
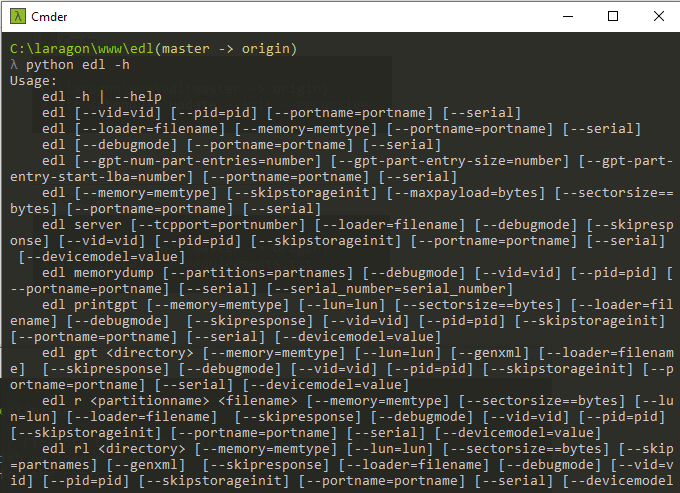
$ edl --serial
$ edl --portname \\.\COM1
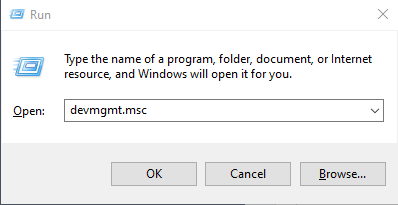
Buscar el puerto COM en Device Manager
Presionar la tecla Windows + R
devmgmt.msc Ejecturar
Install and Setup MTKCLIENT 2
How Install MTK CLIENT
- Download and Install https://github.com/leokhoa/laragon/releases/download/6.0.0/laragon-wamp.exe
- Download and Select Custom Install with path C:\laragon\bin\python\Python312\ https://www.python.org/ftp/python/3.12.4/python-3.12.4-amd64.exe
- Download and Install https://winfsp.dev/rel/
- Download and Install https://github.com/daynix/UsbDk/releases/
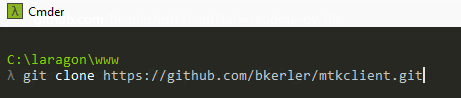
- Clone Repo
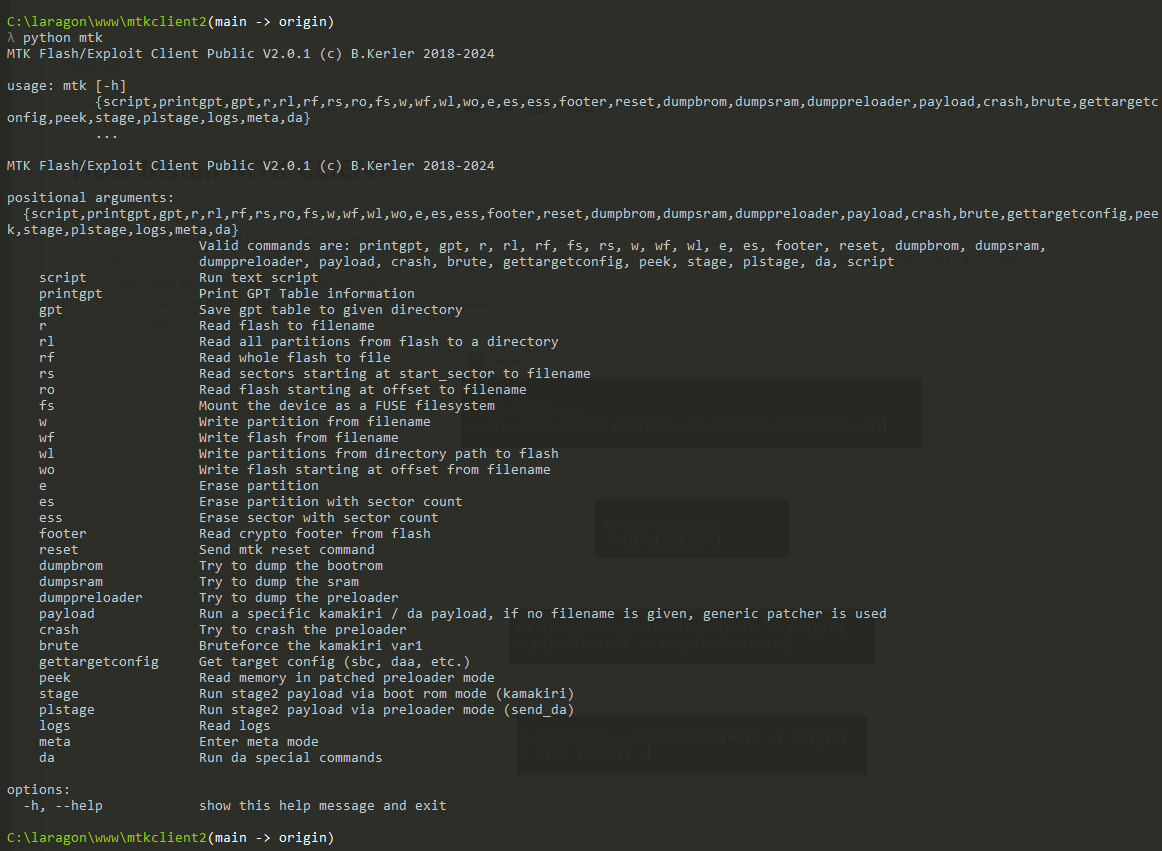
- Exit Brom Mode Phone is Blank Mode or Lcd Black $ python mtk reset
- Read Full Flash $ python mtk rf flash.bin
- Erase partition FRP $ python mtk e frp
- Show gpt $ python mtk printgpt
- Generate and display rpmb1-3 key $ python mtk da generatekeys
- MTK Unlock Bootloader $ python mtk da seccfg unlock
- Bypass SLA, DAA and SBC (using generic_patcher_payload) $ python mtk payload
If you can switch any version mtkclient or install seversal version with git checkout
Example clone mtkclient 1.63
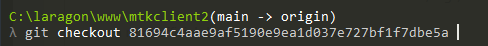
- eba887b9bb3764abf2a56775f6708be1c7589854 refs/tags/1.4
- a70d552fb605c0b8a422ad5899f4a95541079c3d refs/tags/1.41
- 3d4c3f0115ab4c89b823d1d123ec13c24c861dfc refs/tags/1.42
- 1e7f37e5ccdcecc553a8a2363898a6954b6fbdb4 refs/tags/1.52
- 81694c4aae9af5190e9ea1d037e727bf1f7dbe5a refs/tags/1.63
- 537c8c76bccfc5fe7615ecf578081257e45b2591 refs/tags/1.9
you can read official documentation for more use
Best Regard